Understanding Third-Party Vendor Risk Management
A significant 54% of organizations suffered a breach caused by a third party in the last 12 months. That number alone explains why third-party vendor management is no longer a background function; it’s a frontline risk discipline.
When external partners control critical systems, customer data, or operational workflows, even a small lapse on their side can create outsized consequences on yours.
This blog breaks down why investing in structured third-party oversight matters, how it reduces direct business exposure, and what practical steps help teams strengthen vendor decisions without slowing operations.
Quick Glance:
Third-party vendor management requires current, verified data, not static questionnaires.
A structured VRM program reduces exposure to operational, security, and financial risks.
A centralized approach removes scattered evidence and improves vendor transparency.
Continuous oversight strengthens decision-making throughout the vendor lifecycle.
Purpose-built platforms help teams work faster and with fewer manual touchpoints.
What a Third Party Actually Is (and Why It Matters for Third Party Vendor Management)
A “third-party” isn’t just a vendor with a contract on file. It’s any external entity that touches your operations, data, or customers, directly or indirectly, and therefore becomes part of your risk surface. In practical terms, strong third-party vendor management starts with understanding exactly who these entities are and how deeply they influence your day-to-day workflow.
A third party can include:
Suppliers and manufacturers that influence production timelines and material quality.
SaaS providers responsible for uptime, data handling, and security of tools your teams rely on.
Logistics partners that determine whether fulfillment meets expectations or stalls.
Business partners, affiliates, and distributors that shape downstream brand reputation.
Non-contractual entities such as agents or resellers that still operate within your ecosystem.
Upstream or downstream, contractual or informal, if they have access, influence, or operational authority, they qualify as a third party. Misidentifying them (or missing any entirely) is one of the biggest reasons organizations underestimate their actual risk exposure.
Why Third-Party Vendor Risk Still Breaks Security Programs and What it Fixes
Relying on external vendors has become unavoidable, but it has also expanded the average organization’s attack surface faster than internal security teams can keep up. Every integration, API connection, or outsourced workflow creates a new entry point attackers can exploit. And the math isn’t subtle: the more vendors you onboard, the wider your exposure grows.
This is why strong third-party vendor management isn’t optional; it’s fundamental to maintaining a defensible security posture.
The Real Reasons Third-Party Risk Is Now a Critical Priority
Most companies underestimate how deeply vendors are embedded across their tech stack. That oversight creates blind spots that attackers repeatedly exploit.
Here’s what makes third-party risk uniquely dangerous:
Vendors extend your attack surface beyond your direct control. A single vulnerable supplier can become an unmonitored gateway into your environment.
One weak vendor system can compromise thousands. This is exactly how the 2013 Target breach occurred, attackers used stolen credentials from an HVAC contractor to access Target’s network, exposing millions of payment cards.
Regulators are explicitly tightening expectations.
Laws and frameworks, DORA, GDPR, CCPA, FIPA, PIPEDA, the SHIELD Act, LGPD, HIPAA, and SOC 2, now outline how organizations must assess, monitor, and govern third-party risks. Failure isn’t theoretical; it results in penalties, legal exposure, and long-term reputational damage.
Why Mature TPRM Programs Outperform
Organizations with a strong approach to third-party risk consistently see operational and strategic gains:
Clearer visibility across the vendor ecosystem. Instead of working off a static list, teams understand actual risk concentration, data exposure pathways, and dependency chains.
Improved resilience during vendor outages. A structured assessment and monitoring process helps ensure operations continue even when a supplier experiences downtime or disruption.
Stronger stakeholder trust. Customers, partners, auditors, and regulators view proactive TPRM as a signal of operational maturity, not just security hygiene.
A modern third-party risk program doesn’t just satisfy external expectations; it prevents the downstream impact of vendor misconfigurations, lax access controls, or overlooked sub-processors that can quietly erode your security posture.
Learn more about: How to Create a Vendor Management Program
The Real Risks Behind Third-Party Relationships and Why They Escalate Fast
Third-party vendor management isn’t just about onboarding workflows or periodic questionnaires. The real challenge is understanding the specific risk categories that external partners introduce, and how quickly those risks can escalate when visibility is shallow or outdated.
