Enterprise Security Risk Management Guide and Concepts
Security is no longer just an IT concern; it’s a core business function.
Organizations face a constantly evolving landscape of risks, from cyberattacks and insider threats to compliance demands and operational disruptions. What makes the challenge even greater is that these risks are not isolated; they directly affect business continuity, reputation, and customer trust.
This is where Enterprise Security Risk Management (ESRM) comes in. Unlike traditional security models that focus narrowly on technology or compliance, ESRM integrates security into the broader risk management framework of the organization. It ensures that every security decision, whether about data protection, access control, or vendor partnerships is aligned with business priorities.
The result is a proactive, business-driven approach that not only strengthens resilience but also empowers leadership to make informed, risk-aware decisions.
Key takeaways:
ESRM integrates security into business strategy, making risk management a driver of resilience and growth.
Common challenges include silos, resistance to change, and poor data quality, but frameworks and automation help overcome them.
Vendor risk management is critical, as third-party risks can significantly impact enterprise security posture.
Trust centers enhance transparency, ensuring customers and regulators see proof of compliance and accountability.
With platforms like Auditive, organizations can unify ESRM, scale efficiently, and build lasting trust with stakeholders.
What Is Enterprise Security Risk Management?
Enterprise Security Risk Management (ESRM) is a strategic, business-aligned framework for protecting people, assets, and operations from a wide spectrum of threats. Unlike traditional security approaches that often operate in silos, ESRM takes a holistic view of risk, treating security as a core business function that directly impacts organizational resilience and success.
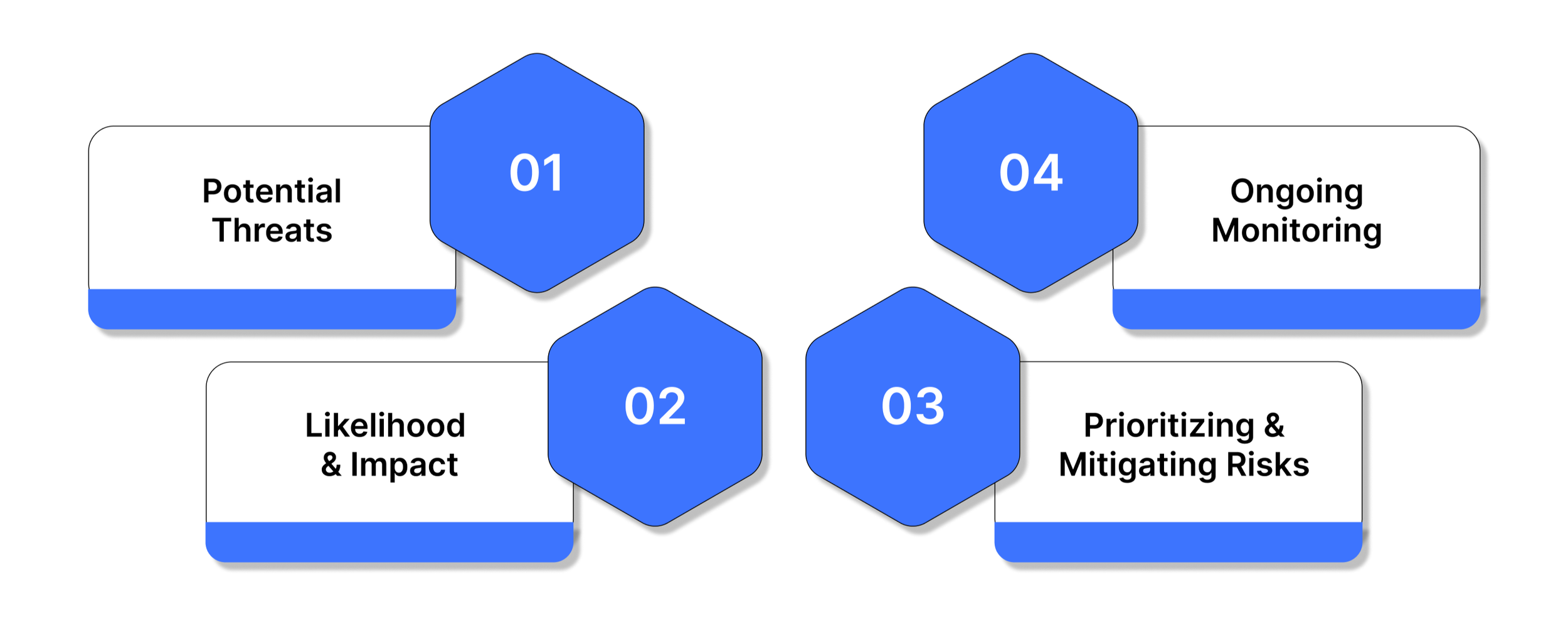
At its core, ESRM involves four fundamental steps:
Identifying potential threats – from natural disasters, physical intrusions, and supply chain disruptions to market fluctuations, political instability, and cyberattacks.
