Third-Party Debit Card Security Breach Insights
Debit card fraud is not new, but its scale, complexity, and reach have changed dramatically in recent years. Today, the greatest risks don’t always come from a bank’s own systems but from its extended ecosystem of vendors, payment processors, fintech partners, and third-party service providers. These external connections, while critical for innovation and convenience, create multiple entry points for cybercriminals.
In 2023, global card fraud losses surpassed $32 billion, with third-party security gaps being a significant contributor. High-profile breaches have shown that even when a financial institution has strong in-house defenses, vulnerabilities in a vendor’s network can expose sensitive cardholder data. The growing reliance on outsourced services, from cloud payment gateways to KYC verification platforms, means the chain is only as strong as its weakest link.
Understanding and managing the risks of third-party debit card security breaches is, therefore, not just a compliance requirement; it’s a business survival strategy.
Overview
Third-party debit card breaches are rising as attackers exploit vendor vulnerabilities to steal sensitive financial data.
Manual vendor checks aren’t enough, businesses need real-time monitoring, automation, and AI-driven fraud detection.
Proactive vendor risk management helps prevent breaches before they escalate, reducing financial and reputational damage.
Auditive empowers resilience with Trust Center transparency, compliance insights, real-time monitoring, and automated vendor risk management.
The core message: Strong technology + smart vendor governance = reduced breach risk, stronger trust, and long-term business resilience.
Understanding Third-Party Debit Card Security Breaches
What qualifies as a third-party debit card breach?
A third-party debit card security breach occurs when unauthorized access to cardholder data happens not through the bank or card issuer’s system, but via a partner organization. These partners might process payments, store transaction details, provide digital wallets, or even offer IT support.
The crucial difference is that while the card issuer may not directly cause the breach, it is ultimately responsible for safeguarding customer trust.
Common third-party entities involved:
Payment processors manage and transmit card payments between merchants and banks.
Fintech platforms offer digital apps that provide peer-to-peer payments, mobile wallets, and buy-now-pay-later services.
Cloud vendors provide infrastructure where financial data is stored and processed.
Outsourced IT or call center vendors often have back-end system access for customer support.
Difference between direct and third-party breaches:
Direct breach: Hackers target the financial institution’s systems directly.
Third-party breach: Attackers compromise an external provider and gain access to customer debit card data indirectly.
This distinction matters because businesses often underestimate third-party risks, assuming outsourced vendors have the same level of security rigor. Reality proves otherwise.
How Third-Party Breaches Happen
Third-party debit card breaches rarely stem from a single vulnerability. Instead, they are often the result of a chain of weaknesses across the vendor ecosystem. Because financial institutions depend on a wide network of payment processors, fintech partners, and third-party service providers, attackers only need to exploit the weakest link to gain access to sensitive debit card data. Below are the most common causes:
1. Weak Vendor Security Controls
Many third-party providers, particularly smaller fintech startups or niche vendors, struggle to implement enterprise-grade security measures due to budget constraints, lack of expertise, or limited compliance knowledge. Hackers exploit these gaps, infiltrating smaller vendors’ networks and then pivoting into larger financial institutions through trusted connections.
In fact, research shows that over 60% of data breaches are linked to third parties with inadequate security controls.
Once attackers breach a vendor with weak firewalls, outdated systems, or poor access control, they often move laterally to access debit card processing systems and customer financial data.
2. Phishing and Credential Theft in Partner Systems
Phishing continues to be one of the most successful attack methods, and vendors are prime targets. By sending deceptive emails or text messages, attackers trick vendor employees into revealing credentials, clicking on malicious links, or downloading infected files.
Once credentials are stolen, attackers gain legitimate but unauthorized access to vendor systems, often with elevated privileges.
This access can then be used to extract debit card information, install malware, or exploit integrations with banking systems.
According to industry reports, 91% of cyberattacks begin with phishing, and vendors handling sensitive payment data are especially attractive targets.
3. Insecure APIs and Integrations
Modern banking relies heavily on application programming interfaces (APIs) to facilitate real-time transactions between banks, apps, and payment providers. While APIs enable convenience and innovation, poorly secured APIs can function as open gateways for attackers.
