Step-by-Step Guide to Continuous Vendor Risk Assessment
Only 13% of organizations actively and continuously monitor their third-party vendor security risks. That means the majority still rely on periodic reviews, leaving blind spots that attackers can exploit. In spaces where vendors have deep access to sensitive data and critical systems, this approach simply isn’t enough.
Continuous vendor risk assessment offers a smarter, more proactive alternative. Instead of treating vendor reviews as one-off events, it turns them into an ongoing process, identifying new risks in real time, strengthening compliance, and ensuring business resilience.
This guide walks you through the step-by-step process of building a continuous vendor risk assessment framework.
Quick Glance:
Continuous vendor risk assessment ensures ongoing visibility into third-party risks.
Strong vendor risk management enhances compliance, trust, and operational resilience.
Automation and real-time monitoring reduce manual effort and risk blind spots.
A Trust Center centralizes vendor data, compliance certifications, and risk scores.
Auditive enables faster onboarding, better collaboration, and continuous oversight.
What does "Vendor Risk Assessment" mean?
A vendor risk assessment (VRA) is the structured process of identifying and managing potential risks caused by third-party vendors, including threats to data security, regulatory compliance, and business continuity. It helps organizations determine whether a vendor can be trusted with sensitive systems and information.
Through this process, businesses:
Identify risks across data, operations, and compliance.
Evaluate vendors against consistent security and performance criteria.
Ensure alignment with frameworks like GDPR, HIPAA, ISO 27001, and SOC 2.
Reduce exposure to cyber threats and supply chain disruptions.
With organizations increasingly dependent on third-party providers, the stakes are higher than ever. According to Gartner, 60% of companies now work with over 1,000 vendors, making vendor risk oversight a core business necessity rather than an optional safeguard.
Modern vendor risk assessments go beyond compliance checklists; they integrate continuous monitoring, data-driven scoring, and even AI-powered risk intelligence to keep up with evolving threats. When done effectively, a VRA not only ensures compliance but also strengthens resilience, transparency, and trust across the entire vendor ecosystem.
Why Continuous Vendor Risk Assessment Matters
As businesses expand their digital ecosystems, their exposure to third-party risks grows exponentially. Every vendor, whether managing cloud infrastructure, payments, or customer data, can become a potential weak link. A single vulnerability can disrupt operations, compromise sensitive information, and damage customer trust.
Consider the 2024 ransomware attack on UnitedHealth Group, which crippled healthcare payment processing across the U.S. and pushed medical offices to the brink of insolvency. Such incidents highlight that vendor risk isn’t isolated, it’s enterprise risk.
A continuous vendor risk assessment approach helps organizations:
Strengthen cybersecurity by detecting and addressing vulnerabilities before exploitation.
Maintain compliance with frameworks like GDPR, HIPAA, and PCI DSS.
Reduce financial exposure from potential breaches, penalties, and downtime.
Safeguard operations by ensuring critical vendor services remain resilient.
Build trusted partnerships through transparency and proactive communication.
In essence, continuous vendor risk assessment transforms third-party oversight from a periodic compliance activity into an ongoing strategy for resilience, trust, and business continuity.
How to Conduct an Effective Vendor Risk Assessment
Performing a thorough vendor risk assessment is a critical step before engaging any third-party vendor. This process helps you evaluate potential risks and establish a clear decision-making framework. Below are five key steps, enhanced for clarity and depth, to guide your approach.
Step 1: Map the Risk Landscape
Start by identifying the various risk types vendors can introduce. Common categories include:
Cybersecurity risks – Weak vendor controls may expose your systems to breaches or data leaks.
Compliance and regulatory risks – A vendor who fails to follow laws or standards could trigger penalties for your organization.
Reputational risks – Vendors with poor security, ethical issues, or unstable performance can damage your brand by association.
Strategic risks – If a vendor’s goals are misaligned with yours, it may hinder your growth or competitive edge.
Operational/business-continuity risks – Vendor failures, delays or disruptions can directly impact your operations.
Understanding these risk types upfront ensures you evaluate each vendor from a comprehensive perspective.
Also read: Guide to Effective Reputation Risk Management and Mitigation
Step 2: Create a Vendor Risk Questionnaire
Gather detailed insights by asking vendors for structured information. Include questions covering:
Data access and protection measures
Compliance certifications and audit results
Financial stability and business continuity plans
Third-party subcontractor relationships
Incident history and remediation practices
A well-designed questionnaire transforms vague vendor evaluations into measurable data, enabling you to make better decisions.
Step 3: Analyze Each Vendor’s Risk Profile
Once you collect vendor responses and supporting documents, dig deeper by assessing:
Their security architecture and access controls
Any identified incidents or vulnerabilities
Financial health and market reputation
Contractual obligations and termination practices
Regulatory or industry-specific compliance gaps
This analysis converts raw data into actionable insights, spotlighting vendors whose performance or practices may expose you to risk.
