How to Create a Vendor Management Policy
Third-party vendors can drive innovation or introduce serious risk. Without a clear framework to manage them, it’s easy for performance to slip, compliance gaps to grow, and security issues to go unnoticed.
A vendor management policy brings structure to this chaos. It outlines how your organization evaluates, selects, monitors, and offboards vendors, so nothing falls through the cracks. Done right, it’s not just a policy, it's a control mechanism for resilience, accountability, and more intelligent decision-making.
This guide walks you through what a vendor management policy is, why it matters, how to build one, and what best practices to follow to make it effective.
TL;DR
A vendor management policy outlines how your organization selects, manages, and offboards third-party vendors to reduce risk and ensure compliance.
Key components include objectives, scope, roles and responsibilities, vetting procedures, performance metrics, compliance requirements, and enforcement.
Classifying vendors by risk level and setting clear communication and escalation paths improves oversight and accountability.
Regular reviews and updates ensure your policy stays relevant and effective as risks and regulations evolve.
Third-party risk management (TPRM) platforms like Auditive’s Trust Center streamline vendor risk management and help enforce your policy at scale.
What is a vendor management policy?
A vendor management policy (VMP) is a formal, strategic document that defines how your organization identifies, assesses, and manages third-party and fourth-party vendors, especially those with the potential to impact security, compliance, or operations.
At its core, a VMP is a risk control. It gives teams a structured way to prioritize vendor relationships based on criticality and exposure, applying consistent oversight across every stage of the vendor lifecycle, from onboarding to offboarding.
The policy typically includes:
Vendor risk classification and prioritization
Security and compliance standards (aligned with frameworks like ISO 27001, SOC 2, or GDPR)