In 2022, API-related attacks grew by 400%, with many directly linked to financial services and payment processing vulnerabilities.
Weak authentication, missing encryption, or insufficient monitoring of API calls allows cybercriminals to intercept or manipulate debit card data.
In some cases, attackers exploit “shadow APIs”, undocumented or forgotten integrations, that are often overlooked in security audits.
4. Human Error or Insider Threats
Despite sophisticated technologies, human mistakes remain one of the largest risk factors in third-party debit card breaches. A single misconfigured cloud storage bucket or the accidental sharing of unencrypted cardholder data can expose millions of customer records.
Insider threats, whether malicious employees selling data or careless staff mishandling sensitive information, contribute to nearly 30% of all financial data breaches.
Vendors with high employee turnover or limited training are especially vulnerable, as gaps in awareness or disgruntled insiders create opportunities for compromise.
Most breaches follow a predictable pattern: insufficient vendor risk management, lack of real-time visibility into third-party systems, and failure to continuously assess controls. Many organizations rely on outdated, point-in-time risk assessments, leaving them blind to emerging threats.
The Impact of a Debit Card Security Breach
The consequences of a third-party debit card security breach go far beyond stolen card numbers or temporary inconveniences. They ripple across consumers, businesses, regulators, and the wider financial ecosystem, often leaving long-lasting scars.
1. Financial Losses
The most immediate and visible impact of a debit card breach is monetary.
For businesses: Costs pile up quickly, fraud reimbursements, forensic investigations, regulatory fines, customer notifications, and legal fees. According to IBM’s 2023 Cost of a Data Breach Report, the average financial services breach cost reached $5.9 million. For smaller institutions, even a fraction of this can threaten survival.
For consumers: Victims often face fraudulent charges, frozen accounts, and disrupted access to funds. Even when banks reimburse losses, the stress and inconvenience of restoring financial stability is significant.
The financial aftershocks can also extend to partners and vendors involved in the transaction chain, amplifying the scope of the crisis.
2. Reputational Damage
While financial losses may eventually be recovered, customer trust is far harder to rebuild.
A single breach can tarnish a company’s brand reputation overnight.
Studies show that 81% of consumers say they would stop engaging with a brand online after a data breach (PwC survey).
In the crowded financial services and fintech market, even loyal customers may quickly switch to competitors they perceive as more secure.
Reputation loss is a silent cost, difficult to quantify, but often more damaging than direct monetary impact.
3. Regulatory Fines and Compliance Challenges
Breaches don’t just result in customer losses, they also trigger strict compliance consequences.
PCI DSS (Payment Card Industry Data Security Standard) requires rigorous controls on handling cardholder data. Non-compliance can lead to steep fines.
Privacy laws such as GDPR (EU) and CCPA (California) impose additional obligations around customer data security, reporting timelines, and consumer rights.
Regulators are increasingly scrutinizing third-party oversight, demanding proof that businesses can manage risks across their vendor ecosystem.
Failure to demonstrate proactive compliance can lead to multi-million-dollar penalties and stricter oversight, further straining business operations.
4. Long-Term Operational Disruptions
The fallout from a debit card breach doesn’t end with financial payouts or PR campaigns, it reshapes how businesses operate.
Incident response and recovery: Redirects critical resources away from innovation, customer service, and growth initiatives.
Vendor relationships: Breaches tied to third parties strain trust with existing partners and complicate future collaborations.
Employee morale: Staff face pressure, burnout, and reputational stress during prolonged recovery phases.
Timeline for recovery: Depending on the severity, full operational recovery can take months or even years.
Breaches not only slow progress but may also hinder long-term strategic growth.
The true cost of a third-party debit card breach often lies in the erosion of trust. Numbers can be recovered, systems can be repaired, but once transparency is questioned, businesses face an uphill battle to restore credibility.
Auditive’s Trust Center addresses this gap. By enabling businesses to demonstrate real-time security practices, vendor oversight, and compliance posture, it helps organizations rebuild customer confidence and maintain resilience in the aftermath of an incident. Vendor risk management isn’t just a compliance checkbox, it’s a foundation for trust that strengthens relationships with customers, partners, and regulators alike.