Assessing likelihood and impact – determining which risks pose the most significant threat to business operations and reputation.
Prioritizing and mitigating risks – allocating resources to the most critical areas, ensuring that controls are both effective and aligned with business objectives.
Ongoing monitoring and adaptation – recognizing that risks evolve constantly and require continuous evaluation.
What makes ESRM particularly complex is the scale and interconnected nature of modern risks. Businesses today don’t just face millions of potential threats, they face threats that overlap across digital, physical, and operational domains. For example, a cyberattack on a vendor could cause a supply chain disruption, leading to financial loss and reputational damage.
By adopting ESRM, organizations move away from a fragmented “checklist” approach and instead embed security into enterprise-wide decision-making. This ensures that risk management is not only about defense, but also about enabling the organization to pursue growth and innovation with confidence.
Also Read: Managing risk in businesses
Key Risk Management Principles for Effective ESRM
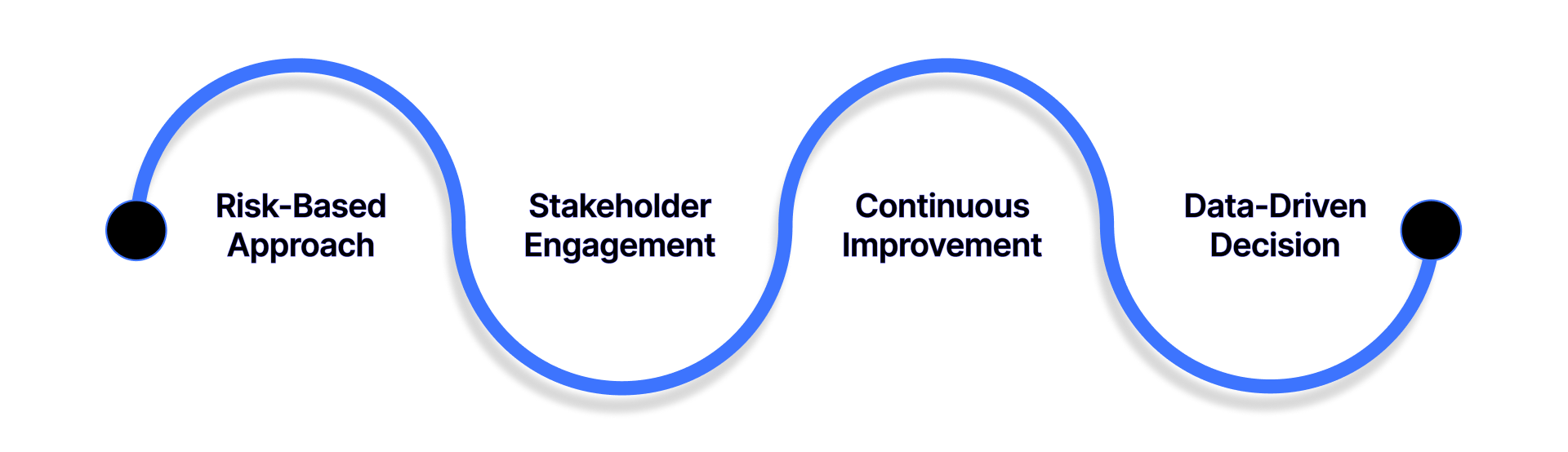
A successful Enterprise Security Risk Management (ESRM) program requires more than deploying security tools or reacting to incidents. It must be built on clear principles that align security priorities with business objectives. The ASIS ESRM Guideline offers a strong foundation, outlining four essential pillars that shape effective risk management strategies:
1. Risk-Based Approach
Every organization has limited resources, which makes prioritization critical. A risk-based approach ensures that security measures focus on protecting the assets and operations that matter most. Instead of applying blanket security controls, risks are evaluated based on their likelihood, potential impact, and alignment with business goals. This principle allows leaders to channel investments where they will have the greatest effect, such as safeguarding sensitive data, ensuring regulatory compliance, or protecting critical infrastructure.
