How to Create a Vendor Management Program
Third-party vendors play a critical role in driving innovation, efficiency, and growth. But this reliance also exposes organizations to a wide range of risks, from data breaches and compliance lapses to service disruptions and reputational damage. That’s why having a robust vendor management program is no longer optional; it’s essential.
A well-defined program helps organizations evaluate, monitor, and manage vendor relationships with precision. It establishes a clear framework to assess performance, mitigate risks, and ensure compliance with corporate, legal, and security standards. In doing so, it turns vendor oversight into a strategic advantage rather than a reactive task.
As supply chains and digital ecosystems expand, vendor management has evolved beyond cost control, it’s about protecting business continuity, building trust, and ensuring long-term resilience. A strong program fosters transparency, accountability, and sustainable growth across every partnership.
Key takeaways:
A vendor management program centralizes vendor oversight, mitigates risk, and ensures compliance.
Effective vendor risk management prioritizes high-risk vendors and maintains continuous monitoring.
Establish a Trust Center to enhance transparency, accountability, and collaboration with vendors.
Technology, such as Auditive, automates workflows, monitors risks, and integrates seamlessly with existing systems.
Continuous assessment and proactive engagement strengthen vendor relationships and safeguard your organization.
What Is a Vendor Risk Management Program?
A vendor risk management program (VRMP) is a structured framework designed to ensure that third-party vendor relationships deliver maximum value while minimizing potential risks. It combines tools, processes, and governance policies to help organizations manage their vendors strategically, focusing not only on performance and cost efficiency but also on security, compliance, and operational resilience.
For instance, third-party data breaches are becoming alarmingly common and impacting industries from banking and healthcare to automotive and telecommunications. These breaches don’t just compromise data; they also erode customer trust and can lead to severe legal and financial consequences.
A well-designed vendor risk management program helps mitigate such risks through a proactive, continuous approach. It allows organizations to:
Identify and assess vendor risks before onboarding.
Evaluate security controls and compliance practices to ensure alignment with regulatory standards.
Negotiate robust contracts and service level agreements (SLAs) that define expectations clearly.
Continuously monitor vendor performance and risk posture throughout the engagement lifecycle.
Ultimately, a vendor risk management program empowers organizations to make informed decisions about who they work with and maintain compliance with data protection regulations.
What Is the Purpose of a Vendor Management Program?
