6 Tips for Managing Third-Party Risk in Cloud Computing
Cloud computing has fundamentally reshaped how enterprises operate, enabling faster scaling, lower infrastructure costs, and access to specialized capabilities. As businesses adopt cloud services more broadly, they increasingly depend on third-party vendors, ranging from SaaS providers and data processors to infrastructure partners, to support critical operations.
This growing interdependence introduces a new layer of risk. Third-party failures, security breaches, or compliance gaps can cascade into serious operational and reputational consequences. Managing these risks is no longer optional; it’s a core component of modern enterprise risk governance.
This blog outlines what third-party risk in cloud environments entails, explores the real benefits and challenges of integration, and provides actionable tips for effective third-party risk management in cloud computing.
Overview
Cloud adoption has increased third-party dependencies, making third-party risk management in cloud computing a critical function, not a secondary concern.
Key risks include excessive permissions, weak vendor controls, and a lack of continuous monitoring across multi-cloud environments.
Effective strategies include context-aware access, automated remediation, Just-in-Time permissions, and policy guardrails.
Auditive modernizes vendor risk management with continuous monitoring, faster onboarding, and a centralized Trust Center that simplifies third-party oversight across the full relationship lifecycle.
What is Third-Party Risk in Cloud Computing?
Third-party risk in cloud computing refers to the potential threats and vulnerabilities introduced by external vendors who provide services, infrastructure, software, or data processing functions within a cloud-based environment. These vendors operate outside the direct control of the enterprise but have varying degrees of access to its systems, data, and workflows.
Third-party risks can manifest in several forms:
Security Risk: Weak security practices by a vendor can expose an organization to data breaches, malware injection, or unauthorized access.
Compliance Risk: Failure by the vendor to adhere to regulatory requirements (e.g., GDPR, HIPAA, SOC 2) may result in legal consequences or fines for the contracting enterprise.
Operational Risk: Downtime or service failures from a cloud-based third party can disrupt core business functions.
Reputational Risk: A publicized incident involving a third party can erode customer trust and brand equity.
Strategic Risk: Overdependence on a single cloud vendor may reduce flexibility or lead to vendor lock-in.
Unlike traditional IT risks, third-party cloud risks extend beyond organizational boundaries. Vendors may subcontract to other service providers (fourth parties), increasing complexity and reducing visibility.
Effective third-party risk management in cloud computing requires more than periodic due diligence; it demands continuous visibility, real-time monitoring, and integrated risk controls that align with evolving threat surfaces across multi-cloud and hybrid ecosystems.
The Need for Third-Party Resources in Today’s Cloud Infrastructure
The shift from on-premises infrastructure to cloud environments has expanded the role of third parties beyond simple software licensing. Enterprises now rely on external vendors for a wide range of cloud-based services, from infrastructure provisioning and data hosting to collaboration tools, APIs, analytics platforms, and security monitoring.
This dependency is not just a matter of convenience; it’s an operational necessity. Building and maintaining proprietary platforms for each function is resource-intensive, time-consuming, and often cost-prohibitive. Third-party providers bring the specialized capabilities and scalability required to compete in dynamic digital markets.
Common examples include:
Cloud-based CRMs are integrated directly with marketing platforms.
Payment APIs connected to e-commerce engines and banking services.
Collaboration tools like Slack or Microsoft Teams that interface with cloud storage, calendars, and productivity software.
These integrations create efficient, interconnected ecosystems, but they also introduce complex interdependencies. Each vendor represents a potential access point into the organization’s cloud environment. Without structured oversight, even routine integrations can evolve into unmonitored risk vectors.
This underscores the growing importance of third-party risk management in cloud computing. As organizations lean on external vendors to extend functionality and accelerate innovation, the responsibility for assessing, controlling, and continuously monitoring those relationships becomes critical to maintaining both security and resilience.
