Third-Party Risk Management: Guidance on Achieving Compliance
As businesses grow more dependent on external vendors and partners, the risks associated with those third-party relationships become harder to ignore. From data breaches and regulatory violations to operational failures, third-party risks can quickly escalate into costly consequences.
That’s why third-party relationship risk management has become a strategic priority, not just for compliance, but for long-term resilience. With increasing regulatory pressure and growing supply chain complexity, organizations need structured, proactive frameworks to assess, monitor, and mitigate vendor-related risks.
This guide breaks down what TPRM is, why it matters, and how to build a compliant, risk-aware third-party ecosystem.
Overview
Third-party relationships expose businesses to operational, cyber, and compliance risks that can escalate quickly if not managed proactively.
A robust Third-Party Risk Management (TPRM) program includes both pre-onboarding due diligence and continuous post-onboarding monitoring.
Key TPRM steps include vetting vendors, evaluating security and compliance standards, remediating gaps, and tracking ongoing risks.
Failing to manage third-party risks can lead to legal penalties, data breaches, and reputational loss, especially under evolving regulations.
Tools like Auditive’s Trust Center centralize vendor risk management, offering real-time visibility, automation, and stronger compliance assurance.
What is Third-Party Risk Management?
Third-party risk management (TPRM) is the structured process of identifying, assessing, and mitigating risks that arise from engaging with external vendors, suppliers, contractors, and other partners. These third-party relationships, while essential to business operations and scalability, introduce potential vulnerabilities, ranging from cybersecurity threats to regulatory non-compliance and reputational harm.
Effective third-party relationship risk management goes beyond initial due diligence. It involves continuously monitoring partner activities, evaluating risk exposure across various domains (such as financial, legal, cyber, and operational), and implementing controls to minimize impact. This holistic approach ensures that external engagements do not compromise business continuity, data security, or brand trust.
TPRM serves as both a compliance requirement and a strategic function, enabling organizations to collaborate confidently while safeguarding against potential disruptions tied to external dependencies.