A vendor management program is more than just a process, it’s a strategic framework that ensures every vendor your organization works with supports your long-term goals, complies with standards, and delivers measurable value. It’s designed to help businesses manage external relationships in a structured, proactive way, turning vendor partnerships into drivers of efficiency, trust, and growth.
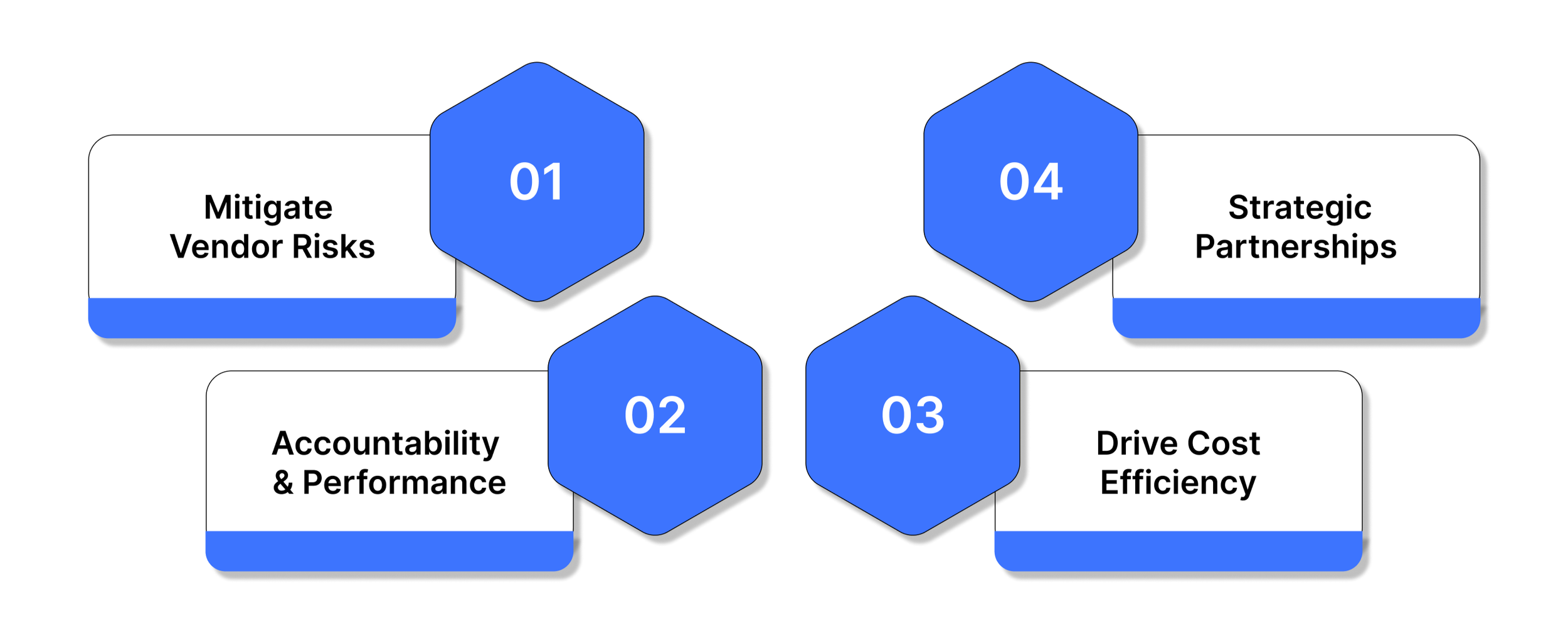
At its core, the purpose of a vendor management program can be understood through four key objectives:
1. Mitigate Vendor Risks:
The program acts as a safety net against potential risks such as data breaches, operational disruptions, financial instability, or regulatory non-compliance. It ensures vendors meet security and ethical standards while protecting the organisation’s data, reputation, and financial stability.
2. Improve Accountability and Performance:
By establishing clear expectations, measurable performance indicators (KPIs), and regular monitoring, the program holds vendors accountable for delivering on their commitments. This transparency builds trust and ensures consistency in product or service quality.
3. Drive Cost Efficiency and Optimization:
While implementing a vendor management program may appear to be an added cost, it actually promotes long-term savings. With visibility into vendor spend and performance, organizations can:
Negotiate stronger, more cost-effective contracts.
Eliminate redundant services or duplicate outsourcing.
Identify opportunities for better pricing or bundled solutions.
4. Strengthen Strategic Partnerships:
Vendor management isn’t only about oversight, it’s about building collaborative, long-term relationships. A structured program encourages open communication, joint problem-solving, and mutual growth, allowing vendors to evolve with your organization’s needs.
When done effectively, a vendor management program provides a systematic approach to third-party oversight, from assessing vendor risks and onboarding new partners to ongoing performance tracking and issue resolution.
In essence, it transforms vendor relationships from reactive management into a strategic discipline that enhances operational resilience, promotes compliance, and supports continuous business improvement.
The Structure of a Vendor Management Program
Building a successful vendor management program begins with establishing a solid structure that clearly defines roles, responsibilities, and accountability across the organization. This structure ensures that every aspect of the vendor lifecycle, from selection and onboarding to performance evaluation and termination, is managed systematically and consistently.
At its core, an effective vendor management framework operates on three lines of defense, each playing a distinct yet interconnected role in maintaining oversight and minimizing risk.
1. Vendor Owner (First Line of Defense)
The vendor owner serves as the primary point of contact for day-to-day vendor interactions. They are directly responsible for overseeing vendor performance, addressing operational issues, and ensuring that vendors deliver according to agreed-upon terms. Because vendor owners work closest to the vendors, they are often the first to identify potential risks or performance gaps. Their responsibilities typically include:
Conducting routine performance assessments and vendor reviews.
