Understanding Attack Surface Management vs Vulnerability Management
Security gaps don’t always begin with major flaws; they often emerge from overlooked assets, misconfigured systems, or outdated tools that silently expand an organization’s exposure to risk. As digital infrastructures grow more complex, pinpointing where threats can enter becomes just as important as identifying what vulnerabilities exist within the system.
This is where two critical yet distinct security strategies come into focus: Attack Surface Management (ASM) and Vulnerability Management (VM). While both aim to reduce risk, they operate in fundamentally different ways. Understanding the contrast between the two, and how they complement each other, is key to building a security program that’s both proactive and resilient.
Overview
Attack Surface Management (ASM) maps what’s externally exposed.
Vulnerability Management (VM) identifies weaknesses within assets.
ASM is proactive; VM is diagnostic, and both are complementary.
Combining both provides stronger risk reduction and faster remediation.
Auditive unifies these practices with automation, a Trust Center, and Vendor Risk Management tools.
What Is Attack Surface Management?
Attack Surface Management, or ASM, is the ongoing process of identifying and reducing all possible entry points that attackers could exploit across an organization’s digital environment. These entry points include known and unknown assets, like websites, APIs, cloud services, IoT devices, and unmanaged systems.
The core goal of ASM is visibility. It helps security teams understand what’s exposed externally, including assets added without IT’s knowledge (often called shadow IT). Each new digital asset expands the attack surface, requiring continuous monitoring to minimize risk.
By identifying potential attack vectors in real time, ASM enables organizations to address issues before they become incidents, especially in fast-moving, cloud-heavy environments where misconfigurations are common.
What is Vulnerability Management?
Vulnerability Management, or VM, is a structured security process focused on identifying, assessing, and addressing weaknesses in an organization’s known assets, such as servers, applications, databases, and network components. These vulnerabilities may include coding flaws, outdated software, or misconfigurations that create entry points for attackers.
The process relies heavily on automated vulnerability scanners that continuously evaluate systems, flagging risks and offering guidance for remediation. It’s not just about detection, VM prioritizes vulnerabilities based on risk severity, often using scoring models like CVSS, so that teams can act quickly on issues with the highest potential impact.
Effective VM helps security teams eliminate gaps before they’re exploited. By applying patches, reconfiguring systems, or isolating affected components, organizations reduce exposure to preventable threats. Given that a significant portion of breaches stem from known but unpatched vulnerabilities, VM plays a critical role in minimizing avoidable incidents and strengthening baseline security.
Difference Between Attack Surface Management and Vulnerability Management
Attack Surface Management (ASM) and Vulnerability Management (VM) both aim to strengthen cybersecurity, but their methods, scope, and outcomes differ significantly. Understanding these differences is critical for security leaders aiming to build a layered, risk-aware defense strategy.
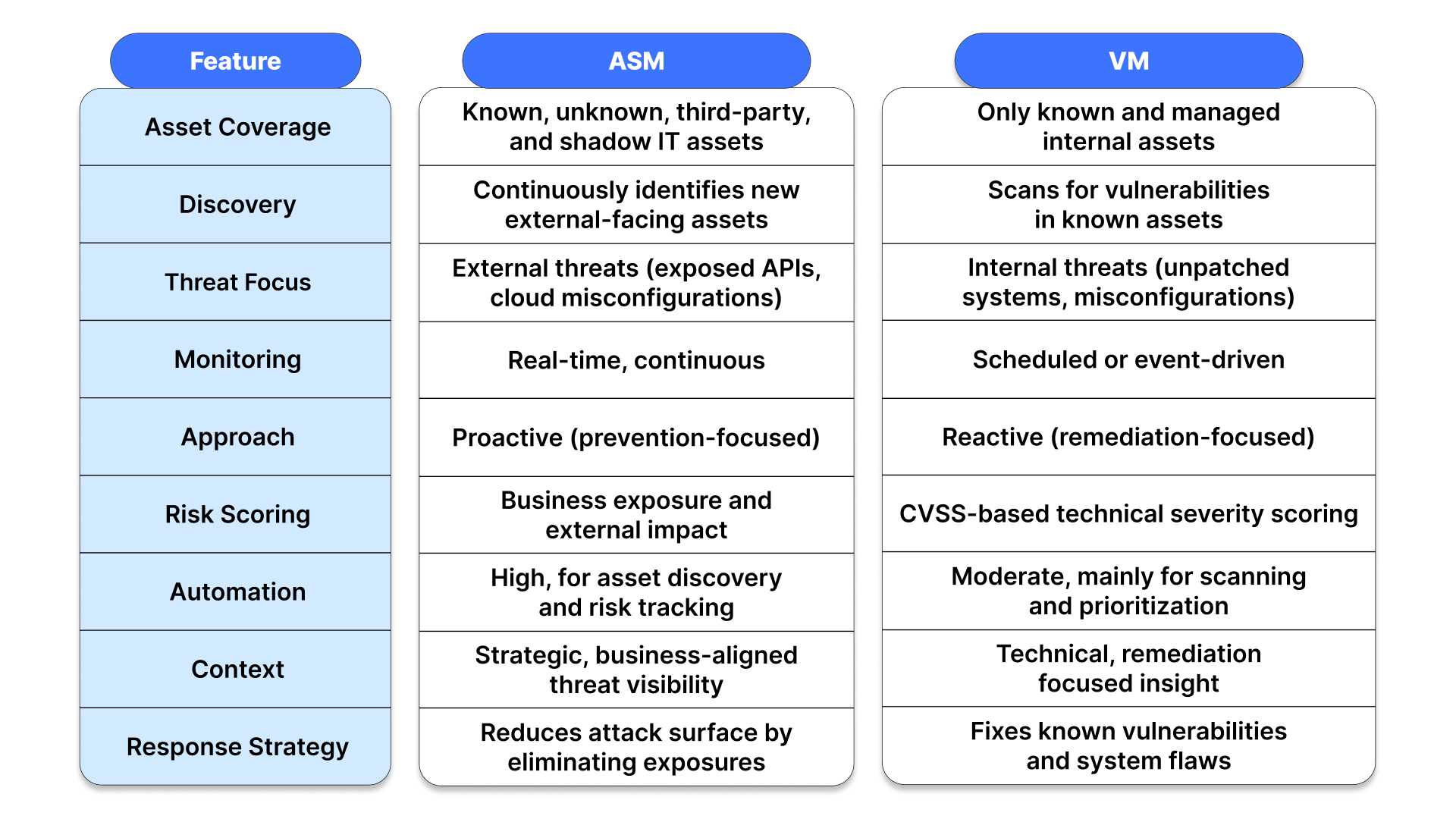
1. Asset coverage