Why is Third-Party Risk Management Important?
Third-party relationship risk management is no longer optional; it’s foundational to maintaining a secure, compliant, and resilient business environment. As organizations increasingly rely on external partners to deliver services, manage data, and support operations, the risks tied to these relationships grow exponentially.
A single weak link in the vendor chain can expose your organization to compliance violations, data breaches, or serious operational setbacks.
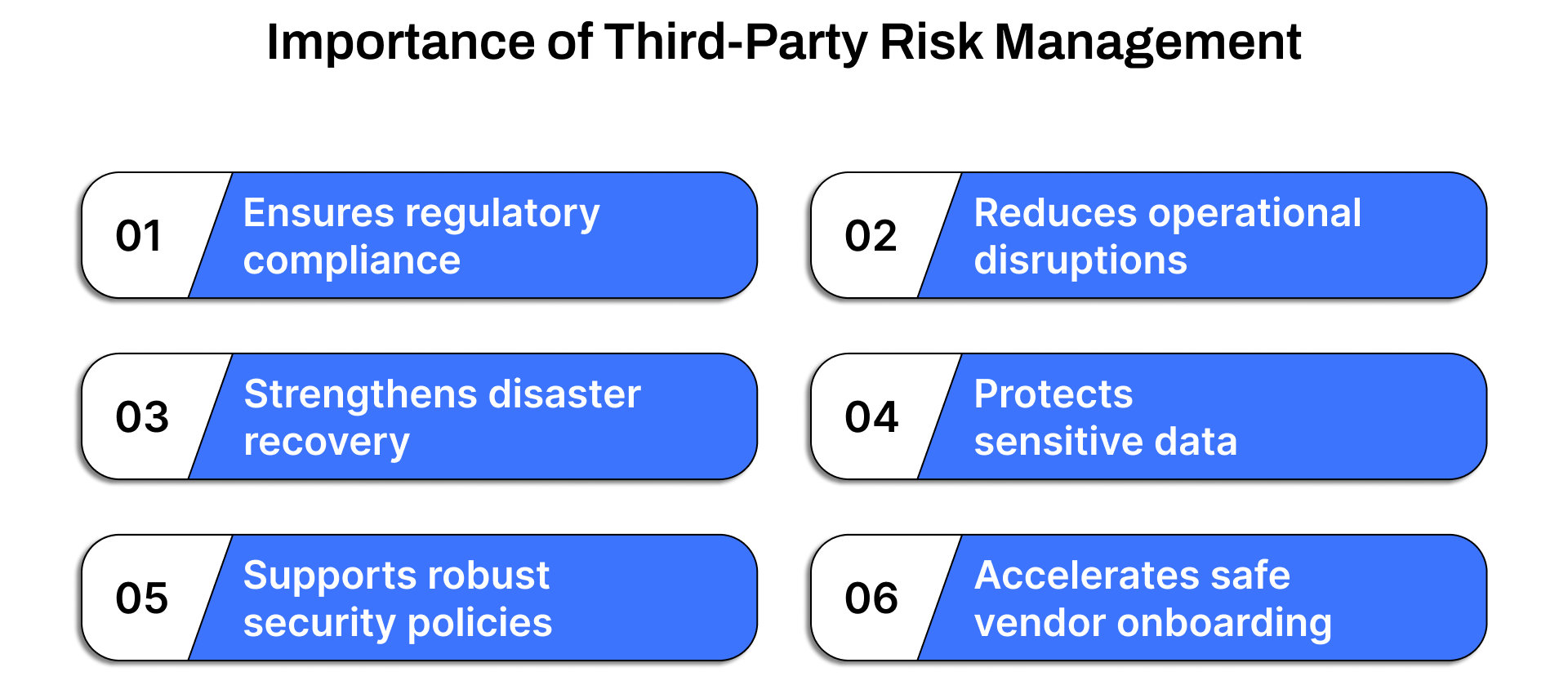
Here’s why third-party risk management should be a priority:
1. Ensures regulatory compliance
Modern regulatory frameworks demand that organizations demonstrate due diligence over their extended ecosystem. TPRM aligns vendor security controls with internal compliance goals, helping you meet mandates like GDPR, HIPAA, PCI-DSS, and ISO standards more confidently.
2. Reduces operational disruptions
TPRM equips you to proactively identify and mitigate vendor-related vulnerabilities that could interrupt core operations. Whether it’s a supply chain delay, service outage, or cyber incident, a strong TPRM strategy keeps your continuity plans intact.
3. Strengthens disaster recovery
According to Shared Assessments, 87% of companies now involve third parties in their disaster recovery processes. With effective risk management, you’re not just reacting to crises; you’re preparing for them by aligning third-party protocols with your own recovery frameworks.
4. Protects sensitive data
As vendors often handle sensitive customer and business data, third-party risk management ensures consistent application of data protection measures across your extended network. It reduces the chances of breaches by enforcing access controls, encryption, and data governance policies.
5. Supports robust security policies
TPRM isn’t just reactive, it’s proactive. It enables the creation of enforceable vendor-facing security policies that guide behavior, require regular training, and promote adherence to standard operating procedures (SOPs).
6. Accelerates safe vendor onboarding
With structured due diligence built into your onboarding workflow, you can evaluate a vendor’s risk profile before formal engagement. This leads to faster onboarding without compromising on security or compliance.
What are the Types of Third-Party Risks?
