Conducting Vendor Performance Reviews
Every vendor your business works with carries a level of operational, security, and strategic risk. Understanding these risks before and during a partnership is not just good practice; it’s essential for protecting your data, systems, and overall business performance. Conducting a thorough vendor review ensures you have a clear picture of how your vendors operate, how they handle incidents, and whether their processes meet your organizational expectations.
A structured vendor review goes beyond checklists or static questionnaires. It combines documentation, past incident analysis, and insights from current customers to evaluate vendors in real time.
By implementing a consistent approach to vendor assessments, organizations can make informed decisions, reduce exposure to security or operational gaps, and maintain trust across all third-party relationships.
In a nutshell:
Vendor reviews should reveal how a vendor handles security, incidents, and risks.
The most important inputs include questionnaires, plans, incident reports, and customer insights.
Reviews fail when they rely on static documents instead of verified signals.
Continuous monitoring gives a more accurate picture than annual check-ins.
Auditive helps teams automate and validate vendor insights in real time.
Conducting Vendor Performance Reviews
A clear, structured look at how organizations assess third-party performance, security posture, and ongoing compliance.
A vendor performance review, often simply called a vendor review, is a structured evaluation process used to identify operational, security, and compliance risks associated with a vendor’s products or services. It helps organizations verify whether their vendors consistently follow security best practices and meet regulatory requirements at all times.
Vendor reviews typically assess areas such as data-handling processes, physical and digital security controls, and adherence to standards like HIPAA, GDPR, ISO 27001, and SOC 2. While each organization may apply its own review framework, the process usually includes a detailed security questionnaire, incident report analysis, remediation plans, and customer or user feedback. Reviews are performed when onboarding a new vendor and repeated periodically to confirm ongoing compliance and performance alignment.
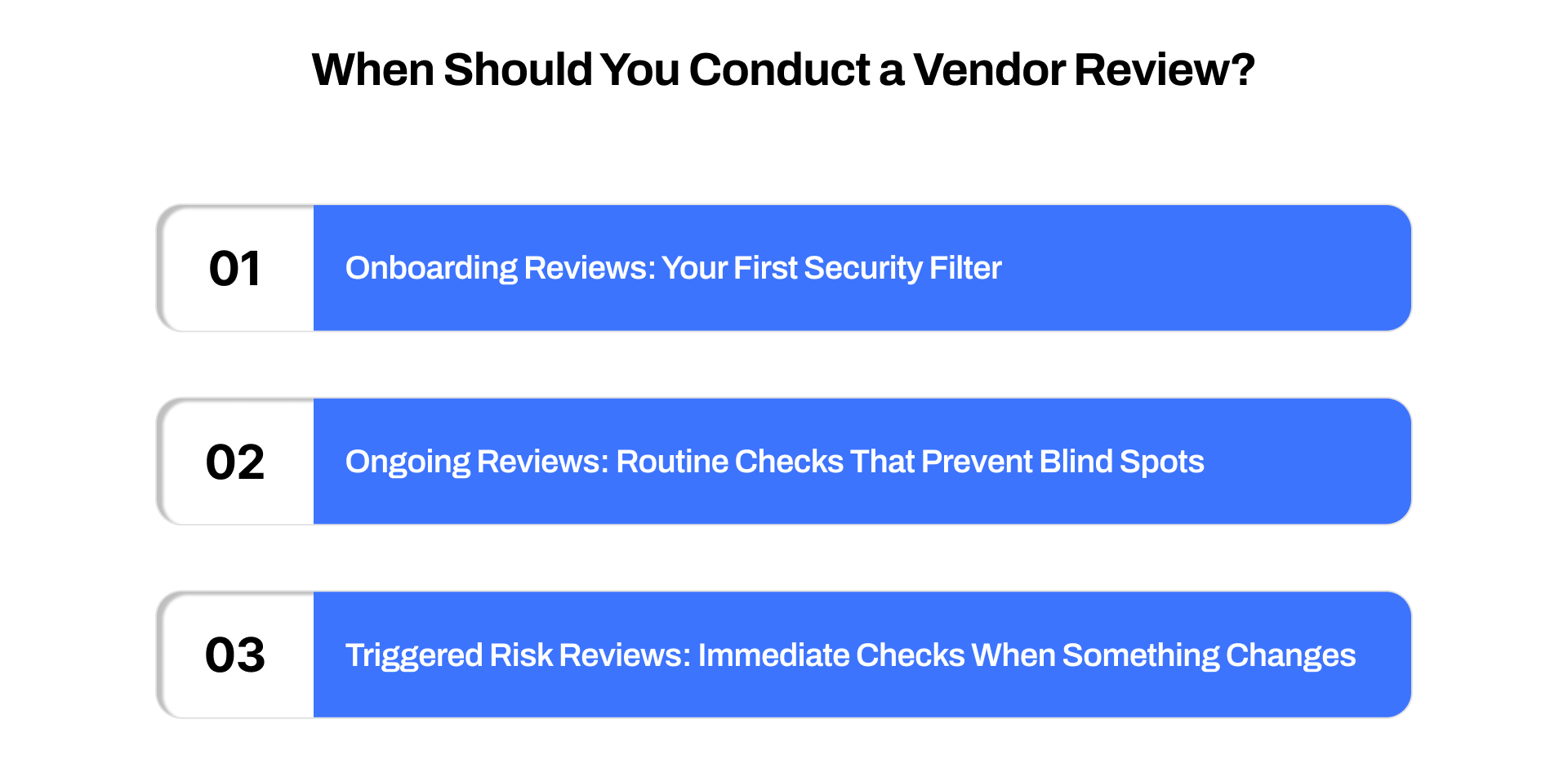
When Should You Conduct a Vendor Review?
Vendor reviews aren’t one-time checkboxes; you run them to confirm that every vendor still meets your security, compliance, and performance standards as your risk environment evolves.