Step 4: Categorize Vendors by Risk Level
Not every vendor demands the same level of oversight. Use your analysis to:
Score each vendor based on access, sensitivity, and business-criticality
Assign vendors into tiers (e.g., High, Medium, Low risk) to prioritize assessment and monitoring efforts
Adjust due-diligence depth, monitoring frequency, and contract terms according to the risk tier
By categorizing intelligently, you focus resources where they matter most, reducing oversight fatigue and improving effectiveness.
Step 5: Develop and Implement Mitigation Strategies
With a clear vendor-risk map, you can define targeted controls. Consider actions such as:
Security and compliance clauses in contracts
Defined KPIs and SLAs tied to vendor performance
On-site or remote audits, penetration testing, or data-access reviews
Exit and transition plans for high-risk vendors
Automated tools and dashboards for ongoing monitoring and alerts
This strategic approach ensures your vendor relationships are not only evaluated once but actively managed throughout the lifecycle.
Manual vendor assessments consume time and create blind spots. In order to help you transition from static assessment to continuous insight, Auditive was designed to optimize your vendor risk workflows by combining real-time monitoring and risk scoring.
With Auditive, you can stay ahead of third-party risks and build a proactive, trusted vendor ecosystem.
Proven Strategies to Strengthen Your Vendor Risk Assessment
Building a mature and resilient vendor risk management (VRM) program requires more than routine audits, it demands structure, consistency, and proactive oversight. To ensure your third-party ecosystem remains secure and compliant, here are some proven best practices to follow:
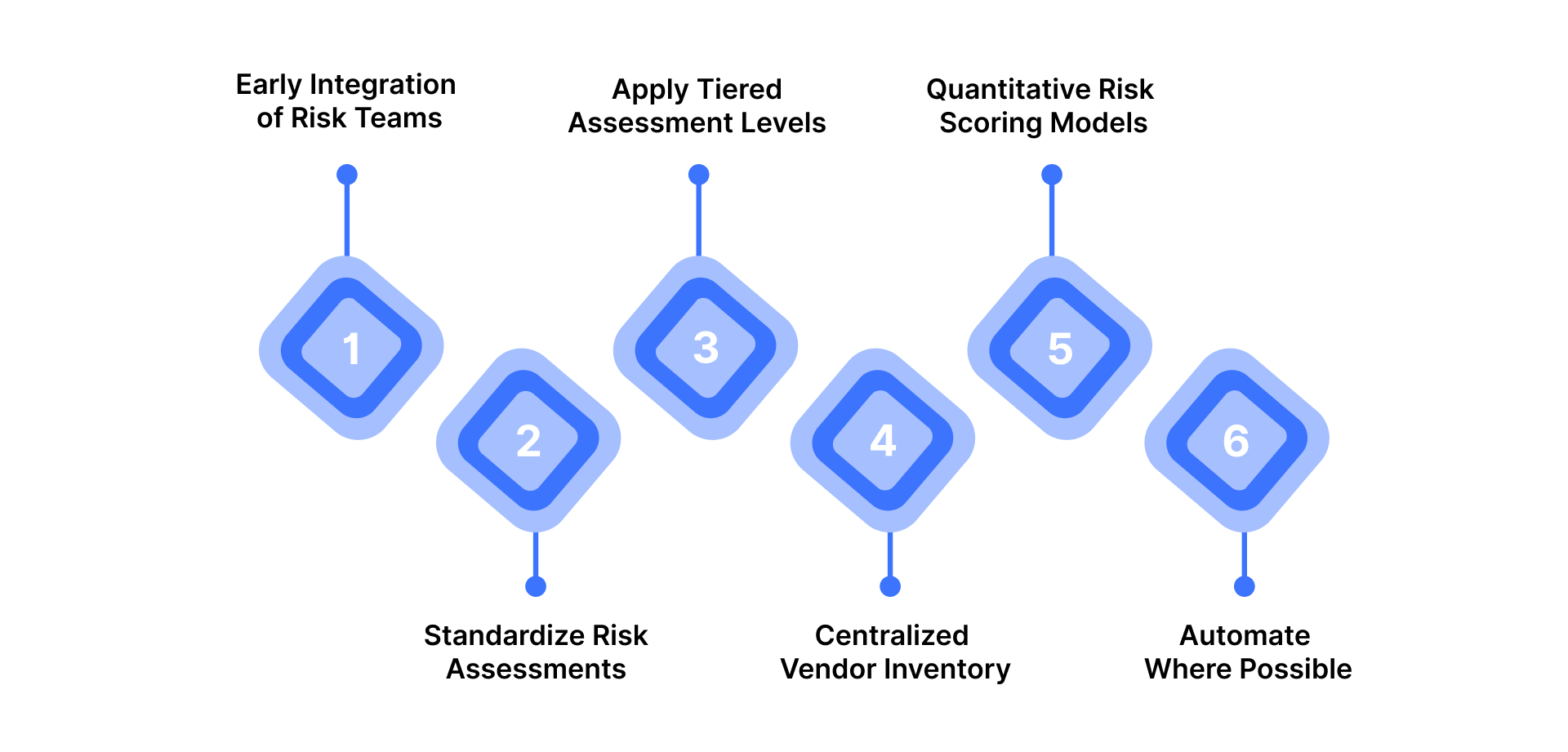
1. Early integration of risk teams
Bring procurement, legal, and risk management together right from the vendor selection stage. This collaboration ensures that security and compliance considerations are built into contracts, reducing exposure before onboarding begins.
