NIST Compliance Checklist Guide for 2026
In 2024, more than 70% of organizations surveyed reported using a recognized cybersecurity framework to structure their security efforts, and among those, the NIST Cybersecurity Framework (CSF) remained the most adopted standard.
That growing adoption underscores a simple truth: in a landscape of evolving threats and vendor dependencies, a common security framework can no longer be optional. It’s the backbone that brings consistency, clarity, and control to cybersecurity programs, no matter the scale, sector, or setup.
This guide shows how to apply a NIST-based checklist in a practical, scalable way, helping teams not only meet basic requirements but also build resilient, transparent security that adapts as risks evolve.
Before we dive in:
A NIST checklist must operate as a continuous system, not a one-time audit exercise.
Vendor risk management is a core part of maintaining real NIST alignment.
A Trust Center keeps controls, vendor evidence, and documentation verified and visible.
Continuous monitoring reduces the gap between “policy” and “actual security posture.”
Using the right tools reduces manual workload and increases the accuracy of NIST control mapping.
What NIST Compliance Really Means for You
If you're building or reviewing a NIST checklist, the first thing to understand is that NIST compliance isn’t a box-ticking routine; it’s about proving that your security controls follow the same standards used across U.S. federal agencies. NIST creates measurable, verifiable, science-backed requirements that help organizations avoid guesswork and build consistency into their security program.
Here’s what that means from your point of view:
No vague controls: NIST gives you specific, testable expectations so you always know what “secure enough” actually looks like.
A foundation built on proven sources: every NIST standard pulls from authoritative frameworks, security documents, and federal publications, so you aren’t relying on industry opinions or scattered best practices.
Clarity when handling federal or sensitive data: if you work with government agencies, contractors, or critical infrastructure, NIST becomes the baseline you’re judged against.
Alignment with FISMA: NIST is what federal bodies use to meet FISMA requirements, so following it ensures you avoid gaps that create administrative or operational friction later.
A structured way to validate your own controls: NIST prioritizes traceability and measurement, meaning your checklist becomes a reliable map of what’s working and what isn’t.
Rather than functioning as another framework to “get through,” a well-built NIST checklist helps you understand your security posture without ambiguity. It’s practical, predictable, and designed to reduce the risks that arise when teams rely on informal or inconsistent security methods.
