Identifying and Managing Supply Chain Vulnerabilities
A resilient supply chain is more than a competitive advantage; it’s a business imperative. But as global networks become more complex and interdependent, even a single point of failure can cascade into widespread disruption.
From geopolitical instability and cyberattacks to natural disasters and vendor insolvencies, supply chain vulnerability is no longer hypothetical; it’s a daily operational risk.
For organizations looking to maintain stability, ensure compliance, and safeguard customer trust, identifying and managing these vulnerabilities isn’t optional. It’s a critical component of enterprise risk management and long-term strategic planning.
This blog will explore what supply chain vulnerability really means, how it affects business continuity, and which strategies can help mitigate these risks before they escalate.
Overview
Supply chain vulnerability refers to weaknesses that can disrupt the flow of goods, data, or services across your supplier network.
Common threats include cyberattacks, geopolitical risks, natural disasters, and supplier failures.
These vulnerabilities can lead to financial losses, compliance breaches, and reputational damage.
Mitigation strategies include supplier vetting, diversification, cybersecurity investment, and real-time monitoring.
Auditive helps organizations identify and manage these risks with robust vendor risk management tools and a centralized Trust Center.
What Is Supply Chain Vulnerability?
Supply chain vulnerability refers to the degree to which a supply chain is exposed to potential disruptions, threats, or breakdowns that can negatively impact operations. These vulnerabilities can surface at any stage, whether in sourcing raw materials, manufacturing, logistics, warehousing, or last-mile delivery.
What makes a supply chain vulnerable isn’t just external shocks; it’s the system’s inability to absorb and recover from them. A lack of redundancy, poor visibility, overly centralized operations, or dependency on single-source suppliers can all increase susceptibility to disruption.
In highly interconnected and globalized environments, even minor vulnerabilities can escalate into major challenges, delaying shipments, increasing costs, or compromising customer commitments. For industries like shipping and logistics, where timing and coordination are critical, addressing supply chain vulnerability is key to operational efficiency and long-term resilience.
