Cybersecurity Frameworks and Standards Guide 2025
As cyber threats continue to evolve, safeguarding digital assets has become more than just an IT priority; it’s a business necessity. Every organization, whether small or enterprise-level, faces growing pressure to meet established cybersecurity standards that ensure data protection, regulatory compliance, and operational resilience.
However, with numerous frameworks available, including NIST and ISO 27001, as well as CIS Controls and SOC 2, determining where to start can be overwhelming. The key lies in understanding how these standards work, how they align with your organization’s goals, and how to implement them effectively to reduce risks and strengthen trust.
This guide breaks down the essential cybersecurity standards and frameworks for 2025, helping you make informed decisions about building a secure, compliant, and future-ready security posture.
Quick Summary
Cyber security standards like ISO 27001, NIST CSF, and CIS Controls set the foundation for modern data protection.
These frameworks provide a roadmap for identifying, managing, and mitigating evolving cyber risks.
The right framework depends on your industry, compliance needs, and digital infrastructure.
Integrating multiple standards enhances overall governance and resilience.
Auditive helps businesses turn compliance efforts into strategic growth drivers, not administrative burdens.
What Are Cybersecurity Standards?
Cybersecurity standards are structured frameworks of best practices and guidelines that help organizations strengthen their digital defenses and safeguard sensitive information. Unlike internal cybersecurity policies, which govern employee behavior and internal processes, standards serve as universal benchmarks for data protection and risk management across industries.
In simple terms, while a company policy might require employees to update passwords every 90 days, a cybersecurity standard could recommend system-wide password updates every month to minimize vulnerabilities.
Recognized authorities typically establish these standards and include detailed processes, security controls, and technical requirements to ensure consistent protection against evolving cyber threats. The right standard for an organization often depends on factors such as industry type, data sensitivity, regulatory obligations, and geographical location.
By adopting the appropriate cybersecurity standards, businesses not only protect their digital assets but also demonstrate trust, compliance, and resilience in an increasingly complex cyber landscape.
Why Cybersecurity Standards Matter
Where threats evolve faster than ever, adhering to well-defined cybersecurity standards isn’t just an option; it’s a necessity. These standards, developed by trusted global organizations, serve as the foundation for protecting business assets, maintaining compliance, and fostering digital trust. Here’s why they matter:
1. Minimize Security Risks
Cybersecurity standards provide structured, proven guidelines to identify and mitigate vulnerabilities before they’re exploited. By following these best practices, organizations can significantly reduce the likelihood of cyberattacks, data breaches, or internal misconfigurations that put sensitive information at risk.
Also read: How to Prevent Data Breaches in Healthcare
2. Strengthen Customer and Partner Trust
Companies that comply with recognized cybersecurity standards, such as ISO 27001 or NIST, demonstrate a clear commitment to safeguarding customer data. This proactive approach boosts brand credibility, attracting clients, partners, and investors who value security and reliability.
3. Improve Security Governance
Implementing cybersecurity frameworks enhances visibility and control over digital assets. It helps organizations establish consistent security policies, streamline incident response, and simplify the adoption of new technologies without compromising safety.
4. Meet Compliance Requirements
Many industries now require strict adherence to cybersecurity standards to meet regulatory obligations. Compliance not only helps avoid legal penalties and financial losses but also positions a company as a trusted, responsible player in the marketplace.
In essence, adopting cybersecurity standards builds resilience, ensures regulatory alignment, and establishes a culture of proactive defense, key ingredients for long-term success in a high-risk cyber landscape.
Key Types of Cyber Security Standards
Protecting an organization from cyber threats requires more than just strong passwords or firewalls. It demands a structured framework that covers every layer of security, from technology and processes to regulatory compliance. Cybersecurity standards are broadly classified into technical, organizational, and legal standards, each playing a vital role in building a resilient security posture.
