Creating a Third-Party Vendor Risk Management Policy: Tips and Template
A third-party vendor risk management policy is effective only when it reflects how your organization actually works, not just how processes look on paper. Most teams struggle not because they lack documentation, but because the policy never becomes part of daily vendor decisions, onboarding steps, or oversight routines.
This blog focuses on how to turn a vendor risk management policy into a functional system, one that guides procurement, reduces exposure from third-party dependencies, and gives leadership verifiable proof that risks are being managed with intent.
The goal is simple: move from a written policy to operational discipline that holds up during audits, incidents, or rapid scaling.
Core Takeaways
A vendor risk management policy works only when it’s consistently implemented and updated.
Clear roles, structured workflows, and ongoing measurement make the policy operational.
Automation reduces manual work and ensures risk insights stay current.
Strong governance, audit readiness, and evidence-backed decisions depend on active monitoring.
Auditive helps teams maintain real-time visibility instead of relying on periodic reviews.
What a Strong Third-Party Vendor Risk Management Policy Really Means
A clear vendor risk management policy establishes how your organization identifies, evaluates, and mitigates risks from external partners while maintaining operational resilience.
A vendor risk management policy defines the rules and processes for overseeing third-party relationships that touch your systems, sensitive data, or critical business functions. It provides a structured framework covering:
Onboarding and due diligence: Vetting vendors for financial stability, security posture, and operational reliability.
Continuous monitoring: Regularly reviewing vendor activities, performance, and risk indicators to detect emerging threats.
Risk mitigation and accountability: Assigning clear ownership, response plans, and escalation procedures for potential incidents.
Offboarding and documentation: Ensuring secure termination of vendor access and retention of audit trails.
Implementing a strong policy ensures that vendor partnerships remain secure, resilient, and aligned with your organization’s risk appetite. Beyond operational protection, it demonstrates governance maturity to stakeholders, supporting informed decision-making and long-term business continuity.
Why a Third-Party Vendor Risk Management Policy Is Critical for Your Business
Modern organizations rely on a growing network of third parties, from IT service providers and cloud platforms to suppliers and consultants. Each connection brings potential risks: operational disruptions, data breaches, or exposure to regulatory scrutiny. A clearly defined vendor risk management policy establishes a structured, measurable approach to oversee these relationships, ensuring that risks are consistently assessed and mitigated across the enterprise.