Why Is Understanding Supply Chain Vulnerability Important?
Understanding where your supply chain is exposed allows you to act before disruption strikes. It’s not just about prevention; it’s about readiness.
Risk Mitigation: Spotting vulnerabilities early enables proactive, targeted strategies.
Business Continuity: Resilient supply chains maintain operations during crises.
Competitive Edge: Faster response and recovery give you an advantage when others are scrambling.
Cost Control: Avoiding emergency fixes saves time, money, and resources.
Stakeholder Trust: Customers, partners, and investors value reliability and resilience.
In high-risk sectors like shipping and logistics, vulnerability assessments are no longer optional; they’re a standard for operational excellence.
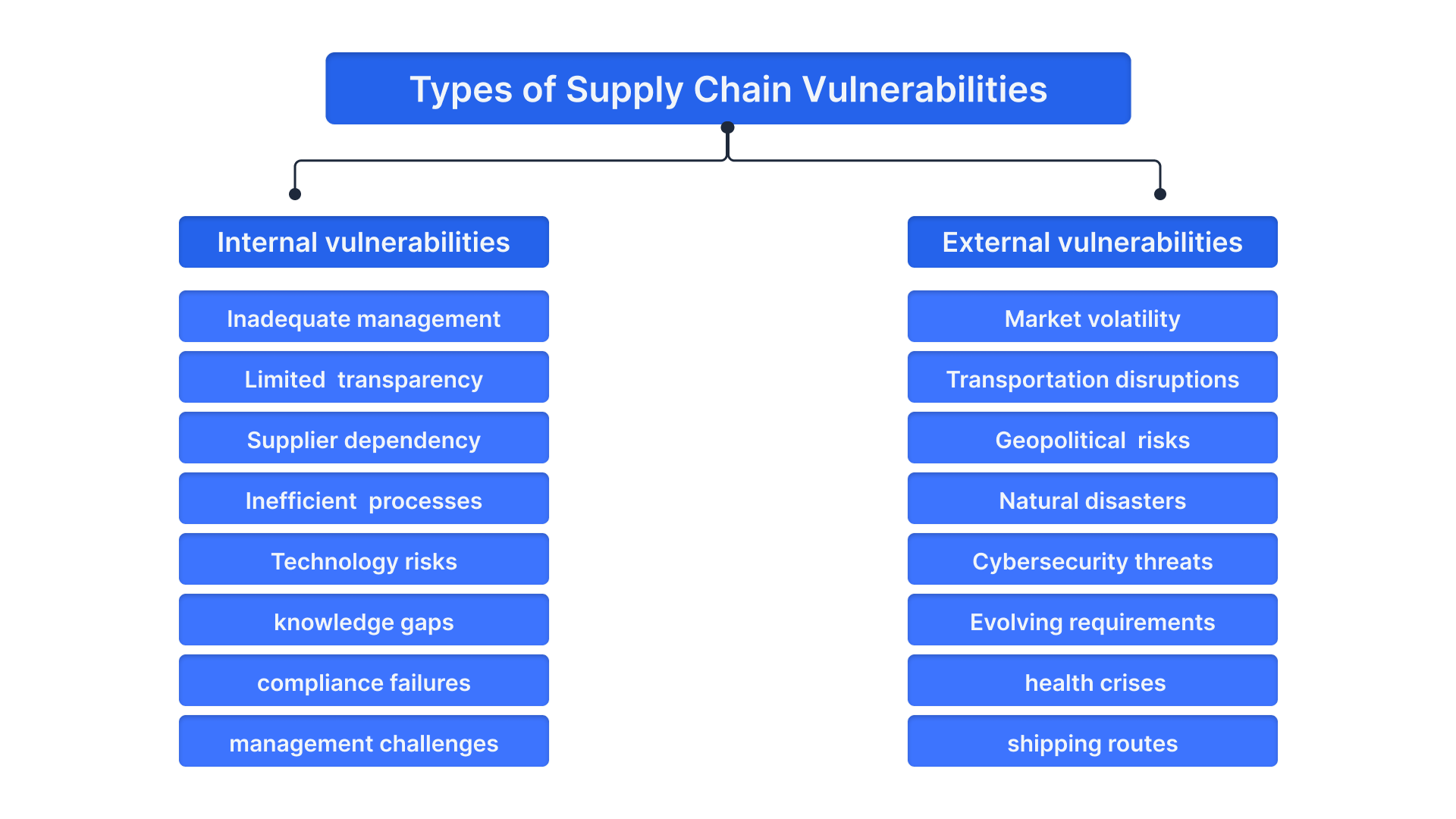
Types of Supply Chain Vulnerabilities
Supply chain vulnerabilities can be broadly classified into internal and external categories. Understanding this distinction is crucial for designing targeted mitigation strategies that improve both operational efficiency and overall resilience.
Internal supply chain vulnerabilities
These originate within the organization’s supply chain structure and are typically within your control. Addressing internal vulnerabilities often involves process optimization, technology upgrades, and workforce training.
Here are the most common internal threats:
Inadequate inventory management
Poor forecasting or manual tracking often leads to stockouts or overstocking, both of which tie up capital and disrupt operations. Real-time inventory systems and data-driven planning tools are essential to resolve this.
Limited visibility and transparency
Without full visibility into inventory, supplier performance, and production workflows, bottlenecks go unnoticed and decisions lack precision. Silos across systems or vendors can compound this issue.
Supplier dependency
Over-reliance on a single supplier or a limited pool for critical components exposes your operations to severe risk in the event of delays, quality issues, or failure on their end.
Inefficient or outdated processes
Manual workflows, paper-based documentation, or non-integrated systems slow down operations and create room for error. These inefficiencies become liabilities during disruptions.