1. Onboarding Reviews: Your First Security Filter
Onboarding reviews → replaced with a more engaging heading, still accurate.
Before onboarding a vendor, run a vendor review as part of your RFP process. Early behavior is often the clearest predictor of long-term performance and risk.
Red flags to look for during the RFP stage:
No data protection process: Indicates weak commitment to customer and security obligations.
No formal security policy: Every vendor should meet baseline data and physical security standards.
No internal risk analysis: Shows the vendor isn’t equipped to detect or contain issues quickly.
No disaster recovery plan: A clear sign they can’t respond effectively during incidents.
Tip: Vendors demonstrating structured processes during RFP tend to maintain stronger compliance post-onboarding.
Must Read: Understanding Vendor Onboarding Costs and Their Impact on Efficiency
2. Ongoing Reviews: Routine Checks That Prevent Blind Spots
Once a vendor is onboarded, their risk posture won’t stay static. Standards change, controls weaken, and new threats appear. That’s why ongoing vendor reviews are essential to validate whether the vendor still meets your expectations.
Recommended review frequency by risk tier:
Low-risk vendors: 1–2 times per year
Medium-risk vendors: 1–2 times per year
High-risk vendors: Quarterly or twice a year
Upcoming contract renewal: Begin the review 180 days before the renewal date
This cadence helps prevent compliance drift, one of the most common causes of late-identified security gaps.
3. Triggered Risk Reviews: Immediate Checks When Something Changes
Some situations require you to run a vendor security review immediately, regardless of schedule. These events typically indicate a change in the vendor’s risk posture.
Run a triggered vendor review when you detect any of the following:
Negative press or public buzz: Often signals internal instability.
Financial red flags: Declining ratings, layoffs, or bankruptcy filings.
Prior risk-assessment concerns: Verify whether the original issue has resurfaced.
Legal disputes: Lawsuits involving the vendor or leadership can indicate governance issues.
Safety or security incidents: Any rumor or report of data leaks or operational failures.
Continuous monitoring, formal and informal, helps you catch these indicators early.
Also Read: Understanding Data Leak Prevention: Key Benefits and Practices
Running the right vendor reviews at the right time protects your business from avoidable security, compliance, and operational risks. With consistent oversight and timely evaluations, you maintain control, not the vendor.
