What is Data Leakage Prevention (DLP)?
Data doesn’t just sit quietly; it moves, replicates, and sometimes leaks. Whether through misconfigured systems, unsecured third-party access, or an employee’s careless click, sensitive data slipping out of your organization can be costly and catastrophic. That’s where Data Leakage Prevention (DLP) comes in.
DLP isn’t just a technical add-on; it’s a strategic layer of defense built to detect, monitor, and stop data from leaving places it shouldn’t. From intellectual property to customer PII, protecting your data assets requires more than just firewalls and antivirus; it calls for policies, visibility, and controls baked directly into your business workflows.
This guide will break down exactly what DLP is, why it matters, what causes data to leak, and how your organization can take control, before confidential information walks out the door.
Overview
Data Leakage Prevention (DLP) helps prevent unauthorized sharing or exposure of sensitive information.
It protects data in use, in transit, and at rest across endpoints, networks, and cloud platforms.
Common causes of data leaks include misconfigurations, human error, shadow IT, and insider threats.
DLP is distinct from Data Loss Protection, which focuses on recovery after data is lost or deleted.
Tools like Auditive’s Trust Center enable organizations to manage DLP and vendor risk efficiently and continuously.
What is Data Leak Prevention?
Data Leak Prevention, or DLP, refers to the strategies, tools, and practices that help organizations identify, monitor, and prevent the unauthorized exposure or transfer of sensitive information outside approved environments. DLP solutions work across endpoints, networks, cloud services, and email systems to detect risky behavior, enforce data-handling policies, and block potential leaks before they happen.
The goal of DLP is not only to safeguard critical business and customer data from accidental or intentional exposure, but also to maintain compliance with industry regulations such as GDPR, HIPAA, and PCI-DSS. Whether it’s trade secrets, financial data, or personally identifiable information (PII), DLP ensures that only authorized users can access and transmit sensitive assets, and only through approved channels.
By integrating policy enforcement with real-time visibility, DLP acts as a proactive control layer in the broader cybersecurity and risk management ecosystem. It’s a critical shield against both insider threats and external attacks that target data as the ultimate prize.
Why Is Data Leak Protection Important?
Leaked data is more than a technical incident; it’s a business crisis. Whether it’s customer PII, financial reports, or internal strategy docs, exposure of sensitive information can lead to long-lasting operational and reputational damage.
Data leak protection (DLP) helps prevent sensitive data from slipping through the cracks, whether through misconfigurations, insider threats, or third-party mishandling. In a world where digital sprawl is growing and cybercrime is increasingly opportunistic, DLP isn’t optional, it’s essential.
Here's why it matters:
Regulatory compliance: Frameworks like GDPR, HIPAA, and CCPA require strict data protection, and violations can lead to multi-million dollar fines.
Reputation and trust: A single leak can erode years of customer trust, kill deals, and hurt investor confidence.
Financial risk: Breaches lead to legal costs, incident response, and revenue loss. IBM pegs the average cost of a breach at $4.45 million.
Cybercriminal efficiency: Leaked data is a shortcut for attackers. They skip reconnaissance and move straight to exploitation.
Complex IT environments: Remote work, BYOD, and SaaS growth have blurred the data perimeter, making traditional security controls less effective.
In 2021 alone, UpGuard researchers found that 47 organizations were unknowingly leaking sensitive data via Microsoft PowerApps, a simple misconfiguration that exposed tens of millions of records.
That’s the cost of not having DLP embedded into your ecosystem: even one oversight can lead to significant exposure.
3 Types of Data Leakage
Data leakage can take many forms, and understanding the various types is key to designing effective prevention strategies. While some incidents are purely accidental, others are deliberate and highly damaging.
1. Accidental Data Leaks
These are the most frequent and often the most overlooked. They occur when employees unintentionally share sensitive information with the wrong recipients, like sending an email to the wrong person due to auto-complete errors or attaching the wrong file. While unintentional, the consequences can be just as serious as malicious breaches.
2. Insider Threats
Also known as malicious internal leaks, these involve employees or contractors who knowingly exfiltrate confidential data. Motivations range from personal grievances to financial incentives from competitors or threat actors. Methods can include copying files to USB drives, emailing confidential documents externally, or even photographing sensitive screens or documents.
3. External Attacks via Digital Channels
Cybercriminals increasingly exploit business communication platforms beyond just email, such as messaging apps, cloud storage, and collaborative tools. These malicious electronic leaks often begin with phishing or spoofing attacks that trick employees into clicking harmful links or sharing credentials, leading to unauthorized access and data theft.
Each type of data leak requires a different mitigation approach, ranging from user training and access controls to DLP solutions that monitor and restrict data movement based on sensitivity and context.
