Enterprise Security Risk Management Strategies
Supply chain vulnerabilities, and operational disruptions are escalating, businesses can no longer afford to treat security as a standalone function. Security must be approached as a strategic business priority, integrated into enterprise-wide decision-making. This is where enterprise protection risk management (ESRM) comes into play.
ESRM bridges the gap between security measures and business objectives by aligning risk management practices with the organization’s overall strategy. Rather than reacting to incidents in isolation, ESRM ensures that security risks, whether physical, digital, financial, or reputational, are assessed in the context of their impact on long-term growth and resilience.
This holistic approach not only helps organizations protect critical assets but also builds trust with stakeholders, ensures compliance with regulatory requirements, and supports sustainable business performance. With the right strategies, ESRM transforms risk management from a defensive function into a proactive driver of value creation and resilience.
TL;DR
Enterprise Security Risk Management (ESRM) aligns security with business objectives for a holistic, scalable approach.
Vendor risk management is essential to protect organizations from third-party vulnerabilities.
Trust Centers enhance transparency and compliance, making it easier to build stakeholder confidence.
Key challenges, like resistance to change, poor collaboration, and incomplete data can be overcome with the right strategy and tools.
Platforms like Auditive empower businesses to transform ESRM into a driver of resilience and long-term trust.
What Is Enterprise Security Risk Management?
Enterprise Security Risk Management (ESRM) is a strategic, organization-wide approach to protecting people, assets, and operations against a wide spectrum of interconnected threats. Unlike siloed approaches that separate cyber, physical, or financial risks, ESRM unifies them under a framework designed to safeguard business continuity and long-term resilience.
At its core, ESRM identifies potential threats, evaluates their likelihood and impact, and implements mitigation strategies that align with organizational objectives. Its strength lies in a holistic perspective understanding how risks overlap, compound, and influence strategic outcomes.
More than just protection, ESRM enables trust, adaptability, and sustainable growth by ensuring security is fully integrated into business strategy.
Key Risk Management Principles for Effective ESRM
For an enterprise protection risk management strategy to succeed, it must rest on strong guiding principles that ensure security is not an isolated function but a business enabler. The ASIS Enterprise Security Risk Management Guideline offers a solid foundation, but the core principles can be adapted to fit the unique needs of each organization. Four stand out as particularly vital:
1. Risk-Based Approach
Instead of deploying resources evenly across all assets, organizations should prioritize based on potential business impact. Not every system or process carries the same level of risk. By identifying critical assets, such as customer data, intellectual property, or operational infrastructure, security teams can align protection efforts with overall business objectives. This makes the program both efficient and effective.
2. Stakeholder Engagement
ESRM thrives on collaboration. Security cannot operate in a silo; it requires the involvement of leadership, employees, vendors, and even customers in some cases. Engaging stakeholders fosters shared ownership of risk and ensures that security initiatives are understood, supported, and integrated across departments rather than confined to IT or compliance teams.
3. Continuous Improvement
The threat landscape is dynamic. What worked yesterday may be insufficient tomorrow. ESRM must be designed as a living process, with regular reviews, testing, and updates. Lessons learned from past incidents, industry developments, and evolving regulatory requirements should all inform ongoing improvements, ensuring the program remains agile and resilient.
4. Data-Driven Decision-Making
Effective ESRM relies on evidence, not assumptions. Leveraging real-time monitoring, analytics, and performance metrics enables organizations to make informed decisions about risk prioritization and mitigation. Data-driven insights help validate the effectiveness of current controls, guide investment in new security measures, and demonstrate accountability to stakeholders and regulators.
Types of Enterprise Risk
Every business, no matter its size or industry, faces a variety of risks that can disrupt operations, drain resources, and weaken stakeholder trust. To build an effective enterprise protection risk management strategy, it’s important to recognize the different categories of risk and how they can affect long-term stability. Below are eight common types of enterprise risk:
1. Financial Risk
Financial risk impacts the stability and liquidity of a business. It often arises from debt mismanagement, volatile markets, or poor investment decisions.
Excessive debt leading to operational strain
Currency fluctuations or interest rate spikes
Inconsistent revenue streams are affecting cash flow
If not properly managed, financial risks can jeopardize business continuity and investor confidence.
2. Operational Risk
This type of risk disrupts the day-to-day functioning of an enterprise. Even small failures can have cascading effects.
IT outages or system downtime
Supply chain interruptions
Human error or internal process inefficiencies
Effective controls and resilience planning are essential to keep core operations running smoothly.
3. Strategic Risk
Strategic risks undermine long-term plans and competitiveness in the market.
Market disruption by new entrants or technologies
Poorly executed business strategies
Losing competitive advantage to rivals
Without strong foresight and adaptability, strategic risks can derail growth and erode market positioning.