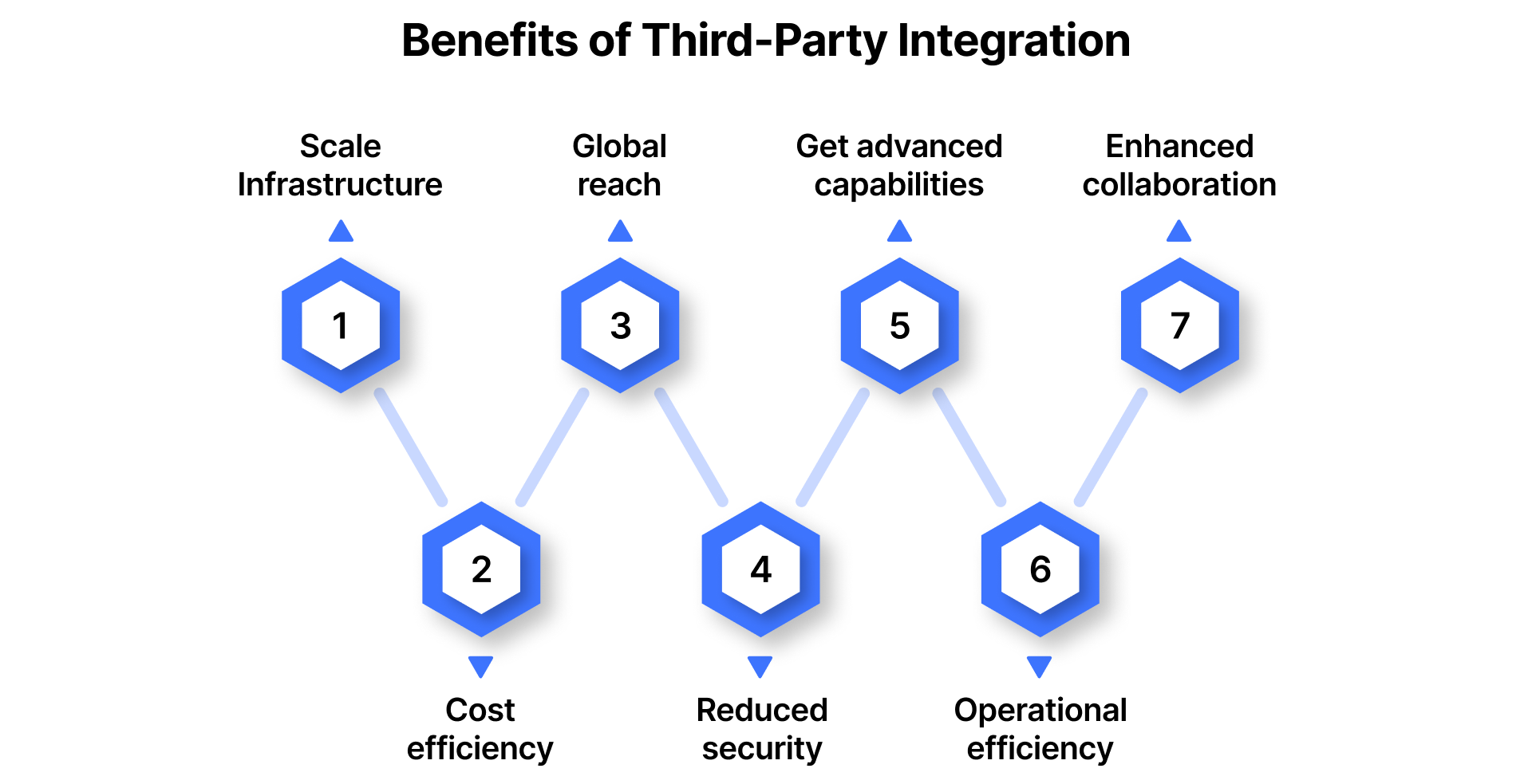
Benefits of Third-Party Integration
Third-party vendors are now embedded into the fabric of modern cloud infrastructure. Their integration is not just a tactical move; it’s a strategic enabler that drives growth, innovation, and resilience at scale. While these partnerships do require oversight, the value they deliver is substantial across key operational and strategic dimensions.
1. Scalability without infrastructure overhead
Cloud-native third-party vendors allow businesses to scale infrastructure and services instantly without investing in physical hardware or internal IT expansion. As user demand, data volumes, or application usage increase, these vendors absorb the surge, ensuring seamless continuity.
Organizations can accommodate exponential growth without technical disruptions.
Cloud-native elasticity reduces the risk of capacity limitations or service degradation.
This agility is especially critical for enterprises operating across volatile or seasonal markets, where demand fluctuations must be met without delay.
2. Cost efficiency through usage-based models
Traditional software licensing models involve substantial upfront costs or annual contracts. In contrast, most third-party cloud vendors operate on a metered, pay-as-you-go billing model. This allows companies to align spending with actual consumption.