Performance metrics and SLAs
Vendor liability and breach response terms
Review cycles and reassessments
Contract termination procedures tied to risk or non-compliance
Beyond documentation, a strong vendor management policy acts as a blueprint for cross-functional alignment, helping legal, IT, security, and procurement teams work from the same playbook when engaging with external partners.
Why do you need a vendor management policy?
Vendor-related risks are often harder to spot than internal ones, but they can be just as damaging. The more vendors you rely on, the more potential points of entry for security threats, compliance failures, or service disruptions.
Regulators are paying attention, too. A Venminder report found that 69% of organizations have faced increased scrutiny from auditors and regulatory bodies around their third-party oversight.
And when things go wrong, the cost is steep. According to the Ponemon Institute and IBM, third-party data breaches increase breach costs by over $370,000, bringing the average total to $4.29 million.
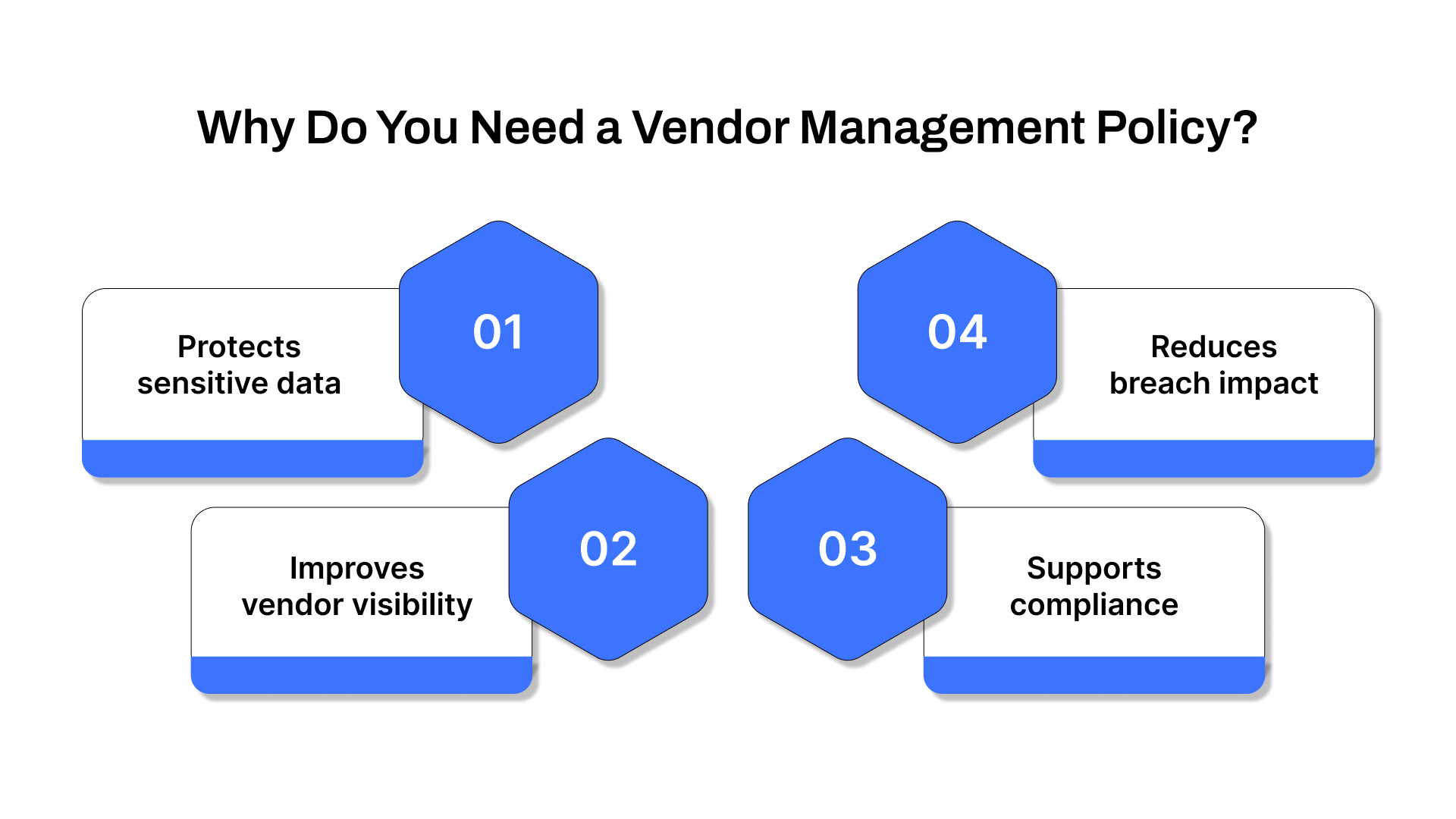
A well-defined vendor management policy helps you get ahead of these risks. Here’s how:
Protects sensitive data
Vendors often handle business-critical processes, which means they also access customer or operational data. A policy enforces strict access controls and handling procedures from the outset.
Improves vendor visibility
Understanding each vendor’s security posture isn’t optional. A VMP ensures structured reviews, so you’re not in the dark about who has access to what, or how well they’re protecting it.
Supports compliance
A documented policy aligns vendor oversight with industry regulations. It demonstrates that your organization takes risk seriously and meets due diligence expectations.
Reduces breach impact
If a vendor-related incident occurs, a clear policy helps contain the damage, with predefined protocols for escalation, liability, and exit.
A strong vendor management policy isn’t just about control; it’s about clarity. It ensures that vendor risk is measured, monitored, and never left to chance.