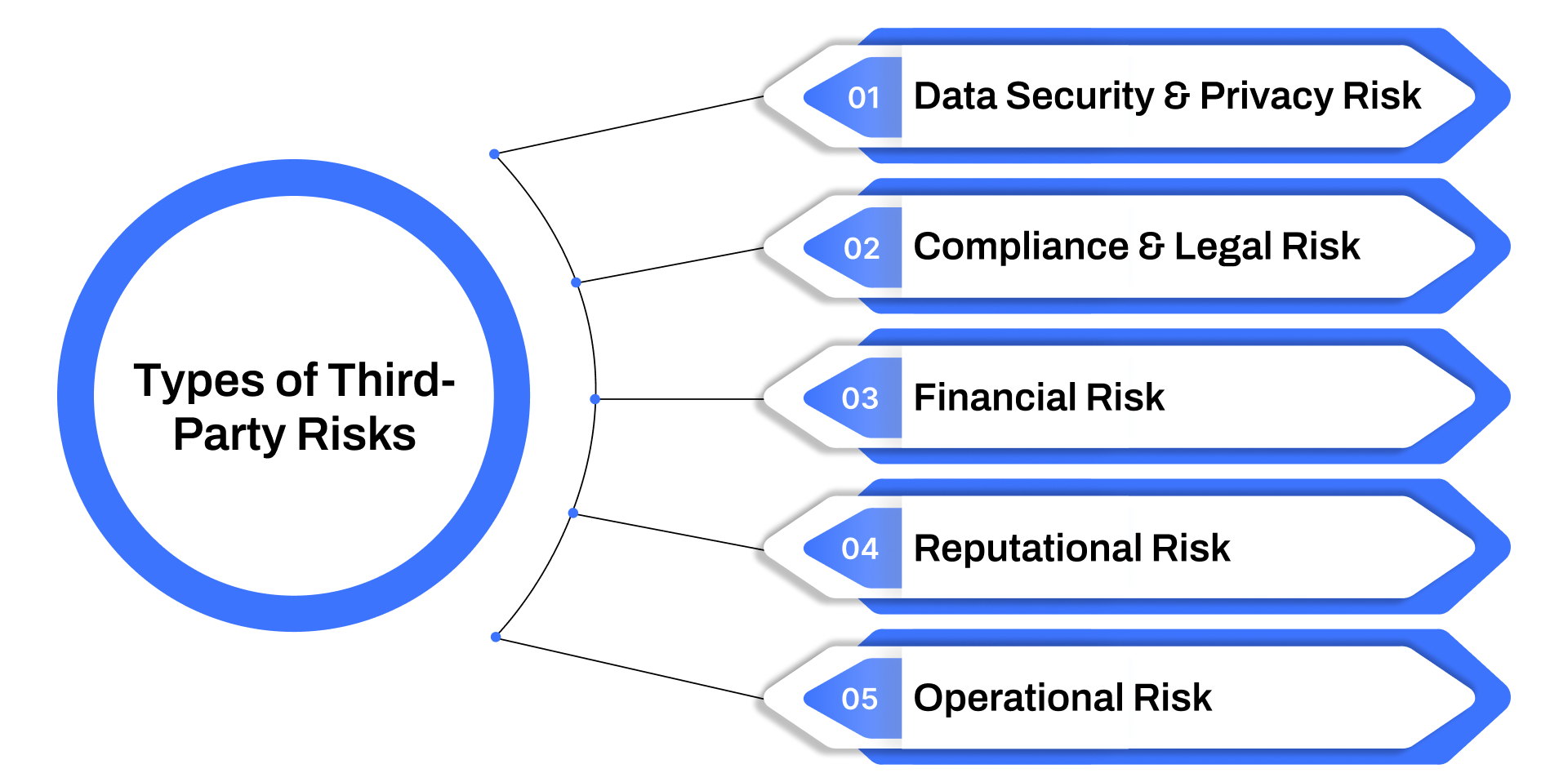
The term "risk" in the context of third-party relationships is broad, spanning everything from data breaches to reputation loss. To manage these risks effectively, organizations must first understand the various categories they fall under:
1. Data Security & Privacy Risk
When third parties access your internal systems, data, or APIs, the risk of exposure increases.