1. Technical Standards
Technical standards focus on the technological side of cyber protection. They define specific controls, best practices, and configurations that safeguard your digital infrastructure from vulnerabilities and attacks.
These standards help organizations maintain confidentiality, integrity, and availability (CIA) of their data and systems, the three pillars of information security.
Key components include:
Vulnerability assessments: Regularly identifying and patching weak spots before attackers can exploit them.
Secure configuration guidelines: Establishing uniform settings for systems and devices to minimize exposure.
Access control measures: Ensuring only authorized personnel can access sensitive data or systems.
Encryption protocols: Protecting data in transit and at rest to prevent unauthorized access.
By adhering to these standards, organizations can operate confidently in the digital space, proactively managing risks and minimizing potential disruptions.
2. Organizational Standards
While technical standards define what needs protection, organizational standards define how to manage that protection. These focus on processes, governance, and compliance mechanisms that ensure a company’s cybersecurity strategy remains consistent and effective.
Core principles of organizational standards:
Structured policies and procedures: Clear documentation outlining responsibilities and risk response actions.
Regular audits: Periodic reviews to ensure compliance and identify areas for improvement.
Employee awareness and training: Empowering teams to recognize and respond to potential threats.
Incident response frameworks: Plans for detecting, reporting, and recovering from cyber incidents.
Implementing these standards helps create a culture of security awareness and accountability across the organization, making cyber resilience a shared responsibility.
3. Legal Standards
Legal standards define the regulatory and compliance obligations that govern how data is collected, processed, and protected. Non-compliance can result in hefty fines, reputational damage, and operational restrictions.
Prominent examples include:
GDPR (General Data Protection Regulation): Governs how personal data is collected, stored, and shared within the EU and EEA, emphasizing transparency and accountability.
HIPAA (Health Insurance Portability and Accountability Act): Regulates the protection of sensitive healthcare information in the United States.
For global businesses, compliance isn’t optional; it’s a trust-building factor. Aligning with these standards demonstrates your organization’s commitment to safeguarding user privacy and maintaining data integrity.
In essence, combining technical, organizational, and legal standards creates a strong defense system, ensuring that your business not only meets compliance benchmarks but also earns stakeholder trust and operational resilience in the face of evolving cyber threats.
Learn more about: What Is Operational Risk Management? Definition, Framework & Tools
Building a resilient framework is just the beginning; platforms like Auditive take it further by empowering organizations to continuously monitor, assess, and strengthen their cyber defense posture in real time.
Top Cybersecurity Standards You Should Know in 2025
If you’re a startup handling sensitive customer data or an enterprise working with global clients, aligning with cybersecurity standards is no longer optional; it’s essential. Some are legally mandatory, while others signal credibility and trustworthiness to your partners and customers. Here’s a breakdown of the most recognized cybersecurity frameworks every business should know about in 2025:
1. HIPAA (Health Insurance Portability and Accountability Act)
A cornerstone of healthcare data security in the U.S., HIPAA governs how organizations manage, store, and transmit protected health information (PHI).
It ensures patient privacy and strict data handling procedures.
Non-compliance can result in penalties of up to $3.2 million, making adherence a must for any healthcare entity or business processing medical data.
2. GDPR (General Data Protection Regulation)
The GDPR sets the gold standard for data privacy across the EU and impacts any company that processes personal data of EU citizens.
It enforces user consent, transparency, and accountability.
Fines for non-compliance can reach €20 million or 4% of annual global turnover, whichever is higher.
Even non-EU businesses working with European customers must comply, making it a global benchmark for privacy.
3. PCI DSS (Payment Card Industry Data Security Standard)
If your business processes, stores, or transmits credit card data, PCI DSS compliance is mandatory.
The latest PCI DSS 4.0 introduces 12 updated requirements for enhanced payment security.
Non-compliance can result in fines from $5,000 to $100,000 per month, making it critical for all payment processors and eCommerce businesses.