ASM provides broad visibility across known, unknown, and third-party digital assets, including shadow IT, exposed APIs, and cloud services. Its job is to surface anything that could widen an organization's attack surface. In contrast, VM focuses on vulnerabilities within known, managed infrastructure, like servers, endpoints, and internal applications, often governed by IT or security teams.
2. Discovery and visibility
ASM is discovery-first. It continuously maps external-facing assets, even those that weren’t previously cataloged. This is especially vital in dynamic environments like cloud-native architectures, where misconfigurations or overlooked services are common. VM, on the other hand, inspects known assets for previously identified vulnerabilities, such as missing patches or misconfigurations. It doesn’t reveal new surfaces, but it ensures the existing ones are secure.
3. Threat focus
ASM prioritizes external threats, risks originating from exposed systems accessible via the internet. These include misconfigured cloud buckets, unsecured web apps, and orphaned domains. VM addresses internal weaknesses, often involving outdated software, system flaws, or poor configurations, issues that attackers can exploit post-breach.
4. Monitoring cadence
ASM operates in real-time, maintaining continuous surveillance of the external attack surface as it evolves. VM is more event-driven or periodic, typically performed during updates, audits, or on a scheduled basis. While some advanced VM tools offer continuous scanning, they are often less agile compared to ASM’s always-on model.
5. Proactive vs. reactive approach
ASM is proactive by design. It identifies and reduces potential entry points before they can be exploited. VM is reactive, focused on detecting and fixing existing weaknesses that could be targeted. This difference in philosophy, prevention vs. mitigation, defines their roles in the security lifecycle.
6. Risk scoring methodologies
Risk in ASM is evaluated based on business impact, exposure level, and potential for external exploitation. It prioritizes assets by how valuable they are to the business and how visible they are to attackers. VM typically uses standardized scoring systems like CVSS, which rank vulnerabilities based on severity, exploitability, and impact.
7. Automation and scalability
ASM depends heavily on automation to continuously scan for new digital assets and assess their risk. Manual tracking of such assets at scale is impractical. VM uses automation primarily for scanning and prioritization, but patching and remediation often remain human-driven.
8. Context and insight
ASM delivers high-level visibility aligned with business risk. It shows how an attacker might use an exposed asset and what that exposure could mean for the organization as a whole. VM offers detailed technical insight, helpful for remediation but less strategic in its outlook.
9. Response strategy
ASM reduces exposure by eliminating or securing risky assets. It’s about closing doors before attackers find them. VM focuses on hardening the internal environment, patching vulnerabilities, fixing configurations, and addressing system-level flaws that are already known.
Quick Comparison: ASM vs. VM
Many organizations struggle to bring both external and internal threat monitoring under one unified operational framework. That’s where Auditive plays a vital role.
Auditive brings internal and external threat management under one roof. Through its unified Trust Center, it supports both attack surface management and vulnerability management, helping teams detect exposures, prioritize risks, and respond faster.
By combining vendor risk management, asset visibility, and continuous monitoring, Auditive simplifies risk control, eliminating silos and strengthening security posture across the board.
