ISO 27001 vs NIST: Key Differences Explained
Robust information security practices are no longer optional; they are essential.
Organizations face growing threats to sensitive data, regulatory pressures, and increasing expectations from clients and partners to demonstrate strong cybersecurity controls. Two of the most widely recognized frameworks for guiding these efforts are ISO 27001 and the NIST Cybersecurity Framework (CSF).
While both aim to strengthen an organization’s security posture, they differ in approach, structure, and application. Understanding these differences is crucial for businesses looking to implement a framework that aligns with their goals, compliance requirements, and operational realities. This guide explores the key features, principles, and distinctions between ISO 27001 and NIST, helping you make an informed choice for your organization.
Key Takeaways
ISO 27001 provides a globally recognized framework for information security, ideal for organizations seeking certification, structured controls, and comprehensive documentation.
NIST CSF is a flexible, prescriptive cybersecurity framework best suited for U.S.-based companies or start-ups looking for a practical, stepwise approach without high certification costs.
The choice between ISO 27001 and NIST CSF depends on organization size, maturity, geographic reach, compliance requirements, and available resources.
Implementing either framework strengthens risk management and overall cybersecurity posture, ensuring trust with partners, clients, and stakeholders.
Using tools like Auditive helps maintain continuous monitoring, transparency, and compliance across vendors and internal teams.
What is ISO 27001?
ISO 27001, developed by the International Organization for Standardization, is a globally recognized standard for establishing, implementing, and maintaining an Information Security Management System (ISMS). It provides organizations with a structured framework to manage sensitive information, safeguard data, and ensure business continuity. By following ISO 27001, companies can systematically identify risks, implement security controls, and continuously improve their information security practices.
At its core, ISO 27001 revolves around three fundamental principles:
Confidentiality: Ensuring that sensitive information remains private and accessible only to authorized personnel. This involves restricting access, using encryption, and protecting both company and customer data.
Integrity: Maintaining the accuracy and reliability of data. Information should remain unaltered except through authorized actions, with proper safeguards like secure backups and version control.
Availability: Guaranteeing that information and systems are accessible when needed. Organizations must ensure that critical data can be retrieved quickly and efficiently to support business operations.
By adhering to these principles, ISO 27001 helps organizations build trust with clients and partners while reducing the risk of data breaches and operational disruptions.
Stages of ISO 27001 Certification
Achieving ISO 27001 certification involves a structured process to ensure that your organization’s information security practices meet the rigorous standards set by ISO. The certification process typically unfolds in the following stages:
1. Documentation Review
The first stage involves a thorough evaluation of your organization’s existing policies, procedures, and Information Security Management System (ISMS). An independent auditor examines your documentation to determine how well your current practices align with ISO 27001 requirements. The goal is to confirm that your ISMS is robust and capable of managing security risks effectively.
2. On-Site Audit for Certification
Once your documentation passes the initial review, the auditor conducts a comprehensive on-site assessment. This phase involves a detailed scrutiny of your security controls, processes, and overall adherence to ISO 27001 standards. Upon successful completion of this audit, your organization becomes eligible for ISO 27001 certification.
3. Ongoing Surveillance and Recertification
Certification is not a one-time achievement. To maintain your ISO 27001 accreditation, regular surveillance audits are conducted, typically annually during the first two years. A recertification audit occurs in the third year to ensure continued compliance with the evolving ISO standards. This ongoing process helps organizations sustain a strong security posture over time.
Achieving ISO 27001 certification demonstrates a commitment to information security excellence, building trust with clients, partners, and stakeholders alike.
What is NIST?
The National Institute of Standards and Technology (NIST) is a U.S. federal agency under the Department of Commerce, dedicated to developing and promoting standards, guidelines, and best practices across technology, measurement, and cybersecurity. Among its many contributions, NIST is renowned for creating frameworks that help organizations strengthen their cybersecurity posture and manage digital risks effectively.
Its publications include special publications (SPs), detailed guidance documents, and the widely adopted NIST Cybersecurity Framework (CSF), along with the NIST SP 800 series, which provides comprehensive security controls for federal and private entities alike.