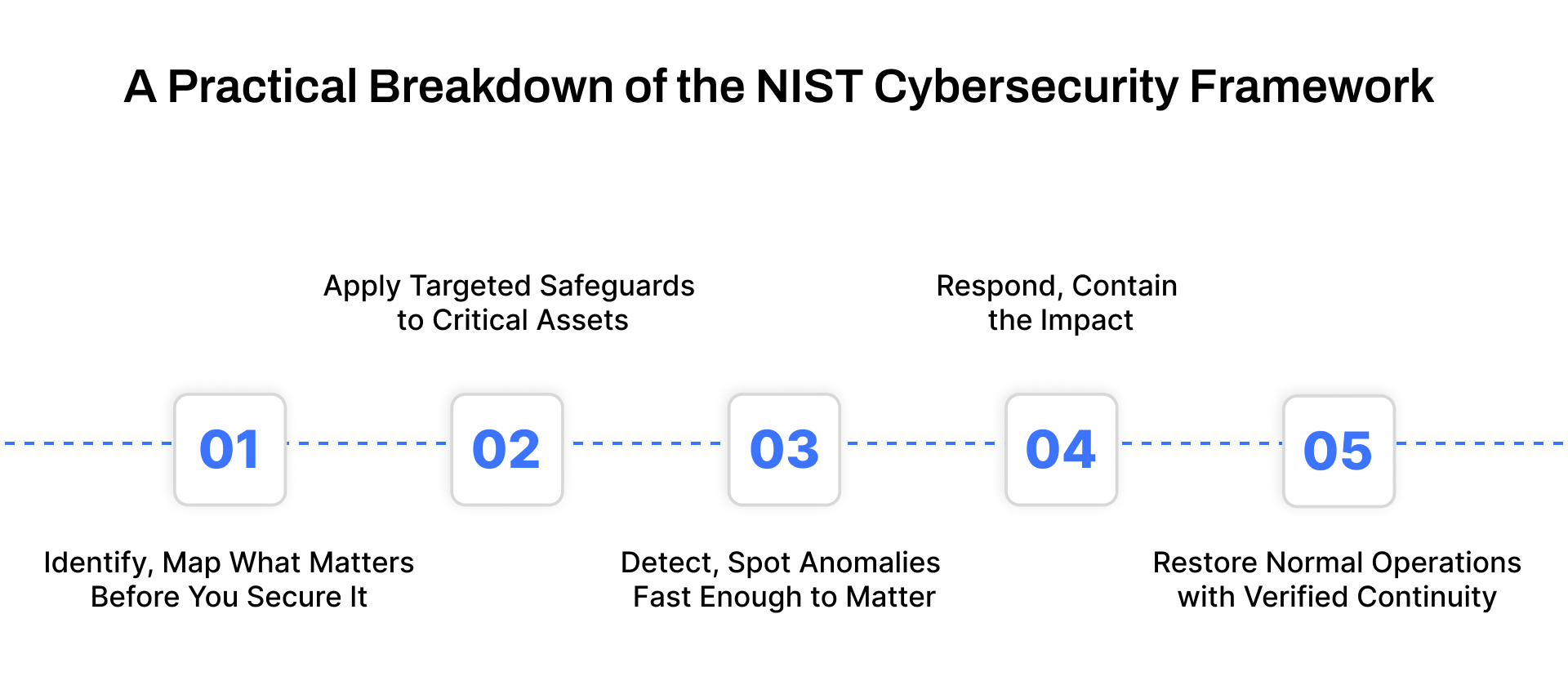
A Practical Breakdown of the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a structured way to strengthen security posture without guesswork. Instead of broad principles, it gives you a clear five-function model that directly translates into what needs to be secured, how to secure it, and how to recover when something breaks. Below is a refined NIST checklist-style breakdown grounded in real operational use cases.
1. Identify, Map What Matters Before You Secure It
Organizations can’t protect what they can’t see. The Identify function sets the baseline by defining which systems, data flows, assets, and vendors create the most exposure.
This stage covers:
Asset management
Business environment mapping
Governance
Risk assessment
Risk management strategy
A strong Identify phase ensures your cybersecurity plan targets the areas where failure would cause the greatest business impact.
2. Protect, Apply Targeted Safeguards to Critical Assets
Once priorities are clear, the Protect function defines how to shield high-value assets from compromise. It emphasizes verified access, human readiness, and resilient data controls, core elements in any effective 2026 NIST checklist.
This stage covers:
Identity and access management (IAM)
Workforce awareness and training
Data security
Preventive maintenance
Protective technologies
Information protection processes & procedures
The goal is to create defense mechanisms that reduce the likelihood of a damaging incident.
3. Detect, Spot Anomalies Fast Enough to Matter
The Detect function centers on real-time visibility and anomaly detection. You need systems that flag unusual events immediately, long before they become incidents.
This stage covers:
Anomalies and events
Continuous security monitoring
Detection processes
This phase ensures you’re not operating blind between point-in-time assessments.
4. Respond, Contain the Impact, and Prevent Escalation
The Respond function activates when an incident occurs. It defines how your teams assess the situation, coordinate communication, and contain impact swiftly.
This stage covers:
Response planning
Analysis
Mitigation
Communications
Improvements
A strong response cycle minimizes operational and reputational fallout.
5. Recover, Restore Normal Operations with Verified Continuity
The Recover function ensures the business bounces back quickly and stronger. It integrates proven restoration strategies and structured post-incident improvements.
This stage covers:
Recovery planning
Communications
Improvements
This is your blueprint for restoring full functionality and embedding resilience into future operations.