Cybersecurity Risk
This is the most immediate and measurable category. A single supplier with weak controls can be an entry point for credential theft, ransomware, or data exfiltration. Pre-onboarding security due diligence and ongoing monitoring are essential because risk indicators, expired certs, new sub-processors, and exposed assets change frequently.
Operational Risk
A vendor outage can halt workflows, delay revenue, and disrupt core processes. Critical vendors require predefined SLAs, tested continuity plans, and, in industries like financial services, a secondary vendor to prevent single-point-of-failure exposure.
Legal, Regulatory, and Data Handling Risk
Vendor missteps can directly affect your regulatory posture, especially in healthcare, finance, or government environments. Inadequate data handling practices, outdated policies, or jurisdiction-specific gaps can push risk back onto your organization, contractually and operationally.
Reputational Risk
Reputation impact isn’t limited to bad press. The most damaging events are publicized third-party breaches tied to insufficient controls, like the Target 2013 incident traced to an HVAC vendor. Trust takes years to build and minutes to lose, especially when customer data is involved.
Financial Risk
If a vendor fails to deliver, underperforms, or experiences financial instability, your own revenue trajectory is at risk. Product delays, supply chain inefficiencies, or rising vendor costs all fall under this category.
Strategic Risk
When a vendor is tightly linked to core initiatives, misalignment with your long-term objectives becomes a structural risk. If they cannot scale, innovate, or maintain pace with your roadmap, your strategic progress stalls.
Auditive’s platform emphasizes verifiable evidence, trust signals, and real-time vendor insights, rather than static questionnaires. This matters here because most third-party risk failures stem from blind spots, data that wasn’t captured, wasn’t updated, or wasn’t verified.
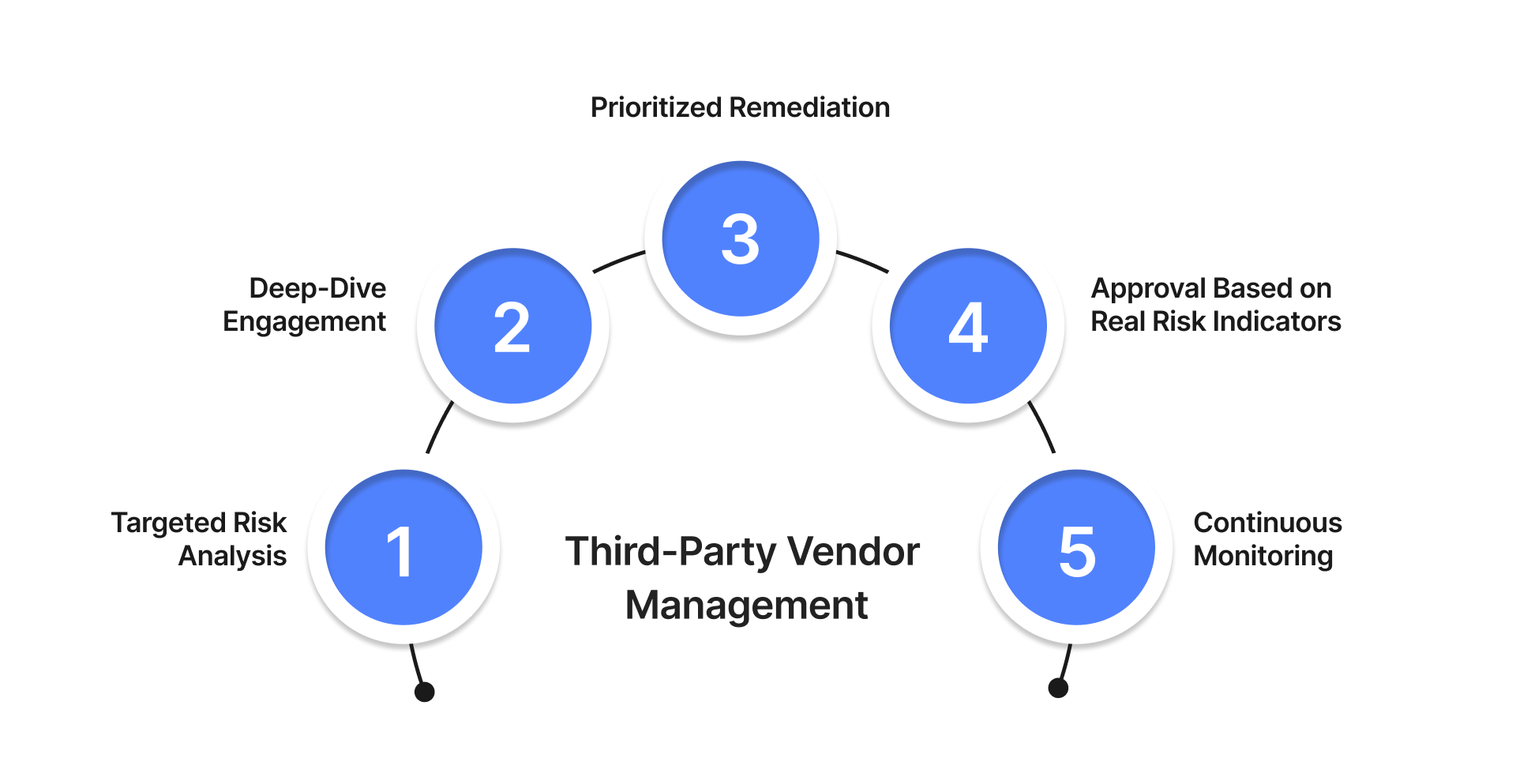
A Practical Breakdown of Third-Party Vendor Management
Implementing an effective third-party vendor management structure is ultimately about removing guesswork from external relationships. Instead of relying on surface-level checks, the program needs a repeatable flow that measures risk, validates controls, and maintains visibility as vendors evolve. Here’s a clear, operational breakdown of each step.
Step 1: Targeted Risk Analysis
Before a vendor enters your ecosystem, the first task is evaluating the specific risks they introduce, not a generic “high/medium/low” label.