Misconfigured settings
Weak access controls
Poor encryption
Outdated or unmanaged systems
These vulnerabilities can be exploited, either accidentally or maliciously, leading to data leaks, breaches, or regulatory violations.
2. Compliance & Legal Risk
Every organization handling sensitive data must comply with legal frameworks (e.g., GDPR, HIPAA, SOX). Vendors become part of this responsibility.
If a vendor violates legal terms, your business can be held liable
Non-compliance can result in fines, lawsuits, or audits
Shared data expands your legal surface area, so vendor oversight is critical
3. Financial Risk
Not all risk hits immediately, but most will hit the bottom line.
Vendor underperformance or failure can disrupt core services
Sudden vendor changes, hidden vulnerabilities, or contract loopholes can cause costly delays
Often, financial risk is discovered after the damage is done
4. Reputational Risk
Customers don’t see your vendor; they see your brand.
If your vendor engages in unethical practices or suffers a breach, your reputation takes the hit
Public perception and trust can plummet, even if the error wasn’t yours
Recovery from reputational loss is slow and expensive
5. Operational Risk
Outsourcing doesn’t mean offloading accountability. If your vendor goes down, your operations may follow.
Common causes: security incidents, tech failures, or infrastructure issues
Downtime from a third party (e.g., cloud hosting, SaaS provider) can halt customer-facing functions
These failures can erode user trust and lead to SLA violations
With Auditive’s real-time Trust Center, businesses gain proactive visibility into vendor health, helping identify weak signals of compliance lapses or service instability, before risk becomes impact.
Third-Party Risk Management Best Practices
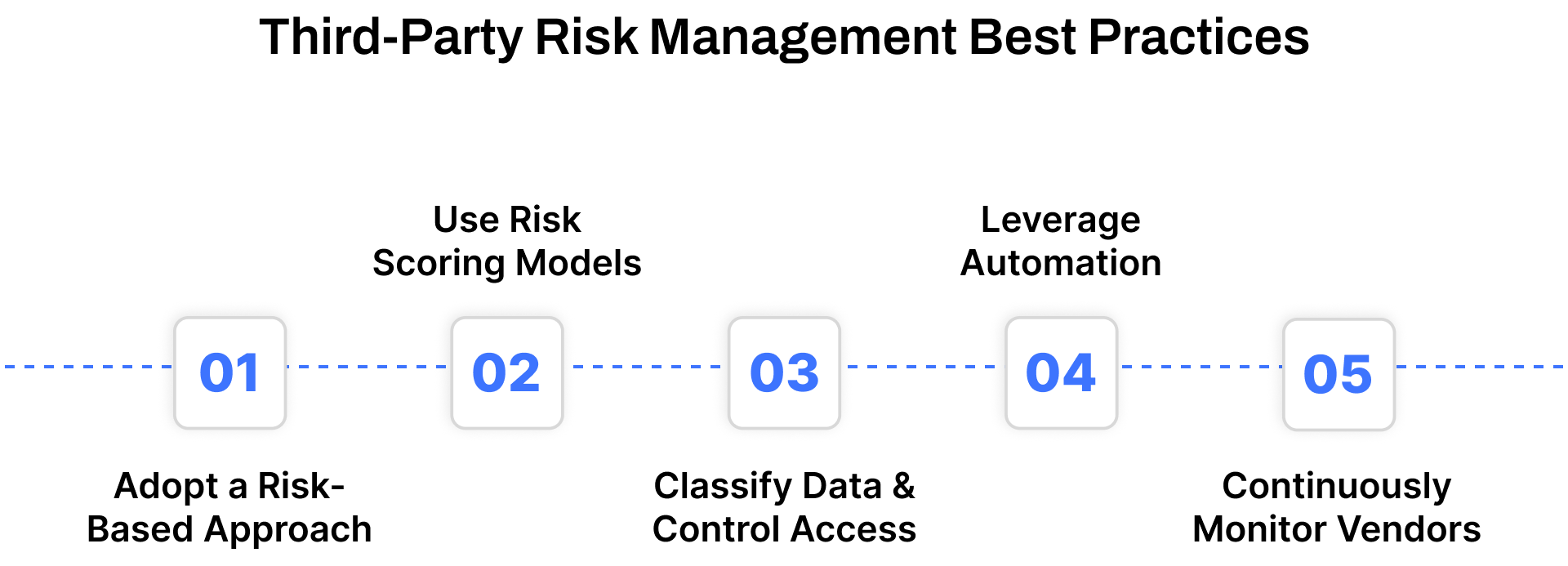
Managing third-party relationships risk management effectively means going beyond one-time assessments or static checklists. It requires a living, risk-informed framework built to adapt as your vendors and threats evolve. Below are proven best practices for reducing third-party exposure and strengthening compliance across your supply chain.