Managing issue resolution and escalation.
Ensuring vendors adhere to contractual obligations and organizational standards.
By maintaining close communication with vendors, the vendor owner acts as the organization’s front-line expert on vendor products, services, and risk exposure.
2. Vendor Management Team (Second Line of Defense)
The vendor management team provides the strategic oversight necessary to ensure consistency and alignment across all vendor relationships. This team is responsible for designing, implementing, and maintaining the organization’s vendor management policies and procedures. Key duties include:
Developing and enforcing vendor management policies.
Setting performance metrics, risk thresholds, and compliance expectations.
Offering guidance to vendor owners to ensure adherence to organizational standards.
Essentially, this team acts as the backbone of the vendor management program, bridging operational execution with strategic governance.
3. Internal Audit (Third Line of Defense)
The internal audit or compliance team plays a crucial role in maintaining transparency and accountability. They independently review vendor management practices to ensure compliance with internal controls, regulatory mandates, and industry best practices. Their focus is on identifying weaknesses, gaps, or noncompliance within the program. Key responsibilities include:
Conducting regular audits and compliance checks.
Assessing the effectiveness of risk mitigation strategies.
Reporting findings to senior leadership for corrective action.
By evaluating the program’s overall integrity, internal auditors provide confidence that vendor relationships are being managed in a compliant, secure, and transparent manner.
Together, these three lines of defense create a strong structural foundation for any vendor management program, one that promotes collaboration, accountability, and resilience throughout the vendor lifecycle.
To bring structure and efficiency into every stage of vendor oversight, organizations are increasingly turning to intelligent automation and centralized monitoring platforms. This is where Auditive steps in, streamlining vendor risk management and ensuring transparency across your entire vendor ecosystem.
The Stages of a Vendor Management Program
A successful vendor management program is not built overnight, it’s developed through a structured, repeatable process that governs every phase of the vendor lifecycle. From onboarding to offboarding, each stage ensures that vendors are properly evaluated, monitored, and managed to align with your organization’s goals, compliance requirements, and risk tolerance.
Below are the key stages that form the backbone of an effective vendor management program:
1. Onboarding Vendors
The onboarding phase lays the foundation for a healthy vendor relationship. It involves a series of strategic steps designed to ensure that vendors meet your organization’s operational, financial, and security standards before any engagement begins.
a. Planning and Risk Assessments
This initial step involves defining business needs, setting clear objectives, and determining which activities will be outsourced. Conducting inherent risk and criticality assessments helps identify potential vulnerabilities and establish how critical a vendor is to your operations. It’s also the stage to assign roles and responsibilities for managing the relationship moving forward.
b. Due Diligence
Due diligence is a critical checkpoint where the vendor’s capabilities, financial health, and compliance posture are examined. You should collect and review documentation such as:
Financial reports to assess stability
SOC (System and Organization Controls) reports for security assurance
Policies and procedures related to data protection, privacy, and governance
Business continuity and disaster recovery (BC/DR) plans to ensure operational resilience
c. Contracting
Once due diligence is complete, it’s time to formalize the relationship. A well-drafted contract sets expectations clearly through Service Level Agreements (SLAs) and legal provisions that safeguard both parties. These should include:
Rights to audit
Data breach notification requirements
Data protection and confidentiality clauses
Termination and renewal conditions
Standardized contract templates help maintain consistency and ensure every vendor relationship meets organizational standards.
