5 Powerful Strategies for Real-Time Risk Management and Monitoring
In financial services, healthcare, and education, where data sensitivity and regulatory compliance are top priorities, real-time risk management plays a pivotal role in safeguarding the organizations from potential financial losses, operational disruptions, and security breaches.
Real-time vendor risk management and monitoring allow businesses to continuously evaluate and adjust their risk exposure, making it possible to respond swiftly when issues arise.
In this article, we’ll explore what real-time vendor risk management and monitoring entail, their core components, market applications, challenges, best practices, and future developments in this growing space.
What is Real-Time Vendor Risk Management and Monitoring?
Real-time vendor risk management involves continuously assessing, monitoring, and mitigating risks from vendors by analyzing data on their activities, financial health, and compliance with agreements. It covers areas like financial stability, cybersecurity, regulatory compliance, and operational effectiveness.
By using automated systems and data analytics, businesses can detect potential threats early and take immediate action, making it more effective than periodic assessments. This approach is especially crucial in sectors like financial services, where compliance with regulations such as GDPR or HIPAA is mandatory to avoid severe penalties.
With Auditive’s Supply Chain Continuous Monitoring, you can track risk exposure across your entire supply chain in real-time, receiving instant updates about any incidents, from security breaches to vendor financial instability. This proactive monitoring helps you address risks swiftly before they impact your operations
Now, let's explore the essential components that make this process effective.
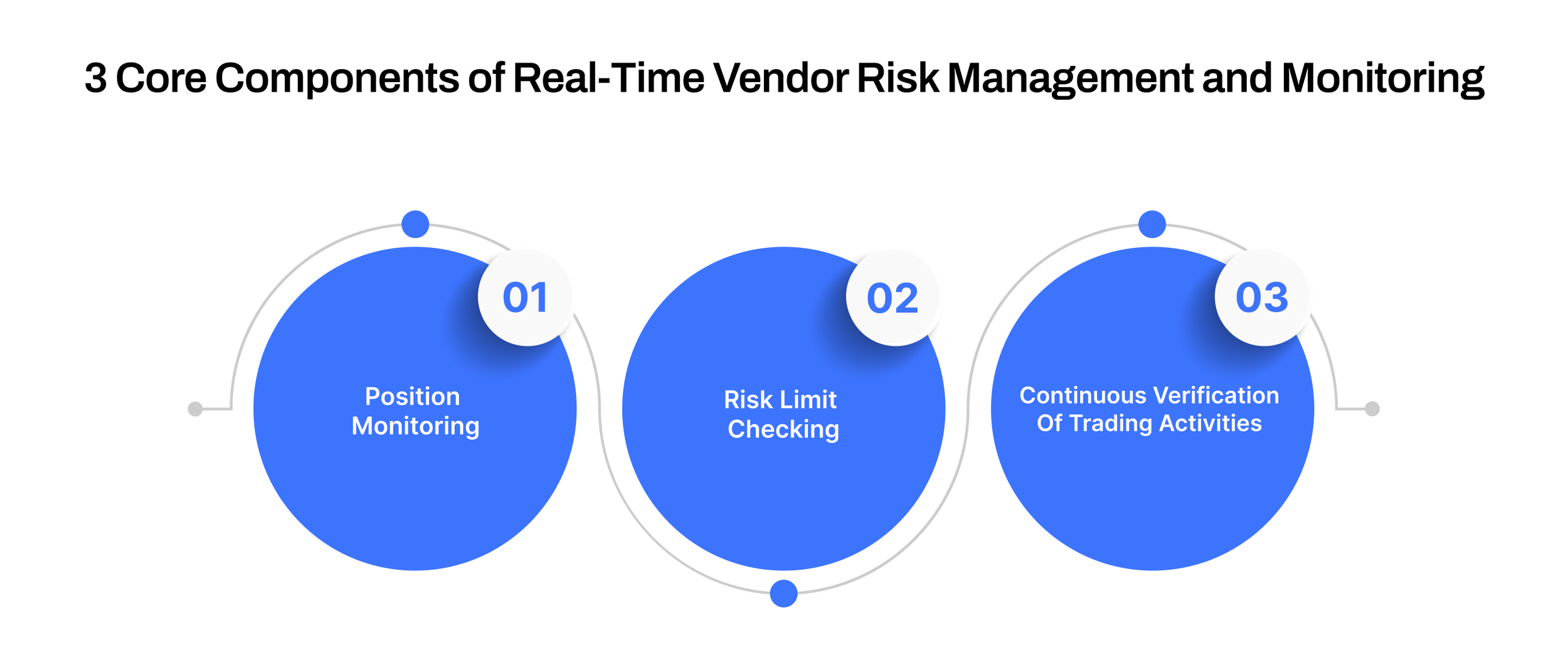
3 Core Components of Real-Time Vendor Risk Management and Monitoring
Effective real-time vendor risk management requires a clear understanding of key components that drive continuous monitoring and mitigation. These components ensure a comprehensive approach to managing vendor-related risks across all business operations.