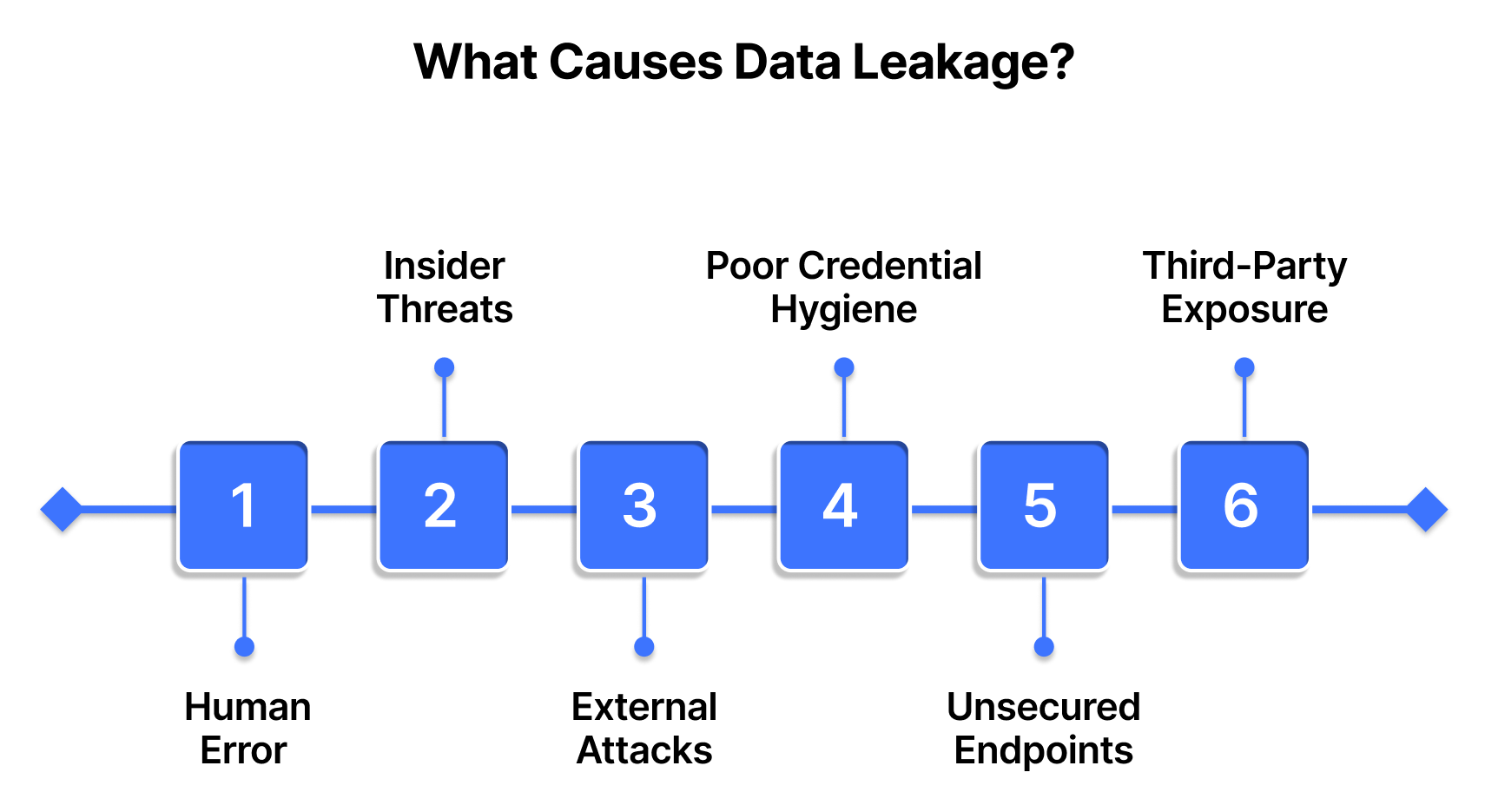
What Causes Data Leakage?
Data leakage can stem from a variety of sources, many of which are avoidable with the right controls and awareness. Here are some of the most common culprits:
1. Human Error
Simple yet frequent mistakes, like misdirected emails or attaching the wrong document, can result in unintended data exposure. Ongoing training and awareness initiatives are essential to minimize these risks.
2. Insider Threats
Employees, contractors, or trusted partners may knowingly or inadvertently leak sensitive data. Limiting access based on roles and monitoring activity through DLP tools can help detect and prevent insider-driven incidents.
3. External Attacks
Cybercriminals often exploit security vulnerabilities to extract confidential data. Without regular patching, strong perimeter defenses, or threat detection, organizations remain vulnerable to these breaches.
4. Poor Credential Hygiene
Reused or weak passwords remain an easy target for attackers. Enforcing strong password policies and implementing multi-factor authentication (MFA) significantly reduces this risk.