Five Core Functions of the NIST Cybersecurity Framework
The NIST CSF structures cybersecurity efforts around five primary functions, providing a holistic approach to managing risks:
Identify: Recognize and catalog critical assets, data, and contractual obligations. This helps define who has access to sensitive information and ensures that roles and responsibilities are clear.
Protect: Implement safeguards to prevent or limit the impact of potential security incidents. Measures may include access controls, internal policies, employee training, and encryption protocols.
Detect: Continuously monitor systems to identify anomalies, vulnerabilities, or breaches. Techniques include logging, network monitoring, and vulnerability scanning.
Respond: Prepare and execute incident response plans to contain threats, minimize damage, and reduce operational downtime. A clear response strategy ensures rapid, coordinated action.
Recover: Restore affected systems, assets, and services while implementing improvements to prevent future incidents. Recovery plans focus on business continuity and resilience.
These functions make NIST a practical, risk-based framework that can be adapted to organizations of any size or industry, helping them systematically manage cybersecurity threats.
Also read: NIST Cybersecurity Framework and Third-Party Risk Management Best Practices
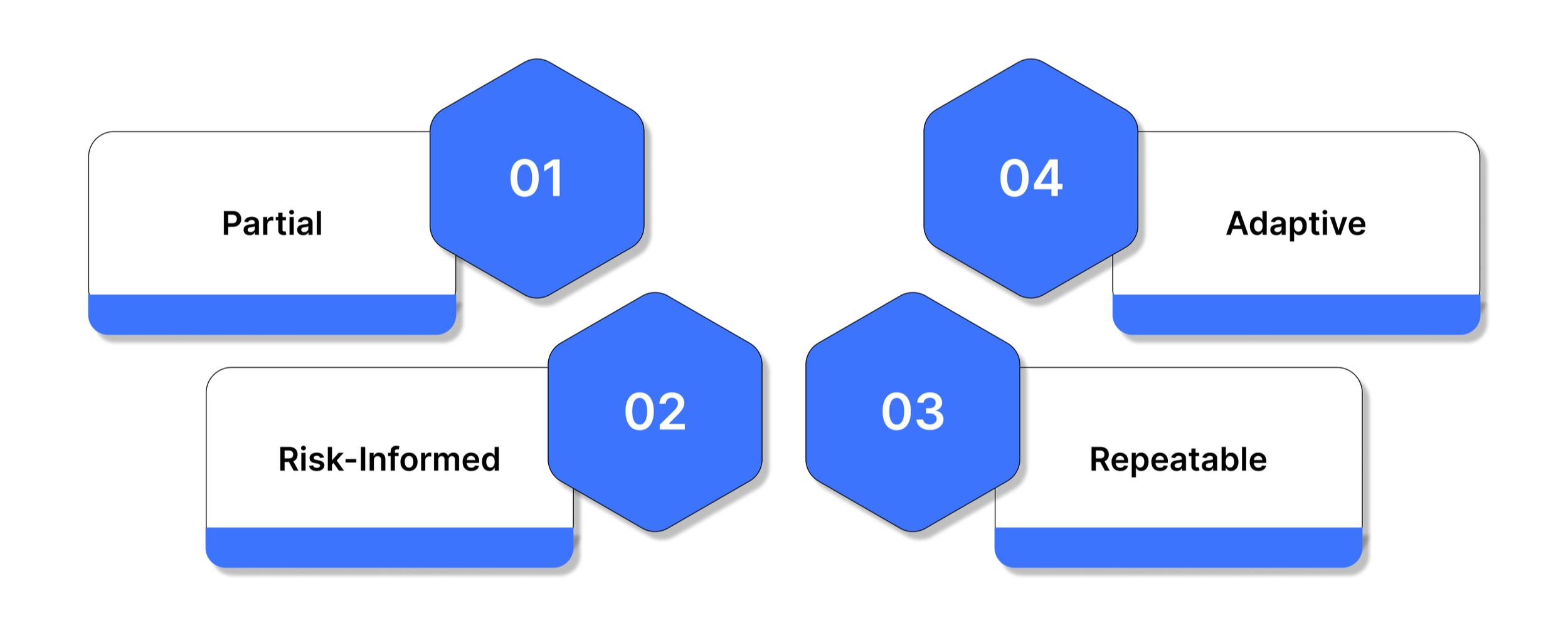
Four Tiers of Implementing NIST
The NIST Cybersecurity Framework (CSF) outlines a four-tiered model that helps organizations assess and enhance their cybersecurity maturity. Each tier reflects increasing levels of risk management sophistication and preparedness:
Tier 1: Partial
Organizations at this level typically have basic or informal cybersecurity practices. They respond to threats reactively, often lacking documented processes or coordinated strategies. Security measures are minimal, and risk management is largely ad hoc.