1. Position Monitoring
Position monitoring tracks a business’s various positions with vendors, including inventory levels, financial commitments, and dependencies. In vendor risk management, continuous monitoring helps identify potential disruptions, such as a vendor’s inability to deliver key components on time, which could affect the business's ability to meet customer demand.
2. Risk Limit Checking
Risk limit checking involves defining the maximum acceptable exposure to specific risks, such as financial loss or operational disruptions, from each vendor. This ensures that the business does not overextend itself or become too reliant on a single vendor. Key risk limits include:
Position Limits: This refers to the maximum number of units or products a business is willing to have tied up in a vendor relationship at any given time.
Loss Limits: Loss limits define the maximum allowable financial loss that can be incurred from a vendor before actions must be taken to mitigate further risk.
Exposure Limits by Counterparty: Exposure limits track the level of financial risk associated with each vendor, based on their ability to meet contractual obligations.
3. Continuous Verification of Trading Activities
Real-time monitoring systems constantly verify vendor activities against predefined risk limits to ensure the organization does not exceed acceptable thresholds. These systems are built to track several key risk factors:
Position Limits: Verifies that no vendor relationship exceeds the predetermined position limits to avoid over-exposure.
Loss Limits: Checks if any losses caused by a vendor are approaching the defined thresholds.
Exposure Limits by Counterparty: Assesses if any individual vendor relationship exceeds the acceptable exposure level.
Value at Risk (VaR) Thresholds: This is a risk management tool used to estimate the maximum potential loss an organization could face due to its vendor relationships under normal market conditions.
Also Read: Applying Successful Risk Mitigation Strategies
Next, let’s look into how these strategies apply in real-world scenarios and industries.
3 Market Applications of Real-Time Vendor Risk Management and Monitoring
Real-time vendor risk management has broad applications across various markets, from trading systems to compliance frameworks. These applications help organizations maintain operational integrity and stay ahead of potential risks.
1. Trading System Risk Controls
In industries such as financial services, trading system risk controls are crucial. Real-time risk management enables automatic halts on trading activities if predetermined risk thresholds are breached, ensuring that any vendor-related issues are contained before they cause systemic problems.
Real-time risk assessment enables:
Automated Trading Halts When Limits Are Breached: If a vendor’s performance drops below an acceptable level, automatic actions are triggered to halt further engagement, preventing potential damage.
Dynamic Adjustment of Trading Parameters: In response to fluctuating risks, trading parameters can be adjusted dynamically, ensuring that the organization remains within its acceptable risk exposure levels.
Circuit Breaker Implementation: A risk management circuit breaker stops any activities that could result in significant losses, much like a financial market circuit breaker halts trading during extreme conditions.
Position Liquidation Triggers: If a vendor’s risk exceeds acceptable limits, position liquidation triggers can be initiated to reduce exposure and prevent further losses.
2. Regulatory Compliance
Real-time risk management also helps ensure that an organization remains compliant with industry regulations. Automated systems monitor the following compliance aspects:
Capital Adequacy Requirements: Ensures that the organization holds sufficient capital reserves when engaging with vendors, particularly in financial services.