5. Unsecured Endpoints
Lost or stolen laptops, phones, and USB drives can lead to serious data leaks if not encrypted or remotely manageable. Device control policies and endpoint encryption are critical to keeping sensitive data secure.
6. Third-Party Exposure
Vendors and partners with network or data access can become weak links if their security posture is lacking. Performing vendor risk assessments and embedding data protection requirements into contracts is a must.
Protecting your data starts with understanding the risks, and mitigating them early to prevent costly consequences later.
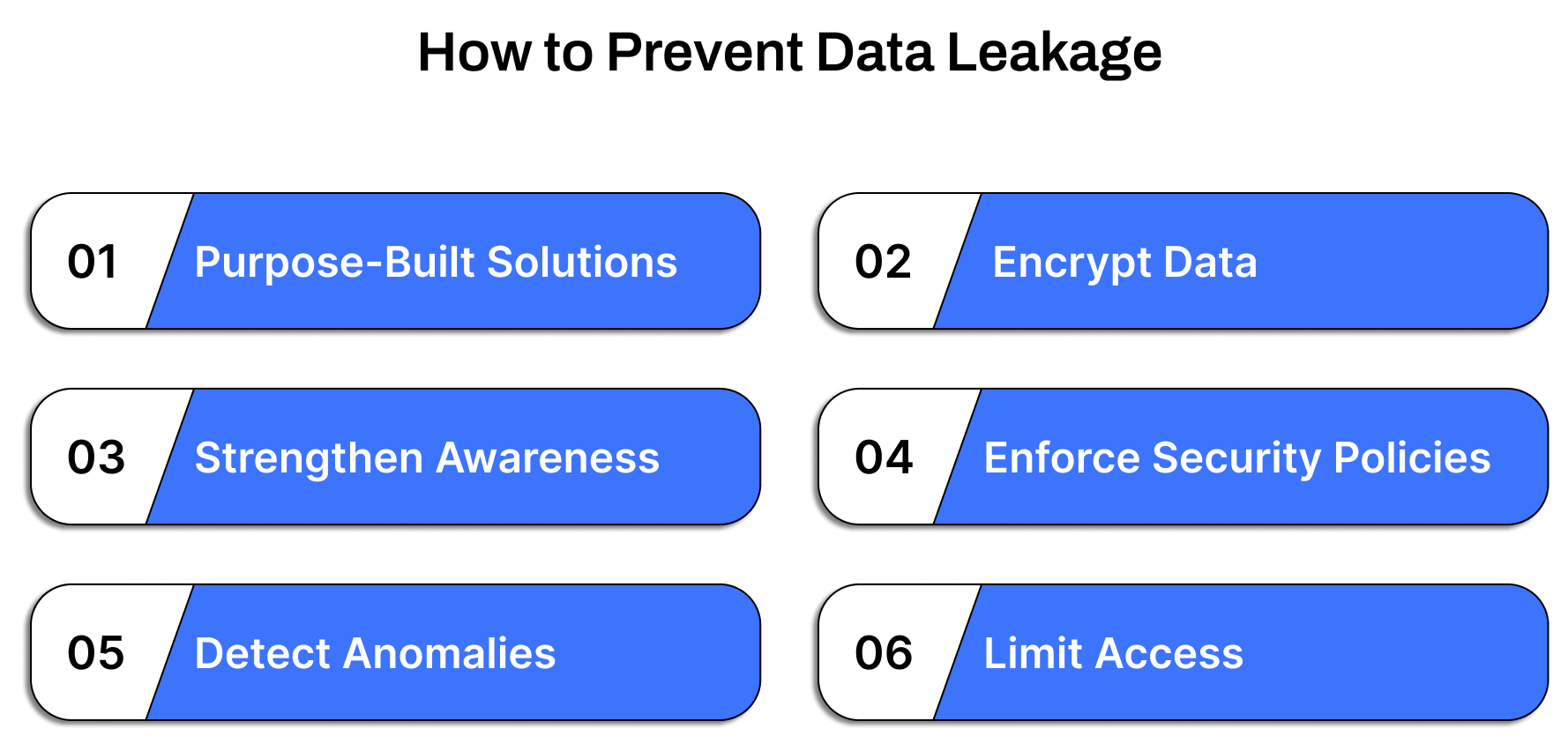
How to Prevent Data Leakage
Preventing data leakage requires more than a one-size-fits-all solution; it demands a layered, strategic approach that spans technology, policies, and human behavior. Here’s how to build an effective defense:
1. Deploy Purpose-Built DLP Solutions
Start with dedicated Data Leakage Prevention (DLP) tools that identify and control the movement of sensitive data across endpoints, emails, cloud apps, and networks. These solutions inspect content, enforce rules, and automatically block or quarantine high-risk transfers, helping reduce the chances of accidental or intentional data exposure.