Also read: How to Prevent Data Breaches in Healthcare
2. Ongoing Monitoring
Vendor management doesn’t stop after onboarding. In fact, ongoing monitoring is where the true value of a vendor management program is realized.
a. Reassessments
Vendors evolve, and so should your assessments. Reassess vendors when significant operational or compliance changes occur. Review risk scores, update documentation, and validate whether existing controls remain adequate.
b. Risk and Performance Monitoring
Continuous monitoring ensures vendors stay compliant with SLAs and regulatory standards. Establish a regular risk review schedule based on each vendor’s risk level and performance. Using dashboards or vendor management software can help automate these evaluations, providing real-time insights into vendor performance.
c. Contract Renewals
Stay proactive with contract renewals and expirations. Monitoring key dates allows your organization to revisit terms, negotiate improvements, or even terminate relationships that no longer align with business needs.
d. Due Diligence Updates
Due diligence isn’t a one-time task. Certain documents, like insurance certificates or disaster recovery plans, need periodic review. Always ensure your vendor files include the most current and accurate documentation to reflect the vendor’s present-day risk posture.
3. Offboarding Vendors
Ending a vendor relationship should be as structured and secure as starting one. Proper offboarding minimizes disruption, protects sensitive data, and ensures all contractual and operational obligations are closed properly.
a. Termination
The process begins with formally notifying the vendor that the contract will not be renewed. This step should adhere to the termination clauses defined in the contract to prevent any legal disputes.
b. Exit Plan Execution
An effective exit plan, established during onboarding, ensures that all offboarding activities are performed smoothly. Key actions include:
Returning or securely destroying sensitive company data
Revoking vendor access to internal systems and networks
Ensuring continuity by transitioning services to another vendor or internal team
c. TPRM Closure
Finally, close all open actions under the Third-Party Risk Management (TPRM) program. Settle final invoices, archive performance records, and update your vendor database to mark the vendor as inactive.
A structured vendor management program ensures that every vendor engagement, from initiation to closure, is transparent, compliant, and strategically aligned with business goals. By following these stages, organizations not only mitigate risk but also build stronger, more reliable vendor partnerships that drive long-term success.
Know more about: Understanding Principles of Third-Party Risk Management (TPRM)
To streamline every stage, from onboarding to monitoring, businesses are now turning to intelligent platforms like Auditive, which centralize vendor performance tracking, automate risk assessments, and integrate seamlessly with governance systems for continuous compliance oversight.
Key Elements of a Vendor Management Program
A robust vendor management program is built on several critical elements that ensure your organization can effectively manage vendor relationships, mitigate risks, and drive value from third-party partnerships. These elements provide the foundation for best practices in vendor oversight and set the stage for operational excellence.
1. Vendor Governance Framework
This framework outlines your organization's overall approach to vendor management. It establishes a clear governance structure, identifies the team or individuals responsible for sponsoring, overseeing, and owning vendor management, and defines their roles and responsibilities. It also specifies authority levels, decision-making processes, and escalation procedures, as well as the tools and technologies to be used for vendor oversight.
2. Vendor Policy and Procedures
Standardized policies and procedures govern all vendor management activities. These include vendor qualification, selection, contract development, execution, onboarding, performance monitoring, risk assessment, and offboarding. Clear policies ensure consistency, compliance, and alignment with organizational goals.
3. Vendor Risk Management Framework
This framework details your approach to identifying, assessing, mitigating, and monitoring risks associated with vendor relationships. It includes risk assessment methodologies, tolerance levels, and mitigation strategies tailored to different vendor categories and business functions, ensuring proactive risk control.
4. Vendor Qualification and Selection Criteria
Establishing clear criteria for evaluating and selecting vendors is essential. Considerations include product or service quality, financial stability, operational capabilities, regulatory compliance, and ethical standards. This step ensures your vendors meet both performance and compliance expectations from the outset.
5. Vendor Contract Development
Contract management is central to formalizing vendor relationships. This includes negotiating, drafting, reviewing, approving, and executing contracts, along with developing standard templates, defining terms and conditions, and setting service level agreements (SLAs). Well-structured contracts safeguard both parties and provide clear accountability.
6. Vendor Performance Monitoring and Evaluation
Establish performance metrics, key performance indicators (KPIs), and reporting mechanisms to monitor vendor performance against predefined benchmarks and SLAs. Conduct regular performance reviews, provide constructive feedback, and address performance issues to maintain service quality and accountability.