1. Adopt a Risk-Based Approach
Not all vendors pose equal risk. Start by classifying third parties based on their business impact, access to sensitive data, and regulatory relevance. Prioritize your efforts where the stakes are highest, such as critical infrastructure providers or those handling regulated data.
Embed risk evaluation early in the vendor lifecycle, during RFPs, contracting, and onboarding, and reinforce it through audits, compliance assessments, and training.
2. Use Risk Scoring Models
A structured risk matrix or scoring system helps make sense of a complex vendor ecosystem. Segment vendors into high, medium, and low-risk tiers using objective criteria like financial health, cybersecurity posture, and data access.
This triage-style approach ensures your team focuses resources where they matter most, while routine checks continue for lower-risk partners.
3. Classify Data and Control Access
Sensitive data deserves special treatment. Begin by categorizing the types of information shared with each vendor, PII, financials, IP, etc., and map it against access levels.
Follow the principle of least privilege: grant access only when absolutely necessary, and revoke it when no longer needed. Keep audit trails of who accessed what and why, especially helpful during compliance reviews or incident response.
4. Leverage Automation
Automation tools can streamline time-consuming aspects of third-party risk management, like onboarding workflows, sending security questionnaires, tracking remediation efforts, or flagging overdue tasks.
By automating these repeatable processes, organizations can reduce manual errors, shorten assessment cycles, and redirect talent to strategic oversight.
Auditive’s automation-ready platform accelerates vendor onboarding, streamlines compliance workflows, and integrates continuous monitoring, all in one centralized system. This enables faster, smarter third-party risk decisions.
5. Continuously Monitor Vendors
The risk landscape is never static. A vendor that was compliant last quarter could be exposed today due to a new vulnerability, breach, or regulatory shift.
Implement continuous monitoring across key performance indicators like SLA adherence, data handling practices, and security posture. Early detection is your best defense against cascading risk events.
By adopting these best practices, organizations can move from reactive to proactive third-party relationship risk management, reducing exposure, enhancing compliance, and strengthening overall resilience. A structured, risk-first approach, when backed by real-time insights and automation, doesn’t just mitigate vendor risk; it transforms it into a source of strategic advantage.
The Third-Party Risk Management Lifecycle
Given the complexity of third-party ecosystems, implementing a successful TPRM program requires structure and strategy. To simplify this process, the lifecycle is best viewed in two distinct stages: actions to take before onboarding a third party and continuous practices to follow during the vendor relationship. Let’s break this down:
Stage 1: Before You Onboard a Third Party
This phase ensures potential vendors meet your organization’s compliance, security, and operational standards before formal engagement.
Step 1: Conduct Thorough Due Diligence
Start by evaluating the vendor’s background, performance history, and potential risk exposure. Platforms like Capterra, G2, and Software Suggest offer real-world reviews that can signal red flags early. Risk teams should assess how the relationship could introduce vulnerabilities based on the vendor’s business model, data handling, and integration depth.