Regulators, including the FCA, OCC, and European authorities under DORA and NIS2, increasingly expect organizations to maintain formal, board-approved oversight of vendors. A strong policy isn’t just about ticking boxes; it helps organizations safeguard resilience, maintain operational control, and protect their reputation in a rapidly evolving risk landscape.
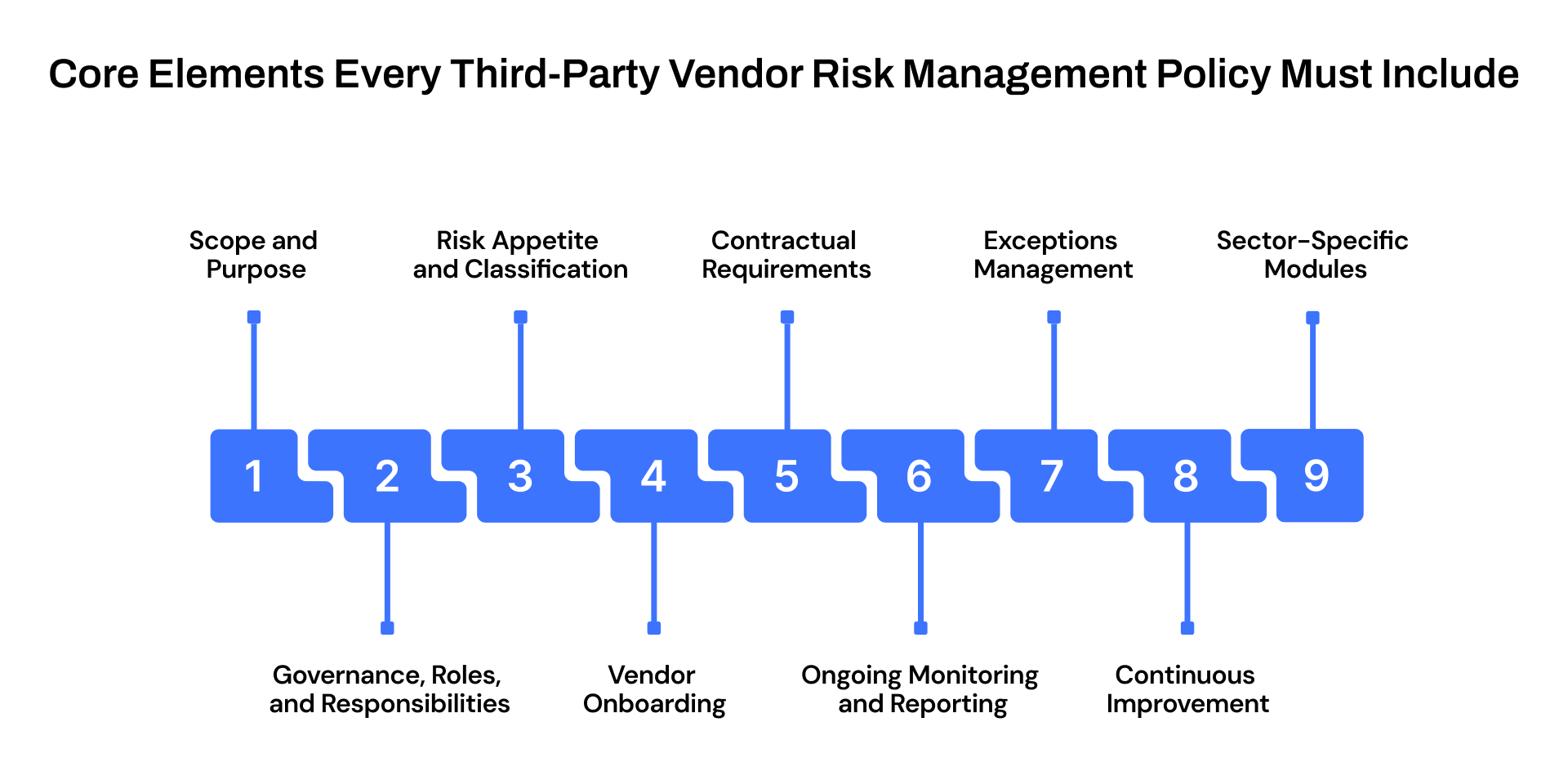
Core Elements Every Third-Party Vendor Risk Management Policy Must Include
A third-party vendor risk management policy is the backbone of how an organization governs its third-party relationships. It ensures operational resilience, mitigates risks associated with suppliers and service providers, and establishes a repeatable, evidence-driven process.
A strong policy balances clarity with enforceability, combining governance principles, operational standards, and practical controls to guide risk management throughout a vendor’s lifecycle.
1. Scope and Purpose
Defining scope and purpose ensures everyone understands the policy’s reach and intention.
Scope: Covers all third-party relationships, including suppliers, contractors, technology partners, and service providers across geographies and business units.
Purpose: Protects sensitive data, reduces operational risk, and aligns vendor oversight with business objectives.
A clearly defined scope prevents ambiguity and ensures stakeholders know which vendor relationships are subject to policy requirements.
2. Governance, Roles, and Responsibilities
Accountability is key to effective risk management. Assigning clear responsibilities avoids overlaps and ensures all risk-related activities are monitored.
Board/Risk Committee: Approves policies, reviews high-risk vendors, and monitors quarterly reporting.
Chief Risk Officer: Oversees policy implementation and ensures alignment with organizational objectives.
Procurement & Business Units: Identify vendors, perform due diligence, and maintain records.
Legal & Security Functions: Review contracts, ensure data protection, and validate cybersecurity standards.
Internal Audit: Independently assesses adherence and effectiveness, providing assurance to leadership.
3. Risk Appetite and Classification
A policy must articulate the organization’s risk tolerance and prioritize oversight accordingly.
Criteria: Evaluate data sensitivity, regulatory exposure, financial impact, and geographical risk.
Classification: Tier vendors into Critical, High, Medium, and Low risk categories to allocate resources efficiently and focus on the most significant threats.
This ensures monitoring and due diligence efforts are proportional to potential risk.
4. Vendor Onboarding and Due Diligence
Proper onboarding ensures risks are identified before the engagement starts.
Pre-contract Checks: Screen for sanctions, verify ownership, assess financial health, and review ESG considerations.
Enhanced Due Diligence: High-risk vendors undergo deeper reviews, including regulatory history, litigation, and data protection maturity.
Approval Workflow: Requires review and sign-off from risk, legal, and security teams, ensuring a comprehensive risk assessment.