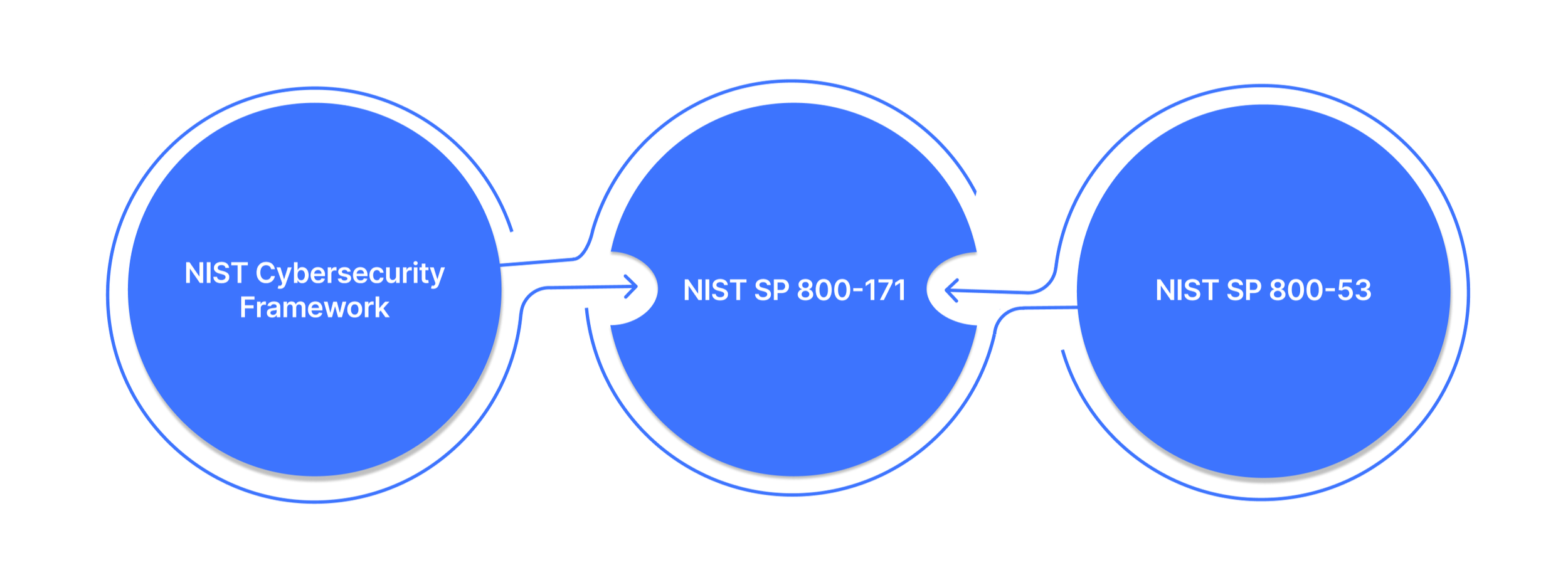
Choosing the Right NIST Framework for Your 2026 Security Strategy
NIST publishes one of the largest public libraries of security and privacy standards in the US. But for most teams building a 2026 NIST checklist, three frameworks consistently determine how they structure controls, documentation, and monitoring.
1. NIST Cybersecurity Framework (CSF): Enterprise-Wide Risk Reduction
The CSF is best suited for businesses that need a structured, repeatable approach to managing cybersecurity risk across the entire organization.
It is built around:
Five core functions: Identify, Protect, Detect, Respond, and Recover.
Profiles: Tailored to your industry and risk tolerance.
Implementation tiers: Indicate how mature your security program is.
CSF is ideal for organizations wanting measurable progress without the depth of federal-grade control catalogs.
2. NIST SP 800-171: Protecting CUI for Government Contractors
If your company handles Controlled Unclassified Information (CUI) under federal contracts, SP 800-171 is non-negotiable.
It defines:
110 requirements across 14 control families (access control, training, audit logs, incident response, etc.).
Mandatory safeguards that must be implemented before signing or renewing DoD or federal agreements.
This framework is purpose-built for manufacturers, defense suppliers, and any vendor that stores or transmits CUI.
3. NIST SP 800-53: Full-Scale Federal Control Framework
SP 800-53 is the most comprehensive NIST publication, used by U.S. federal agencies and contractors operating federal information systems.