Avoid over-provisioning by paying only for what is used.
Predictable cost structures improve financial planning and cloud ROI.
Ideal for short-term projects, testing environments, or pilot programs.
Strategic vendor partnerships can also reduce long-term operational costs by eliminating the need for in-house development and support of non-core solutions.
3. Accelerated time-to-market and global reach
Cloud-based third parties offer plug-and-play services that drastically reduce deployment cycles. Whether launching a new application, entering a new region, or enabling hybrid workforces, vendors can provide the infrastructure and tools almost instantly.
Rapid deployment accelerates innovation and experimentation cycles.
Global service availability reduces the need for physical presence in new markets.
Internal teams are freed from time-intensive setup and configuration tasks.
This speed-to-execution is critical in competitive markets where time is directly tied to market share and customer experience.
4. Reduced security burden on internal teams
High-quality vendors often bring robust security controls, compliance certifications (like SOC 2, ISO 27001, GDPR), and full-stack monitoring as part of their service. By offloading many of the operational security responsibilities, internal IT and security teams can focus on more strategic risk areas.
Vendors manage patching, threat detection, and infrastructure hardening.
Enterprises benefit from shared responsibility models without compromising control.
Lower resource strain for internal cybersecurity and compliance teams.
Auditive enables enterprises to continuously validate that third-party security claims are more than just checkboxes, through integrated monitoring, proactive risk alerts, and unified visibility across the full vendor ecosystem.
5. Access to advanced capabilities without internal investment
Third-party vendors often specialize in advanced technologies, ranging from AI, machine learning, and behavioral analytics to data warehousing and workflow automation. This expertise is often out of reach for internal teams constrained by budget, headcount, or domain knowledge.
Leverage vendor R&D to stay ahead of technology curves.
Incorporate cutting-edge features without building them in-house.
Stay competitive by adopting solutions refined across multiple client use cases.
This technical leapfrogging allows businesses to innovate with less friction and fewer delays.
6. Operational efficiency and strategic focus
Third-party solutions offload non-core workloads, allowing teams to focus on what matters most: delivering value to customers, scaling product lines, or executing strategic initiatives.
Reduce time spent maintaining commodity systems or internal tooling.
Lower overhead in hiring, training, and managing specialized functions.
Reclaim internal bandwidth for transformation and growth.
When managed properly, third-party vendors act as force multipliers, not distractions.
7. Enhanced collaboration and remote enablement
Collaboration platforms like Zoom, Slack, Microsoft Teams, and project management tools allow for fluid communication across distributed teams. These tools, provided by third parties, underpin the success of remote and hybrid work models.
Teams collaborate in real-time across time zones and departments.
Managers gain visibility into workflows and project progress.
Secure access ensures data integrity regardless of employee location.
By enabling always-on connectivity, these vendors empower flexible work without sacrificing structure or control.
Challenges of Third-Party Integration in Cloud Environments
Bringing third-party vendors into a cloud ecosystem can enable rapid growth, but it also introduces risks that demand serious attention. Below are key challenges enterprises must manage when scaling cloud partnerships.
1. Data security and privacy
Third parties often handle sensitive business and customer data. If they operate with weak security practices or outdated controls, they can become a major liability.
Potential exposure of personal or financial data
Weak encryption or identity controls at the vendor level
Limited visibility into how data is stored, shared, or processed
Every additional vendor becomes a potential entry point for attackers. Monitoring security compliance across a growing vendor ecosystem is both critical and resource-intensive.
2. Vendor lock-in
Vendor lock-in occurs when a cloud partner uses proprietary tools or architectures that are difficult to migrate away from. This limits agility and inflates switching costs.
Long-term contracts that restrict exit strategies
Proprietary APIs or configurations that require custom reengineering
Dependency on a single vendor’s roadmap or support lifecycle
This challenge becomes more pronounced when business needs change or the vendor alters its service terms.
3. Compatibility and integration issues
Smooth interoperability is not guaranteed. Cloud services from third parties must align with your existing tech stack, data flows, and performance expectations.
Integration delays due to API mismatches
Data inconsistencies across platforms
Performance degradation in real-time applications
A lack of technical compatibility or insufficient onboarding support can disrupt operations and lead to long-term inefficiencies.
4. Regulatory compliance risk
Third parties operating outside your governance structure can expose your organization to regulatory violations, especially in sectors like healthcare, finance, or critical infrastructure.