What’s the Real Goal of a Vendor Review?
A vendor review helps you understand exactly who you’re trusting with your systems, data, and operational stability before any risks turn into business-wide damage.
A well-structured vendor review focuses on assessing whether a third-party partner can operate securely, reliably, and in full alignment with your organization’s risk appetite. At its core, the goal is to identify risks early and evaluate how well the vendor can prevent, manage, or escalate them.
Here’s what a precise, outcome-driven vendor review aims to uncover:
Pinpoint any risks the vendor introduces, from data exposure to process gaps.
Evaluate the vendor’s ability to eliminate or minimize those risks, based on controls, processes, and past performance.
Monitor risks that cannot be fully removed, ensuring they remain visible and measurable.
Understand the potential business impact of major risks, especially on uptime, compliance, and customer trust.
Determine whether your organization can reasonably absorb those risks, given its security posture and tolerance levels.
Confirm whether the vendor’s services truly meet operational and security requirements, not just on paper but in execution.
When done right, a vendor review turns uncertainty into clarity. It helps you surface risks early, verify whether a partner can truly support your operations, and avoid surprises that could disrupt your business later.
Learn more about: Understanding Vendors: Definition, Types, and Differences
How to Conduct a Vendor Review (Clear, Practical, and Purpose-Driven)
A vendor review gives you evidence, not assumptions, about whether a vendor is strengthening your operations or silently holding them back. It helps you evaluate performance, risk, and value so you can make decisions grounded in data.
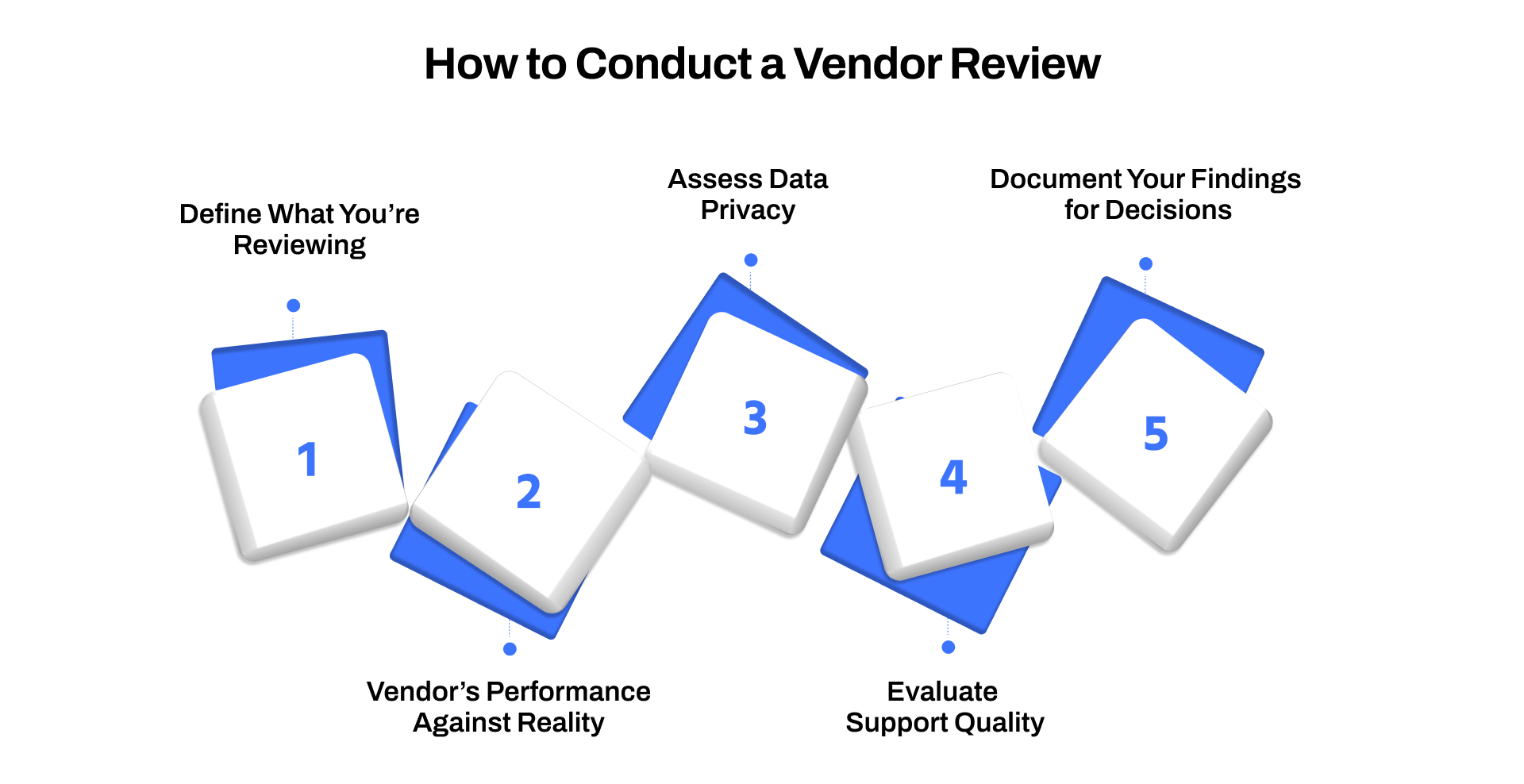
1. Define What You’re Reviewing and Why It Matters
Start by identifying the KPIs that directly affect your operational outcomes. Whether it’s service reliability, cost alignment, compliance, or delivery accuracy, tie every metric back to an actual business impact. Gather contracts, SLAs, pricing files, performance logs, and communication history.
This upfront clarity ensures your vendor review focuses on what moves the needle, not broad checklists.