4. ISO 27001 (Information Security Management System)
The internationally recognized ISO 27001:2022 provides a structured framework for building and maintaining an Information Security Management System (ISMS).
It helps organizations safeguard data systematically and align with modern cybersecurity challenges such as cloud and remote work risks.
While not legally required, it’s a strong trust signal for clients and partners, often influencing contract approvals.
5. SOC 2 (Service Organization Control 2)
SOC 2 compliance is a must for SaaS and cloud service providers handling customer data.
It assesses adherence to five trust principles: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Unlike other frameworks, SOC 2 is customizable; businesses can define its scope based on their needs, but auditors demand precision and rigor.
6. NIST (National Institute of Standards and Technology) Framework
Originally designed for U.S. federal agencies, the NIST Cybersecurity Framework has become a go-to resource for organizations of all sizes.
It focuses on five core functions: Identify, Protect, Detect, Respond, and Recover.
NIST is free, making it a popular choice for SMBs and enterprises alike to enhance their security posture.
7. COBIT (Control Objectives for Information and Related Technologies)
COBIT aligns IT governance with business strategy, particularly in finance and government sectors.
It focuses on Governance, Risk, and Compliance (GRC) to ensure IT operations drive value.
COBIT offers practical guidance on access management, data encryption, and incident response to establish a strong control environment.
8. CCPA (California Consumer Privacy Act)
The CCPA enhances data privacy rights for California residents, mirroring GDPR’s impact in the EU.
It applies to any business collecting or processing Californian residents’ data, regardless of location.
Fines for intentional violations can reach $7,500 per incident, highlighting the importance of transparency in data handling.
9. CMMC (Cybersecurity Maturity Model Certification)
A must for organizations working within the U.S. Department of Defense (DoD) supply chain.
CMMC ensures the protection of Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
It includes five maturity levels, from basic cyber hygiene to advanced security capabilities, each with distinct compliance requirements.
10. FISMA (Federal Information Security Management Act)
Mandatory for federal agencies and contractors, FISMA requires the development and maintenance of strong information security programs.
Built on NIST’s best practices, it ensures the protection of government data from cyber threats.
Vendors, subcontractors, and agencies working with federal data must comply.
11. HITRUST CSF (Common Security Framework)
HITRUST CSF consolidates multiple standards like HIPAA, ISO 27001, and NIST into a single, unified framework.
It’s especially valuable for multi-sector organizations needing to meet several compliance requirements simultaneously.
HITRUST certification not only simplifies compliance but also enhances credibility and competitiveness.
12. SOX (Sarbanes-Oxley Act)
Initially aimed at improving financial transparency, SOX also enforces IT controls to protect financial data from tampering or fraud.
It’s mandatory for all publicly traded U.S. companies and their subsidiaries.
SOX promotes accountability across internal systems, external auditors, and analysts, strengthening investor trust.
13. FedRAMP (Federal Risk and Authorization Management Program)
For cloud service providers aiming to work with U.S. government agencies, FedRAMP certification is essential.
It standardizes security assessments for cloud-based solutions.
Although achieving FedRAMP authorization can be time-consuming, it’s a gateway to federal contracts and long-term partnerships.
Cybersecurity standards can be tricky to understand, but they’re vital for protecting your data, customers, and brand. Each framework is designed for a specific purpose: HIPAA for patient information, SOX for financial accountability.
If you want to simplify compliance while maintaining continuous vendor and data protection, integrating these frameworks into your strategy is the smartest step toward resilience and trust.