2. Stakeholder Engagement
Security is no longer confined to a single department, it is a shared responsibility across the enterprise. Effective ESRM encourages collaboration between executives, employees, external vendors, and even customers when appropriate. By involving stakeholders at every level, organizations can foster transparency, build trust, and ensure that security initiatives support broader organizational priorities. This engagement also reduces resistance to change, since stakeholders understand how risk management decisions affect their roles and objectives.
3. Continuous Improvement
The risk landscape is constantly evolving, and a static program quickly becomes ineffective. Continuous improvement means regularly reviewing, testing, and refining ESRM strategies to stay ahead of emerging threats. Feedback loops, post-incident reviews, and lessons learned from past experiences help organizations adapt quickly. This principle also supports a culture of resilience, where the organization treats every challenge as an opportunity to strengthen security practices and prepare for the future.
4. Data-Driven Decision-Making
Modern enterprises generate vast amounts of information, and utilizing this data is key to informed decision-making. ESRM relies on metrics, analytics, and real-time insights to identify vulnerabilities, monitor risks, and measure the effectiveness of security programs. A data-driven approach minimizes guesswork, ensures accountability, and enables leadership to justify security investments with clear evidence. By aligning decisions with data, organizations not only reduce risk but also gain confidence in the efficiency and outcomes of their security initiatives.
Learn more about: Risk Monitoring Practices
How to Build a Effective ESRM Program for Security Management
Balancing business growth with the need to safeguard employees, assets, customers, and data is one of the biggest challenges leaders face today. The reality is that threats come from every direction, cybercriminals, market instability, supply chain disruptions, even insider risks. Focusing only on defense can limit opportunities, but ignoring security can expose organizations to catastrophic losses. The answer lies in Enterprise Security Risk Management (ESRM), a framework that aligns protection strategies with business priorities.
Here’s a step-by-step approach to building an ESRM program that is both resilient and adaptable:
Step 1: Identify Risks
Effective ESRM begins with understanding the full range of risks, beyond generic “cyber threats” or “compliance issues.” Organizations need to get granular. One way to achieve this is by conducting a SWOT analysis (Strengths, Weaknesses, Opportunities, Threats).
Strengths – existing advantages such as strong security controls, reputation, or skilled teams.
Weaknesses – gaps like resource constraints, outdated tools, or lack of expertise.
Opportunities – external factors that could boost security or efficiency, such as new technologies or strategic partnerships.
Threats – external risks including regulatory changes, natural disasters, or competitive pressures.
While SWOT highlights known challenges, emerging or unpredictable risks require additional tools such as threat intelligence software. These platforms use analytics, machine learning, and predictive modeling to spot risks early and guide smarter decisions.
Step 2: Assess and Prioritize Risks
Not all risks are created equal. A strong ESRM program weighs risks based on likelihood and impact.
Some risks, like phishing attempts, may occur frequently but seem small. Yet repeated incidents can accumulate into major breaches.
Others, such as the sudden loss of a key executive, may be rare but carry massive consequences.
Using a risk matrix helps categorize threats into high, medium, and low priorities. This ensures leadership focuses resources where they matter most.
Step 3: Develop Risk Mitigation Strategies
Once risks are prioritized, mitigation comes into play. Strong ESRM strategies combine preventive, detective, and corrective controls:
Preventive controls – Firewalls, access controls, encryption, supplier diversification, or facility security.
Detective controls – Continuous monitoring, incident logging, compliance checks, or anomaly detection systems.
Corrective controls – Incident response playbooks, disaster recovery, business continuity plans, or backup infrastructure.
Mitigation is not just about technology. It includes preparing people and processes with resilience testing, penetration exercises, and tabletop drills, ensuring teams know how to act when risks materialize.
Step 4: Monitor and Report Continuously
Security risks evolve every day, which makes ongoing monitoring and reporting critical. Tracking key performance indicators, such as mean time to detect (MTTD), mean time to respond (MTTR), and security control effectiveness, provides a clear view of performance.
Regular after-action reviews ensure lessons learned from incidents or simulations translate into stronger defenses. ESRM also emphasizes intelligence-driven decision-making: using data not only to react to risks, but to anticipate them before they occur.
As security leader Bridget Guerrero notes, resilience depends on the “Three C’s”, collaboration, curiosity, and continual improvement. Security is not static. By keeping ESRM adaptive and business-aligned, organizations can strike the balance between growth and protection.