2. Measure the Vendor’s Performance Against Reality
Look beyond promises. Track how the vendor performs in real conditions:
Uptime and availability data
Response times for incidents and queries
Feature delivery or project timelines
SLA adherence across quarters
Stability and reliability of the service
Patterns matter more than isolated failures. This assessment shows whether a vendor is improving, stagnating, or becoming a liability.
3. Assess Data Privacy and Security Posture
A strong vendor relationship must include strong protection of your data. Review:
Encryption standards
Access controls
Compliance readiness (GDPR, HIPAA, SOC 2, etc.)
Disaster recovery capability
Vulnerability and patch management practices
This step is crucial for minimizing third-party risk, especially when vendors have access to sensitive or regulated information.
4. Evaluate Support Quality and Responsiveness
Support isn't “nice to have”; it defines operational resilience. Examine:
Time to first response
Resolution efficiency
Escalation workflows
Quality and accuracy of guidance
Transparency during outages or delays
A vendor with excellent technology but poor support becomes a long-term burden.
A vendor with consistent, accountable support becomes an asset.
5. Document Your Findings for Decisions, Not Storage
Compile a structured report that highlights strengths, gaps, risks, and required actions. Share it internally and with the vendor.
This documentation ensures:
Accountability
Traceability across review cycles
Visibility for leadership
A clear roadmap for performance improvement
Documentation turns the vendor review from an annual exercise into an operational tool.
Organizations rarely struggle because they lack vendor data. They struggle because the data is scattered, uncontextualized, or reviewed too late to prevent financial or operational risks.
Auditive’s philosophy centers on visibility, continuity, and measurable accountability. In the same way Auditive helps teams detect operational deviations early, a precise vendor review helps you detect hidden inefficiencies, compliance gaps, and support failures long before they impact customers or revenue.
The purpose isn’t just to evaluate a vendor; it’s to strengthen your ability to run reliably, predict issues early, and make confident decisions backed by clean, verifiable insight.