2. Encrypt Data at Every Stage
Encryption is a non-negotiable safeguard. Whether data is in motion (e.g., email, file sharing) or at rest (e.g., databases, cloud storage), encryption ensures that stolen or intercepted data remains unreadable without proper credentials. Apply strong encryption standards across all critical systems.
3. Strengthen Employee Awareness
Technology alone can’t close the gap, people need to understand the stakes. Deliver ongoing security awareness training that covers data handling best practices, real-world phishing scenarios, and how to spot suspicious activity. Well-informed employees are your first line of defense.
4. Define and Enforce Security Policies
Establish clear guidelines for data classification, handling, and sharing. Document who is allowed to access what types of data, through which channels, and under which conditions. Policies should also define the disciplinary consequences for violations to encourage compliance.
5. Monitor and Detect Anomalies
Use network monitoring and intrusion detection tools to gain visibility into data flows and spot irregular behavior in real time. Anomalies, such as unusual data transfers or access attempts, can indicate early signs of a leak or breach, enabling faster containment.
6. Limit Access with Precision
Adopt a least privilege model to ensure employees only access data essential to their roles. Combine role-based access controls with regular audits to identify and remove outdated or unnecessary permissions, especially when employees change roles or leave the organization
Differences Between Data Leak Prevention and Data Loss Protection
Although often used interchangeably, Data Leak Prevention (DLP) and Data Loss Protection serve distinct roles in a comprehensive data security strategy.
At its core, Data Leak Prevention focuses on preventing sensitive data from leaving your organization inappropriately, whether it’s through emails, uploads, or insider threats. It’s about controlling access, monitoring usage, and stopping unauthorized disclosures before they happen.
On the other hand, Data Loss Protection is about ensuring data remains available and recoverable, even in the face of unexpected failures like hardware malfunctions, accidental deletions, or ransomware attacks. It’s more about durability and continuity than access control.
| Feature | Data Leak Prevention | Data Loss Protection |
|---|---|---|
| Primary Focus | Preventing unauthorized disclosure of sensitive data | Ensuring data remains available and recoverable |
| Key Functions | Monitoring, detecting, and blocking data in use, in transit, or at rest | Backup, replication, and data recovery processes |
| Use Areas | Emails, endpoints, network traffic, cloud apps | Storage systems, backup servers, disaster recovery plans |
| Technologies | Content inspection, contextual analysis, policy enforcement | Backup software, encryption, snapshots, and replication tools |
| Risk Addressed | Data breaches, regulatory violations, insider threats | Data loss due to accidents, failures, or cyberattacks |
| Compliance Support | Helps meet GDPR, HIPAA, PCI DSS by controlling data flow | Supports business continuity and disaster recovery compliance |
| Typical Use Case | Blocking outgoing emails with unencrypted credit card numbers | Restoring systems after a ransomware attack or server crash |
Together, these approaches form a defense-in-depth strategy. DLP keeps sensitive data from slipping out, while Data Loss Protection ensures it’s always there when you need it.
Conclusion
Data leakage isn’t just a technical glitch; it’s a business-critical risk that can jeopardize compliance, reputation, and customer trust. As data volumes grow and digital ecosystems expand, organizations must go beyond perimeter defenses and adopt a proactive approach to safeguarding sensitive information.
This is where effective Vendor Risk Management and robust Data Leak Prevention (DLP) strategies converge. Ensuring your vendors uphold the same data protection standards as your internal teams is no longer optional; it’s essential.
Auditive helps you take control. With real-time insights through its Trust Center, automated vendor assessments, and continuous monitoring, Auditive empowers you to prevent leaks before they happen, across both internal and third-party environments.
Ready to simplify DLP and vendor risk management? Schedule a demo with Auditive and start building a more secure, transparent ecosystem today.
FAQs
Q1. What is the difference between data leakage and data loss?
A1. Data leakage refers to unauthorized exposure or sharing of sensitive data, while data loss means the permanent or temporary unavailability of data due to incidents like deletion, hardware failure, or ransomware.
Q2. What are the most common causes of data leakage?
A2. Data leakage is often caused by misconfigured cloud services, unmonitored SaaS tools (shadow IT), insider threats, weak access controls, or accidental email disclosures.
Q3. How does Data Leakage Prevention (DLP) work?
A3. DLP solutions monitor and control sensitive data across endpoints, networks, and storage. They block unauthorized access, detect suspicious behavior, and enforce encryption or policy-based restrictions.
Q4. Why is DLP important in vendor risk management?
A4. Vendors often have access to sensitive company or customer data. Without proper controls, they can become a weak point. DLP ensures vendors follow secure data handling practices and comply with your organisation’s privacy standards.
Q5. Can DLP help with regulatory compliance?
A5. Yes. DLP supports compliance with frameworks like GDPR, HIPAA, and PCI DSS by ensuring data flow is controlled, monitored, and secured according to regulatory requirements.