Top Vendor Security and Privacy Assessment Software for 2025
Third-party vendors play a vital role in driving growth, but they also expand an organization’s attack surface. About 29% of all data breaches are caused by third-party vendors; selecting the best vendor security and privacy assessment software has become a strategic priority rather than a technical choice.
Good tools in this space go beyond basic questionnaires or periodic checks; they offer continuous visibility into vendor risks, automate assessments, and help teams detect threats before they escalate. They provide clarity where manual tracking fails, allowing CISOs and security teams to manage complex vendor ecosystems with confidence and precision.
This guide highlights how the right software can transform your vendor oversight, improving risk transparency, operational efficiency, and decision-making at every stage of the vendor relationship.
Key takeaways:
Vendor ecosystems introduce operational and data risks that demand continuous oversight.
Strong vendor risk management programs combine automation, visibility, and measurable outcomes.
A Trust Center centralizes all vendor data and evidence for easier tracking and faster action.
Auditive empowers teams with real-time insights, streamlined onboarding, and integrated workflows.
Choosing the right solution ensures a scalable and resilient third-party security posture.
What Is Vendor Security and Privacy Assessment Software?
A vendor security and privacy assessment software is a digital platform designed to evaluate, monitor, and manage the security posture and data-handling practices of third-party vendors. Only 32% of organizations maintain a full inventory of third-party vendors sharing sensitive data. It helps organizations ensure that external partners do not expose them to cyber or data-privacy risks.
In simple terms, vendor security and privacy assessment software acts as your extended security radar by identifying weak links, validating vendor safeguards, and ensuring external partners uphold the same security and privacy standards as your internal systems.
How Vendor Risk Management Software Actually Works
Understanding how vendor risk management (VRM) software operates is key to evaluating the best vendor security and privacy assessment software for your organization. Instead of relying on spreadsheets and manual tracking, VRM platforms automate every stage of the vendor lifecycle, from onboarding to offboarding, while providing real-time visibility into vendor security performance.
At its core, VRM software acts as a centralized control system where CISOs and security teams can:
Run risk assessments to identify vulnerabilities across active vendor relationships.
Track remediation progress for ongoing vendor risks and security incidents.
Prioritize vendors based on their security posture and criticality to operations.
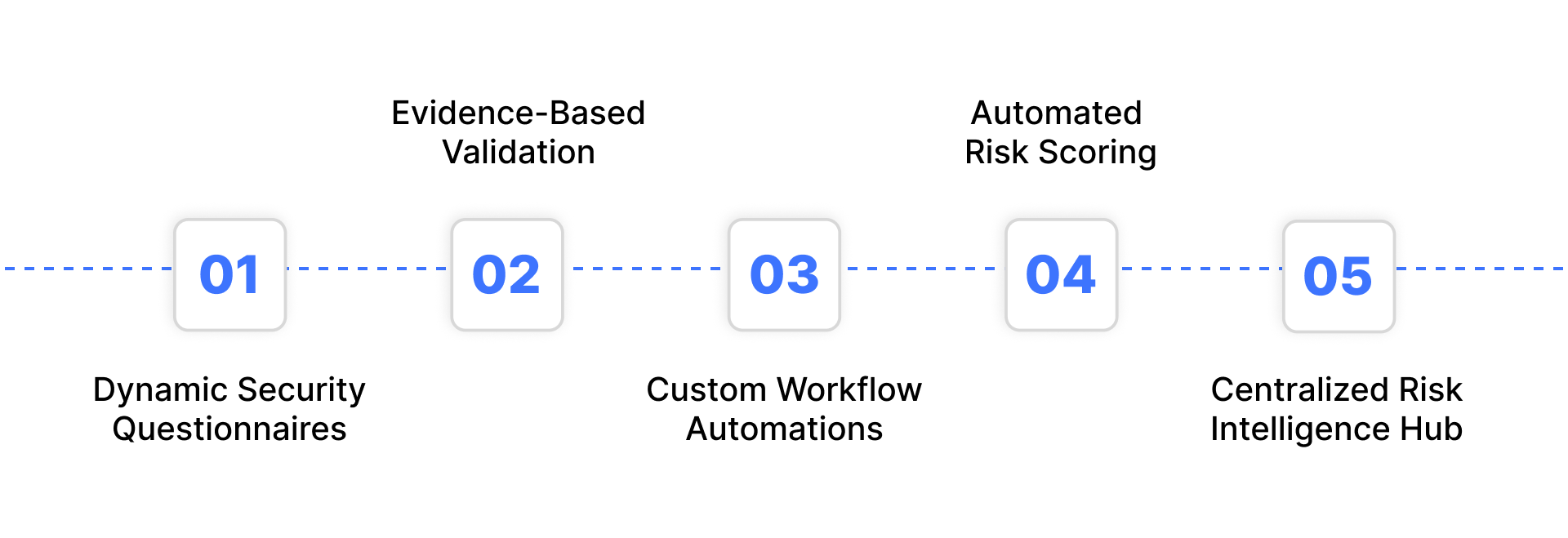
Here’s a closer look at how it drives continuous vendor oversight:
Dynamic Security Questionnaires