A structured analysis typically includes:
Reviewing external security posture (e.g., security ratings, exposure surfaces, historic breach records).
Mapping vendor risk against your defined risk appetite and dependency thresholds.
Verifying whether the vendor meets a minimum acceptable posture before deeper assessment.
This step sets the baseline for how much diligence is needed and prevents teams from wasting cycles on unqualified vendors.
Step 2: Deep-Dive Engagement
Once the initial posture looks acceptable, the next step is to collect internal, non-public security details directly from the vendor.
This stage often includes:
Completing structured security questionnaires aligned to control frameworks (SIG, CAIQ, NIST, HECVAT, etc.).
Requesting evidence around data handling, incident response, encryption practices, and access control.
Validating the vendor’s claims through documentation and audit artifacts, not verbal assurances.
This gives you a complete picture of the vendor’s control environment, beyond what’s externally visible.
Step 3: Prioritized Remediation
If evidence reveals gaps, remediation becomes the deciding factor, not the rating itself.
A mature remediation process includes:
Flagging specific controls that fall below threshold (e.g., weak authentication, lack of logging, outdated SSL, missing certifications).
Assigning timelines and accountability based on the risk severity and vendor criticality.
Tracking progress with an auditable trail to prevent issues from disappearing in inboxes or spreadsheets.
The goal is clear: risk reduction before the vendor touches your environment.
Step 4: Approval Based on Real Risk Indicators
Approval should reflect actual risk posture, not convenience, vendor popularity, or contractual momentum.
Organizations typically evaluate:
Whether remediation has closed all critical gaps.
Whether remaining risks fall within acceptable tolerance.
Whether the vendor’s role is critical enough to justify any residual exposure.
This is where third-party vendor management becomes operational and business-aligned, not checkbox-driven.
Step 5: Continuous Monitoring
Vendor risk doesn’t freeze after onboarding, and static, yearly reviews don’t reflect real-world change.
Continuous monitoring should include:
Tracking new vulnerabilities, leaks, expired certifications, and security incidents.
Watch for organizational changes such as ownership shifts, staff turnover, or expanded access to internal systems.
Triggering reassessment workflows when risk levels change.
Continuous monitoring prevents silent degradation of a vendor’s security posture.