Tier 2: Risk-Informed
At this stage, organizations understand the cybersecurity risks they face but have only informal procedures to manage them. While there is awareness of potential threats, systematic processes for consistent risk management are still developing.
Tier 3: Repeatable
Organizations operating at Tier 3 have formalized policies and procedures to identify and respond to cybersecurity threats. These processes are consistently applied across the organization, though additional tools and technologies may be needed to fully automate and optimize risk management efforts.
Tier 4: Adaptive
Tier 4 represents the highest level of maturity. Organizations here have fully integrated cybersecurity programs with proactive risk management. They can quickly detect, respond to, and recover from incidents, continuously adapting and improving their processes to mitigate future threats effectively.
By understanding these tiers, organizations can assess their current cybersecurity posture, identify gaps, and plan a roadmap for gradual improvement towards an adaptive, resilient framework.
For organizations looking to elevate their vendor and third-party risk management, integrating NIST’s tiered approach through platforms like Auditive ensures continuous monitoring and adaptive security, keeping risk visibility high while reducing operational gaps.
Key Similarities Between ISO 27001 and NIST CSF
While ISO 27001 and the NIST Cybersecurity Framework (CSF) differ in structure and origin, they share several core principles that make them complementary in many cybersecurity programs. Both frameworks are fundamentally designed to help organizations safeguard sensitive information, mitigate cyber risks, and maintain a strong security posture against evolving threats.
Key similarities between ISO 27001 and NIST CSF include:
Focus on Risk Management: Both frameworks emphasize the identification, assessment, and mitigation of risks to ensure that critical data and systems are adequately protected. This risk-based approach allows organizations to prioritize resources and address the most pressing threats first.
Continuous Improvement: ISO 27001 and NIST CSF encourage a cycle of continual evaluation and improvement. By implementing structured processes, organizations can regularly assess their security posture, learn from incidents, and refine controls to adapt to emerging threats.
Global Applicability: While NIST originates from the U.S., both frameworks are flexible enough to be adopted worldwide. This makes them suitable for multinational organizations or businesses that must comply with international security standards.
Structured Documentation: Both ISO 27001 and NIST CSF require organizations to maintain documentation of their security processes, policies, and risk assessments. ISO 27001 is more prescriptive, detailing specific documents and records, whereas NIST provides flexibility, allowing organizations to tailor documentation to their unique needs.
Framework-Driven Approach: Both standards provide structured frameworks that guide organizations in developing, implementing, and refining cybersecurity programs. This structured approach helps ensure that security measures are comprehensive, consistent, and aligned with organizational goals.
In essence, while ISO 27001 and NIST CSF differ in terms of specificity and prescriptive requirements, they converge in their goal: enabling organizations to systematically protect their information assets while fostering continuous improvement and risk-aware decision-making.