2. Standardize Risk Assessments
Adopt industry-standard questionnaires like CAIQ (Cloud Security Alliance) or SIG (Standardized Information Gathering). These frameworks promote uniformity, making it easier to benchmark vendor controls and scale your assessment process.
3. Apply Tiered Assessment Levels
Not every vendor poses the same level of risk. Use a tiered approach, subjecting high-risk or critical vendors to deeper due diligence while applying lighter assessments to low-impact ones. This optimizes resources without compromising oversight.
4. Maintain a Centralized Vendor Inventory
Keep a single source of truth that lists all vendors, their services, data access levels, and risk scores. A well-maintained inventory supports transparency and simplifies audits or compliance reviews.
5. Use Quantitative Risk Scoring Models
Translate qualitative findings into measurable risk scores. Quantifying risk enables easy comparison, trend analysis, and more informed decision-making when prioritizing mitigation efforts.
6. Automate Where Possible
Using modern GRC or VRM tools to streamline repetitive tasks like questionnaire distribution, evidence collection, and follow-ups. Automation enhances accuracy, consistency, and overall program efficiency.
Implementing these best practices is far more effective when supported by intelligent automation and real-time insights. Auditive can help with that by enabling organizations to simplify vendor oversight, quantify risk exposure, and maintain compliance through continuous monitoring and data-driven transparency.
How Auditive Solves Your Vendor Risk Challenges
Managing third-party vendor relationships across procurement, security, and legal functions often feels like juggling multiple disconnected systems. Disparate data, manual reviews, and slow onboarding can leave critical risks hidden. Auditive addresses these issues head-on:
Unlock one unified hub, Auditive places “all vendors at your fingertips”, letting organizations continuously monitor their full vendor ecosystem in a single platform.
Accelerate onboarding and engagement, With statistics like “4× faster onboarding” and elimination of up to “80% of risk-review work” for both buyers and vendors, Auditive converts tedious processes into streamlined experiences.
Embed risk management into existing workflows, Seamless integration with procurement, security, and productivity tools means no more dual-entries or fragmented vendor data across platforms.
Continuous visibility, not point-in-time checks, Through continuous monitoring and a live network exchange, Auditive keeps vendor risk posture visible and actionable at all times.
For CISOs and security teams in Finance, Healthcare, EdTech, Because many of these industries face high vendor-related risk (e.g., PHI handling, financial data), Auditive’s proactive vendor risk management and Trust Center offerings are tailored to meet these high-stakes needs across countries
If your vendor risk program is struggling with slow reviews, limited transparent insight, or siloed workflow hand-offs, Auditive turns that problem into a strategic advantage.
Learn more about: How to Prevent Data Breaches in Healthcare
Turning Continuous Vendor Risk into a Competitive Advantage
Continuous vendor risk assessment isn’t just another compliance task; it’s the foundation of strong vendor risk management. In industries like healthcare, finance, and education, where even a single third-party failure can compromise trust and compliance, proactive oversight is non-negotiable. The ability to continuously evaluate, score, and respond to vendor risks in real time separates resilient organizations from vulnerable ones.
That’s where Auditive stands out. By combining automation, continuous monitoring, and an integrated Trust Center, Auditive empowers teams to move from reactive assessments to proactive risk intelligence. Instead of scrambling to identify vulnerabilities, you gain full visibility across your vendor ecosystem, all in one intuitive platform.
Book a personalized demo with Auditive to simplify vendor oversight and strengthen your risk posture, without slowing down your operations.
FAQs
1. What is continuous vendor risk assessment?
Continuous vendor risk assessment involves the ongoing evaluation of third-party vendors to detect changes in their risk posture, compliance status, or security performance, ensuring consistent oversight rather than one-time reviews.
2. Why is continuous monitoring important for vendor risk management?
Because vendor risks evolve constantly, continuous monitoring allows organizations to identify emerging threats early, respond proactively, and prevent costly disruptions.
3. How does a Trust Center improve vendor oversight?
A Trust Center provides a central hub for viewing vendor compliance documents, certifications, and risk metrics, giving teams real-time visibility and confidence in vendor relationships.
4. What challenges does automation solve in vendor risk management?
Automation eliminates repetitive manual tasks such as questionnaire reviews and document tracking, allowing teams to focus on high-impact risk analysis and faster decision-making.
5. How does Auditive support continuous vendor risk management?
Auditive integrates with procurement and security workflows, automates monitoring and reporting, and delivers actionable insights through its Trust Center, making vendor risk management more transparent, efficient, and proactive.