Build or tailor questionnaires to assess how a vendor manages data security, financial integrity, and operational resilience. Responses are stored and compared automatically for faster decision-making.
Evidence-Based Validation
Upload, verify, and review supporting documentation such as audit reports, security certifications, and incident summaries, helping teams validate every vendor’s security claims with tangible proof.
Custom Workflow Automations
Configure workflows for assessments, document reviews, and escalation paths. This streamlines repetitive tasks and ensures your security team focuses on higher-priority risk analysis.
Automated Risk Scoring
The system continuously evaluates vendors using real-world cybersecurity metrics, such as network defense maturity, phishing susceptibility, and breach history, producing adaptive risk scores that reflect ongoing changes in vendor posture.
Centralized Risk Intelligence Hub
A unified data repository keeps every department aligned, reducing fragmented communication and improving traceability across vendor interactions.
Essentially, VRM software transforms vendor management from a periodic exercise into a continuous, data-driven process, allowing security leaders to detect risks early and respond faster.
Top Vendor Security and Privacy Assessment Software for 2025
Choosing the best vendor security and privacy assessment software can define how effectively your organization identifies, monitors, and mitigates third-party risks. With growing dependencies on external vendors, enterprises need tools that provide real-time visibility, continuous monitoring, and actionable intelligence, not just static reports.
Here are the leading platforms trusted by security leaders in 2025.
1. Auditive – Transforming Continuous Vendor Risk Oversight
Auditive redefines vendor risk management with a single, intelligent platform that centralizes all vendor data, automates security assessments, and builds digital trust across your network.
Key Strengths:
Continuous vendor risk assessment through real-time monitoring and dynamic updates.
Trust Center for assessing, tracking, and sharing vendor security posture transparently.
Automated risk workflows that align security, procurement, and legal teams effortlessly.
Faster onboarding with integrated workflows, reducing time from weeks to days.
Auditive empowers you to move from static assessments to proactive, continuous assurance, ensuring complete visibility into vendor performance and reducing the operational burden of manual reviews.
Learn more about: Risk Management: Critical Steps for Business Success
2. Scrut – Automated Monitoring for Multi-Cloud Environments
Scrut streamlines vendor oversight by automating the evidence collection and tracking process across diverse cloud infrastructures. Its adaptive dashboard delivers real-time updates to keep your vendor security status transparent and measurable.
Key Strengths:
Automated monitoring of vendor security controls.
Unified dashboard for ISO 27001, SOC 2, GDPR, PCI DSS, and more.
Custom reports for performance tracking and vendor benchmarking.
Multi-cloud and hybrid environment support for comprehensive visibility.