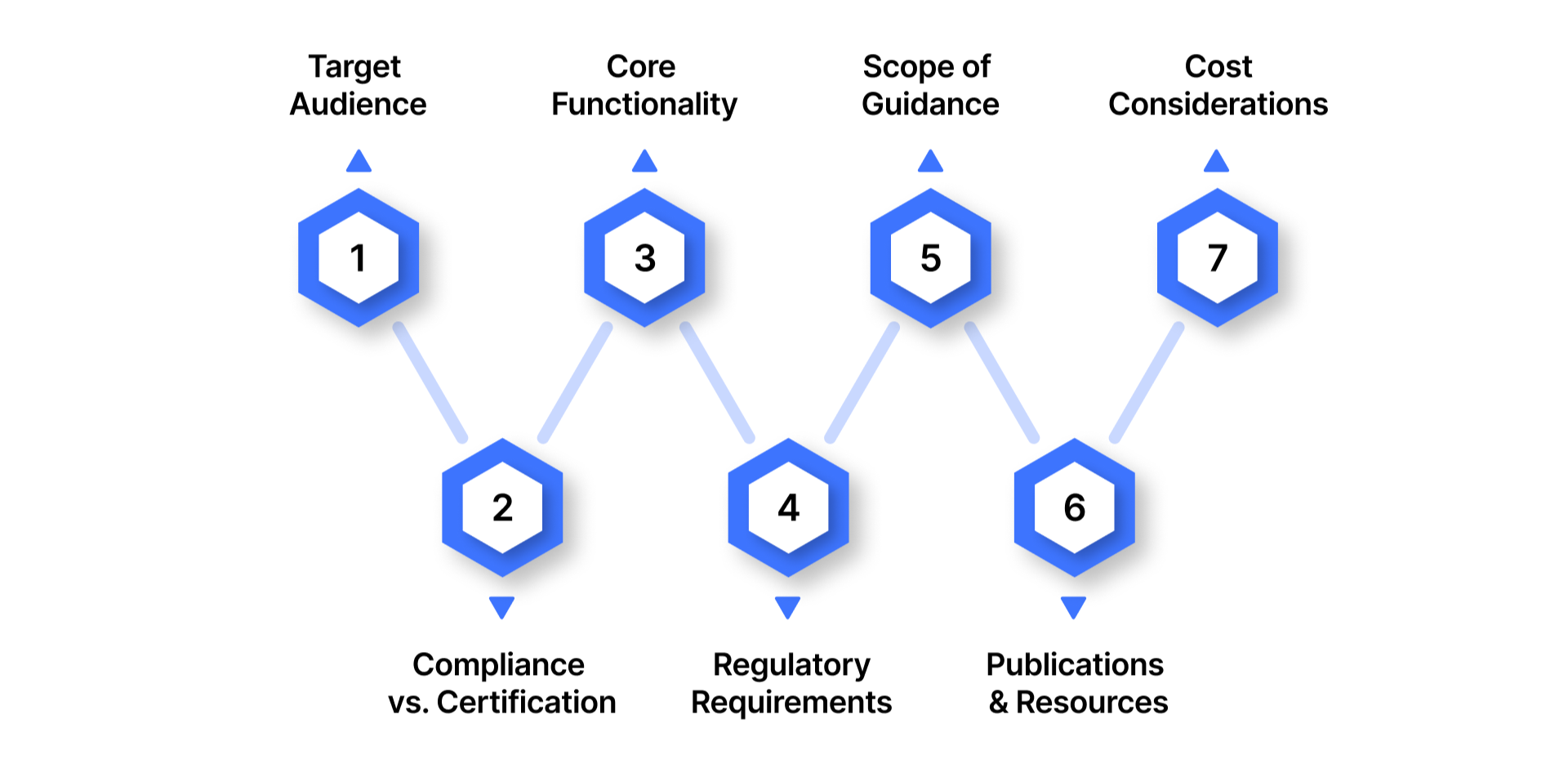
Key Differences Between NIST and ISO 27001
While both ISO 27001 and NIST CSF aim to strengthen an organization’s cybersecurity posture, they take different approaches and serve different purposes. Understanding these distinctions can help organizations select the framework best suited to their needs.
1. Target Audience
NIST CSF: Primarily designed for U.S. federal agencies and organizations that work closely with government entities. However, it is widely adopted by private sector companies seeking a flexible, high-level cybersecurity framework.
ISO 27001: Applicable across a wide range of industries and company sizes worldwide. It is suitable for organizations that want to demonstrate formal compliance with internationally recognized information security management standards.
2. Compliance vs. Certification
NIST CSF: Functions as a voluntary guideline rather than a formal certification. Organizations can implement it at their own pace, tailoring controls to their specific needs.