Failure to meet compliance standards like HIPAA, GDPR, and SOC 2
Inconsistent audit trails or reporting mechanisms
Limited transparency into subcontractors or fourth-party vendors
A single oversight from one vendor can trigger penalties, data investigations, or legal scrutiny across your enterprise.
5. Inconsistent support and response
Service quality across third-party vendors varies widely. When issues arise, such as outages, misconfigurations, or suspected breaches, support response time is critical.
Delayed response during service interruptions
Limited escalation paths or SLAs
Internal teams may lack the expertise to diagnose vendor-side problems
Auditive addresses these challenges by offering a network-driven risk model that tracks third-party relationships, automates monitoring, and continuously identifies high-risk signals. Instead of relying on static assessments, teams gain real-time visibility into vendor risk posture, empowering faster, smarter decisions.
Common Misconceptions About Using Third-Party Resources
Third-party integrations offer speed, specialization, and scalability but also introduce complexities that many teams underestimate. Misunderstandings around access, accountability, and risk ownership can leave organizations exposed to avoidable threats. Below are three common myths that hinder effective third-party risk management in cloud computing.
Myth #1: Third-party vendors handle all aspects of security
This is one of the most persistent misconceptions in cloud operations. Under the shared responsibility model, third-party vendors are accountable for securing their own infrastructure and applications. However, responsibility for protecting enterprise data, configuring secure access, and monitoring usage lies with the organization.
Security gaps often emerge not from the vendor’s system, but from misconfigurations, excessive permissions, or poor visibility into third-party behavior. Without structured oversight and continuous validation, even trusted tools can become weak links.
Auditive helps eliminate this blind spot by providing real-time visibility into third-party risk posture across cloud-connected environments, giving security teams the control they need without disrupting operations.
Myth #2: Third parties always prioritize data privacy
While many vendors follow strong data privacy protocols, assumptions can be dangerous. Not all third-party providers operate under the same compliance standards or regional data laws. Businesses must verify what data is accessed, how it’s processed, and whether it's stored, transferred, or shared with other entities.
Conducting thorough privacy reviews, validating contractual obligations, and continuously auditing data flows are essential steps, not one-time checks.
Myth #3: Internal access controls don’t apply to third-party tools
Access management should be universal. Enterprises often implement detailed internal controls but overlook external integrations. Unrestricted or poorly configured third-party access can expose sensitive systems to unauthorized users, especially if permissions are overly broad.
For example, connecting a collaboration app like Slack or Trello without limiting scope may unintentionally allow users to share sensitive documents beyond their intended audience. Identity and access management (IAM) must extend to all third-party resources, cloud-native or otherwise.
Tips for Managing Third-Party Risk in Cloud Computing
Effectively managing third-party risk in the cloud requires more than a checklist approach. It demands smart automation, context-aware policies, and frictionless enforcement that supports, rather than slows down, business operations. Here are six key practices for enhancing third-party risk management in cloud computing:
1. Monitor for excessive third-party permissions
Cloud entitlements are inherently complex, especially when third-party integrations span multiple accounts or regions. Automated, multi-cloud monitoring should continuously evaluate third-party credentials for overly permissive access or toxic permission combinations.
Controls must assess whether these privileges violate least-privilege principles by granting unnecessary rights to modify infrastructure or access sensitive data. A robust solution will not only surface these issues but also categorize them by risk severity, highlight potential attacker reconnaissance paths, and factor in mitigating controls such as network segmentation or access policies.
2. Apply context-aware monitoring
Not all third-party actions are inherently risky. Risk should be measured in context. Security controls should distinguish between routine operations and activities that genuinely exceed risk thresholds.
Excessive permissions, those that go beyond a third party’s operational necessity, should be the primary focus. By allowing trusted entities and accounts to be marked accordingly, contextual monitoring reduces alert fatigue and sharpens prioritization.
Solutions like Auditive’s network-driven platform help eliminate blind spots by continuously mapping access and enforcing policies through contextual insight, not static rules.
3. Auto-remediate third-party vulnerabilities
Teams are already managing an overwhelming number of alerts. Effective tools should not just detect issues; they must enable rapid response. Look for automated solutions that can generate and apply recommended policy substitutions, integrate directly into infrastructure-as-code pipelines, and auto-remediate misconfigurations across cloud services.