Technology risks and downtime
Legacy systems or poorly maintained IT infrastructure can result in data breaches, cyberattacks, and service outages. Technology that isn’t secured or scalable becomes a hidden vulnerability.
Human error and knowledge gaps
A lack of employee training or unclear operational protocols leads to mistakes, inconsistent execution, and process breakdowns. Critical decisions can be delayed or misinformed.
Regulatory compliance failures
Non-compliance with local or international regulations may trigger financial penalties, halt shipments, or damage brand credibility. Global operations face the added complexity of navigating varied regulations.
Change management challenges
Rolling out new technologies or restructuring supply chain operations without a clear change management plan often results in resistance, errors, and temporary inefficiencies.
External supply chain vulnerabilities
These threats originate outside your organization’s control but still impact your supply chain significantly. Managing external vulnerabilities requires foresight, flexibility, and often collaboration with third parties.
Key external vulnerabilities include:
Market volatility
Fluctuations in customer demand, commodity prices, and currency exchange rates can alter costs and disrupt procurement and distribution plans.
Transportation and logistics disruptions
Delays from infrastructure breakdowns, strikes, customs bottlenecks, or natural disasters can interrupt the movement of goods. These points of failure are common in last-mile delivery and global shipping.
Geopolitical and trade risks
Trade restrictions, export bans, sanctions, and political unrest in supplier regions can make sourcing unstable or unpredictable. Monitoring global developments becomes a must.
Natural disasters
Events like earthquakes, floods, or hurricanes can cripple production or distribution hubs. As climate risks grow, so does the need for geographic diversification and emergency preparedness.
Cybersecurity threats
Increasingly, digital supply chains are now prime targets for cyberattacks. Compromises at any point, vendors, systems, or software, can expose sensitive data and interrupt services. In 2023 alone, organizations experienced an average of 4.16 supply chain-related cybersecurity incidents, according to BlueVoyant.
Evolving regulatory requirements
Changing laws on trade, environmental standards, or safety can require significant operational shifts. Those unprepared may face penalties or rushed transitions.
Pandemics and health crises
Global health emergencies like COVID-19 impact every layer of the supply chain, labor, manufacturing, logistics, and customer behavior. Contingency planning must now include health-related disruptions.
Dependency on critical shipping routes
Heavy reliance on chokepoints like the Suez Canal makes supply chains vulnerable to blockage, accidents, or geopolitical conflict. Redundant routes and inventory buffers are key to risk reduction.
Summary Table: Internal vs. External Vulnerabilities
| Aspect | Internal Vulnerabilities | External Vulnerabilities |
|---|---|---|
| Source of Risk | Within the organization | Outside the organization |
| Examples | Inventory mismanagement, tech gaps, and supplier dependency | Natural disasters, market shifts, cyberattacks, geopolitical risk |
| Control Level | High, can be mitigated through internal process improvements | Low, requires external monitoring, collaboration, and contingency plans |
| Response Strategy | Process automation, workforce training, and compliance systems | Diversification, scenario planning, third-party risk management |
| Frequency | Often ongoing or systemic | Often sporadic but high-impact |
| Risk Amplification | Inefficiencies, lack of visibility, non-compliance | Globalization, complexity, and lack of transparency across tiers |
Auditive’s research across global supply chains reveals that third-party risk is now one of the top three sources of operational disruption, often underestimated due to limited visibility into supplier networks.