Step 2: Engage the Third Party
Once initial checks are complete, a deeper review of internal security protocols begins. This includes:
Completion of comprehensive security questionnaires
Verification of compliance certifications (e.g., ISO, SOC 2)
Examination of data protection and privacy policies
Evaluation of employee training programs
Assessment of incident response readiness
This stage ensures that the vendor's internal controls align with your expectations before any sensitive access or data exchange begins.
Step 3: Remediate Gaps and Security Concerns
If misalignments arise, like missing certifications or weak incident response frameworks, don’t move forward blindly. Communicate these gaps clearly and collaboratively address remediation timelines. In some cases, fallback options or contract renegotiation (e.g., stricter SLAs or additional oversight) may be required to reduce exposure before onboarding.
Stage 2: Optimizing Existing Vendor Relationships
After onboarding, continuous monitoring is essential to ensure that third parties remain aligned with evolving business and security requirements.
Step 4: Conduct Periodic Security Assessments
Ongoing assessments help identify drift from contractual or compliance baselines. These checks typically involve:
Reviewing access controls
Evaluating cybersecurity posture
Updating risk profiles
Assessing SLAs and service delivery
Collecting stakeholder feedback
These insights are vital for maintaining a resilient TPRM program, especially when vendors scale operations or pivot services.
Step 5: Track Security Incidents and Breaches
Prompt breach detection and reporting protocols are non-negotiable. If a vendor experiences a security incident, your internal teams must understand response roles, timelines, and communication expectations. Likewise, if your organization is breached, vendors must be informed if impacted. Clear workflows and incident documentation protect both parties.
To effectively manage this lifecycle at scale, you need real-time intelligence. This is where Auditive brings clarity. With automated breach detection, continuous vendor monitoring, and a centralized Trust Center, Auditive ensures third-party risk oversight doesn't stop at onboarding; it evolves dynamically across the vendor lifecycle.
How Auditive Accelerates TPRM Compliance
Staying compliant across third-party relationships requires more than just documentation; it demands real-time oversight, cross-domain visibility, and continuous assurance. That’s exactly where Auditive delivers strategic advantage.
With centralized risk dashboards, automated monitoring, and trust scoring across financial, compliance, cyber, and ESG domains, Auditive empowers teams to anticipate issues before they escalate. Its built-in workflows make onboarding, reassessments, and incident reviews seamless, without chasing spreadsheets or siloed systems.
For risk and compliance leaders navigating evolving regulations, Auditive doesn’t just manage third-party risks, it operationalizes trust across your vendor ecosystem.
Conclusion
Third-party relationships are integral to modern operations, but they also introduce growing layers of risk. Implementing a mature vendor risk management program is no longer optional; it’s a compliance and continuity imperative. From pre-onboarding due diligence to ongoing monitoring, a structured lifecycle approach helps organizations build resilience, ensure alignment, and respond quickly when red flags appear.
Platforms like Auditive take this further by consolidating third-party intelligence into a single Trust Center, offering real-time visibility and automated workflows that reduce manual effort while boosting control.
Ready to make compliance proactive, not reactive?
Explore how Auditive can power your TPRM strategy, from onboarding to breach response, by turning risk into measurable trust.
FAQs
Q1. What is third-party risk management?
A1. It's the process of identifying, assessing, and controlling risks associated with external vendors or partners that your organization depends on.
Q2. Why is TPRM important for compliance?
A2. Regulatory bodies expect organizations to continuously monitor third-party relationships to prevent data breaches, ensure data privacy, and maintain operational resilience.
Q3. What types of risks do third parties introduce?
A3. Cybersecurity threats, regulatory non-compliance, operational failures, financial instability, and reputational damage are the most common.
Q4. How often should third-party vendors be reassessed?
A4. Ideally, vendors should be reviewed periodically, annually or semi-annually, and immediately after any major incident or contractual change.
Q5. How does a platform like Auditive help in TPRM?
A5. Auditive provides centralized vendor intelligence, automated risk assessments, and continuous monitoring, all within a real-time Trust Center that supports smarter decisions and faster compliance.