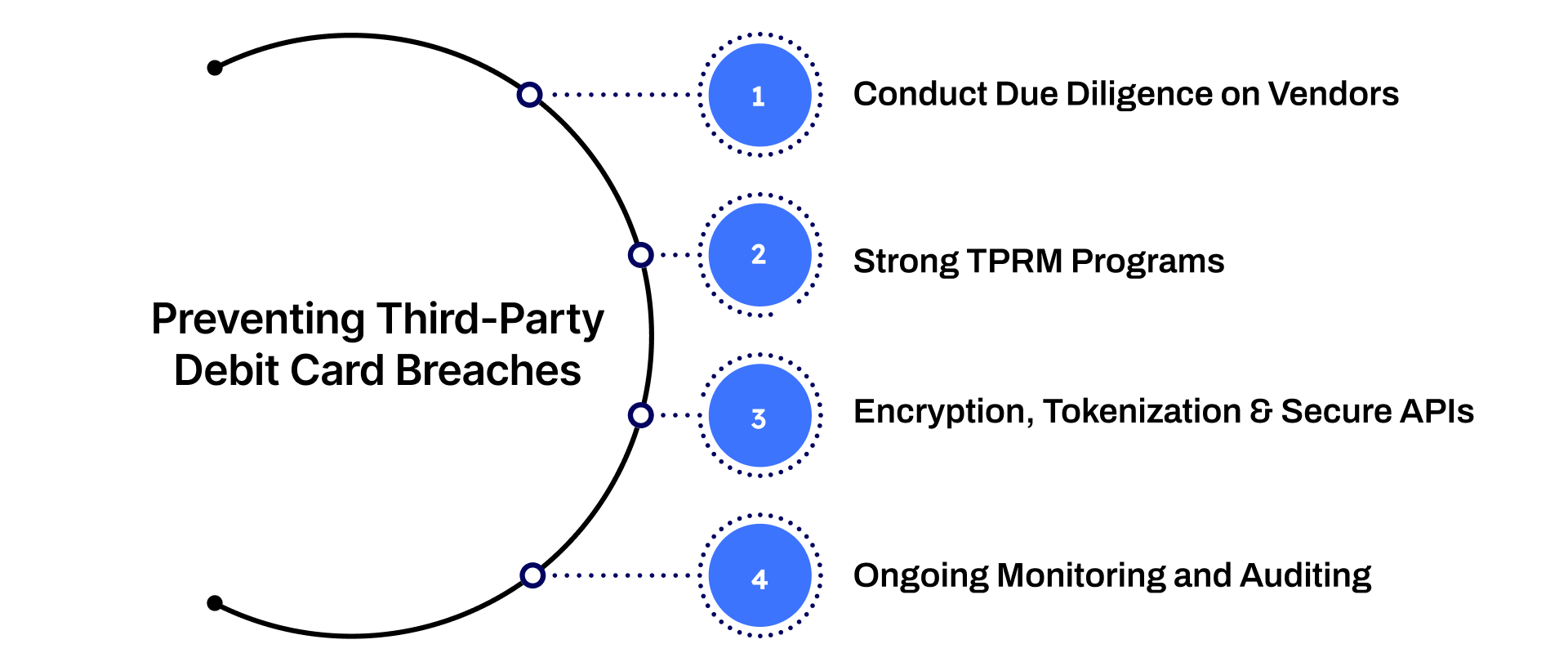
Best Practices to Prevent Third-Party Debit Card Breaches
Preventing third-party debit card breaches is not about implementing a single control, it’s about building a layered, proactive defense that recognizes the evolving nature of threats. Businesses must shift from reactive patching to continuous oversight, ensuring that vendor ecosystems are as secure as their internal systems.
1. Conduct Due Diligence on Vendors
A significant number of debit card breaches can be traced back to poorly vetted vendors. Due diligence should be the first gatekeeper in vendor onboarding.