Its scope includes:
Security + privacy controls mapped to FIPS 200 requirements.
Supporting publications like 800-53A (assessment procedures) and 800-53B (control baselines).
This framework is the foundation for high-assurance environments where risk management and continuous monitoring must be fully documented and defensible.
And if you need a way to operationalize these NIST requirements without building the workflows manually, Auditive centralizes controls, evidence, and vendor risks in one place, removing the overhead that usually slows NIST adoption.
Learn more about: What is Compliance Monitoring: Essential Guide for Definition & Importance
Why NIST Compliance Still Matters in 2026
Achieving NIST alignment isn’t just a regulatory checkbox; it creates structural advantages that compound over time. When done right, a NIST checklist becomes a roadmap for operational resilience and predictable security outcomes.
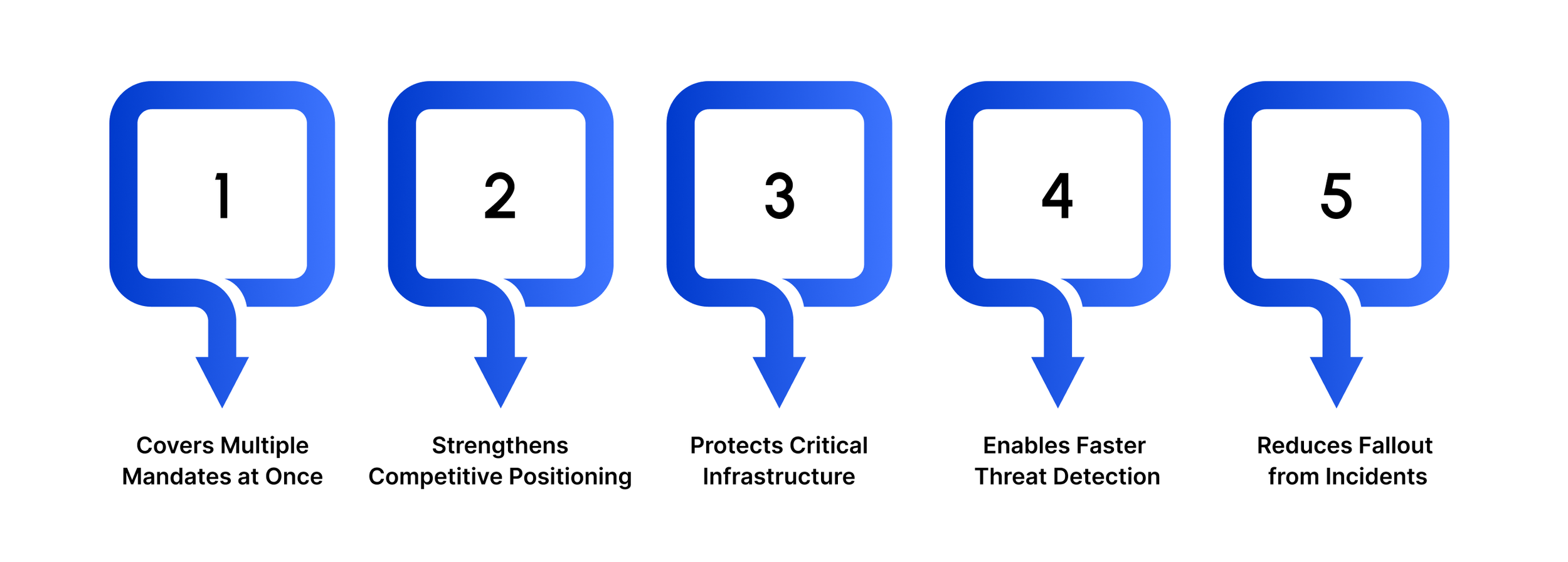
Key Benefits of Following a NIST Checklist
Covers multiple mandates at once
NIST’s control families map cleanly to HIPAA, FISMA, FedRAMP, and industry security baselines, reducing duplication and allowing teams to maintain one standardized security posture.