4. Compliance Risk
Failing to meet regulatory or industry requirements can result in fines, penalties, and reputational loss.
Violations of accounting or reporting standards
Ignoring data privacy and security laws
Non-adherence to industry frameworks or certifications
Compliance risk reminds enterprises that governance and accountability are not optional but vital to survival.
5. Economic Risk
Global and regional economic conditions can directly influence business performance.
Stock market volatility is affecting investors
Inflation reduces purchasing power
Recessions lead to reduced demand
Since external economics are beyond direct control, enterprises must build buffers and flexible strategies to weather downturns.
6. Legal Risk
Legal issues not only drain resources but also tarnish brand reputation.
Customer lawsuits
Contract disputes with vendors
Liability from defective products or services
Strong legal frameworks and proactive compliance can minimize exposure to expensive and reputation-damaging lawsuits.
7. Natural Disaster Risk
Unpredictable natural events can have devastating impacts on operations and supply chains.
Earthquakes, floods, or hurricanes can damage infrastructure
Workforce displacement in affected regions
Production halts due to damaged facilities
Business continuity planning and disaster recovery measures are critical in reducing the long-term damage of natural risks.
8. Security Risk
Security risks, both cyber and physical, pose a growing threat in a digital-first world.
Data breaches exposing sensitive customer information
Phishing or ransomware attacks on systems
Theft or sabotage affecting physical assets
Security risk must be prioritized as a frontline defense to protect both digital and physical assets.
Managing such a wide range of risks requires not only awareness but also the right tools. This is where platforms like Auditive help enterprises streamline risk tracking, strengthen vendor oversight, and build trust through solutions like the Trust Center.
Components of Enterprise Risk Management
Unlike traditional risk management, which usually focuses on four basic pillars, identifying, evaluating, handling, and controlling risks, enterprise risk management (ERM) takes a broader, more integrated approach. The COSO framework, one of the most widely adopted models, breaks ERM down into eight interrelated components. Together, these components create a structured system that ensures risks are managed proactively and in alignment with business goals.
Here’s a closer look:
1. Internal Environment
Every ERM program begins with the tone set by leadership. The internal environment shapes how risk is perceived, managed, and prioritized. Senior leaders define the organization’s risk appetite and establish a culture of accountability that influences every risk-related decision.
2. Objective Setting
Clear objectives are the foundation of effective risk management. Enterprises must first determine what they want to achieve and then align those objectives with their risk tolerance and overall mission. Without this step, risk management efforts risk becoming fragmented or misaligned with strategy.
3. Event Identification
Risks can arise from both internal operations and external pressures such as market changes, regulations, or cyber threats. ERM encourages businesses to identify these events early, whether they represent potential threats or opportunities, so leaders can act before they escalate.
4. Risk Assessment
Once identified, risks must be measured in terms of likelihood and impact. This assessment should be ongoing and occur across multiple levels of the organization, not just at the top. Regular evaluations allow enterprises to stay ahead of emerging threats and reallocate resources where risks are most critical.
5. Risk Response
Risk responses typically fall into four categories: avoid, accept, reduce, or share. The chosen response depends on the enterprise’s tolerance and strategic priorities. For example, a financial institution might choose to reduce cyber risks with advanced monitoring systems, while accepting minor operational risks that pose little impact.
6. Control Activities
Once responses are defined, organizations implement controls to ensure risks are addressed effectively. These may include policies, audits, or automated safeguards that allow businesses to track progress and ensure consistency in risk handling.
7. Information and Communication
No risk management strategy succeeds without clear communication. Relevant risk information must reach the right stakeholders, executives, managers, and frontline employees, at the right time. This ensures everyone understands their role in mitigating risks and fosters collaboration across departments.
8. Monitoring
ERM is not static. Risks evolve, markets shift, and new threats emerge. Continuous monitoring ensures organizations can adapt quickly, updating controls and strategies as conditions change. This dynamic approach is what keeps ERM effective in the long run.
Together, these eight components transform ERM from a checklist into a living framework that ties risk directly to enterprise value and resilience.
Many organizations struggle to operationalize these components consistently across their vendor and partner networks. This is where platforms like Auditive can bridge the gap, by automating monitoring, centralizing communication, and providing real-time insights into vendor risks that align directly with the COSO framework.
