Understanding Common Security Frameworks: Examples and Types
A 2024 industry benchmark found that 55% of organizations have adopted a common controls framework to streamline governance, risk and vendor oversight efforts.
Where business systems, data handling, and external dependencies constantly evolve, a common security framework gives a baseline: defining controls, mapping risks, and ensuring consistency across internal and vendor operations.
This blog explains how to choose the right framework depending on your risk profile, data exposure, and vendor dependencies, helping you build repeatable, measurable security practices before incidents force reactive fixes.
In a nutshell:
A common security framework only works when controls are applied consistently and monitored continuously.
Vendor risk directly influences your ability to meet framework expectations.
A centralized vendor provides evidence, certifications, and risk signals.
Framework alignment becomes easier when assessments and updates are automated.
Auditive helps maintain control integrity with real-time vendor visibility.
Why a Common Security Framework Matters More Than a Checklist
A common security framework isn’t a stack of policies; it’s the operating system for how your organization identifies, manages, and strengthens its security controls. It defines the procedures, guardrails, and review cycles needed to protect systems and reduce ambiguity across teams.
Where most companies fail isn’t selecting the framework but in treating implementation as a one-time project. Analysts repeatedly note that static, unreviewed controls are a leading cause of preventable breaches. When teams “set it and forget it,” gaps grow quietly until an incident exposes them.
A framework only works when it’s actively maintained. Security isn’t a destination; it’s an ongoing cycle. A well-run framework keeps controls current, forces regular verification, and provides visibility into emerging risks; not just during audits, but every day operational decisions depend on it.
A Practical Guide to Common Security Frameworks That Shape Modern Risk Standards
Choosing the right common security framework determines how your organization detects risk, governs data, and earns trust from partners and customers. Below is a clear breakdown of the most widely adopted frameworks and what they actually enable inside a security program.
1. SOC 2
SOC 2 measures whether an organization can consistently protect customer data under the five Trust Services Criteria. Beyond documentation, it evaluates real-world control performance, monitoring, change management, vendor oversight, access governance, and logging practices.
Where it matters: Essential for SaaS companies and vendors handling sensitive data, especially when customers expect objective verification of internal security maturity.
Learn more about: Complete Guide to SOC 2 Compliance and Audits
2. ISO 27001
ISO 27001 defines how to build and maintain an Information Security Management System (ISMS). It formalizes risk identification, treatment plans, control selection, internal audits, and leadership accountability. The 2022 update expanded requirements for cloud services, threat intelligence, and data masking.
Where it matters: Organizations that need a globally recognized certification to support international deals or demonstrate structured, repeatable security governance.
3. NIST Cybersecurity Framework
NIST CSF organizes security operations into five core functions: Identify, Protect, Detect, Respond, and Recover. It includes detailed categories like asset visibility, supply chain oversight, anomaly detection, and incident containment. Its tier model gives leaders a measurable way to track maturity.
Where it matters: Ideal for teams needing a flexible, risk-based roadmap that prioritizes controls based on actual threats rather than regulatory checklists.
4. HIPAA
HIPAA outlines administrative, technical, and physical safeguards for protecting PHI. It requires organizations to run routine risk analyses, implement strict access controls, secure transmission channels, and maintain audit logs for every interaction with patient data.
Where it matters: Healthcare organizations and their technology partners rely on HIPAA-aligned processes to limit breach exposure and ensure traceable handling of patient information.
5. PCI DSS
PCI DSS requires organizations to encrypt cardholder data, limit access to payment systems, document secure network configurations, and monitor all card-related activity. Version 4.0 introduced stronger authentication, continuous testing, and expanded logging expectations.
Where it matters: Mandatory for any company touching card data and critical for reducing financial fraud and chargeback-related losses.
6. GDPR
GDPR governs how organizations collect, process, retain, and transfer data belonging to EU residents. Requirements include explicit consent, purpose limitation, user access rights, breach notification within 72 hours, and strict data minimization rules.
Where it matters: Businesses with European customers or operations use GDPR-aligned controls to reduce regulatory exposure and strengthen user trust.
7. HITRUST CSF
HITRUST merges elements of ISO 27001, NIST, HIPAA, and PCI into a unified, prescriptive control set. It grades organizations on control maturity across policy, procedure, implementation, measurement, and management.
Where it matters: Industries needing a single framework recognized across healthcare, financial services, and cloud ecosystems use HITRUST to simplify overlapping audits.
Must read: HITRUST vs HIPAA: Key Differences Explained
8. COBIT
COBIT provides governance models that align IT decisions with enterprise goals. It focuses on risk optimization, value delivery, performance monitoring, and accountability across leadership and security operations.
Where it matters: Public companies use COBIT for SOX-aligned governance and to ensure security decisions directly support business strategy.
9. NERC-CIP
NERC-CIP defines mandatory cybersecurity standards for organizations in the electricity and power sector. Controls cover personnel screening, asset inventories, incident response, system hardening, and recovery planning.
