Steps to Make a Company HIPAA Compliant in 2025
Healthcare organizations handle some of the most sensitive information, patient records, billing details, medical histories, and insurance data. Protecting this information is not only essential for maintaining trust but also a legal requirement in the United States. The Health Insurance Portability and Accountability Act (HIPAA) sets strict standards for how such information must be stored, accessed, and shared.
For any company working with protected health information (PHI), making a company HIPAA compliant is a critical step. Compliance helps prevent costly breaches, ensures patient privacy, and safeguards your business from penalties. However, many organizations struggle to understand what HIPAA compliance really involves and how to implement it effectively.
Quick Glance:
HIPAA compliance protects sensitive patient data and prevents regulatory penalties.
Steps include risk assessments, policies, safeguards, employee training, and BAAs.
Compliance is ongoing, monitoring, audits, and updates are essential.
Vendor risk management ensures third parties don’t create vulnerabilities.
Using a Trust Center centralizes compliance efforts and builds transparency.
What is HIPAA Compliance?
HIPAA compliance refers to the continuous process of adhering to the standards outlined in the Health Insurance Portability and Accountability Act of 1996 (HIPAA). This federal law was introduced to simplify the exchange of healthcare information, reduce fraud and abuse, and, most importantly, ensure that protected health information (PHI) remains private, secure, and accessible to those who need it.
Compliance is not a one-time effort. It requires organizations to adopt clear policies, implement strict safeguards, and maintain accountability across all departments that handle PHI. This includes how data is:
Stored – whether on servers, cloud systems, or internal databases
Transmitted – through emails, portals, or integrated software platforms
Accessed – ensuring only authorized individuals have entry
Reported – in the event of a breach or security incident
For companies such as healthcare providers, insurers, and even SaaS vendors working with healthcare data, HIPAA compliance acts as both a legal obligation and a framework for responsible data management. Beyond avoiding penalties, compliance strengthens patient trust and demonstrates a clear commitment to safeguarding sensitive health information.
HIPAA Legislation and Compliance Requirements
The Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, was originally designed to protect health insurance coverage when individuals changed or lost their jobs. Over time, the legislation has evolved to address the growing need for safeguarding sensitive health information, especially in the digital era. Today, HIPAA provides a comprehensive framework for protecting patient data and guiding how healthcare organizations and their partners manage information.
At its core, HIPAA defines protected health information (PHI) as any data that can identify a patient, such as:
Name and address
Social Security Number or insurance ID number
Medical records and treatment history
Full facial photographs and other identifying demographics
To ensure PHI remains secure, HIPAA compliance is governed by a set of rules, each serving a specific purpose:
HIPAA Privacy Rule – Establishes standards for the use and disclosure of PHI by healthcare providers, insurers, and other covered entities.
HIPAA Security Rule – Focuses on safeguarding electronic PHI (ePHI), requiring administrative, physical, and technical safeguards to maintain confidentiality and integrity.
HIPAA Omnibus Rule – Extends compliance requirements to business associates, enforces Business Associate Agreements (BAAs), and strengthens protections under the HITECH Act.
HIPAA Breach Notification Rule – Requires organizations to notify affected individuals and authorities in the event of a breach involving PHI.
HIPAA Enforcement Rule – Grants the Department of Health and Human Services (HHS) authority to investigate violations and impose civil or even criminal penalties for non-compliance.
Together, these rules form the backbone of HIPAA legislation, ensuring that patient privacy is not just a best practice but a legal obligation. By complying with these requirements, organizations reduce risks of data breaches, avoid steep fines, and most importantly, maintain patient trust.
Also read: Prevent Data Breaches in Healthcare
Does Your Organization Need to Become HIPAA Compliant?
Not every organization is required to follow HIPAA regulations, but those that deal with protected health information (PHI) in any form must take compliance seriously. Broadly, HIPAA applies to two categories: covered entities and business associates.
Covered entities are organizations that directly manage PHI as part of their core functions. This includes hospitals, clinics, private practices, insurance providers, and healthcare clearinghouses. Essentially, if your organization is delivering care or handling patient records, you fall into this group.
Business associates are third parties that provide services to covered entities while having access to PHI. These can range from billing companies and consultants to cloud storage providers, IT vendors, or communication platforms. Even if your company does not deliver healthcare directly, if your software or services store, process, or transmit PHI, HIPAA compliance still applies.
In short, if your organization is connected to the U.S. healthcare system, either by treating patients or by supporting those who do, then becoming HIPAA compliant is not optional. It is a legal requirement designed to protect patient data and ensure trust across the healthcare ecosystem.