Customer Rating:
G2: 4.9/5
3. RFP360 – Streamlined Vendor Risk Assessments and Collaboration
RFP360 brings simplicity to vendor evaluations with a central workspace for RFx processes. It helps security teams automate questionnaires, analyze proposals, and measure risk through standardized scoring models.
Key Strengths:
Digital platform for RFI, RFP, and vendor risk assessments.
Built-in templates and import options for risk questionnaires.
Real-time collaboration between security, procurement, and IT teams.
Consolidated reports offering a unified view of vendor performance.
Customer Rating:
G2: 4.4/5 | Capterra: 4.4/5
4. Loopio – Accelerating Vendor Evaluation Through Automation
Loopio helps organizations accelerate their vendor assessment workflows by automating responses to RFPs, RFIs, and security questionnaires. It ensures that security teams can evaluate vendors faster without compromising accuracy.
Key Strengths:
Centralized repository for RFP and security questionnaire content.
Automation for repetitive responses, saving hours of manual work.
Built-in collaboration tools for security and procurement teams.
Enhanced visibility into vendor readiness and risk posture.
Customer Rating:
G2: 4.7/5 | Capterra: 4.6/5
5. Drata – Real-Time Vendor Security Monitoring
Drata’s platform delivers continuous monitoring and automated evidence collection to keep your vendor ecosystem secure and audit-ready. It integrates with popular SaaS and infrastructure tools to ensure full transparency into vendor controls.
Key Strengths:
Real-time vendor security tracking across frameworks like SOC 2 and HIPAA.
Automated control verification and alerts for anomalies.
Single dashboard for managing multiple vendor connections.
Pre-built integrations for scalability across global vendor networks.
Customer Rating:
G2: 4.9/5 | Capterra: 5/5
6. OneTrust – Unified Risk Intelligence for Vendors
OneTrust provides organizations with deep visibility into vendor ecosystems through its data governance platform. It identifies hidden risks, quantifies exposure, and enables informed decision-making for vendor onboarding.
Key Strengths:
Comprehensive view of vendor risk across data and infrastructure layers.
Risk heat maps for faster prioritization and mitigation.
Integrated modules for vendor management and security assessments.
Advanced analytics for predicting emerging vendor threats.
Customer Rating:
G2: 4.3/5
7. Ncontracts – Real-Time Vendor Risk Monitoring
Ncontracts focuses on real-time vendor intelligence by monitoring cybersecurity, financial health, and continuity metrics. It allows organizations to take preemptive action before risks escalate.
Key Strengths:
Automated tracking of vendor financial and operational health.
Risk scoring across cybersecurity, continuity, and legal parameters.
Centralized repository for documentation and performance history.
Predictive insights to flag potential vendor failures or disruptions.
Customer Rating:
G2: 4.6/5 | Capterra: 4.8/5
8. Whistic – Fast and Transparent Vendor Evaluations
Whistic simplifies vendor vetting by giving you access to verified security documentation and certifications through shared vendor profiles. It helps reduce evaluation time while maintaining control over data access.
Key Strengths:
Shared vendor profiles with pre-verified security documents.
Custom access controls and expiration settings for data sharing.
Built-in audit trails for accountability and traceability.
Instant alerts for changes in vendor security posture.
Customer Rating:
G2: 4.8/5
9. Vanta – Automated Security Tracking and Evidence Collection
Vanta enhances vendor risk visibility by automating data collection and validation. Its integration ecosystem connects directly with identity providers and cloud services to track controls in real-time.
Key Strengths:
Continuous evidence gathering for vendor performance tracking.
Integration with major SaaS and infrastructure tools.
Vendor benchmarking to compare risk levels across partners.
Intuitive dashboard for risk prioritization and reporting.
Customer Rating:
G2: 4.7/5 | Capterra: 4.9/5
10. Tugboat Logic – Simplified Vendor Risk Evaluation
Tugboat Logic brings clarity to vendor assessment by allowing direct comparison of vendor responses to predefined security criteria. It helps organizations select the most secure vendors quickly.