ISO 27001: Provides a structured approach to establishing, maintaining, and continually improving an Information Security Management System (ISMS). Organizations can pursue formal certification, which is externally audited and recognized globally.
3. Core Functionality
NIST CSF: Offers a comprehensive set of guidelines to manage cybersecurity risks, focused on improving cybersecurity maturity through its five core functions: Identify, Protect, Detect, Respond, and Recover.
ISO 27001: Focuses on creating a systematic and documented approach to managing information security risks. It emphasizes continuous monitoring, risk assessment, and implementing controls to protect sensitive data.
4. Mandate and Regulatory Requirements
NIST CSF: Mandatory for U.S. federal agencies and organizations that handle federal contracts. Private companies can adopt it voluntarily to strengthen cybersecurity practices.
ISO 27001: Not legally mandatory but often required by customers or partners to demonstrate adherence to international information security standards. Certification can enhance trust and credibility.
5. Scope of Guidance
NIST CSF: A high-level framework designed to guide organizations in improving cybersecurity measures. It is flexible, allowing adaptation to organizational needs without prescribing a fixed set of controls.
ISO 27001: Provides a prescriptive, structured methodology for establishing, maintaining, and auditing an ISMS, ensuring comprehensive management of information security risks.
6. Publications and Resources
NIST CSF: Comprises multiple publications and guidelines addressing different aspects of cybersecurity, offering detailed recommendations but requiring interpretation and adaptation.
ISO 27001: Presented as a single publication detailing requirements for an ISMS, supported by additional guidance documents for implementation and certification.
7. Cost Considerations
NIST CSF: Free to use and implement, making it accessible for organizations of all sizes. Implementation costs are primarily internal, such as training and process adaptation.
ISO 27001: Typically involves costs for training, documentation, and third-party audits. Certification fees vary depending on the size and complexity of the organization.
The table below highlights the key differences between NIST CSF and ISO 27001 and provides an overview for organizations to understand which framework aligns better with their cybersecurity and compliance needs.
| Feature | NIST CSF | ISO 27001 |
|---|---|---|
| Target Audience | U.S. federal agencies and organizations working with them; voluntary adoption by private companies | Organizations of any size and sector worldwide |
| Compliance / Certification | Voluntary guideline; no formal certification | Formal certification available; globally recognized ISMS standard |
| Function | High-level framework for managing and improving cybersecurity measures | Systematic approach to establishing, maintaining, and auditing an ISMS |
| Mandate | Mandatory for federal agencies; voluntary for others | Not legally mandatory; often required by customers or partners |
| Scope | Flexible, high-level guidance with five core functions (Identify, Protect, Detect, Respond, Recover) | Prescriptive methodology with structured controls and continuous monitoring |
| Publications | Multiple separate guidelines addressing various aspects of cybersecurity | Single standard publication with supporting guidance documents |
| Cost | Free to implement; internal costs only | Costs for training, documentation, and third-party audits; certification fees apply |
Learn more about: NIST Risk Management Framework: Steps and Overview Guide
How to Choose Between ISO 27001 vs NIST for Your Organization
Selecting the right cybersecurity framework depends on multiple factors, including your organization’s maturity, geographic reach, compliance obligations, and budget. Here are some key considerations to guide your decision:
1. Organizational Maturity
Established organizations often benefit from ISO 27001 certification to demonstrate their commitment to robust information security and build customer confidence. Start-ups or smaller businesses, on the other hand, may find NIST CSF more practical, offering a structured approach to assess and strengthen cybersecurity without extensive upfront investment.
2. Geographic Presence
For companies operating internationally, ISO 27001 provides widely recognized security standards that can enhance trust and market access globally. Conversely, U.S.-based organizations or those engaging with federal agencies may find NIST CSF, including NIST 800-53 and NIST 800-171, more relevant for regulatory compliance.
3. Prescriptiveness
ISO 27001 provides a flexible framework with a comprehensive security control structure, leaving room for organizations to adapt it to their needs. NIST, however, is highly prescriptive, with detailed guidance on controls and risk management, making it ideal for organizations seeking step-by-step instructions.