Auditive’s platform removes the operational drag that slows down most third-party vendor management programs. The product isn’t built solely on questionnaires; it centralizes evidence, vendor artifacts, trust documentation, and security posture signals.
Why Investing in Third-Party Vendor Management Pays Off
A structured third-party vendor management program isn’t a checkbox exercise; it’s a financial, operational, and strategic safeguard with measurable impact.
Reduced breach exposure
Third-party incidents remain one of the most expensive vectors in the risk landscape. IBM’s 2024 Cost of a Data Breach Report shows breaches involving third parties cost an average of $4.55M, higher than internally caused breaches. When organizations build a dedicated TPRM motion, they cut exposure by reducing insecure access paths, unverified integrations, and unmanaged data flows.
Clearer regulatory footing
Sector frameworks such as FISMA, SOX, HITECH, CPS 234, GLBA, and the NIST Cybersecurity Framework expect organizations to validate the maturity of their vendors, not just themselves. If your vendors touch regulated data (PII, PHI, financial records), you’re accountable for downstream failures. Mature TPRM gives you audit-ready evidence, structured oversight, and proof of ongoing control monitoring, all essential for reducing regulatory friction.
Reduced operational risk
Strong TPRM shortens onboarding cycles, enforces consistent due diligence, and keeps vendor relationships aligned with your internal risk thresholds. Because risk profiles change (mergers, system upgrades, incidents, staffing turnover), continuous reassessment is what prevents latent vulnerabilities from becoming incidents. This closes risk gaps early, before they influence your production environment.
Better decision-making
Visibility into how each vendor handles data, uptime, access, and incident response allows teams to make informed choices, not assumptions. Over time, this elevates procurement decisions, strengthens contract negotiations, and ensures higher confidence across the vendor lifecycle.
Also read: Third-Party Risk Management: Guidance on Achieving Compliance
Where Auditive Fits In, Without the Generic Heavy Lifting
And this is where Auditive changes the equation. Instead of relying on static questionnaires, it pulls live vendor signals into one place so your risk decisions reflect what vendors are doing today, not what they documented months ago.
How Auditive Supports Third-Party Vendor Management
Auditive gives teams a verified, always-current view of their vendors, not static questionnaires that age out within weeks.
Continuously updated vendor profiles: Security controls, policies, and certifications refresh automatically, reducing stale data during evaluations.
Real-time posture changes: Expired certificates, policy updates, and missing controls surface immediately, helping teams react before risks grow.
Faster vendor decisions: Procurement, security, and legal teams rely on the same validated information, which shortens onboarding and renewal cycles.
Reduced manual chasing: Assurance data updates on its own, limiting repetitive follow-ups and manual documentation requests.
Auditive removes the lag and uncertainty that typically slows down third-party vendor management, giving teams clearer oversight with less operational friction.
Summary
Effective third-party vendor management depends on consistent oversight, verified information, and the ability to make decisions based on current, not outdated, risk signals. A structured approach to risk assessment strengthens how teams assess vendors, track their security posture, and maintain transparency across the lifecycle.
This combination of disciplined processes and reliable, centralized data creates a stronger, more predictable vendor ecosystem and reduces the uncertainty that typically surrounds third-party work.
If you want to streamline how your team evaluates, monitors, and communicates vendor risks, Schedule a demo with Auditive to see how its automated VRM capabilities can support your workflows.
FAQs
1. Why is third-party vendor management important?
It helps organizations reduce exposure to breaches, operational failures, and financial losses caused by external vendors.
2. What does a vendor platform provide?
A vendor platform centralizes risk and compliance data, automates evidence collection, and provides real-time insights into vendor performance and security posture, allowing teams to assess and monitor third-party risks efficiently.
3. How often should vendors be reassessed?
Assessment frequency depends on vendor criticality, but high-risk vendors usually require more frequent reviews and ongoing monitoring.
4. Does VRM replace due diligence?
No. VRM supports and enhances due diligence by automating evidence updates and improving visibility across vendors.
5. How does a platform like Auditive improve VRM?
It keeps vendor information current, reduces manual requests, and provides a single source of truth to support faster and more accurate decisions.