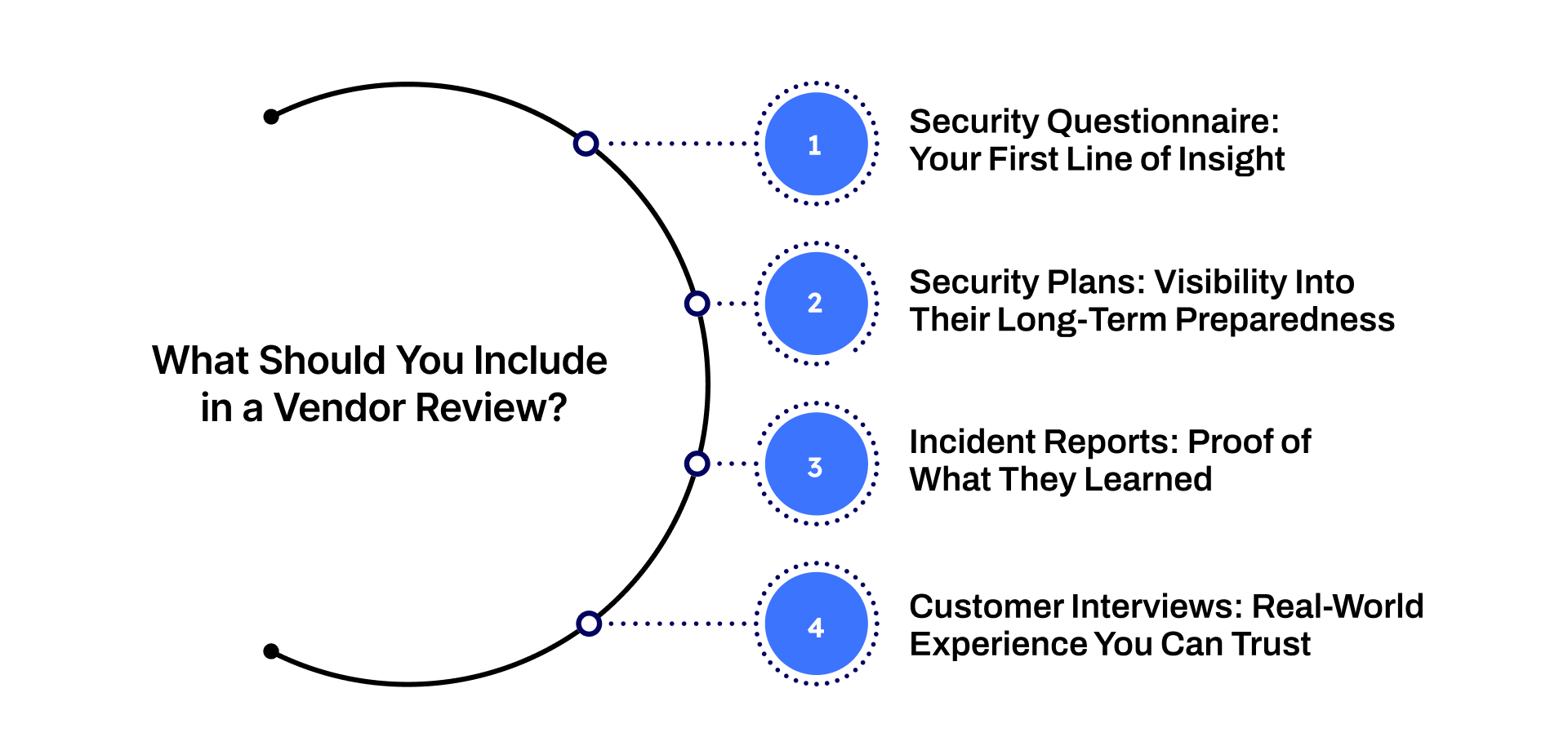
What Should You Include in a Vendor Review?
A clear breakdown of the essentials you must assess before trusting any external partner.
A vendor review isn’t just a checklist; it’s a deeper look into how a vendor protects your data, responds to incidents, and maintains security maturity. While criteria can shift depending on the type of vendor you’re evaluating, these core components remain critical for security, compliance, and risk prevention.
1. Security Questionnaire: Your First Line of Insight
Security questionnaires give you a structured way to uncover a vendor’s vulnerabilities, limitations, and overall security posture. These are often detailed spreadsheets covering how they store your data, what controls they enforce, and how they prevent breaches. A strong vendor should respond clearly, consistently, and without hesitation.