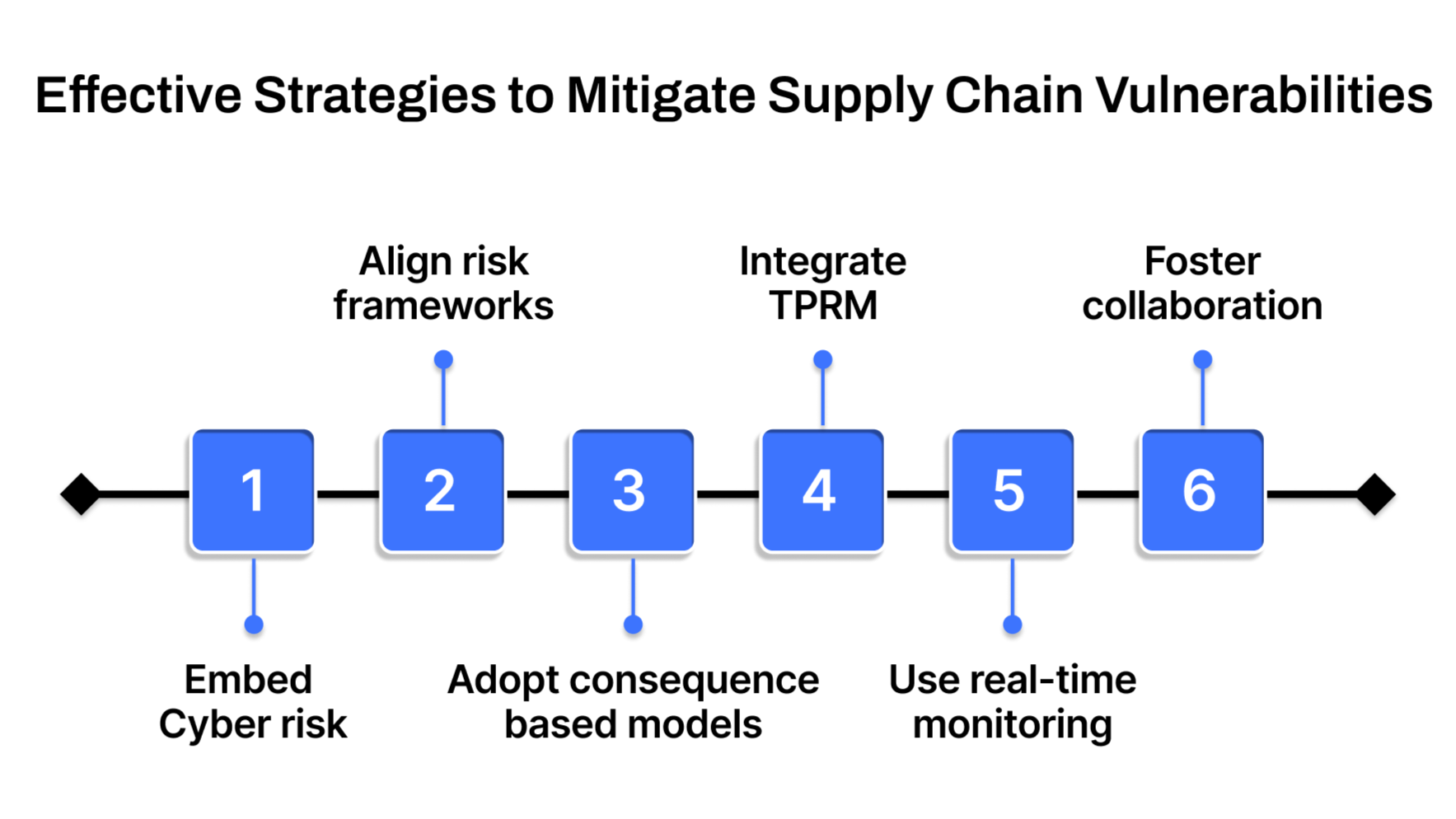
Effective Strategies to Mitigate Supply Chain Vulnerabilities
Once high-risk vulnerabilities have been identified and prioritized, the next step is action. Mitigation requires a multi-layered approach that blends proactive supplier oversight with operational flexibility, cybersecurity readiness, and a deeply ingrained culture of risk awareness. Below are six proven strategies to strengthen supply chain resilience:
1. Vet and continuously monitor suppliers
Robust supplier management begins before the contract is signed and continues throughout the relationship.