By embedding automation into workflows, remediation becomes part of the build process, not an afterthought.
4. Set permissions guardrails
To limit the blast radius of a third-party misstep or compromise, permissions guardrails must be proactively defined. Default cloud configurations often lean toward permissiveness, making it easy for IT teams to over-grant access in the name of speed.
Automated guardrails restrict what a third-party identity can do, ensuring they only access what’s essential to fulfill their purpose while denying access to critical resources or administrative functions.
5. Prioritize usability and integration
Security mechanisms must integrate with how teams already operate. Tools that demand constant context switching, manual analysis, or specialized expertise will be bypassed or underused.
Effective third-party risk management in cloud computing relies on intuitive dashboards, clear instructions, and seamless integration into collaboration tools like Slack, PagerDuty, or Jira, as well as into CI/CD pipelines for engineering teams.
6. Enforce Just-in-Time (JIT) access
Granting third parties permanent access is a high-risk move. Just-in-Time (JIT) access helps mitigate this by only allowing temporary, scoped access when needed, which is revoked automatically once the task is complete.
For example, a vendor performing emergency maintenance on production should have temporary, time-bound access, not a standing invite. JIT controls reduce dwell time and eliminate unnecessary exposure windows. Look for solutions that support JIT at scale and tie it to ticketing or approval workflows.
How Auditive Streamlines Third-Party Risk Management
Traditional third-party risk processes are fragmented, slow, and heavily manual, especially when cloud vendors operate across distributed environments. Auditive eliminates these inefficiencies with a modern, network-based approach to third-party risk management in cloud computing, enabling organizations to understand and act on vendor risk faster and more accurately.
With Auditive, teams can:
Measure true risk, not just generic compliance scores, but tailored evaluations aligned with the frameworks and regulations that matter to your business.
Get seller responses faster; vendors prefer Auditive’s workflow, resulting in up to 35% higher response rates during security reviews.
Continuously monitor seller risk across the full lifecycle of a third-party relationship, not just at onboarding.
Onboard vendors 4x faster by leveraging Auditive’s shared network of sellers, pre-mapped to relevant compliance and risk frameworks.
Integrate seamlessly with procurement systems, productivity tools, and internal workflows, ensuring security reviews don’t become a bottleneck.
Auditive’s Trust Center also gives buyers a central view of all vendor interactions, enabling transparency and collaborative accountability throughout the vendor lifecycle.
Conclusion
Managing third-party risk in cloud computing is no longer a compliance checkbox—it’s a business-critical function. As cloud infrastructure scales and third-party dependencies increase, the potential impact of overlooked risk grows significantly. Static assessments, delayed onboarding, and inconsistent monitoring only widen the exposure window.
Auditive helps organizations modernize vendor risk management with continuous visibility, contextual controls, and a network approach that simplifies every stage of the risk lifecycle. From onboarding to offboarding, from due diligence to ongoing compliance, every seller relationship can be evaluated, monitored, and managed through one unified Trust Center.
Ready to reduce third-party risk without slowing down your business?
Schedule a Demo of Auditive’s platform and see how efficient, intelligent third-party risk management works.
FAQs
Q1. What makes third-party risk management in cloud computing more complex than traditional environments?
Cloud environments involve distributed infrastructure, decentralized control, and multi-layered services. This complexity increases the likelihood of misconfigurations, excessive permissions, and limited visibility—especially when third parties are granted broad access.
Q2. How often should third-party access be reviewed or re-evaluated?
Access should be monitored continuously and reviewed regularly—especially when roles change, vendors onboard new sub-processors, or sensitive environments are involved. Just-in-Time (JIT) access and automated remediation help enforce proper boundaries.
Q3. Can a Trust Center help improve response times during vendor security assessments?
Yes. A centralized Trust Center streamlines communication and documentation between buyers and sellers, leading to faster, more consistent responses and a higher completion rate during assessments.
Q4. What are some key indicators of excessive third-party permissions?
Indicators include broad read/write access to sensitive data, infrastructure modification rights, or access inherited through poorly defined IAM policies. Automated tools should flag these permissions based on severity and exposure risk.
Q5. How does Auditive differ from traditional vendor risk tools?
Auditive uses a network-based approach, enabling faster onboarding, higher seller response rates, and continuous risk monitoring across all vendor relationships. It integrates directly with procurement workflows and compliance frameworks, reducing manual workload by up to 80%.