2. Security Plans: Visibility Into Their Long-Term Preparedness
A robust vendor review must include an assessment of the vendor’s security action plans. These documents outline current protocols, governance models, and long-term protection strategies. Reviewing their active security plans helps you confirm whether the vendor aligns with your internal standards and whether they’ve invested in more than just surface-level compliance.
3. Incident Reports: Proof of What They Learned
Even the biggest brands have faced breaches. What matters is how clearly a vendor documents the incident, what corrective actions they took, and whether those changes reduced the likelihood of recurrence. Incident reports give you factual, behavior-based evidence of how the vendor responds under pressure, far more valuable than polished sales claims.
4. Customer Interviews: Real-World Experience You Can Trust
Speaking with existing customers is one of the most reliable ways to validate a vendor’s security credibility. These conversations reveal how clients assessed the vendor, why they trusted their practices, and whether the vendor consistently delivers value. Customer interviews also help you understand day-to-day reliability, something paperwork alone can’t show.
Analyzing how modern teams assess vendors, based on real adoption patterns and evaluation behaviors from the Auditive audience.
Most teams today aren’t just looking for “secure enough.” They want vendors who can prove maturity, documented controls, transparent reporting, measurable response times, and real customer validation. This shift reflects a more data-driven buying process, where security depth matters as much as product capability.
A strong vendor review helps teams filter out vendors who only claim security from those who can demonstrate it with evidence.
How Auditive Gives You Continuous Clarity Into Vendor Security
Auditive makes vendor reviews faster, clearer, and continuously updated, removing the manual lag that slows most security teams.
Real-time risk monitoring: AuditiveX lets you start evaluating a vendor instantly, even before full onboarding, using live security signals and public data pulled into one profile.
Auto-updating vendor profiles: Certifications, incidents, policy updates, and documentation changes sync automatically so your team isn’t reviewing outdated information.
AI-assisted assessment: Auditive uses AI to read vendor documents, map controls to multiple frameworks, and surface gaps so analysts don’t spend hours on manual review.
Supports any framework: SOC 2, ISO 27001, NIST, or custom internal standards Auditive aligns vendor evidence to whichever controls you follow.
Integrated workflows: With 100+ integrations, risk updates, and tasks flow directly into your existing systems, keeping procurement, security, and legal aligned.
Auditive shifts vendor review from a periodic checklist to continuous, evidence-backed oversight so teams always evaluate vendors based on current security posture, not static documents.
Final Thoughts
Vendor reviews only work when they provide clarity, not more paperwork. The real value comes from understanding how a vendor operates, how they handle incidents, and whether their security practices hold up under real scrutiny. When done well, a vendor review becomes a decision-making tool, not an administrative burden. It helps teams reduce uncertainty, verify controls, and avoid risks that would otherwise go unnoticed until they become operational or security challenges.
Suppose you want to move from scattered documents and one-off evaluations to a continuous, accurate view of vendor health. In that case, Auditive gives you a real-time window into the signals that matter.
Schedule a demo to see how Auditive turns vendor assessments into a continuous, reliable process, backed by live data instead of assumptions.
FAQs
1. How often should a vendor review be conducted?
Most businesses reassess vendors annually, but high-risk vendors may require quarterly or ongoing monitoring to ensure controls haven’t degraded over time.
2. What makes a vendor review different from a basic vendor questionnaire?
A questionnaire only collects answers; a review evaluates the vendor’s actual performance, historical behavior, incident patterns, and alignment with your internal requirements.
3. Do all vendors require the same level of review?
No, vendors are evaluated based on risk tier. Those handling sensitive, regulated, or customer-facing systems generally require deeper assessments and more frequent follow-ups.
4. How important are customer interviews in a vendor review?
Customer insights provide real-world feedback on reliability, support responsiveness, and operational issues that may not appear in formal documentation.
5. Can a vendor review reduce long-term security risk?
Yes, effective reviews help identify weak controls early, track recurring issues, and ensure vendors maintain the standards your organization relies on throughout the partnership.