Where it matters: Critical infrastructure operators depend on NERC-CIP to minimize service disruption risks and safeguard national power systems.
10. FISMA
FISMA requires federal agencies and contractors to document systems, categorize risks, implement minimum controls, and maintain continuous monitoring. It integrates directly with NIST SP 800-53 control requirements.
Where it matters: Any entity supporting U.S. government operations must meet FISMA standards to maintain eligibility for federal work.
11. NIST SP 800-53
NIST SP 800-53 provides a comprehensive library of controls spanning access control, data governance, monitoring, privacy, supply chain oversight, and contingency planning.
Where it matters: Adopted by large enterprises and public-sector organizations needing a deep, customizable control catalog aligned with federal expectations.
12. NIST SP 800-171
NIST 800-171 defines how contractors should protect controlled unclassified information (CUI). Requirements include encryption, audit logging, multi-factor authentication, and secure configuration baselines.
Where it matters: Essential for defense contractors and manufacturers aiming to remain competitive within federal supply chains.
13. CCPA / CPRA
CCPA expands consumer rights related to data visibility, deletion, opt-out preferences, and limitations on data sale or sharing. CPRA adds stricter rules around sensitive personal information and mandatory risk assessments.
Where it matters: Any business handling data belonging to California residents must adopt CCPA-aligned transparency and control mechanisms.
Also read: CCPA Compliance Tools in 2025
14. CIS Controls
CIS Controls provide prioritized, tactical actions that reduce the most common attack vectors. They address endpoint visibility, vulnerability management, access governance, data recovery, and continuous monitoring.
Where it matters: Companies needing fast, measurable reductions in risk rely on CIS Controls to build foundational defenses.
Security frameworks don’t exist to overwhelm teams; they exist to standardize decisions, reduce uncertainty, and provide a reliable path for scaling security with the business.
Understanding the strengths of each framework makes it easier to select the right structure and implement controls that meaningfully reduce risk exposure.
Choosing the Right Common Security Framework for Your Environment
Selecting the right common security framework isn’t about chasing badges; it’s about choosing the structure that actually fits your data exposure, industry expectations, and customer trust requirements. The reference points below stay focused on what matters: what you handle, who you serve, and how your systems operate.
Here’s a streamlined way to assess which framework aligns with your reality:
Retail or healthcare data?
PCI DSS or HIPAA will shape most of your requirements.
User data from the EU or California?
GDPR and CCPA aren’t optional; they’re legally binding based on user geography.
Cloud-based customer data?
SOC 2 and ISO 27001 offer the clearest path to proving security maturity and operational discipline.
Publicly traded company?
COBIT provides the governance foundation needed to meet SOX expectations.
Working with US federal agencies?
NIST SP 800-53 or NIST SP 800-171 are typically required, not recommended.
Most organizations evolve through multiple frameworks over time. The good news: many share overlapping controls, making it easier to adopt an additional framework once you’ve established one solid baseline.
Auditive simplifies this progression by mapping shared controls across frameworks, reducing duplicate evidence work, and giving teams a unified place to track readiness as requirements expand. It’s a practical lift for teams managing several overlapping frameworks, not a generic checklist layer.