Must look into: Third Party Contract Management Best Practices
Key HIPAA Requirements You Should Know
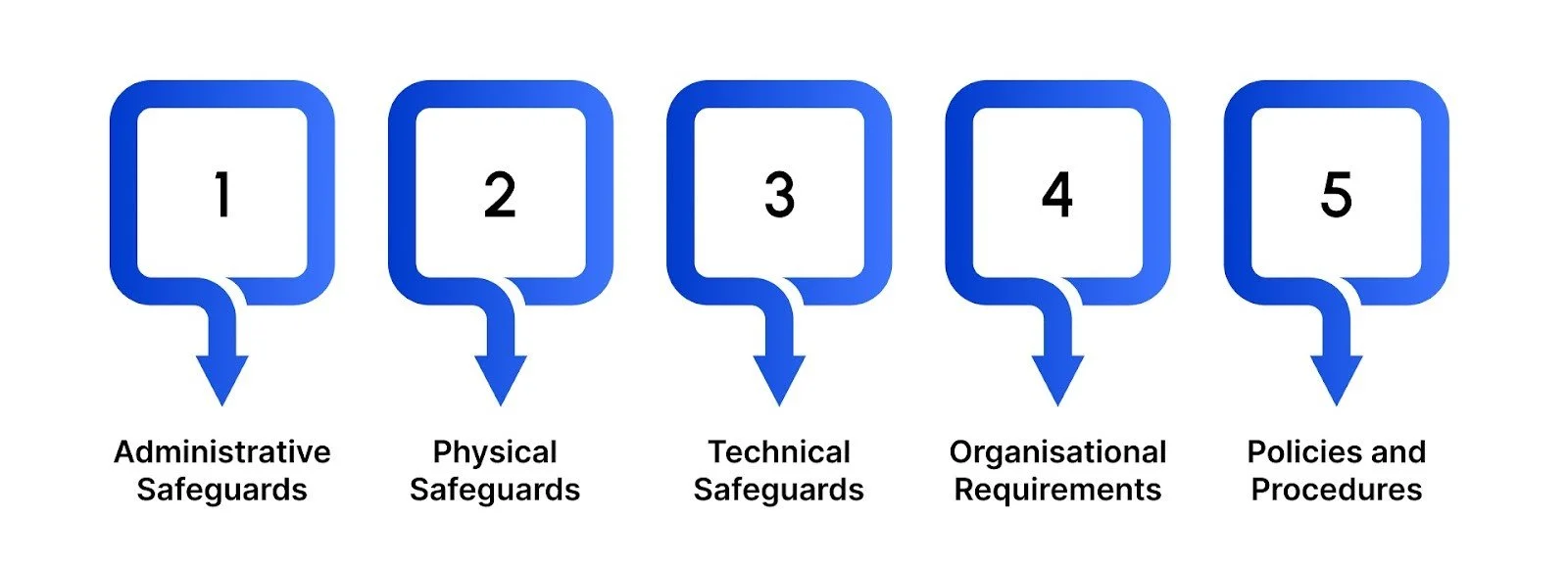
Achieving HIPAA compliance goes beyond technology; it requires a complete approach that addresses people, processes, and systems. The framework is structured around five core areas, each focusing on a different layer of protection for patient information.
1. Administrative Safeguards
These are the policies and governance measures that set the foundation for compliance. Organizations must designate security leadership, carry out regular risk assessments, and ensure staff are properly trained to handle protected health information (PHI).
2. Physical Safeguards
HIPAA also requires measures to secure the physical environment where PHI is stored or accessed. This includes controlling entry to data centers, securing workstations, and making sure outdated devices are disposed of in a secure manner.
3. Technical Safeguards
On the IT side, strong technical controls are essential. Encryption, access restrictions, audit trails, and secure authentication methods are key to protecting electronic PHI both in storage and during transmission.
4. Organizational Requirements
Any vendor or partner that handles PHI on your behalf must also comply. Formal Business Associate Agreements (BAAs) ensure accountability and set clear expectations for data protection across the extended network of service providers.
Learn more about: Understanding Vendors Definition Types Differences
5. Policies and Procedures
Finally, compliance must be documented and regularly updated. Written protocols that reflect actual business practices are crucial for audits and for ensuring consistent enforcement across the organization.
Taken together, these requirements form a layered defense. A company may have advanced cybersecurity measures in place, but without updated policies, vendor oversight, or staff training, it could still fall short of compliance. By addressing each requirement with equal attention, organizations not only safeguard patient trust but also build resilience against regulatory penalties and reputational risks.