Assess cybersecurity posture during onboarding, including data handling standards and breach preparedness.
Apply strict qualification criteria aligned with your security and compliance frameworks.
Conduct regular performance evaluations and third-party risk assessments.
Define clear service-level agreements (SLAs) and key performance indicators (KPIs).
Maintain open communication channels to flag potential issues before they escalate.
2. Diversify supply and transportation networks
Relying on a single supplier, or a single region, is a risk multiplier. Diversification reduces exposure and increases agility.
Build relationships with secondary suppliers across multiple geographies.
Explore near-shoring or re-shoring for high-priority or high-risk components.
Leverage multiple transport modes to avoid carrier-specific disruptions.
Use analytics to evaluate alternative vendors based on cost, lead time, and resilience metrics.
3. Build logistics flexibility and maintain buffer inventory
Operational flexibility can absorb shocks without halting production or delivery.
Maintain safety stock or buffer inventory of critical inputs.
Invest in manufacturing capabilities that can pivot between inputs or suppliers.
Develop alternative routing strategies and backup distribution centers.
Use real-time data to proactively reroute shipments or adjust schedules due to port congestion or extreme weather.
4. Invest in cybersecurity across the supply chain
Digital supply chains are now as vulnerable as physical ones, if not more.
Implement a layered cybersecurity architecture: firewalls, anti-malware, and intrusion detection systems.
Train both internal teams and partners on secure data-sharing protocols and phishing prevention.
Run regular penetration testing, vulnerability scans, and cybersecurity audits.
Develop and maintain an incident response plan that accounts for cyber disruptions.
5. Train staff on risk awareness and best practices
Resilient supply chains require risk-aware teams, not just resilient systems.
Provide training on identifying, reporting, and responding to supply chain threats.
Integrate risk responsibilities into roles across procurement, logistics, IT, and finance.
Run periodic simulations and tabletop exercises to test readiness.
Promote a “no-blame” culture that encourages proactive reporting of weak points or potential risks.
6. Implement continuous monitoring and patch management
Visibility and speed are essential in managing emerging threats.
Deploy real-time monitoring tools to track supplier systems, logistics endpoints, and digital interfaces.
Maintain an up-to-date asset inventory of supply chain technology infrastructure.
Regularly apply patches and software updates as vulnerabilities are identified.
Track both actual incidents and near misses to refine mitigation strategies over time.
Include data privacy monitoring and compliance tracking in your ongoing evaluations.
Individually, these measures reduce specific risks. Together, they form a strategic foundation for supply chain resilience, built not just to withstand disruption but to adapt, respond, and thrive through it.
At Auditive, we’ve worked with enterprises across industries to operationalize supply chain resilience. What separates the most resilient organizations is not just the strategies they use, but how consistently and intelligently they apply them.