How to create a vendor management policy
A vendor management policy isn’t a generic document; it’s a strategic control mechanism. To make it effective, it needs to be tailored, structured, and built to evolve with your business. Here’s how to create one that works in the real world:
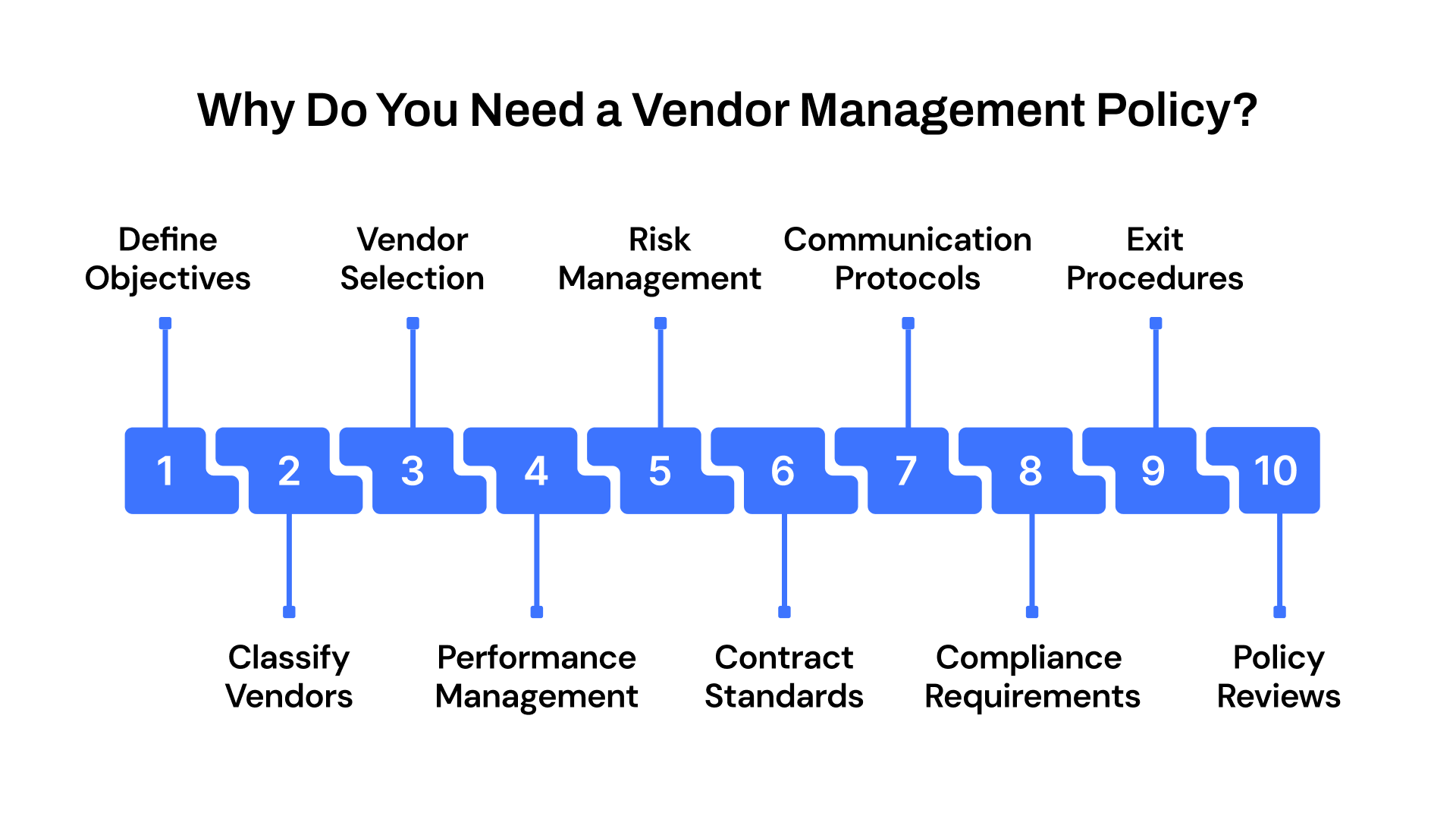
Step 1. Define clear objectives and scope
Start by outlining what your vendor management policy is designed to accomplish. Objectives typically include improving vendor performance, minimizing third-party risk, ensuring compliance with regulatory standards, and streamlining vendor operations.
Define:
Which vendors are included, all third-party vendors, or only those classified as high-risk or critical?
What outcomes are expected, such as reduced security incidents, audit readiness, or better contract terms?
A clear scope ensures the policy is relevant and actionable across departments.
Step 2. Identify and classify vendors
Before enforcing controls, understand who your vendors are and what role they play. Categorizing vendors helps prioritize oversight based on impact and risk.
Common categories include:
Strategic vendors: essential to your core operations (e.g., infrastructure providers, major SaaS platforms)
Operational vendors: support daily functions (e.g., office management, logistics)
Transactional vendors: ad hoc or low-risk suppliers (e.g., event vendors, temporary staffing)
Classification enables differentiated risk treatment and optimized resource allocation.
Step 3. Standardize vendor selection and onboarding
A structured selection process reduces inconsistency and subjectivity. Your policy should document how vendors are chosen and vetted before engagement.