Key Strengths:
Security questionnaire templates for faster evaluations.
Vendor comparison features to identify low-risk partners.
Document repository for storing verified vendor responses.
Easy evidence mapping for internal audits.
Customer Rating:
G2: 4.6/5
11. UpGuard – Proactive Risk Insights and Performance Tracking
UpGuard delivers real-time insights into vendor security health, scanning across multiple domains to detect potential weaknesses before they impact your organization.
Key Strengths:
Continuous monitoring across email, network, and website layers.
Pre-built assessment tools to speed up vendor reviews.
Categorized risk insights, including phishing, malware, and reputation.
Visual risk dashboard for instant visibility and decision-making.
Customer Rating:
G2: 4.4/5 | Capterra: 5/5
In 2025, vendor security and privacy assessment software isn’t just about managing risk, it’s about building digital trust at scale. The right platform doesn’t just track vulnerabilities; it empowers your organization to make faster, smarter, and more confident decisions about who you do business with.
Must Read: How to Conduct a Comprehensive Security Risk Assessment?
Selecting the Right Platform to Support Your Third-Party Security Policy
When your corporate operations depend on external vendors for data, services, and technology, you're also inheriting their risks. A misstep by a third-party can undermine your data protection strategy, disrupt essential workflows, and compromise stakeholder trust. That’s why choosing the right solution for your third-party security policy is not just helpful, it’s imperative.
A tool worth deploying must do more than track vendors; it must help transform vendor risk into a manageable component of your security posture.
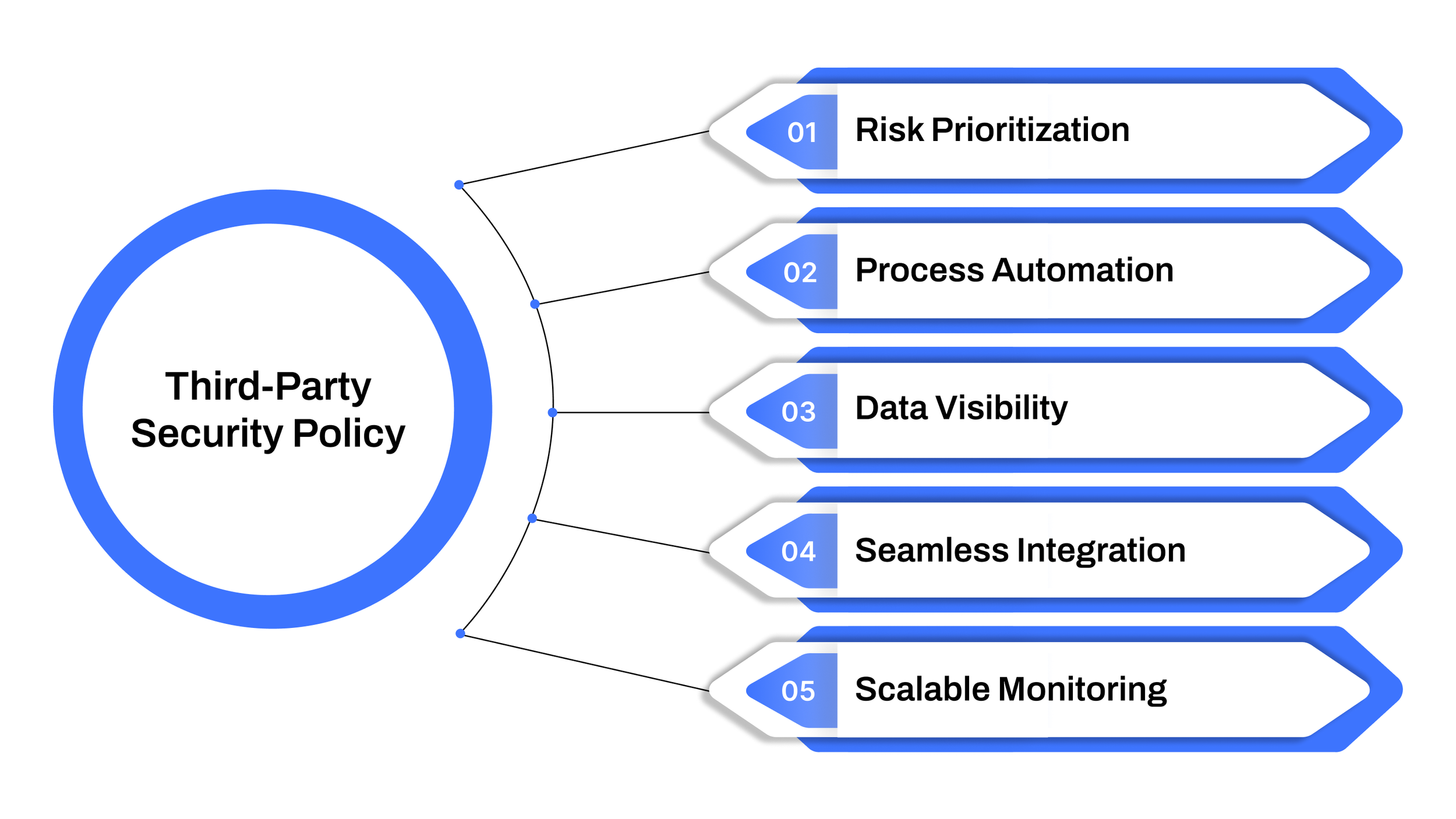
Below are concrete criteria to help CISOs and cyber-security teams evaluate platforms with the precision your role demands:
Risk Prioritization: The platform should prioritize vendor exposure based on actual business impact, not just generic ratings.
Process Automation: It should automate key workflows such as vendor onboarding, questionnaire distribution, evidence collection, and follow-up actions.
Data Visibility: A single dashboard where you can see vendor access to systems/data, audit trails of released documents, and real-time changes in vendor status.
Seamless Integration: The tool must plug into your existing ecosystem, procurement, identity/access, SIEM, so you minimize disruption and data silos.