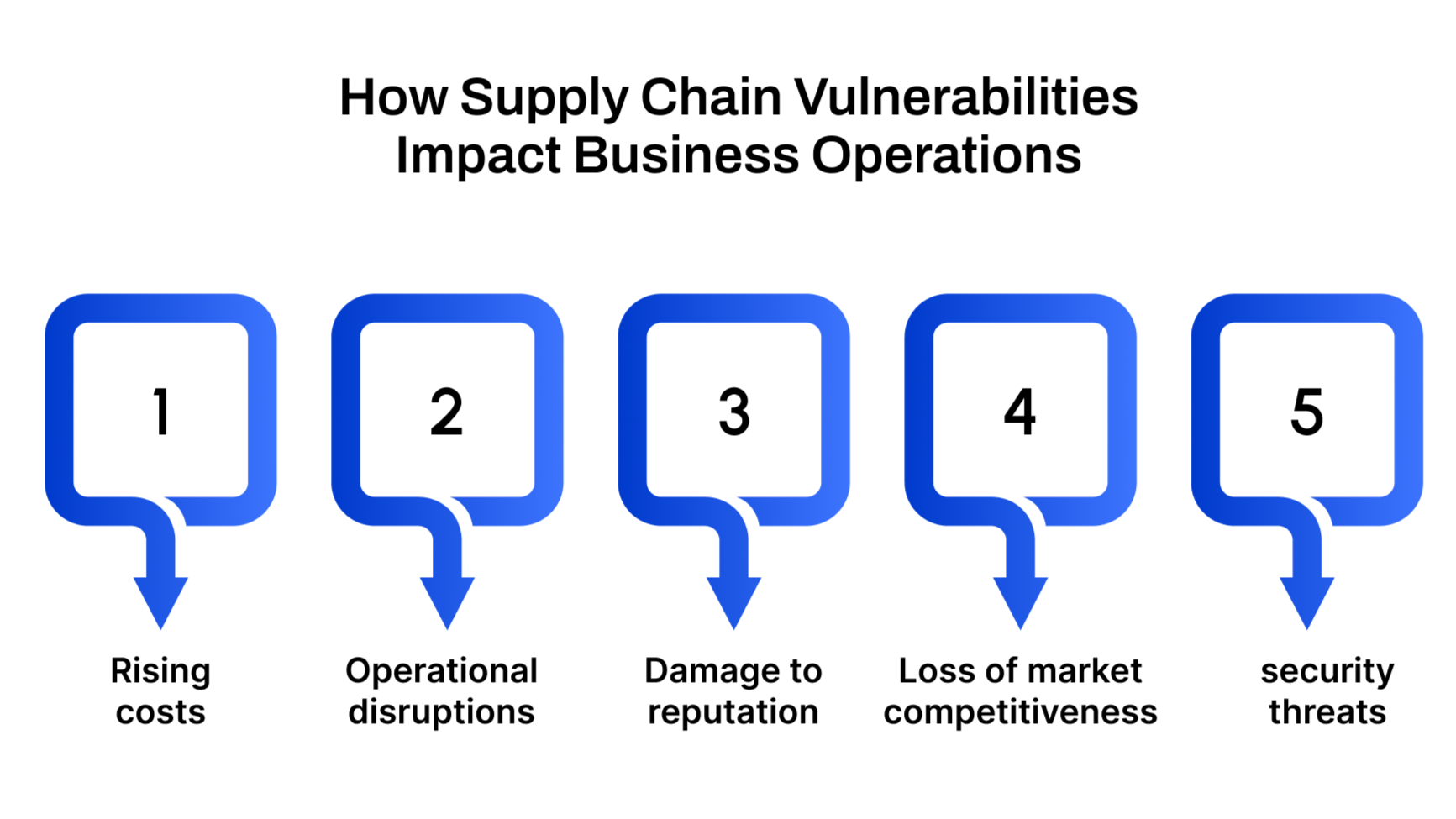
How Supply Chain Vulnerabilities Impact Business Operations
A single supply chain vulnerability can ripple across an organization, disrupting not only logistics and inventory but also financial stability, customer relationships, and long-term growth. Understanding these impacts is essential for building both operational resilience and strategic agility.
Financial losses and rising operational costs
When vulnerabilities surface, whether from cyberattacks, supplier insolvency, or transportation breakdowns, the financial consequences can be immediate and severe:
Revenue impact from production delays, unfulfilled orders, or canceled shipments.
Increased costs due to emergency sourcing, expedited freight, or temporary vendors.
Regulatory fines for compliance failures tied to safety, environmental, or documentation lapses.
The result is more than just disrupted cash flow, it’s diminished profitability and resource strain across departments.
Operational disruptions and inefficiencies
Vulnerabilities disrupt core workflows, from procurement through delivery:
Inventory misalignment from inaccurate forecasts or delayed materials leads to overstocking or costly shortages.
Production halts when critical parts or raw materials are unavailable.
Schedule breakdowns affect downstream processes, delaying launches, fulfilment, or even regulatory filings.