Must Read: Comprehensive Guide to Vendor Due Diligence Reports
5. Contractual Requirements
Contracts formalize risk management and enforce vendor obligations.
Right to Audit: Enables oversight of vendor operations and data handling practices.
Data Protection Clauses: Align with GDPR, HIPAA, or other applicable regulations.
Service Level Agreements (SLAs): Set measurable performance metrics.
Incident Reporting & Termination: Define timelines for reporting breaches and conditions for ending contracts.
Also read: Third-Party Contract Management: Steps and Best Practices
6. Ongoing Monitoring and Reporting
Vendor oversight is continuous, not static.
Monitoring: Frequency is risk-tier dependent, from annual reviews for low-risk vendors to continuous monitoring for critical vendors.
Data Sources: Use sanctions lists, financial filings, ESG databases, and cyber threat feeds to maintain visibility.
Reporting: Dashboards and KPIs track performance and highlight risks for senior management review.
7. Escalation and Exceptions Management
Defines how deviations and incidents are handled, reinforcing accountability.
Exceptions: Temporary deviations must be documented, approved, and logged.
Escalations: Significant incidents like breaches or fraud are escalated to the Risk Committee within defined timelines.
Documented escalation paths enhance regulatory confidence and internal governance.
8. Review and Continuous Improvement
Policies should evolve alongside the organization and its environment.
Review Cycle: Typically annually or sooner if regulations or operations change.
Integration: Lessons from audits, incidents, and new regulatory obligations feed into updates.
Continuous improvement ensures the policy remains actionable, relevant, and aligned with risk trends.
9. Annexes and Sector-Specific Modules
Annexes allow customization for industry-specific risks.
ESG Module: Addresses human rights, modern slavery, and environmental impact.
Anti-Bribery & Corruption (ABC): Aligns with FCPA, the UK Bribery Act, and OECD principles.
Cybersecurity & Data Privacy: ISO 27001, GDPR, and NIST CSF alignment.
Financial Crime/AML: Screening obligations for regulated sectors.
Auditive supports your management policy by offering continuous vendor monitoring, AI‑powered assessments, and a unified vendor risk platform delivering verified vendor posture, automatic risk alerts, and streamlined evidence collection to keep oversight active rather than static.
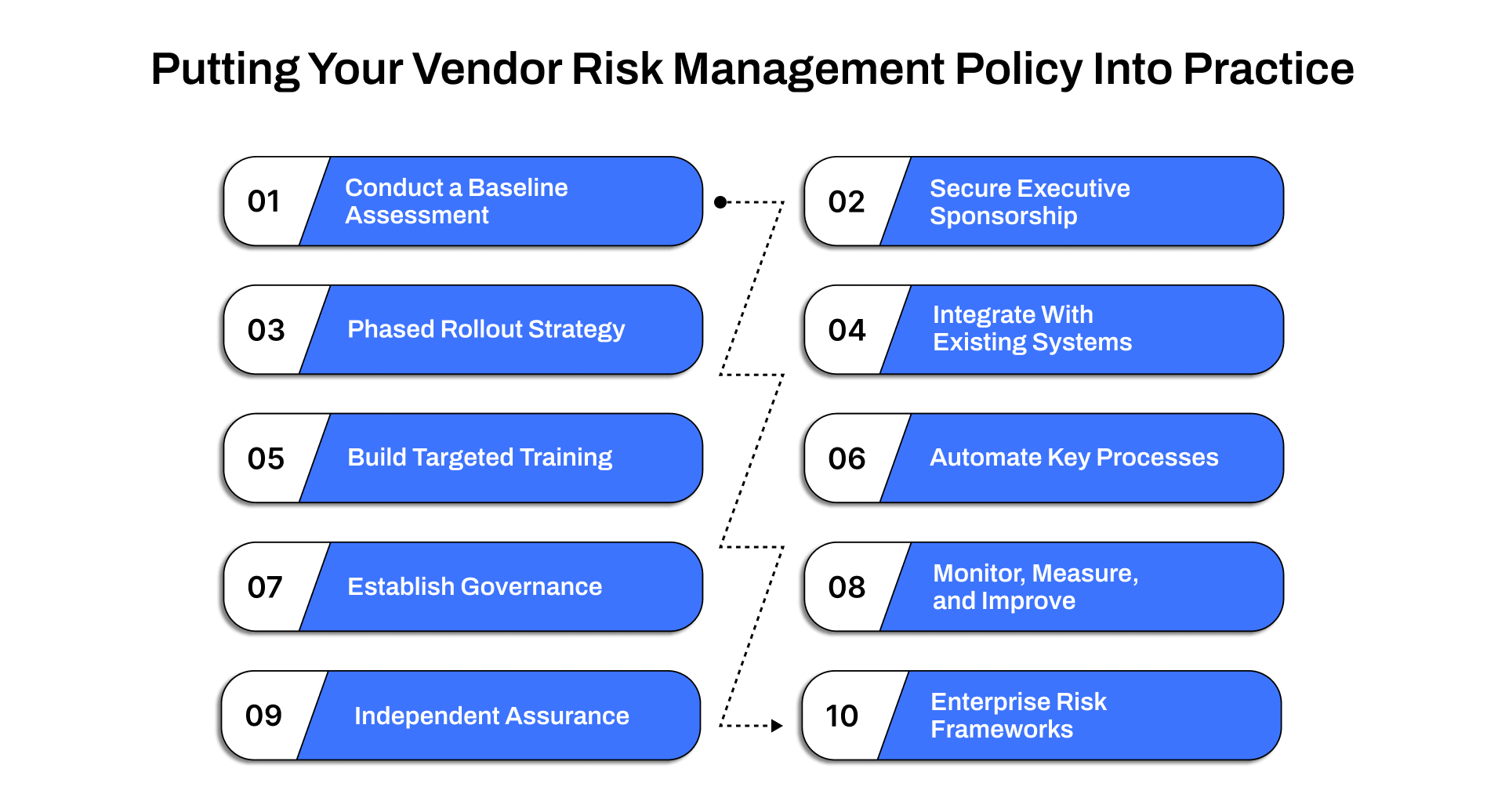
Putting Your Vendor Risk Management Policy Into Practice
A vendor risk management policy delivers value only when it’s embedded into day-to-day decision-making. This section outlines how organizations translate policy guidelines into real workflows, structured governance, and measurable outcomes.
1. Conduct a Baseline Assessment
A policy rollout only works when you know exactly where you stand. A structured baseline assessment reveals your current exposure, process maturity, and the true size of your third-party ecosystem.