7. Vendor Relationship Management
Strong vendor relationships foster collaboration and alignment with business objectives. Define communication channels, engagement strategies, and relationship-building activities. Establish mechanisms for conflict resolution, issue escalation, and grievance handling to maintain a productive partnership.
8. Vendor Compliance and Audit
Ensure adherence to regulatory requirements, industry standards, and internal policies. Conduct due diligence, assess vendors’ compliance posture, and perform periodic audits to verify contractual and regulatory adherence. This element safeguards your organization from compliance-related risks.
9. Vendor Continuity and Contingency Planning
Prepare for vendor disruptions with continuity and contingency plans. Establish procedures for mitigating risks associated with vendor dependencies, transitioning to alternative vendors, or bringing services in-house when necessary. These measures ensure business continuity even during unforeseen vendor failures.
By incorporating these key elements into your vendor management program, organizations can achieve a structured, proactive, and resilient approach to managing third-party relationships, minimizing risks, and maximizing value from every vendor partnership.
To take your vendor management to the next level, tools like Auditive provide real-time insights, continuous monitoring, and a centralized Trust Center, helping organizations streamline vendor oversight while mitigating risks efficiently.
How to Create an Effective Vendor Risk Management Program
Establishing a robust vendor risk management (VRM) program is essential for safeguarding sensitive data, ensuring regulatory compliance, and mitigating operational risks arising from third-party relationships. By implementing a structured VRM workflow, organizations can proactively manage vendor risks throughout the entire lifecycle, from onboarding to ongoing monitoring and eventual offboarding.
Step 1: Write Vendor Risk Management Documentation
The foundation of any VRM program is comprehensive documentation. Organizations should develop clear policies and procedures detailing the roles and responsibilities of all stakeholders involved in vendor risk management. This documentation should be integrated into the broader information security policy and updated regularly to reflect changes in regulatory requirements, security maturity, and vendor inventory. A well-documented VRM program ensures consistency, accountability, and a clear roadmap for managing vendor risks.
Step 2: Establish Vendor Selection Standards
Onboarding a new vendor often involves granting access to sensitive data or critical systems. It is essential to establish stringent vendor selection standards to ensure that potential partners meet your security and compliance expectations. This involves:
Conducting thorough Request for Proposal (RFP) evaluations.
Reviewing vendor submissions with a focus on compliance certifications and security posture.
Ensuring that vendors’ internal security practices extend to their interactions with your organization.
By defining clear selection standards, your organization can minimize exposure to third-party risks from the outset.
Step 3: Perform Vendor Due Diligence
Vendor due diligence is the process of verifying and validating a vendor’s claims regarding security, compliance, and operational reliability. This should occur before onboarding and continue throughout the vendor lifecycle. Key due diligence practices include:
Sending risk assessment questionnaires at least annually.
Requesting documentation such as SOC 2 reports, business continuity plans, incident response plans, and information security policies.
Using vendor tiering to prioritize high-risk vendors for closer scrutiny.
Assessing security posture via security ratings and continuous monitoring of potential vulnerabilities.
Due diligence ensures that vendors maintain appropriate standards and allows your organization to manage risks effectively.
Step 4: Audit Your Vendors Regularly
Regular audits help organizations identify compliance gaps, vulnerabilities, and evolving risks within their vendor network. Effective auditing involves:
Maintaining a single source of truth for all vendor-related events, including contracts, risk assessments, and remediation actions.
Leveraging security questionnaires to evaluate ongoing compliance.
Producing detailed reports that track vendor performance, risk mitigation progress, and compliance status.
Audits not only maintain transparency but also help reinforce accountability and continuous improvement.
Step 5: Define Reporting Expectations
Executive and operational teams need concise and consistent reporting to understand the broader impact of vendor risks. Effective reporting should summarize vendor metrics in a digestible format, including:
Average vendor security ratings.
Number of monitored vendors over time.
Distribution of vendor risk levels.
Identification of high-risk or underperforming vendors.