Assess Security Policies: Review whether vendors follow frameworks such as ISO 27001, SOC 2, or NIST Cybersecurity standards.
Review Certifications and Compliance History: Verify past breaches, regulatory penalties, or history of data handling practices.
Independent Security Audits: Require third-party penetration tests or audit reports before granting access to cardholder data.
According to a Ponemon Institute study, 51% of organizations experienced a data breach caused by a third party, most due to inadequate vetting and oversight.
2. Strong Third-Party Risk Management (TPRM) Programs
A one-size-fits-all vendor approach creates blind spots. Instead, businesses need structured TPRM frameworks that adapt based on vendor risk levels.
Vendor Classification: Segment vendors into high, medium, and low risk based on their access to sensitive data.
Contractual Safeguards: Enforce obligations for encryption, access controls, and incident reporting.
Continuous Monitoring: High-risk vendors, such as payment processors, should face ongoing oversight rather than annual reviews.
Organizations with mature TPRM programs are 60% more likely to avoid severe third-party data breaches, according to Deloitte.
3. Encryption, Tokenization, and Secure APIs
Payment data remains a top target for attackers, making encryption and tokenization non-negotiable safeguards.
Encryption: Always encrypt cardholder data both in transit and at rest using strong cryptographic standards like AES-256.
Tokenization: Replace actual debit card numbers with unique tokens, ensuring breaches yield meaningless data.
Secure APIs: Implement strong authentication, rate limiting, and anomaly detection to prevent API abuse, one of the fastest-growing attack vectors in fintech.
A report by IBM shows that encryption and tokenization can reduce breach costs by up to 28%.
4. Ongoing Monitoring and Auditing
Security is dynamic, vendors that were secure today might become a risk tomorrow. Ongoing monitoring closes the gap.
Real-Time Network Monitoring: Detect anomalies and suspicious vendor activity before they escalate.
Continuous Vulnerability Scanning: Identify misconfigurations or unpatched systems that attackers could exploit.
Penetration Testing & Compliance Checks: Regular assessments ensure vendors stay aligned with evolving security requirements.
At Auditive, we help organizations establish continuous vendor oversight through automated monitoring and intelligent risk dashboards. This eliminates blind spots in the supply chain and ensures businesses maintain full visibility into vendor performance and compliance, without manual effort.
Role of Compliance and Regulations
In the financial services ecosystem, regulatory compliance is the foundation of debit card security. But while compliance frameworks provide structure, they should be seen as the starting line, not the finish line.
PCI DSS (Payment Card Industry Data Security Standard)
Purpose: PCI DSS sets global requirements for the secure storage, processing, and transmission of payment card data.
Impact: Non-compliance can lead to hefty fines and even revocation of card processing privileges.
Key Controls: Network segmentation, encryption, and regular vulnerability assessments.
Verizon’s 2023 Payment Security Report found that only 43% of organizations remain fully PCI DSS compliant a year after certification.
GDPR & CCPA
GDPR (General Data Protection Regulation): Protects EU customer data with fines of up to 4% of global annual turnover for non-compliance.
CCPA (California Consumer Privacy Act): Grants California residents greater control over their personal data, with fines ranging from $2,500 to $7,500 per violation.
Relevance for Debit Card Data: Even if card data is tokenized, personal identifiers tied to transactions may still fall under privacy law requirements.
Banking and Fintech Industry Guidelines
Beyond global compliance mandates, central banks and financial authorities emphasize resilience and vendor accountability.
Third-Party Risk Assessments: Increasingly mandated to ensure suppliers meet minimum cybersecurity standards.
Operational Resilience Requirements: Regulators expect firms to plan for supply chain failures, cyberattacks, and vendor outages.
Focus on Vendor Accountability: Businesses can no longer shift blame to vendors, regulators hold the contracting organization responsible.
Leveraging Technology for Security
Technology has become the backbone of modern security strategies, particularly when it comes to preventing and mitigating third-party debit card security breaches. With the increasing sophistication of cyberattacks and the complexity of vendor ecosystems, relying on traditional manual checks or outdated tools is no longer sufficient. Businesses must harness advanced technologies to stay ahead of risks.