Map all active vendors and classify them by data sensitivity and operational impact.
Review your existing due diligence files, monitoring cadence, and contract controls.
Identify redundant steps, missing documentation, and inconsistencies across business units.
Benchmark against regulatory expectations such as DORA, NIS2, and OCC.
A precise baseline gives you a factual starting point, ensuring you don’t implement controls blindly.
2. Secure Executive Sponsorship
Vendor governance cannot scale without executive ownership. Leadership endorsement gives the policy authority and ensures every team takes its responsibilities seriously.
Gain formal approval to enforce roles, decision rights, and resource commitments.
Use leadership visibility to reduce friction across procurement, security, and legal.
Link policy outcomes to executive-level dashboards for ongoing accountability.
When leadership reinforces the policy, it becomes part of business governance, not a compliance checkbox.
3. Define a Phased Rollout Strategy
A controlled rollout prevents disruption and helps teams adopt the policy with confidence. Phased execution allows you to refine the model before applying it organization-wide.
Pilot the policy with high-risk vendor groups or a single business unit.
Capture operational feedback to refine forms, classification models, and approval flows.
Extend the framework across all functions once the workflow is stable.
A phased strategy turns policy adoption into a predictable, measurable, and low-friction transition.
4. Integrate With Existing Systems
A policy succeeds when it plugs into systems your teams already use. Integration removes manual work and ensures adoption becomes automatic rather than optional.
Connect vendor intake steps to procurement and contract management tools.
Link continuous monitoring triggers to GRC or enterprise risk platforms.
Sync cyber-risk insights with existing IT dashboards for unified visibility.
By embedding vendor oversight into everyday systems, you eliminate shadow processes and strengthen traceability.
5. Build Targeted Training and Awareness
A policy holds value only when people understand how to apply it. Targeted training ensures every stakeholder group knows what’s expected and where their responsibilities begin and end.
Procurement: intake, risk tiering, and escalation criteria.
Risk & Compliance: controls evidence, exceptions, and documentation quality.
IT & Security: monitoring workflows and indicators of increased cyber exposure.
Executives: governance checkpoints and oversight expectations.
Clear, role-based guidance ensures consistent execution, reducing misalignment across the business.
6. Automate Key Processes
Manual oversight breaks down at scale. Automation helps teams stay ahead of vendor changes without expanding headcount.
Automate evidence collection, expiration reminders, and periodic reassessments.