Fourth-party risk and vendor geolocation insights.
Automated vendor risk management platforms can consolidate these reporting functions, streamlining executive decision-making and providing real-time insights into your vendor portfolio.
Leveraging tools like Auditive can transform your VRM program by automating risk assessments, continuous monitoring, and reporting.
Learn more about: How to Create an Effective Vendor Onboarding Packet
Best Practices of a Vendor Risk Management Program
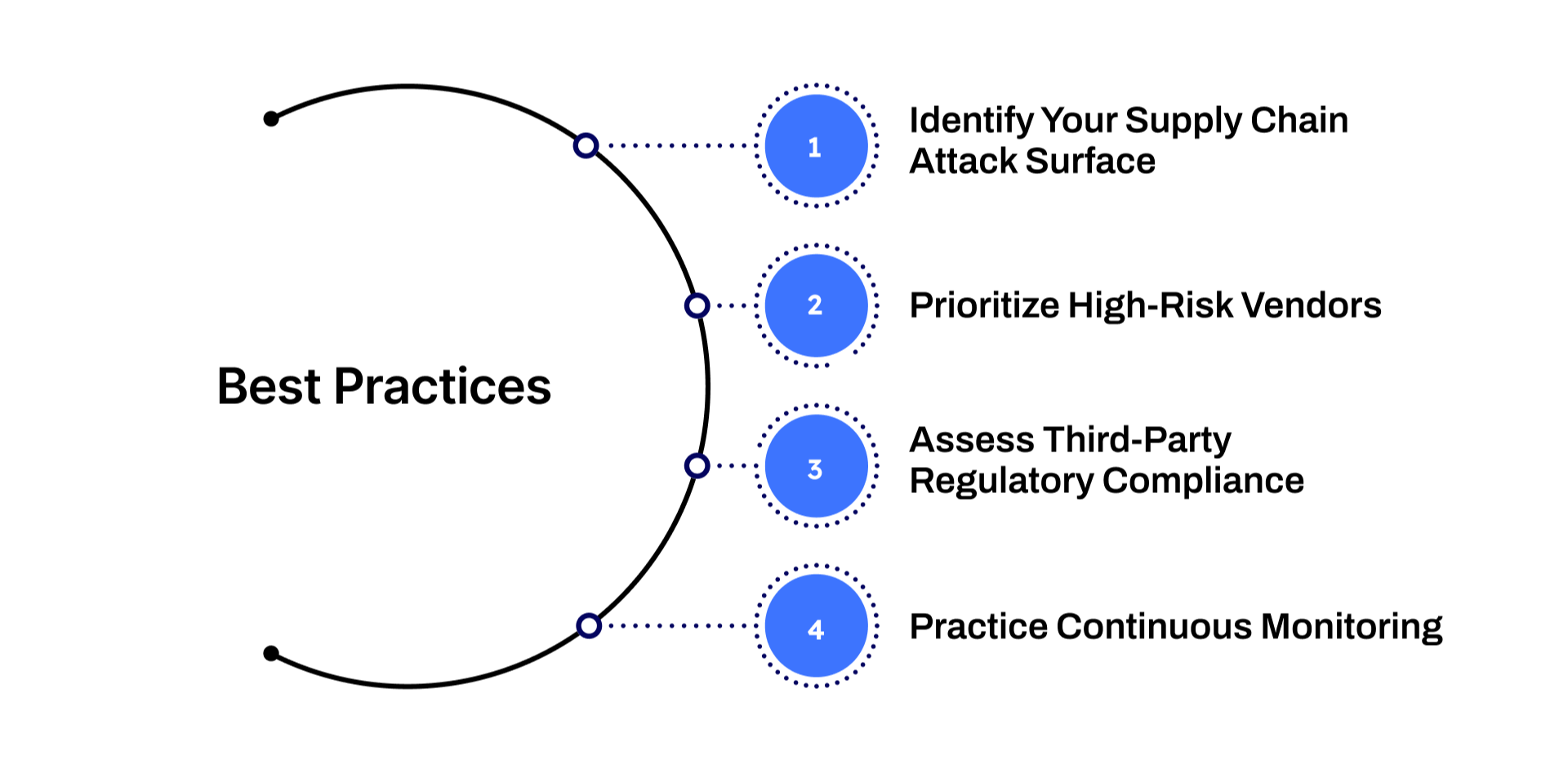
An effective vendor risk management (VRM) program requires more than just policies on paper, it demands strategic processes, continuous oversight, and the right tools to manage the ever-growing vendor ecosystem. Below are some best practices that organizations can adopt to optimize their VRM programs and maintain a secure, resilient supply chain.