Key components:
Selection criteria such as financial stability, security practices, certifications, and industry reputation
RFP/RFI process for high-value or strategic contracts
Due diligence covering regulatory compliance, data security protocols, and service quality
Reference checks and scoring frameworks to quantify vendor evaluations
This process ensures vendors align with your performance, compliance, and risk expectations from day one.
Step 4. Define vendor performance management
Once a vendor is onboarded, continuous oversight is critical. Your policy should outline how performance is measured, reported, and remedied.
Include:
Performance metrics (e.g., SLA adherence, response time, data accuracy)
Scorecards or dashboards to track trends
Audit and review cadence (quarterly or bi-annually based on vendor tier)
Corrective action plans for underperformance or non-compliance
This encourages accountability and continuous improvement.
Step 5. Implement a risk management framework
Every vendor introduces risk, whether through data access, service delivery, or compliance. Your policy should establish how these risks are assessed, monitored, and mitigated.
Include:
Initial risk assessments based on impact and likelihood
Risk tiering to set differentiated oversight levels
Third-party security audits for high-risk vendors
Contingency planning with documented backup vendors or failover procedures
This framework helps your organization stay resilient, even when external partners fail.
Step 6. Define contract management standards
Contracts are the foundation of vendor governance. Your policy should establish consistent contract practices that protect your organization legally and operationally.
Cover:
Standardized contract templates including SLAs, data handling terms, exit clauses, and liability
Internal approval workflows involving legal, security, procurement, and finance
Contract review timelines to keep terms aligned with evolving needs
A clear contract framework reduces ambiguity and enforces shared accountability.
Step 7. Establish communication and escalation protocols
Effective communication is key to vendor relationships. The policy should define when and how your team interacts with vendors, especially when issues arise.
Include:
Regular meeting schedules to review performance, resolve issues, and share updates
Defined points of contact on both sides
Escalation paths for unresolved issues
Reporting expectations for compliance or security-related incidents
This ensures timely resolution and transparency across all engagements.
Step 8. Integrate regulatory and compliance requirements
Vendors often operate within your compliance boundaries, especially those handling sensitive data. Your policy must reflect this.
Include:
Compliance checklists for applicable laws (e.g., GDPR, HIPAA, PCI-DSS)
Documented audit rights and reporting expectations
Frequency of compliance reviews based on vendor risk tier
This protects your organization from shared liability and reputational harm.
Step 9. Define termination and exit procedures
Vendor offboarding is just as important as onboarding. A structured exit plan reduces the risk of operational disruption or data exposure.
Your policy should define:
Conditions for termination like breach of contract, non-performance, or business realignment
Required notice periods
Exit strategies include knowledge transfer, data return/deletion protocols, and transition support
Well-documented exits reduce risk and ensure business continuity.
Step 10. Schedule regular policy reviews
Your business, technology stack, and regulatory landscape will evolve, so should your policy. Set a cadence to review and revise it regularly.
Recommend:
Annual reviews or ad-hoc updates following major incidents or regulatory changes
Cross-functional input from legal, security, compliance, and operations
Version control and documented changes to ensure transparency
Keeping the policy current ensures it remains useful, not just archived.
Creating a vendor management policy is not about adding red tape; it’s about establishing a framework for making smarter decisions, responding more quickly, and mitigating risk. Done right, it empowers your teams, clarifies expectations, and creates a foundation for stronger vendor relationships across the board.
The policy you create today should not just help your team stay compliant; it should help your organization stay ahead.
Vendor management policy best practices
There’s no one-size-fits-all vendor management policy, and that’s the point. Your policy should reflect your organization’s specific risk tolerance, industry obligations, and operational structure. That said, some principles apply universally.
Here are six best practices to anchor your approach:
1. Plan for vendor failures before they happen
Even trusted vendors can fail, whether due to outages, contract breaches, or unexpected shutdowns. Build contingency into your policy by identifying which business functions each vendor supports and outlining specific internal response plans. Assign ownership to the right teams so there’s no confusion when speed matters.
2. Assign clear vendor ownership
Every critical vendor needs a clear point of contact inside your organization. Appointing a dedicated vendor manager for high-risk or IT-related vendors ensures accountability for oversight, communication, and issue escalation.
3. Apply consistent standards across all vendors
It’s tempting to focus only on your most critical vendors, but gaps often appear further down the supply chain. Your policy should hold all vendors to the same baseline requirements, regardless of size or perceived importance. This promotes fairness, reduces oversight gaps, and simplifies enforcement.