Steps to Become HIPAA Compliant
Achieving HIPAA compliance requires a structured approach that goes beyond simply knowing the rules. Organizations must build security into their culture, operations, and technology. Here are the essential steps to guide you through making a company HIPAA compliant:
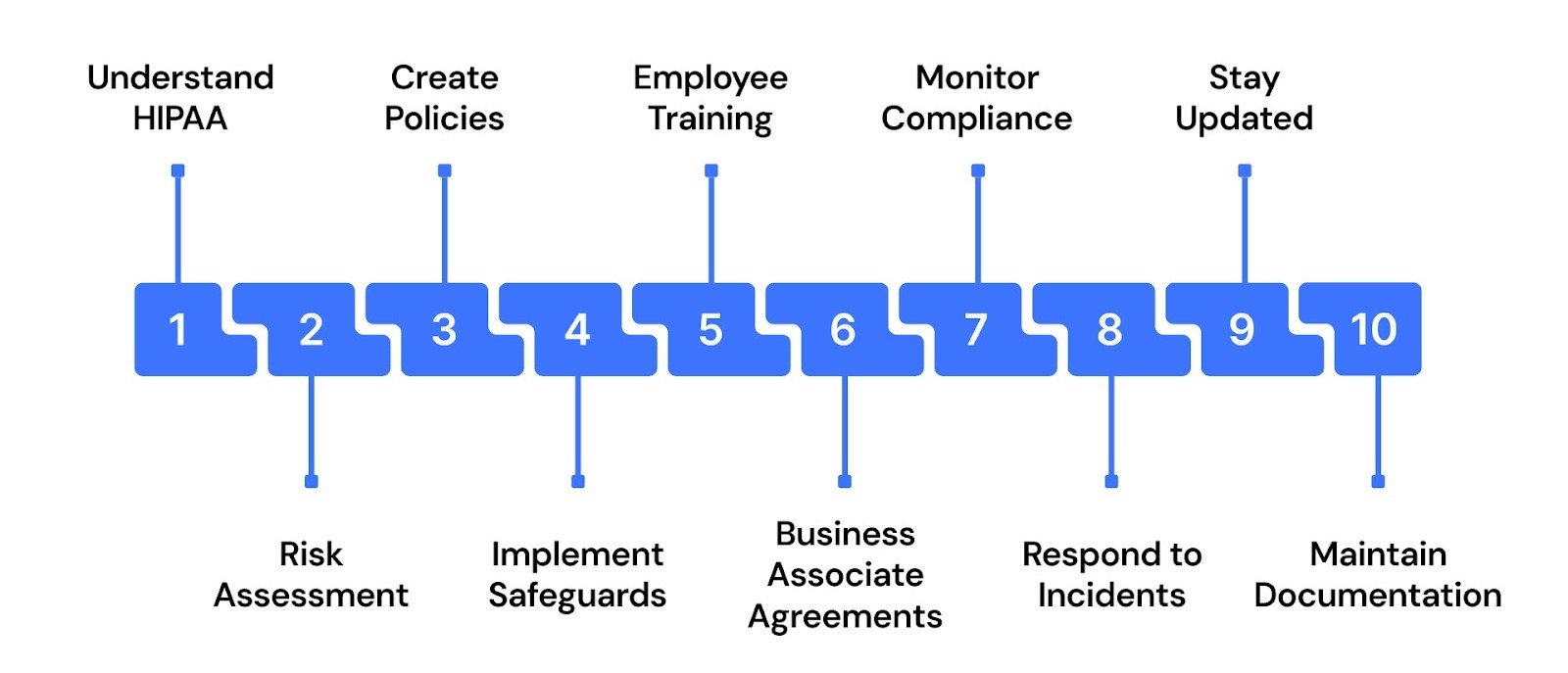
1. Gain a Clear Understanding of HIPAA Rules
The first step is to know exactly what HIPAA expects from your organization. Compliance is built on understanding the legislation itself.
Review the Privacy Rule to understand limits on data use and disclosure.
Study the Security Rule, which outlines safeguards for electronic PHI (ePHI).
Learn the Breach Notification Rule, detailing obligations in case of data incidents.
A strong grasp of these rules ensures your compliance efforts are rooted in the correct legal framework.
2. Conduct a Comprehensive Risk Assessment
Identifying risks early prevents costly problems later. A risk assessment shows where data is most vulnerable.
Map out all systems and processes where PHI is stored or transmitted.
Document vulnerabilities, from weak access controls to outdated software.
Develop a remediation plan to address each identified risk.
Record all findings and corrective actions for audit readiness.
Completing this step provides a roadmap for securing PHI and proving accountability.