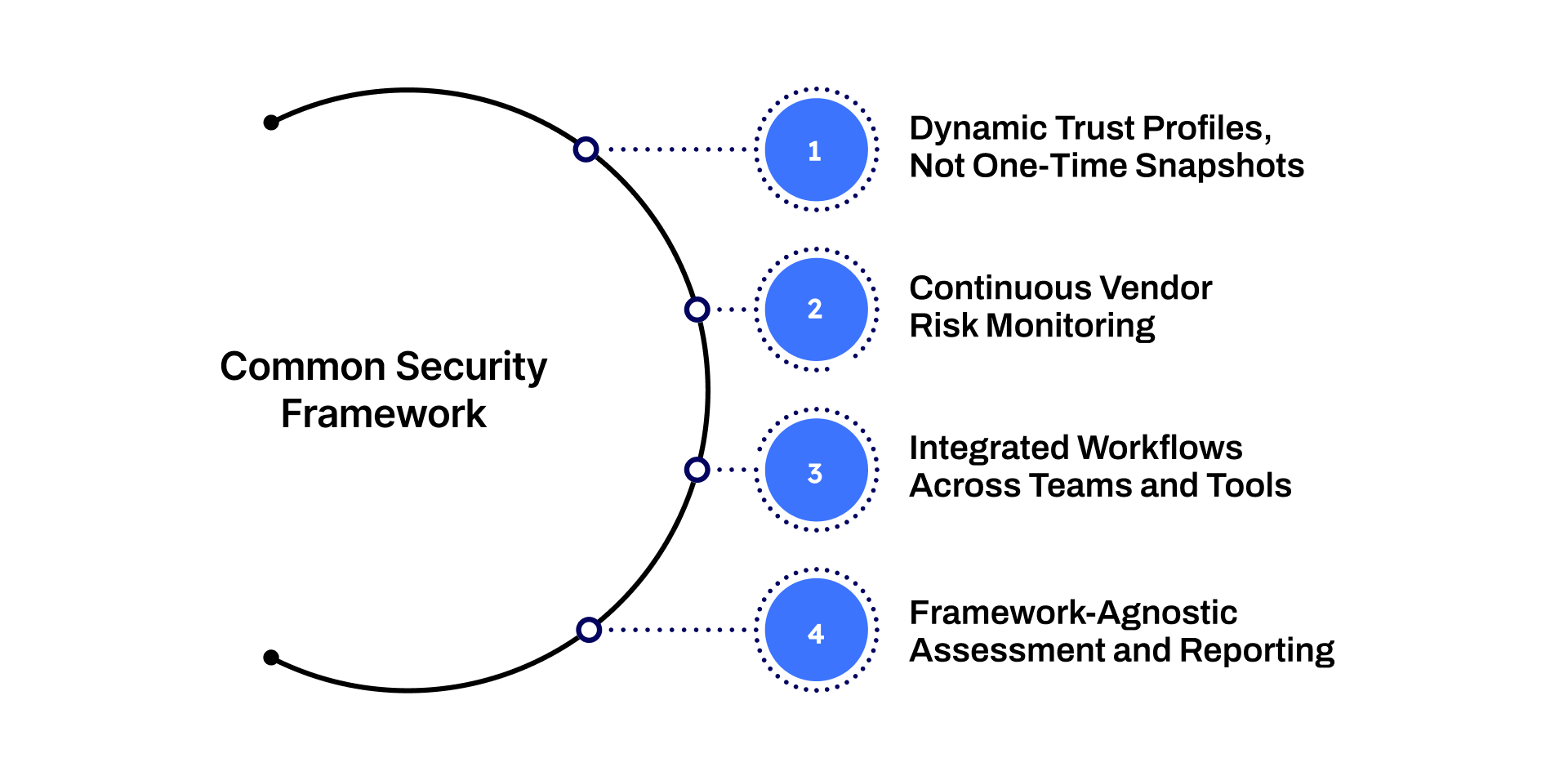
Why Auditive Fits When You Use a Common Security Framework
When organizations adopt a common security framework, the real challenge isn’t picking controls ,it’s ensuring they stay valid over time, across every vendor, system, and third party. Auditive bridges that gap by turning static assessments into continuous, real-time monitoring and vendor insight.
Dynamic Trust Profiles, not one-time snapshots. Auditive builds AI-powered Trust Profiles for each vendor, which update automatically, reflecting new certificates, policy changes, incident disclosures, or security posture shifts.
Continuous risk monitoring. Instead of relying solely on point-in-time audits, AuditiveX monitors vendors 24/7 for new risk signals, giving you live insight into any changes that might affect adherence to your chosen security frameworks.
Integrated workflows across teams and tools. With 100+ API integrations (e.g., Slack, Salesforce, JIRA) and in-platform collaboration, Auditive ensures that procurement, security, and compliance or audit teams work from the same verified vendor data, reducing duplication and miscommunication.
Framework-agnostic assessment and reporting. Auditive supports multiple frameworks (SOC 2, ISO 27001, and others) and custom questionnaires, enabling organizations to align vendor evaluations with whichever security framework they implement.
By combining continuous monitoring, verified vendor data, and flexible assessment logic, Auditive turns a common security framework from a static checklist into a living, enforceable posture, reducing drift, improving vendor transparency, and giving leadership confidence that controls still hold even as vendors evolve.
To Sum Up
Selecting a common security framework isn’t about chasing labels; it’s about creating a security posture that holds up under real-world risk, vendor dependencies, and operational growth. The right framework gives structure, but its effectiveness depends on how consistently your organization enforces controls, how quickly you detect deviations, and how much visibility you maintain across third-party ecosystems.
A centralized approach brings all of these elements together by giving teams a single source of truth for vendor controls, evidence, certifications, and ongoing risk signals. Instead of scattered documents and manual tracking, you gain a unified, continuously updated view aligned to the framework you rely on, whether SOC 2, ISO 27001, NIST, or others.
If you want to operationalize your chosen framework with continuous monitoring, live vendor intelligence, and automated updates, Auditive provides a streamlined way to do that at scale.
Schedule a demo to explore how your team can reduce manual workload and strengthen end-to-end assurance.
FAQs
1. Do all organizations need to adopt a security framework?
Not always, but most benefit from one. Frameworks provide structure for managing risk, documenting controls, and improving security maturity.
2. Can multiple common security frameworks be used at the same time?
Yes. Many companies map overlapping controls across frameworks to reduce duplicate work.
3. How does vendor risk affect framework adherence?
Weak vendor controls can undermine your own security posture since third parties often handle sensitive data or critical operations.
4. What role does Auditive play in security frameworks?
It centralizes vendor evidence, certifications, and monitoring so teams work from verified, current data.
5. How does Auditive support organizations using these frameworks?
Auditive provides real-time vendor insights, automated updates, and unified trust reporting that help maintain continuous alignment with the chosen framework.