4. Keep the policy focused
Your vendor management policy should be broad enough to set direction, and concise enough to be actionable. Avoid bloated documents. Aim for 5–7 pages that clearly define responsibilities, requirements, and governance workflows without burying teams in complexity.
5. Review and revise annually
A policy created once and never updated becomes a liability. Build in a cadence to review your vendor management policy at least annually, or more often when new risks, technologies, or regulations emerge. Lessons learned from vendor incidents should directly inform updates.
6. Cover the six core pillars of vendor management
A strong vendor management policy includes controls and guidance across six foundational areas:
Vendor selection and procurement
Risk assessment and tiering
Due diligence and background checks
Contractual standards and SLAs
Reporting requirements for compliance and violations
Ongoing monitoring and reassessment
A clear policy doesn’t just reduce risk, it drives accountability, improves vendor performance, and gives you full visibility into who you're working with and why.
What to include in your vendor management policy?
There’s no universal template for a vendor management policy, and there shouldn’t be. Each organization’s vendor landscape, risk profile, and regulatory obligations are different. However, a strong policy always includes certain foundational elements.
Here’s a breakdown:
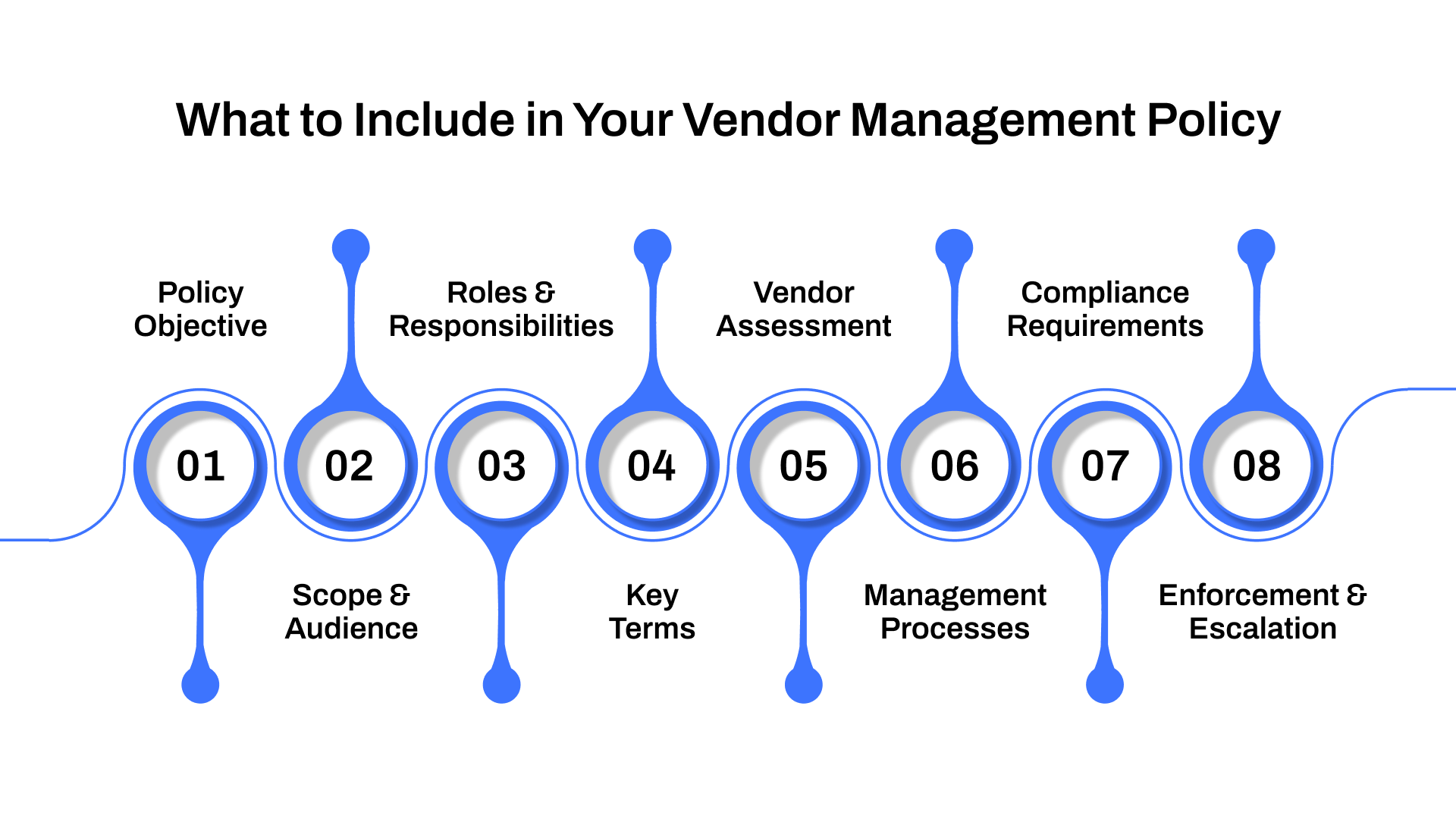
1. Purpose
State the objective of the policy
Emphasize risk management, data security, and compliance
Example:
“This Vendor Management Policy outlines the requirements for engaging, managing, and terminating third-party vendors to protect organizational data and operations from vendor-related risks.”