Real-Time Threat Detection and Monitoring
Instead of waiting for quarterly audits or after-incident investigations, real-time threat detection enables businesses to spot red flags as they happen. Continuous monitoring of vendor systems can identify unusual patterns, such as spikes in transaction activity, unauthorized access attempts, or system misconfigurations, well before attackers can exploit them.
According to IBM’s Cost of a Data Breach Report 2024, organizations using real-time monitoring reduced breach costs by nearly 30% compared to those that didn’t.
For financial institutions, early detection is critical; minutes matter when debit card data is at stake.
AI and Machine Learning for Fraud Detection
AI-powered fraud detection tools analyze millions of transactions across multiple channels in real time. These systems use machine learning to identify anomalies, such as unusual transaction volumes, irregular geographies, or suspicious device fingerprints, that might indicate fraudulent activity.
Mastercard reports that AI-driven fraud detection has helped reduce false declines by up to 50%, ensuring security doesn’t come at the cost of customer experience.
Unlike static rule-based systems, AI models continuously learn from evolving fraud patterns, making them more effective against new types of attacks.
Automation in Vendor Risk Management
Vendor risk management (VRM) often fails when it’s treated as a one-time due diligence exercise. Manual spreadsheets, static questionnaires, and annual assessments simply can’t keep pace with today’s threat landscape. Automation addresses these gaps by:
Continuously scoring vendors on their security posture.
Flagging compliance gaps in real time.
Streamlining vendor onboarding with automated security questionnaires and validations.
This proactive, technology-enabled model turns VRM from a reactive, check-the-box process into a dynamic and ongoing defense mechanism.
Auditive: Turning Risk into Resilience
At Auditive, we know that businesses no longer operate in isolation. They function within interconnected digital ecosystems where third-party risks, from payment processors to fintech integrations, are inevitable. Managing these risks effectively requires more than ad hoc checks; it requires visibility, transparency, and control.
That’s why Auditive provides an integrated suite of solutions designed to help organizations mitigate debit card breach risks while maintaining compliance and building customer trust.
Trust Center: A centralized space for sharing and demonstrating security practices transparently to clients and regulators.
Real-Time Monitoring: Continuous visibility into third-party risks, not just annual checklists.
Compliance Insights: Automated tracking of PCI DSS, GDPR, and financial regulations.
Vendor Risk Management Tools: Scalable solutions for onboarding, monitoring, and auditing vendors effectively.
By combining automation, compliance, and transparency, Auditive empowers businesses to turn risk into resilience.
Conclusion
A third-party debit card security breach is more than just an IT failure; it’s a breakdown of trust. As businesses increasingly rely on fintech partners, cloud vendors, and payment processors, the responsibility to manage third-party risks becomes mission-critical.
The path forward requires proactive vendor risk management, continuous monitoring, and transparent communication with customers and regulators. Tools like Auditive’s Trust Center help organizations not only meet compliance requirements but also build long-term trust by showing that security is embedded at every level.
Don’t wait for a breach to expose your vulnerabilities. Strengthen your defenses today with Auditive’s vendor risk management and Trust Center solutions.
Book a demo to see how Auditive can help protect your business against third-party debit card security breaches.
FAQs
Q1. What is a third-party debit card security breach?
A1. It’s when unauthorized access to debit card data occurs through an external vendor’s system rather than the bank or card issuer itself.
Q2. Why are third-party breaches more common today?
A2. The rise of fintech partnerships, outsourced payment processors, and cloud services has expanded the attack surface for cybercriminals.
Q3. What’s the biggest risk for businesses during a debit card breach?
A3. Loss of customer trust, which can damage long-term revenue, often outweighs immediate financial costs.
Q4. How can companies prevent third-party debit card breaches?
A4. By implementing strong vendor risk management, encrypting sensitive data, conducting regular audits, and monitoring vendors continuously.
Q5. How does Auditive help in reducing breach risks?
A5. Auditive provides real-time monitoring, vendor risk management, and the Trust Center to ensure businesses maintain compliance and protect against third-party risks.