These disruptions ripple across manufacturing, warehousing, and logistics, causing unpredictable downtime and escalating costs.
Damage to reputation and customer trust
Supply chain breakdowns are rarely invisible to customers. Inconsistent delivery, product unavailability, or ethical sourcing failures can quickly erode trust:
Customer dissatisfaction grows when orders are delayed or quality is compromised.
Brand perception suffers, especially when environmental or labor-related issues make headlines.
Loyalty loss follows repeated failures, pushing customers toward more reliable competitors.
The reputational cost of supply chain vulnerability can far outweigh the immediate financial damage.
Loss of market competitiveness
A vulnerable supply chain limits your ability to adapt and grow:
Demand shortfalls mean you can’t capitalize on surges or new opportunities.
Inflexibility in vendor relationships or logistics chains reduces responsiveness.
Strategic hesitation sets in as organizations become overly cautious, stalling innovation or expansion.
In dynamic markets, resilience isn’t just operational; it’s a differentiator.
Safety hazards and security threats
The risks aren’t just financial; they’re physical and digital:
Safety concerns arise when essential safety-critical materials are unavailable or improperly sourced.
Cybersecurity breaches can halt entire operations, exposing sensitive data or locking down critical systems.
Environmental damage from poor vendor oversight or improper handling of materials adds legal and reputational risk.
Every gap in the supply chain is a potential exposure point, one that attackers, regulators, and customers are watching closely.
Industry Insight: Why Proactive Risk Management Is Gaining Board-Level Attention
Supply chain risk has moved beyond the realm of operations; it’s now a strategic concern discussed in boardrooms, investor calls, and regulatory filings. From the rise of ESG disclosures to the scrutiny of third-party data handling, supply chain resilience is now tied directly to brand reputation and investor confidence.
Auditive has observed a shift in how organizations treat vendor risk. No longer a reactive checklist, risk management is becoming a dynamic, intelligence-led capability woven into procurement, compliance, and cybersecurity functions.
Boards now expect answers to questions like:
How fast can we detect a supplier breach?
Which third parties are exposing us to non-compliance?
How often are our vendors re-assessed?
As these expectations rise, the organizations that thrive are those that embed real-time monitoring, continuous risk scoring, and a centralized Trust Center, a model we champion at Auditive.
Conclusion
Supply chain vulnerabilities are unavoidable, but unmanaged risk doesn’t have to be. As threats grow more complex, resilience depends on proactive strategies like diversification, cybersecurity, and continuous monitoring.
At the center of it all is effective Vendor Risk Management, ensuring every third-party relationship is secure, compliant, and resilient under pressure.
Auditive’s platform delivers real-time visibility, automated risk scoring, and a centralized Trust Center to help you stay ahead of disruptions.
Ready to take control of your supply chain risk?
Partner with Auditive and transform vendor risk management into a strategic advantage.
FAQs
Q1. What is supply chain vulnerability?
A1. Supply chain vulnerability refers to any weakness within the supply chain network that could lead to disruption, ranging from supplier instability and cyber threats to natural disasters and geopolitical shifts.
Q2. How can supply chain vulnerabilities impact business operations?
A2. They can cause delayed deliveries, production halts, increased costs, data breaches, and even regulatory non-compliance, affecting both revenue and brand trust.
Q3. What are the most common types of supply chain vulnerabilities?
A3. Common types include supplier dependency, lack of visibility, cybersecurity gaps, transportation delays, and reliance on single regions or vendors.
Q4. How can businesses proactively reduce supply chain risks?
A4. By diversifying suppliers, building logistics flexibility, investing in cybersecurity, monitoring third-party risk continuously, and training staff on risk protocols.
Q5. How does Auditive support supply chain risk management?
A5. Auditive provides automated vendor risk assessments, real-time alerts, and a unified Trust Center to help organizations continuously monitor and manage third-party risks across their supply chain.