Scalable Monitoring: Choose a platform designed to support large vendor sets, evolving business models, and emerging data-privacy or security requirements.
Auditive aligns with these criteria and more.
According to Auditive’s own site, the platform lets buyers track all vendors in one place, onboard vendors 4× faster, and integrate with procurement workflows seamlessly.
Final Thoughts
As the complexity of third-party ecosystems continues to grow, maintaining control over vendor risks is becoming a defining factor in enterprise security. The right vendor risk management approach ensures not just visibility but accountability across every external connection that touches your data. A centralized Trust Center adds to this by providing real-time insights into vendor performance, documentation, and security posture, empowering CISOs and risk leaders to make faster, data-driven decisions.
For organizations seeking to strengthen oversight without adding layers of manual work, Auditive offers a unified, intelligent solution. Its continuous monitoring, automated workflows, and integrated Trust Center simplify how you manage vendor security end-to-end.
Schedule a demo with Auditive and see how effortless secure vendor relationships can be.
FAQs
1. What is vendor risk management?
Vendor risk management is the process of identifying, assessing, and mitigating risks that arise from third-party vendors who have access to your systems, data, or operations.
2. Why is a Trust Center important?
A Trust Center provides a single source of truth for all vendor security information, policies, certifications, assessments, making it easier for teams to monitor and validate vendor performance.
3. How often should vendor risks be reassessed?
Critical vendors should be reassessed quarterly or after any major operational change, while lower-risk vendors can be reviewed annually.
4. What features should I look for in vendor risk management software?
Look for automation in risk scoring, continuous monitoring, integration with procurement workflows, and clear visibility into vendor performance.
5. How does Auditive support continuous vendor risk management?
Auditive automates the entire vendor risk lifecycle, from onboarding to continuous monitoring, through its integrated platform and centralized Trust Center, allowing faster, smarter, and more secure decision-making.