As threats evolve and security demands intensify, enterprises need partners who can transform ESRM from theory into action. Auditive provides that transformation.
Challenges in Implementing ESRM
Adopting Enterprise Security Risk Management (ESRM) is not simply about adding another security framework, it represents a fundamental shift from siloed, reactive security measures to a unified, business-driven strategy. This transformation requires strong alignment between technical teams, business leaders, and compliance stakeholders. However, many organizations encounter roadblocks during implementation.
Below are the most common challenges and practical strategies to overcome them:
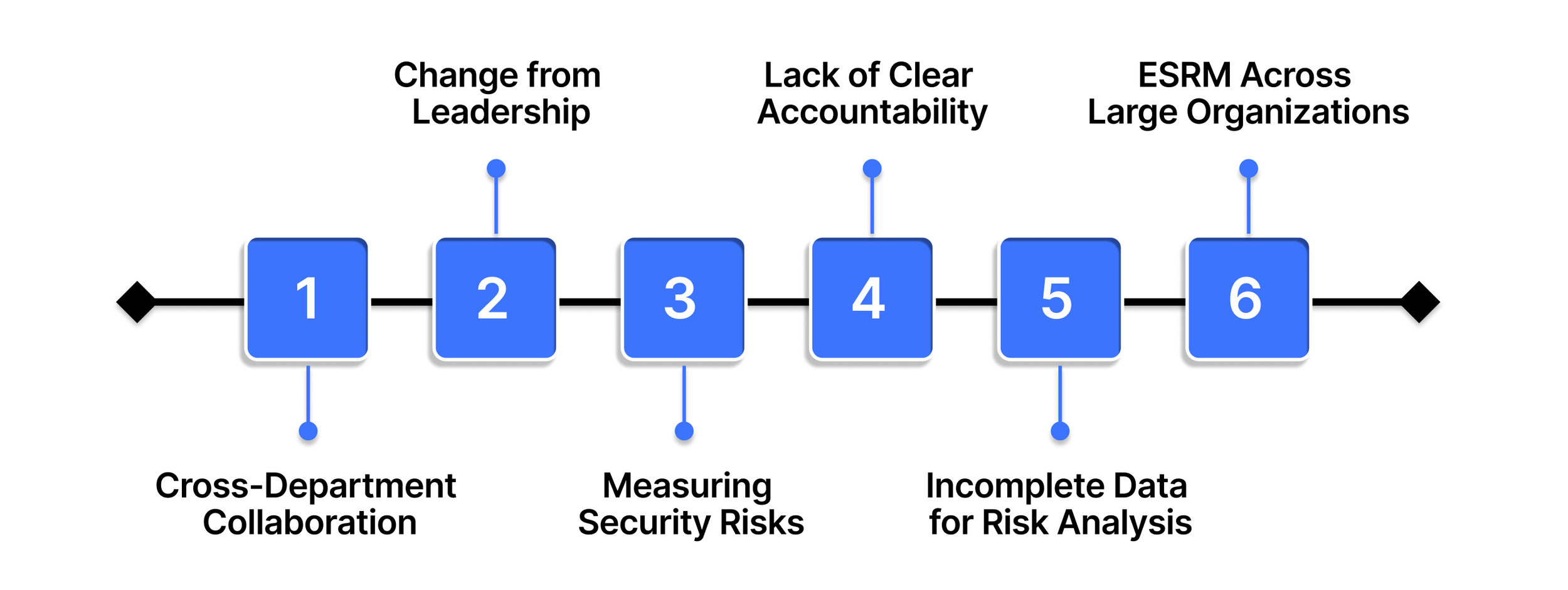
1. Lack of Cross-Department Collaboration
Challenge: Security responsibilities often remain fragmented across IT, operations, compliance, and legal teams, creating blind spots.
Solution: Establish a centralized risk management committee that includes representatives from IT, legal, compliance, and operations. These members act as liaisons to the security operations center, ensuring consistent communication, alignment, and enterprise-wide transparency.
2. Resistance to Change from Leadership or Staff
Challenge: Business leaders and employees may view ESRM as an additional burden rather than a value driver.
Solution: Demonstrate the business benefits of ESRM by linking it directly to reduced risk, improved efficiency, and cost avoidance. Regular training and workshops help address misconceptions and reinforce how ESRM integrates smoothly with existing workflows.
3. Difficulty in Defining and Measuring Security Risks
Challenge: Without a clear method to quantify security risks, organizations struggle to prioritize investments.