How Attack Surface Management and Vulnerability Management Work Together
Attack Surface Management (ASM) and Vulnerability Management (VM) are not competing strategies; they’re complementary layers of a complete security posture. Each addresses a different dimension of risk, and when used together, they create a stronger, more responsive defense framework.
ASM focuses on identifying all external-facing digital assets, those most likely to be targeted by attackers. VM, in contrast, zeroes in on known systems to detect and remediate internal weaknesses.
Together, they offer:
Full-spectrum visibility: ASM discovers shadow IT, exposed APIs, and unknown external assets.
Precision diagnostics: VM identifies software flaws, misconfigurations, and patching gaps.
Stronger compliance posture: Many regulations require both asset mapping and vulnerability scanning.
Proactive threat response: ASM highlights unknown risks; VM enables structured remediation.
Minimized attack windows: The overlap ensures fewer blind spots and faster response times.
Managing both ASM and VM under one unified approach ensures external threats and internal vulnerabilities are handled in tandem.
Auditive enables this integration by combining real-time asset intelligence, vendor exposure tracking, and continuous vulnerability insights, giving teams the visibility and control they need to act decisively.
Best Practices for Implementing Both Strategies
A strong security posture requires more than just tools; it demands precision in execution. When combining Attack Surface Management and Vulnerability Management, organizations need structured, ongoing practices that align with evolving risks.
1. Prioritize what matters most
Not all assets carry the same weight. Begin by identifying critical infrastructure, data stores, and systems that, if compromised, would cause the most damage. Prioritize vulnerabilities not just by severity scores, but by context: likelihood of exploitation, exposure level, and potential business impact. This targeted approach ensures resources are spent where they matter most.
2. Monitor continuously, not occasionally
Point-in-time assessments no longer suffice. Security teams must implement continuous discovery and monitoring to track every internet-facing asset, shadow IT element, and change in configuration. This visibility is crucial for both attack surface awareness and timely vulnerability detection. It’s not about reacting to yesterday’s threats, it’s about detecting and mitigating emerging ones before they escalate.
3. Build a tight feedback loop for incident response
When gaps are detected, whether through ASM tools or vulnerability scans, swift remediation is key. Organizations should maintain a clear incident response process that links detection to action, supported by ownership, timelines, and escalation paths. Don’t just patch, verify the fix, assess for collateral exposure, and feed the lessons back into your program.
Auditive empowers security and compliance teams to bring structure to these processes. With capabilities that span asset inventory, risk scoring, and real-time monitoring, the platform enables teams to act quickly, reduce manual tracking, and maintain oversight across both known and unknown exposures.
Strengthening Risk Posture with Auditive
Managing your external attack surface while staying ahead of internal vulnerabilities requires clarity, coordination, and real-time insights. Auditive brings these elements together into a unified, intelligent platform, turning reactive security practices into a proactive trust strategy.
With Auditive, teams can:
Discover and monitor dynamic assets across your digital footprint
Prioritize vulnerabilities based on business context and exploitability
Automate workflows for faster, policy-aligned remediation
Extend oversight to vendors and third parties with built-in Vendor Risk Management
Visualize risk posture through an integrated Trust Center
By consolidating visibility and control in one place, Auditive reduces noise, sharpens focus, and empowers security teams to act on what matters.
Conclusion
Attack Surface Management and Vulnerability Management are both essential, but neither is complete on its own. One identifies what’s exposed, the other evaluates how exposed it is. To stay resilient, organizations need a cohesive strategy that connects both, across systems, teams, and third-party relationships.
Auditive helps enterprises close this gap. With centralized visibility, contextual insights, and automation across both internal and external surfaces, Auditive ensures risk is not only detected but acted on, intelligently and consistently. Its Trust Center provides a clear view of your overall security posture, while Vendor Risk Management ensures third-party exposures don’t become blind spots.
Ready to take control of your risk surface?
Get in touch with Auditive to streamline your security strategy today.
FAQs
Q1. Is Attack Surface Management a replacement for Vulnerability Management?
A1. No. ASM and VM serve different purposes. ASM identifies what’s exposed; VM assesses how vulnerable those exposures are. Both are required for complete coverage.
Q2. How does Auditive support both ASM and VM strategies?
A2. Auditive centralizes asset discovery, risk prioritization, and remediation tracking, while integrating external (ASM) and internal (VM) data into one platform.
Q3. Why is Vendor Risk Management important in this context?
A3. Vendors often expand your attack surface. Auditive’s Vendor Risk Management ensures third-party risks are tracked, evaluated, and aligned with internal controls.
Q4. Can the Trust Center be customized for specific business units or compliance goals?
A4. Yes. Auditive’s Trust Center provides tailored dashboards and controls that align with enterprise policies, regulatory frameworks, and stakeholder needs.
Q5. What’s the first step to adopting Auditive’s platform?
A5. Start by scheduling a risk assessment or demo to map your current posture and explore how Auditive can streamline and elevate your ASM and VM strategies.