Use OSINT-based monitoring to detect sanctions, data breaches, and adverse media.
Trigger automatic alerts when a vendor’s risk score or security posture shifts.
Automating what’s repeatable preserves team bandwidth and strengthens response speed.
7. Establish Governance and Escalation Paths
A strong policy needs clear governance lines so decisions aren’t left to interpretation. Defined structures ensure the right people act at the right time.
Maintain an exceptions register with remediation owners and deadlines.
Set escalation levels by business impact and risk severity.
Conduct quarterly governance reviews to examine risk trends and control failures.
Governance turns your policy from a document into an accountability system.
8. Monitor, Measure, and Improve
Continuous measurement keeps your policy relevant as business and vendor risks evolve. Monitoring ensures the controls you implement actually deliver value.
Track KPIs like risk coverage, onboarding cycle time, and remediation completion rates.
Feed insights into policy updates and vendor engagement improvements.
Use monitoring outcomes to refine training, tooling, and classification criteria.
Measurement closes the loop, transforming oversight from static to adaptive.
Learn more about: What is Compliance Monitoring: Essential Guide for Definition & Importance
9. Audit and Independent Assurance
Independent validation strengthens credibility with regulators, customers, and leadership. Audits verify whether your controls operate as intended.
Review vendor files, evidence logs, and escalation entries.
Ensure workflows match documented procedures and approval paths.
Retain audit trails for regulatory or executive review.
Routine assurance proves your vendor risk management policy functions in practice, not just in theory.
10. Align With Enterprise Risk Frameworks
Vendor oversight becomes more effective when aligned with broader enterprise risk management. Integrated governance prevents siloed decision-making.
Sync third-party risks with enterprise risk appetite and scoring models.
Link vendor dependencies to business continuity and incident response plans.
Ensure consistent data-access controls across internal and external environments.
Alignment ensures vendor risk contributes directly to overall business resilience.
Policy → practice succeeds when evidence, signals, and workflows live in one place. Auditive does this by automating vendor evidence collection, maintaining live vendor profiles, and pushing risk signals into the exact systems teams already use.
How Auditive Strengthens Vendor Risk Management policy
Auditive gives teams real-time, automated visibility into vendor risk so they don’t rely on static questionnaires or scattered documents.
Continuous Monitoring: Auditive tracks vendor posture, certifications, and external risk signals year-round, alerting you the moment something changes.
Automated Document & Questionnaire Review: AI processes security documents and responses at scale, cutting hours of manual assessment work.
Unified Vendor Profiles: Every vendor’s controls, history, and risk data are stored in one dynamic profile, eliminating spreadsheet-heavy tracking.
Faster Decisions: With automated checks and continuous oversight, teams approve, monitor, and re-evaluate vendors far more efficiently.
Auditive replaces slow, periodic checks with real-time visibility, so vendor oversight stays accurate every day, not just during annual reviews.
Final Thoughts
A vendor risk management policy only creates value when it translates into measurable improvements, faster onboarding, tighter oversight, clearer accountability, and consistent visibility across every third-party relationship. The policy becomes a real governance asset when it is maintained, tested, and adjusted as the business and its vendor ecosystem evolve.
Treating it as a dynamic framework rather than a static document ensures decisions are based on current risk signals, not outdated assumptions. That discipline is ultimately what strengthens operational continuity and removes blind spots that typically surface during audits or incidents.
If you want a practical way to operationalize your vendor risk management policy with real-time monitoring and verifiable evidence, schedule a demo with Auditive.
It shows exactly how continuous oversight replaces fragmented checks and gives teams the clarity they need to make risk decisions with confidence.
FAQs
1. Why is a vendor risk management policy important?
It creates a structured mechanism for assessing, categorizing, and monitoring third-party risk so decisions are based on documented controls rather than assumptions.
2. How often should a vendor risk management policy be updated?
Most organizations review it annually, but updates may be needed sooner if there are regulatory changes, new vendor categories, or new risk insights from operational monitoring.
3. Who should be responsible for managing the policy?
Ownership typically sits with risk or governance teams, but procurement, IT, security, and business units all share responsibility for applying the policy in daily workflows.
4. What’s the most difficult part of implementing a vendor risk management policy?
Ensuring consistent adoption across departments, especially when existing processes, tools, or data sources aren’t integrated, often becomes the primary challenge.
5. How does Auditive support vendor risk management policy?
Auditive provides continuous vendor insights, updated evidence, and automated monitoring so teams can enforce their policy with real-time data rather than periodic checks.