Solution: Using industry-recognized frameworks such as NIST 800-30, ISO 27001, or FAIR to standardize risk assessments. Complement this with automated tracking tools to provide ongoing visibility and data-driven insights.
4. Lack of Clear Accountability for Security Risks
Challenge: When ownership of security risks is unclear, gaps in responsibility can delay response times and weaken governance.
Solution: Assign risk owners for each critical area, ensuring that accountability is tied directly to asset owners. Define these roles in organizational policies and incorporate accountability into performance evaluations.
5. Inconsistent or Incomplete Data for Risk Analysis
Challenge: Risk analysis becomes unreliable when based on fragmented or outdated information.
Solution: Standardize data collection using SIEM platforms, automated threat intelligence feeds, and compliance tracking systems. Conduct regular audits and reporting cycles to validate data integrity and support informed decision-making.
6. Challenges in Scaling ESRM Across Large Organizations
Challenge: Expanding ESRM beyond pilot projects to enterprise-wide adoption often overwhelms resources.
Solution: Take a phased approach, beginning with high-risk business units before extending across the enterprise. Cloud-based security platforms and automation tools can accelerate scalability while reducing complexity.
Overcoming these challenges requires more than frameworks, it calls for continuous monitoring, integrated reporting, and adaptive risk intelligence. This is where platforms like Auditive provide a decisive advantage. By unifying security data, automating risk assessments, and offering real-time visibility into vulnerabilities, Auditive empowers organizations to operationalize ESRM effectively.
How Auditive Strengthens Enterprise Security Risk Management
Building an Enterprise Security Risk Management (ESRM) program is not just about frameworks, it’s about ensuring that risk identification, accountability, and resilience are embedded across the organization. This is where Auditive plays a vital role.
Auditive provides businesses with the tools to manage risk visibility, vendor risk management, and compliance alignment in one place. By centralizing data and insights, organizations can break down silos between departments and strengthen decision-making at every level.
Key capabilities Auditive brings to ESRM include:
Centralized Risk Monitoring – Real-time dashboards to track risks across IT, vendors, and operational workflows.
Vendor Risk Management Integration – Assess, monitor, and manage third-party risks seamlessly to prevent gaps in security posture.
Automated Reporting & Analytics – Save time while ensuring consistent, accurate reporting for regulatory compliance and executive visibility.
Trust Center Support – Enable organizations to demonstrate accountability and transparency by consolidating compliance certifications and risk documentation.
Scalability & Flexibility – Designed to adapt as businesses grow, allowing phased ESRM adoption without overwhelming existing security teams.
Also read about: Third Party Contract Management Best Practices
With Auditive, enterprises can move from reactive security measures to proactive, strategic risk management, ensuring that ESRM becomes a driver of trust, resilience, and long-term value.
Wrapping Up
Enterprise Security Risk Management is no longer an optional layer of protection, it’s the backbone of building resilient, trustworthy businesses in a dynamic threat landscape. From aligning security with business objectives to overcoming challenges like siloed processes and inconsistent data, ESRM helps organizations transform security into a strategic enabler.
However, the effectiveness of ESRM relies on the right tools, frameworks, and cultural mindset. This is where solutions like Auditive step in, providing centralized risk monitoring, vendor risk management, automated analytics, and a trust center to ensure transparency and accountability. By applying these capabilities, organizations not only safeguard operations but also foster confidence among customers, partners, and regulators.
The future of security is proactive, integrated, and transparent. Organizations that invest in ESRM today position themselves for sustained growth and resilience tomorrow.
Partner with Auditive to unify risk management, strengthen your trust center, and gain confidence in every business decision.
FAQs
1. What is Enterprise Security Risk Management (ESRM)?
ESRM is a business-focused approach to security that integrates risk management into overall business strategy, ensuring that security decisions align with organizational goals.
2. Why is ESRM better than traditional security approaches?
Traditional security is often siloed and reactive, while ESRM provides a holistic, proactive framework that aligns with business needs and manages risks enterprise-wide.
3. How does vendor risk management fit into ESRM?
Vendors are a major source of security risk. ESRM incorporates vendor risk management to evaluate, monitor, and mitigate third-party threats consistently.
4. What role does a trust center play in ESRM?
A trust center consolidates compliance certifications, policies, and risk documentation, enabling transparency with stakeholders and building long-term trust.
5. Can ESRM scale with large enterprises?
Yes. ESRM can be phased in across departments, starting with high-risk areas and expanding with cloud-based platforms and automation for scalability.