Position Reporting Obligations: Tracks vendor position levels to meet reporting requirements set by regulatory bodies.
Risk Exposure Limits: Monitors and maintains exposure within regulatory limits to prevent financial instability.
Trading Conduct Rules: Ensures vendors adhere to established conduct rules, reducing the risk of non-compliance.
3. Risk Reporting
Real-time risk management provides valuable risk reporting, which generates:
Risk Dashboards for Traders: Displays real-time risk data to help traders make informed decisions.
Alerts for Limit Breaches: Provides immediate alerts when a vendor exceeds predefined risk limits, allowing for quick intervention.
Regulatory Reports: Generates necessary reports to meet regulatory obligations, ensuring ongoing compliance.
Management Information: Provides actionable insights to senior management, ensuring they have the data to make strategic decisions.
Also Read: The Importance of Continuous Monitoring in Risk Management
As you implement real-time strategies, it's important to be aware of the challenges that come with them.
8 Challenges in Real-Time Vendor Risk Management and Monitoring
Despite its effectiveness, real-time vendor risk management comes with its own set of challenges. Here are some of the key issues businesses face when implementing real-time monitoring systems:
1. High Volume and Velocity of Data
Real-time risk management systems must process vast amounts of data quickly to ensure timely risk assessments. The high volume and velocity of data can overwhelm traditional systems, making it difficult to spot potential risks in a timely manner.
2. Complexity of Financial Instruments
Financial products and services are becoming increasingly complex. For example, in financial services, derivatives and structured products add layers of complexity when assessing vendor risks. Tracking these risks in real-time requires sophisticated systems and advanced algorithms.
3. Regulatory Compliance
Keeping up with changing regulations across industries like healthcare, education, and financial services can be a challenge. Compliance requirements vary by region and sector, necessitating constant updates to risk management systems.
4. Market Volatility
Market conditions can change quickly, often rendering risk assessments outdated. Real-time risk management allows businesses to respond dynamically, but accurately forecasting volatility remains a challenge.
Also Read: AI in Supply Chain Risk Management Strategies
5. Cybersecurity Threats
Vendors’ cybersecurity postures are constantly changing. Real-time monitoring must account for new threats, vulnerabilities, and attacks targeting vendors’ systems, as seen with the SolarWinds breach.
6. Global and 24/7 Operations
Managing risk in a 24/7 environment requires systems that can monitor and respond to risks at any time, across different time zones.
7. Latency in Large Dataset Processing
Handling vast datasets in real-time can introduce latency issues. Even small delays can compromise the effectiveness of real-time risk monitoring, leaving the organization vulnerable.
8. Handling High-Speed Data and System Integration
Integrating real-time monitoring systems with existing enterprise software can be difficult, particularly when dealing with high-speed data streams and ensuring system compatibility.
As part of your real-time risk management strategy, Auditive’s Accelerated Intake Form automates your vendor onboarding process, giving you immediate insight into a vendor’s inherent risks. By quickly categorizing and assessing new vendors, you can ensure that every third-party partner meets your security standards and compliance requirements from the very beginning.
Knowing the challenges allows businesses to implement best practices, improving effectiveness and reducing risk exposure.