4. Compliance Requirements
Consider whether adherence to a specific framework is mandatory. NIST standards are often required for federal agencies or organizations handling controlled, unclassified information. ISO 27001 is voluntary but can enhance security practices and customer confidence where certification is valued.
5. Documentation Preferences
ISO 27001 requires extensive documentation, which can be resource-intensive but ensures a structured approach. NIST allows more flexibility, enabling organizations to maintain documentation in a way that aligns with internal processes while still meeting regulatory and security needs.
6. Cost Considerations
Achieving ISO 27001 certification can range from $50,000 to $200,000, depending on company size and existing controls, with a certification validity of three years. NIST CSF, however, is free to implement, allowing organizations, especially start-ups, to adopt security controls at their own pace without heavy financial investment.
Ultimately, the right choice depends on your organization’s objectives, risk profile, and strategic priorities. For companies seeking a streamlined approach to risk management and continuous visibility into compliance, integrating tools like Auditive can simplify the implementation of either framework, offering real-time insights and a centralized approach for monitoring vendor and internal security controls.
Streamline Compliance and Risk Management with Auditive
Adopting ISO 27001 or NIST CSF is only the first step; maintaining ongoing compliance and managing third-party risks effectively is where many organizations face challenges. Auditive offers a centralized platform that simplifies these processes, providing visibility, automation, and actionable insights across your entire vendor ecosystem.
Key Benefits of Using Auditive:
Centralized Risk Management: Track all vendors and third parties in one place, ensuring continuous oversight of security postures aligned with ISO 27001 or NIST frameworks.
Continuous Monitoring: Receive real-time alerts on changes in vendor compliance, vulnerabilities, or incidents, helping you respond swiftly to potential threats.
Transparency: Maintain a secure, centralized hub where vendors can share compliance documentation, certificates, and risk profiles, reducing manual follow-ups and enhancing trust.
Workflow Automation: Automate assessments, approvals, and reporting processes, saving time while ensuring no critical steps are overlooked.
Integration with Existing Systems: Seamlessly connect Auditive with procurement, IT, and workflow management tools to streamline operations without disrupting existing processes.
Scalable Solutions: Whether you are a start-up implementing NIST CSF or a multinational pursuing ISO 27001 certification, Auditive scales to meet your organization’s compliance and risk management needs.
By leveraging Auditive, organizations can not only simplify ISO 27001 or NIST implementation but also maintain proactive risk assessment.
Summary
Choosing between ISO 27001 and NIST CSF depends on your organization’s size, maturity, regulatory obligations, geographic presence, and budget. ISO 27001 is ideal for organizations seeking internationally recognized certification with comprehensive documentation and structured security controls. NIST CSF is more flexible, cost-effective, and particularly suited for U.S.-based organizations or start-ups looking for a practical, stepwise approach to cybersecurity.
Beyond selection, ongoing risk management and transparent reporting are critical. Platforms like Auditive help organizations monitor vendor compliance continuously, automate risk assessments, and maintain a single source of truth for compliance documentation. By integrating ISO 27001 or NIST CSF into your broader risk management ecosystem, your organization strengthens security, builds trust with partners and customers, and ensures long-term resilience.
Book a Demo with Auditive today to see how ISO 27001 or NIST implementation can be managed efficiently and effectively.
FAQs
1. Can a company follow both ISO 27001 and NIST CSF simultaneously?
Yes, many organizations use ISO 27001 for international certification while implementing NIST CSF for detailed, prescriptive guidance, ensuring comprehensive cybersecurity coverage.
2. How long does it take to achieve ISO 27001 certification?
Typically, achieving ISO 27001 certification takes 6–12 months, depending on the organization’s size, existing security controls, and documentation readiness.
3. Is NIST CSF mandatory for all organizations?
No, NIST CSF is voluntary for most companies but mandatory for U.S. federal agencies and organizations handling controlled unclassified information.
4. Which solution is more cost-effective for small businesses?
NIST CSF is generally more cost-effective for start-ups and small businesses since it is free and can be implemented gradually, unlike ISO 27001, which has certification and compliance costs.