Strengthens competitive positioning
Organizations already aligned with NIST controls can qualify faster for federal, healthcare, and enterprise contracts, a direct growth lever for vendors handling sensitive data.
Protects critical infrastructure from real-world threats
NIST controls directly target high-frequency attack vectors, including ransomware, credential abuse, phishing infrastructure, misconfigurations, and privilege misuse.
Enables faster threat detection and response
Structured requirements around asset visibility, logging, incident response, and configuration management help teams uncover anomalies earlier and contain impact quicker.
Reduces fallout from incidents and legal exposure
Clear documentation, established response protocols, and verifiable technical controls reduce fines, liability, and recovery timelines when breaches occur.
Most teams struggle not with understanding NIST but with operationalizing it across dozens of systems, vendors, and workflows. Auditive solves this gap directly.
Auditive’s platform consolidates control monitoring, vendor risk signals, policy evidence, and Trust Center updates into one verifiable source of truth, something NIST’s own documentation emphasizes but does not provide. Instead of chasing spreadsheets or scattered tooling, security teams get a clear view of which NIST controls are met, which need remediation, and which require cross-team intervention.
This is the exact friction point NIST adopters feel and the exact operational layer Auditive removes.
How Auditive Makes Security Frameworks Work in Practice
Even the best framework fails if control evidence lives scattered across spreadsheets, inboxes, or forgotten vendor portals. Auditive solves that by combining automated monitoring with a unified Trust Center, turning frameworks from theory into daily operational clarity.
Live vendor posture tracking. AuditiveX continuously watches vendor status: certifications, control changes, incident reports, and more. That means any vendor-side change that could affect your compliance or security posture shows up instantly.
Centralized Trust Profiles for every vendor. Instead of chasing documents, you get a verified record of vendor controls, security posture, and evidence, all in one accessible place.
Automated, framework-agnostic assessments. Whether you follow SOC 2, ISO 27001, NIST, or a hybrid of standards, Auditive supports multiple frameworks and adapts to custom control sets, reducing duplication and saving time.
Cross-team workflows without friction. Procurement, security, and legal teams all see the same verified vendor data, approvals, and risk history. Integration with tools like Salesforce and JIRA means the system fits into your existing workflow, not the other way around.
Faster onboarding and consistent oversight. New vendors go through intake, assessment, and monitoring in days, not weeks, while existing vendors stay under continuous surveillance, ensuring frameworks remain enforced long-term.
Auditive transforms what many organizations treat as a periodic audit task into an ongoing, actionable vendor oversight system, one where compliance, risk posture, and vendor trust are transparent, live, and audit-ready.
Also read: Fundamentals and Best Practices in IT Information Risk Assessment
Final Thoughts
A NIST checklist only works when it moves beyond documentation and becomes part of how your organization actually detects, measures, and mitigates risk every day. That includes extending NIST controls to your third-party ecosystem, especially since vendor dependencies now introduce as much operational and security exposure as internal systems.
Treat the checklist as a living system: updated as assets change, informed by continuous monitoring, and supported by verified evidence rather than assumptions. When NIST is implemented this way, it strengthens both your internal security baseline and your external trust posture.
Schedule a demo with Auditive to see how automated monitoring, vendor oversight, and a live Trust Center keep every NIST requirement audit-ready all year, not just at audit time.
FAQs
1. Does NIST require vendor risk management?
Yes. NIST frameworks include controls that require evaluating and monitoring third-party service providers, since vendors can directly affect your security posture.
2. How often should NIST checklists be updated?
They should be reviewed whenever systems, vendors, or internal processes change — not just annually. NIST is built for continuous assessment.
3. Does NIST apply only to U.S. federal agencies?
No. Many private organizations adopt NIST because its controls strengthen security, reduce incidents, and map easily to other frameworks.
4. How does a Trust Center support NIST requirements?
A Trust Center centralizes verified evidence, policies, vendor documents, and control status, making NIST audits smoother and reducing redundant work.
5. Can tools automate parts of the NIST checklist?
Yes. Platforms like Auditive automate evidence collection, vendor assessments, and monitoring so teams can maintain NIST alignment with less manual burden.