1. Identify Your Supply Chain Attack Surface
A robust VRM program begins with a complete understanding of your third-party and fourth-party vendors. With Gartner reporting that over 60% of organizations manage 1,000+ third parties, maintaining visibility across the entire supply chain attack surface can quickly become complex.
Create a comprehensive vendor inventory: This serves as the foundation of your VRM program, allowing you to track all vendors and their connections to your systems.
Automate discovery of fourth parties: Manual identification is time-consuming and often inaccurate. Automation helps detect indirect dependencies and potential vulnerabilities across the supply chain.
Categorize vendors by risk: Assign risk levels to vendors based on their potential impact and likelihood of causing harm, enabling focused remediation efforts from onboarding through offboarding.
By fully mapping your supply chain, your organization can better anticipate attack vectors and proactively reduce exposure to cyber threats.
2. Prioritize High-Risk Vendors
Not all vendors pose the same level of risk. With hundreds or thousands of third-party relationships to manage, it is crucial to focus resources on the vendors that matter most.
Tier vendors by risk: Assign each vendor a risk level and implement tier-specific due diligence processes. High-risk vendors receive more frequent reviews and stringent controls.
Regularly reassess all vendors: Even low-risk vendors should undergo periodic assessments to ensure no hidden threats emerge.
Allocate resources efficiently: Prioritizing high-risk vendors allows security teams to scale their efforts without compromising overall coverage.
Prioritization ensures that your team’s efforts are aligned with the greatest threats, enhancing both efficiency and security posture.
3. Assess Third-Party Regulatory Compliance
Compliance assessment is critical, especially in regulated industries like healthcare, finance, and government sectors. Organizations remain fully responsible for protecting sensitive data, regardless of where a breach occurs in the supply chain.
Use standardized security questionnaires: Automate the distribution, collection, and analysis of compliance responses.
Evaluate certification and frameworks: Ensure vendors meet regulatory standards such as HIPAA, SOC 2, ISO 27001, or CCPA.
Continuous lifecycle assessment: Regulatory compliance should not end after onboarding. Vendors must be periodically reassessed to confirm ongoing adherence.
A thorough compliance evaluation ensures that your organization and your vendors maintain accountability and reduce regulatory exposure.
4. Practice Continuous Monitoring
A VRM program is not a one-time effort, it requires ongoing vigilance.
Real-time attack surface monitoring: Identify and report emerging cyber risks across third and fourth-party vendors.
Prompt remediation: Quickly address vulnerabilities and track vendor responses.
Automation for scalability: Leveraging automated VRM tools allows your security team to maintain constant visibility without overwhelming manual processes.
Continuous monitoring ensures that your organization remains proactive rather than reactive, strengthening overall cyber resilience.
Auditive: Streamlining Vendor Risk Management
For organizations aiming to take their vendor risk management to the next level, Auditive offers a comprehensive, user-friendly solution that simplifies and strengthens every stage of the vendor lifecycle. Whether you’re just starting a TPRM (Third-Party Risk Management) program or looking to enhance an existing one, Auditive provides tools to continuously monitor, assess, and engage with vendors efficiently.
AuditiveX: Free and Accessible TPRM
AuditiveX provides organizations with democratized access to a vendor risk management platform:
Instant Onboarding: Begin immediately without the need for demos or lengthy meetings.