3. Create Tailored Policies and Procedures
Policies guide day-to-day behavior and ensure staff handle PHI responsibly.
Define who has authorized access and under what conditions.
Establish encryption practices for data at rest and in transit.
Outline incident response procedures for potential breaches.
Integrate HIPAA requirements into existing operational workflows.
Well-designed policies ensure compliance becomes part of your organization’s culture.
4. Put Safeguards into Practice
HIPAA requires three safeguard categories, each designed to strengthen data protection.
Administrative safeguards: appoint a security officer, enforce access rules, and conduct evaluations.
Physical safeguards: restrict facility access, secure workstations, and protect portable devices.
Technical safeguards: implement access controls, monitor system activity, and secure transmissions.
Together, these safeguards form the backbone of a HIPAA-compliant security program.
5. Train Employees and Keep Records
Employees are often the first line of defence, and training is essential.
Provide role-based training tailored to staff responsibilities.
Include practical examples of how HIPAA applies in daily work.
Repeat training annually to reinforce awareness.
Document sessions as evidence for audits.
Consistent, well-recorded training ensures everyone contributes to compliance.
6. Establish Business Associate Agreements (BAAs)
Vendors handling PHI must follow HIPAA rules, too. BAAs formalize this responsibility.
Identify all third parties who store, process, or access PHI.
Draft agreements outlining each party’s compliance obligations.
Ensure vendors understand breach reporting requirements.
Retain signed copies for records.
These agreements protect your organization from liability linked to vendor mishandling of PHI.
7. Continuously Monitor and Audit Compliance
Compliance is ongoing, not a one-time achievement. Monitoring helps maintain standards.
Track access logs and review them regularly.
Conduct internal audits of policies and systems.
Investigate unusual activity immediately.
Keep records of monitoring activities for future reference.
Active oversight ensures that safeguards remain effective over time.
8. Respond Promptly to Security Incidents
Breaches are inevitable, but your response determines the impact.
Have a documented breach response plan in place.
Notify affected individuals as required by law.
Involve IT teams to contain and investigate incidents.
Record all response actions for compliance evidence.
Quick, organized responses help reduce damage and maintain trust.
9. Stay Aligned with Regulatory Updates
HIPAA requirements may evolve, and staying informed avoids compliance gaps.
Assign a HIPAA security officer to track updates.
Revise policies whenever regulations change.
Refresh training programs with updated requirements.
Communicate updates to all employees working with PHI.
Keeping compliance current safeguards your organization from outdated practices.
10. Maintain Complete Documentation
Documentation is the evidence that proves compliance to auditors and regulators.
Keep risk assessments, audit logs, and incident reports.
Retain training records and policy updates.
Store disaster recovery and breach response plans.
Ensure documentation is organized and accessible.
Proper records demonstrate accountability and readiness for audits at any time.
This structured approach ensures HIPAA compliance is clear, actionable, and sustainable across the organization.
Conclusion
Becoming HIPAA compliant is more than a regulatory requirement; it’s a strategic necessity for protecting sensitive patient data and preserving organizational trust. From risk assessments to implementing safeguards and training employees, every step plays a crucial role in maintaining compliance and avoiding costly breaches.
For companies working with third parties, vendor risk management is equally important, as a single weak link can expose your organization to penalties. That’s where resources like a Trust Center become invaluable, providing a central hub for compliance documentation, risk visibility, and ongoing monitoring.
At Auditive, we empower organizations to simplify HIPAA compliance, strengthen vendor relationships, and build trust through transparency. With the right framework in place, compliance isn’t just about meeting requirements; it becomes a foundation for resilience and credibility.
Ready to take the next step? Partner with us to create a compliance program that goes beyond checklists and builds lasting trust.
FAQs
1. What does HIPAA compliance mean for a company?
HIPAA compliance means following federal regulations that safeguard protected health information (PHI) through security, privacy, and breach notification standards.
2. Who in an organization is responsible for HIPAA compliance?
Typically, a designated HIPAA security or privacy officer is responsible, but compliance requires collective responsibility across IT, legal, HR, and operations teams.
3. How often should a company conduct HIPAA risk assessments?
Risk assessments should be performed annually at a minimum, and more frequently if major system changes, new technologies, or significant breaches occur.
4. Do business associate agreements (BAAs) apply to all vendors?
Yes, any vendor that accesses or processes PHI must sign a BAA, ensuring they share responsibility for compliance.
5. What happens if an organization fails to maintain HIPAA compliance?
Non-compliance can result in hefty fines, legal action, reputational damage, and the loss of patient trust.