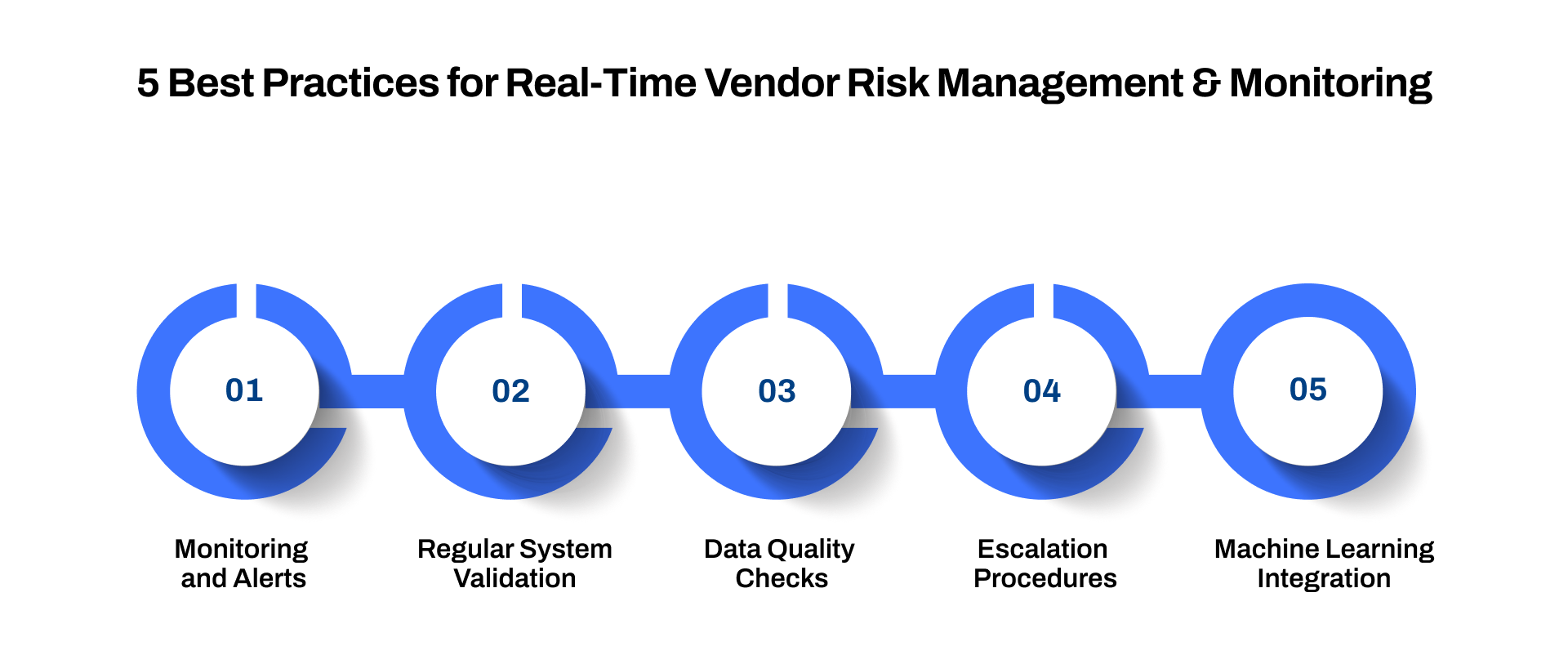
5 Best Practices for Real-Time Vendor Risk Management and Monitoring
To get the most out of your real-time risk management systems, here are some best practices:
1. Monitoring and Alerts
Real-time monitoring is only effective if alert thresholds are set clearly. Alerts should be tailored to each vendor’s risk profile and include multiple notification channels, such as email, SMS, or direct system alerts.
2. Regular System Validation
Ensuring your risk management system’s reliability is crucial. Regular backtesting, stress testing, and performance monitoring of risk models will ensure your system’s readiness to handle emerging risks.
3. Data Quality Checks
Ensuring data integrity is paramount. Implement routine data quality checks to verify the accuracy and completeness of the data feeding into your real-time risk monitoring system.
4. Escalation Procedures
When a threshold is breached, there should be a predefined escalation process. Ensure that key stakeholders are notified and action is taken quickly to mitigate any further risk.
5. Machine Learning Integration
Machine learning can enhance real-time risk monitoring by identifying hidden patterns and predicting potential risks based on historical data. This provides an additional layer of intelligence to your risk management strategy.
Also Read: Step-by-Step Guide to Continuous Vendor Risk Assessment
Next, let's look at the future developments shaping the industry.
Future Developments in Real-Time Vendor Risk Management and Monitoring
Real-time risk management continues to develop with advancements in technology. The future of this space includes:
Advanced Analytics Capabilities: Real-time monitoring will incorporate more sophisticated data analytics tools, improving decision-making and risk prediction.