Search and Monitor Vendors: Instantly access thousands of vendors, assess their risk and compliance, and continuously monitor their performance.
Dynamic Trust Profiles: Vendors can proactively share compliance information, keeping your network up-to-date.
In-App Communication: Simplifies collaboration with vendors directly within the platform.
Weekly Incident Monitoring: Stay informed about any incidents impacting your vendors without the overhead or noise of manual monitoring.
With AuditiveX, organizations gain a centralized hub for managing vendors while maintaining transparency and control across their supply chain.
AuditiveX Plus: Enterprise-Level Capabilities
For larger organizations or those with complex compliance requirements, AuditiveX Plus offers advanced features:
Unlimited Risk Assessments: Conduct thorough evaluations across multiple vendors with automated workflows.
Support for 20+ Frameworks: Includes SOC 2, ISO 27001, and other industry-standard frameworks.
Custom and Standard Vendor Questionnaires: Implement SIG, CAIQ, or VSA questionnaires to streamline regulatory compliance.
100+ Pre-Built Integrations: Integrate with tools such as Slack, Salesforce, and JIRA; custom APIs are also supported.
AI-Powered Automation: Automatically review vendors, prioritize high-risk parties, and ensure compliance consistently.
Advanced Reporting: Gain actionable insights and track vendor alignment in real time.
Seamless Integration with Existing Workflows
Auditive integrates smoothly with procurement and productivity tools, so teams don’t need to alter their existing workflows. From onboarding to continuous monitoring, every process becomes faster, more transparent, and easier to manage.
Proactive Trust and Transparency
By using Auditive, organizations can establish a Trust Center that builds confidence with both internal teams and external vendors. Real-time monitoring, dynamic risk profiles, and automated reporting foster accountability and strengthen vendor relationships.
Get Started Today
AuditiveX is free to join, requiring no meetings, demos, or upfront investment. For organizations ready to scale, AuditiveX Plus unlocks enterprise-level features that take vendor risk management to a new standard of efficiency and compliance.
Wrapping Up
Effectively creating a vendor management program is no longer optional, it is a critical strategy for mitigating risks, ensuring compliance, and driving operational efficiency. By implementing a structured vendor risk management program, organisations can gain full visibility into their vendor ecosystem, prioritize high-risk vendors, and continuously monitor for emerging threats. Leveraging technology like Auditive allows businesses to centralise vendor information, automate risk assessments, and maintain real-time compliance insights.
Establishing a Trust Center fosters transparency with both internal stakeholders and vendors, ensuring accountability and strengthening trust across your supply chain. By combining structured processes, automation, and proactive engagement, your organization can not only manage risks effectively but also enhance vendor relationships, improve operational resilience, and achieve long-term business success.
Start building or enhancing your vendor management program with Auditive.
Join AuditiveX for free to begin monitoring vendors instantly, or upgrade to AuditiveX Plus for enterprise-level TPRM capabilities. Ensure your vendor ecosystem is secure, compliant, and transparent.
FAQs
1. What is a vendor management program?
A vendor management program is a structured framework for managing vendor relationships, mitigating risks, ensuring compliance, and optimizing procurement processes throughout the vendor lifecycle.
2. Why is vendor risk management important?
Vendor risk management helps organizations identify, prioritize, and mitigate risks posed by third-party and fourth-party vendors, protecting sensitive data, ensuring regulatory compliance, and safeguarding business operations.
3. What is a Trust Center in vendor management?
A Trust Center is a centralized hub for transparency and communication, where vendors can share compliance information, security practices, and risk assessments, fostering trust and accountability with buyers.
4. How can technology improve vendor management programs?
Technology streamlines vendor onboarding, performance tracking, risk assessments, and continuous monitoring. Platforms like Auditive automate workflows, centralize vendor data, and provide actionable insights to improve efficiency and compliance.
5. How often should vendor risk be assessed?
Vendor risk should be assessed continuously, with regular evaluations and automated monitoring to detect emerging threats, ensure compliance, and address any security gaps proactively.