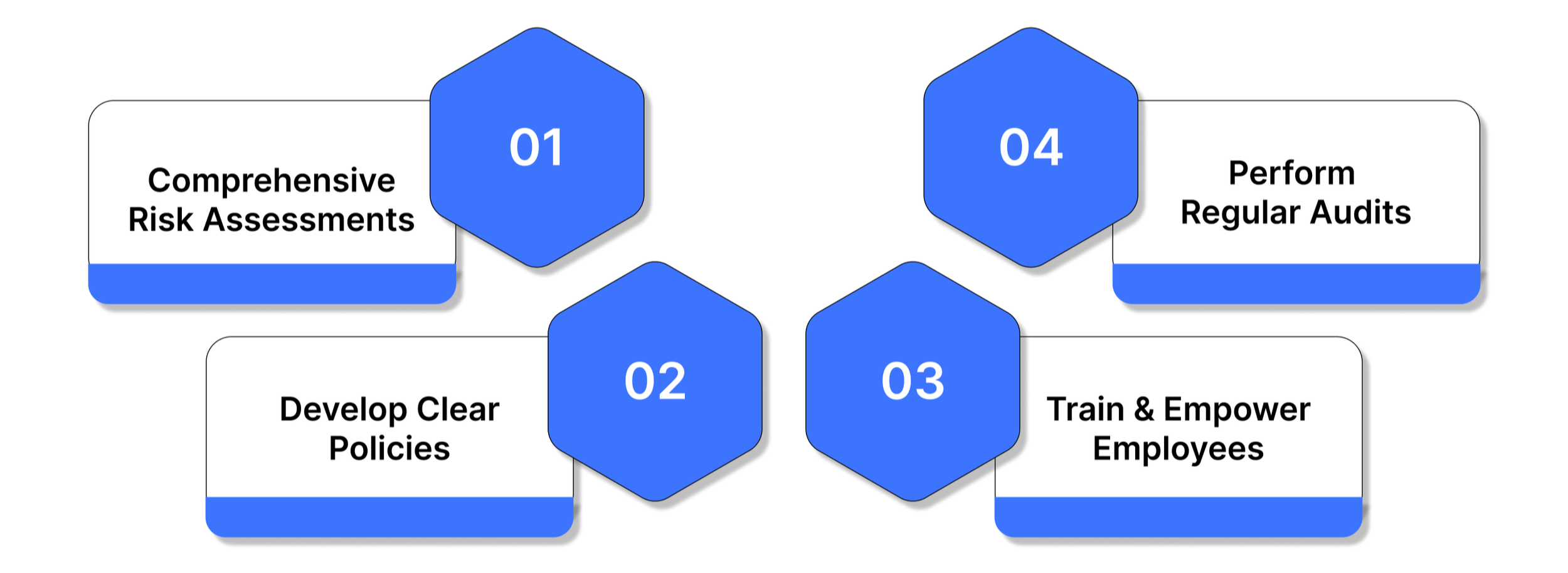
How Organizations Implement Cybersecurity Standards
Building a strong cybersecurity posture doesn’t happen overnight; it requires structure, awareness, and continuous improvement. Implementing cybersecurity standards helps organizations stay ahead of threats, protect sensitive data, and maintain trust with clients and regulators. Here’s how organizations typically put these standards into action:
1. Conduct Comprehensive Risk Assessments
Before setting any controls, organizations must understand where they stand.
Identify vulnerabilities across systems, networks, and operations.
Assess potential threats that could exploit those weaknesses.
Prioritize critical risks to focus resources effectively.
Develop mitigation strategies to strengthen defenses and reduce exposure.
A thorough risk assessment helps establish a clear view of the company’s current security posture and guides decision-making on where improvements are most needed.
2. Develop Clear Policies and Procedures
Once risks are identified, the next step is to define how they’ll be managed.
Create governance controls and compliance frameworks aligned with recognized standards like ISO 27001 or NIST.
Document step-by-step procedures for handling sensitive data, reporting incidents, and managing third-party risks.
Ensure all departments understand and follow these guidelines consistently.
Strong policies and procedures act as a roadmap for the entire organization, ensuring consistency and accountability in how cybersecurity is handled.
3. Train and Empower Employees
Even the most advanced security tools can fail if employees aren’t aware of cyber threats.
Conduct regular cybersecurity awareness sessions.