2. Scope and audience
Define covered vendor types (third-party, fourth-party, etc.)
List impacted departments (HR, IT, Legal, etc.)
Clarify internal audiences subject to the policy
3. Roles and responsibilities
Assign vendor manager(s)
Define roles for security, compliance, procurement, legal
Identify policy review owner
4. Definitions
Clarify key terms (e.g., critical vendor, data breach, fourth-party)
Standardize language across teams
5. Vendor assessment and vetting process
Classify vendors by risk tier
List due diligence requirements
Set assessment frequency
Align with relevant regulations
6. Vendor management processes
Define onboarding and offboarding steps
Set contract and SLA expectations
Establish performance tracking (KPIs, reviews)
Include incident response and access revocation
7. Vendor compliance requirements
Specify required frameworks (ISO 27001, SOC 2, etc.)
Set audit/reporting frequency
List acceptable evidence formats
Define corrective action protocols
8. Enforcement and escalation
State grounds for termination
Outline escalation procedures
Define sanctions and internal response steps
Get these foundational elements right, and your policy becomes more than a formality. It becomes a competitive strength.
How Auditive helps
Writing a vendor management policy is step one. Enforcing it at scale? That’s where Auditive excels.
Auditive gives you a real-time view of seller risk across your entire vendor network, helping you:
Understand 80% of your risk exposure in seconds
Evaluate vendors using industry-specific frameworks
Speed up security reviews with 35% higher seller response rates
Onboard 4x faster through seamless workflow integrations
From onboarding to offboarding, Auditive simplifies third-party risk management — continuously and confidently.
Conclusion
A strong vendor management policy lays the groundwork for consistent, secure, and scalable vendor risk management. But policy alone isn’t enough; visibility and enforcement are key.
Auditive’s Trust Center helps bring your policy to life by centralizing vendor data, automating compliance workflows, and reducing third-party risk in real time.
Want to make vendor oversight effortless?
Let’s talk about how Auditive can help operationalize your vendor management strategy and build lasting trust.
FAQs
Q1. What is a vendor management policy?
A1. It’s a formal document that defines how your organization handles the selection, oversight, and termination of third-party vendors. It helps mitigate risks, enforce compliance, and maintain operational integrity.
Q2. Why is a vendor management policy important?
A2. Vendors often have access to sensitive systems and data. A structured policy protects your organization from data breaches, service disruptions, and compliance violations, especially as regulatory scrutiny increases.
Q3. What should be included in a vendor management policy?
A3. Core sections include the policy’s purpose, scope, stakeholder responsibilities, vendor risk assessments, contract and performance management processes, compliance standards, and enforcement actions.
Q4. How often should the policy be reviewed?
A4. At minimum, annually, or whenever there are significant changes to vendor relationships, internal processes, or regulatory requirements.
Q5. How can Auditive help with vendor risk management?
A5. Auditive’s Trust Center centralizes vendor data, automates compliance checks, and provides real-time visibility into third-party risk, making your policy easier to enforce and your vendor ecosystem more secure.