Improved Visualization Tools: Enhanced dashboards and visualization tools will allow risk managers to better understand and communicate risk data.
Enhanced Predictive Capabilities: The use of AI to predict future risks based on historical data will help businesses stay one step ahead of potential disruptions.
Also Read: Supply Chain Risk Management Strategies and Examples
To make the most of these advancements, it’s time to use the right tools for comprehensive vendor risk management.
Take Control of Real-Time Vendor Risk Management with Auditive
With Auditive, you can stay ahead of potential threats by using real-time risk monitoring to ensure your vendors meet the highest security standards. If you're faced with the complexities of vendor risk management or ensuring your third-party partnerships remain secure, Auditive’s platform offers the tools you need to manage risks with confidence.
Here’s how Auditive transforms your real-time vendor risk management strategy:
Contract Monitor: Auditive’s Contract Monitor ensures vendor adherence to contracts by extracting key contract information in seconds, automating renewal reminders, and flagging any deviations from regulatory standards or missed SLAs.
Partner Trust Exchange: With Partner Trust Exchange, Auditive connects you to a dynamic network of suppliers, providing real-time risk-relevant data. Vendors create Trust Profiles that are tailored for your needs, ensuring transparency and streamlining vendor reviews.
Accelerated Intake Form: The Accelerated Intake Form automates third-party intake, providing immediate awareness of a supplier’s inherent risk. Using AI, it categorizes vendors and provides instant risk measurement, ensuring faster and more informed decisions.
Questionnaire Copilot: Questionnaire Copilot uses AI to complete over 80% of RFP and risk questionnaires with high accuracy, automatically integrating data from your systems and streamlining vendor assessment processes with minimal manual effort.
Supplier Risk Assessment Agent: Auditive’s Supplier Risk Assessment Agent delivers faster risk assessments by using AI to analyze third-party documentation and provide actionable insights, helping you understand the true risk exposure.
Supply Chain Continuous Monitoring: Supply Chain Continuous Monitoring allows you to track your risk exposure in real time, receiving instant updates and notifications of any incidents affecting your vendors or their suppliers.
See how PayNearMe improved its security information sharing process with Auditive, making them stand out as a modern, professional organization; check out the full case study.
With these Auditive features, you gain the ability to monitor vendor risks continuously, validate security practices in real time, and ensure your business remains resilient and compliant.
Conclusion
With continuous monitoring and risk assessment, businesses can identify threats early, comply with regulations, and ensure operational stability. Integrating these strategies can ensure more resilient, secure supply chains, safeguarding their operations from unforeseen disruptions.
For effective real-time risk management, combining Contract Monitor and Supplier Risk Assessment Agent by Auditive ensures that your vendors remain compliant throughout their contract lifecycle. Monitor contract changes, deviations, and missed SLAs in real time, while leveraging AI-powered risk assessments to quickly identify and address risks.
Contact Auditive and stay ahead of potential disruptions while maintaining full visibility into your entire supply chain.
FAQs
1. How can real-time vendor risk monitoring prevent financial losses due to vendor defaults?
By continuously tracking financial stability and operational performance, real-time monitoring helps identify risks early, allowing businesses to take corrective actions before losses occur.
2. What role does AI play in verifying vendor security profiles for financial service companies?
AI ensures the accuracy of vendor security claims by analyzing data from multiple sources, providing real-time insights into vulnerabilities that could threaten compliance or security.
3. How to handle compliance monitoring for vendors across multiple jurisdictions?
For real-time notifications of compliance violations across several jurisdictions, you can monitor vendors' adherence to rules like GDPR, HIPAA, and local data protection laws.
4. How do real-time risk assessments help in managing cybersecurity risks from third-party vendors?
Real-time assessments continuously monitor cybersecurity practices, detecting vulnerabilities or security breaches immediately, which helps mitigate potential cyber threats and maintain data integrity.
5. Can real-time monitoring tools detect supply chain disruptions before they affect business operations?
Yes, by tracking key performance indicators (KPIs) like delivery timelines and financial stability, real-time monitoring alerts you to potential disruptions before they impact operations.