Educate staff on phishing, social engineering, and password hygiene.
Use interactive simulations to test real-world scenarios and reinforce best practices.
By making employees an active part of the defense system, organizations build a culture of vigilance and shared responsibility.
4. Perform Regular Audits and Testing
Security isn’t static; it needs constant evaluation and refinement.
Schedule periodic audits to verify compliance with established standards.
Perform penetration testing to uncover hidden vulnerabilities before attackers do.
Implement continuous monitoring tools to detect unusual activity in real time.
Regular audits and testing ensure that controls remain effective and adapt to evolving threats, keeping the organization’s digital assets secure.
Managing risk frameworks, audits, and vendor compliance manually can quickly become overwhelming. That’s where Auditive helps. With its Trust Center and Vendor Risk Management capabilities, organizations can centralize security governance, automate assessments, and gain real-time visibility into their cyber health, all in one place.
Strengthen Your Cybersecurity Compliance with Auditive
Implementing cybersecurity standards isn’t just about meeting checklists; it’s about maintaining continuous visibility, trust, and resilience across your digital ecosystem. That’s where Auditive helps you take control.
With Auditive’s Trust Center, you can centralize and automate compliance across frameworks like ISO 27001, SOC 2, NIST, and more, without the manual overhead. The platform continuously monitors your vendors and partners, identifying potential threats before they turn into costly incidents.
Key advantages of using Auditive include:
Centralized Trust Management: Keep all your compliance reports, certifications, and vendor risk insights in one accessible dashboard.
Continuous Monitoring: Get real-time alerts for changes in vendor security posture or compliance status.
Faster Framework Alignment: Map your existing controls effortlessly across multiple frameworks to save time and reduce audit fatigue.
Collaborative Security Posture: Empower internal teams and external partners to stay aligned with the same security goals.
By integrating Auditive into your workflow, you build a stronger, more transparent defense against cyber risks while simplifying your organization’s path to compliance.
Stay compliant. Stay confident. Strengthen your Trust Center with Auditive.
Wrapping Up
As organizations expand their digital footprint, the threat landscape grows equally complex. Cybersecurity frameworks and standards are no longer optional; they’re the foundation of trust, governance, and business continuity. From NIST CSF to ISO 27001, adopting structured security practices ensures your systems remain resilient and your data stays protected.
But compliance isn’t just about ticking boxes; it’s about anticipating risks, especially across interconnected vendor ecosystems. A strong vendor risk management approach, guided by the right frameworks, helps you identify vulnerabilities before they impact operations.
At Auditive, we integrate cybersecurity standards into your broader risk management strategy, ensuring every vendor, process, and system contributes to a unified, compliant, and secure digital ecosystem.
Strengthen your vendor risk management and cybersecurity posture with Auditive’s compliance-led approach. Connect with us today to implement the frameworks that power trust and resilience.
FAQs
1. What are cybersecurity frameworks, and why are they important?
Cybersecurity frameworks provide structured guidelines for managing and reducing cyber risks. They help organizations establish policies, processes, and controls to protect systems and data effectively.
2. Which cybersecurity standards are most relevant for 2025?
In 2025, key standards include ISO 27001:2022, NIST CSF 2.0, CIS Controls v8, and GDPR for data privacy compliance. Each framework addresses different risk and governance needs.
3. How do I choose the right cybersecurity framework for my organization?
The choice depends on your industry, regulatory requirements, and data sensitivity. For example, financial institutions may prefer ISO 27001, while government agencies often adopt NIST.
4. Can an organization adopt multiple frameworks?
Yes, many organizations integrate multiple frameworks for broader coverage. For example, combining NIST for risk management with ISO 27001 for certification ensures stronger governance.
5. How can Auditive help in achieving compliance with cybersecurity standards?
Auditive provides tailored assessments, implementation roadmaps, and continuous compliance monitoring to align your organization with the most relevant standards, ensuring security and regulatory confidence.