How to Build a Strong ESRM Program for Security Management
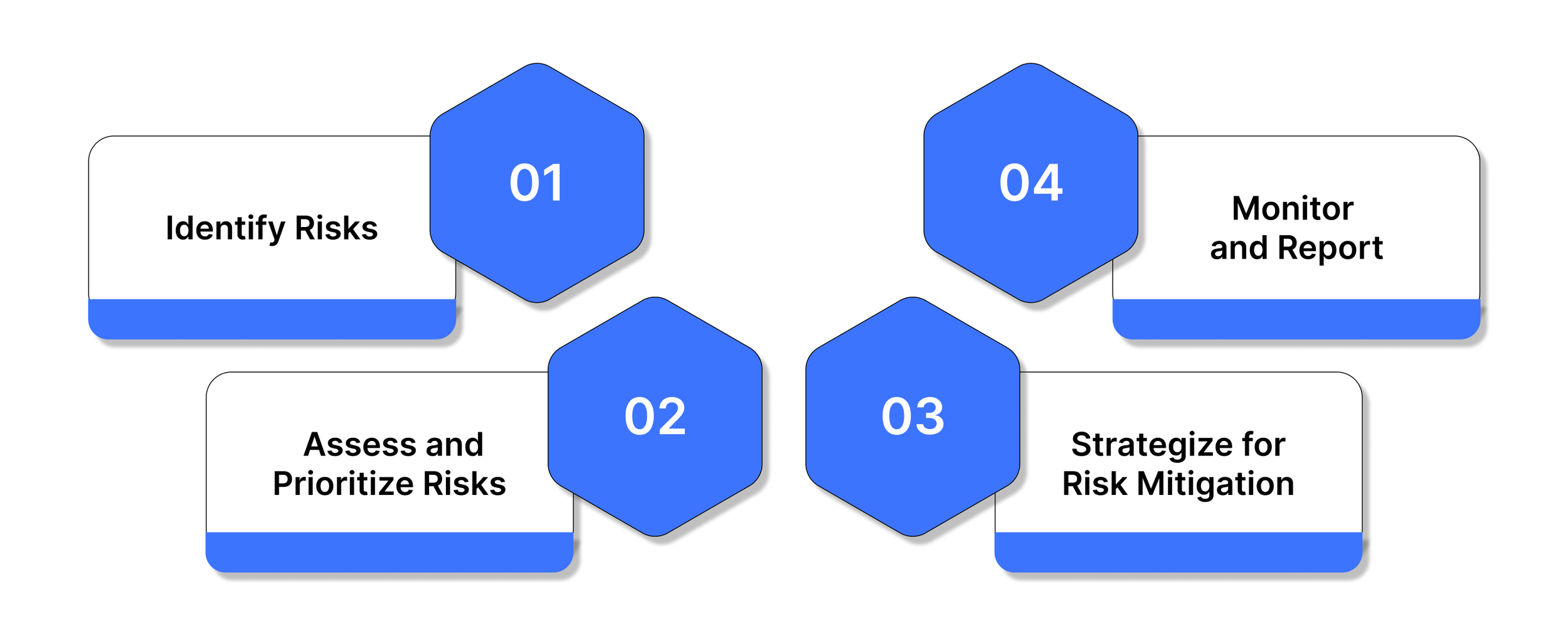
Building a strong enterprise protection risk management (ESRM) program requires more than policies on paper, it demands a structured, data-driven, and adaptable approach that evolves alongside business priorities and external threats. A resilient ESRM program is typically built on four core stages: risk identification, assessment, mitigation, and continuous monitoring.
Read more about: Comprehensive Guide Identifying Managing Business Risks
Step 1: Identify Risks
The foundation of any ESRM program is a deep understanding of the risks that could affect your organization. Rather than focusing only on broad or generic threats, effective ESRM digs into specific vulnerabilities, both internal and external.
One proven tool for organizing these insights is a SWOT analysis:
Strengths (Internal): Strong processes, brand reputation, or skilled workforce.
Weaknesses (Internal): Gaps in expertise, heavy reliance on a single vendor, or outdated systems.
Opportunities (External): New technologies, expansion markets, or favorable regulations.
Threats (External): Cyberattacks, supply chain disruptions, economic downturns, or industry competition.
For example, a mid-sized healthcare supplier might identify its strong logistics network as a strength, rising demand for eco-friendly products as an opportunity, but dependence on limited suppliers as a major weakness. This structured view allows leaders to proactively align business strategies with security priorities.
Beyond SWOT, organizations should incorporate threat intelligence tools to detect and analyze emerging risks. These data-driven systems use analytics, predictive modeling, and machine learning to identify trends and provide early warnings that manual reviews might miss.
Step 2: Assess and Prioritize Risks
Not all risks carry the same weight. Some are low-probability but high-impact, such as the sudden loss of a key executive, while others, like phishing attacks, may occur frequently but compound into significant financial or reputational harm.
To manage this complexity, businesses often rely on a risk matrix, which maps risks by likelihood and impact. This visualization makes it easier to prioritize which threats require immediate resources versus ongoing monitoring.
By applying this structured evaluation, organizations can avoid wasting resources on low-impact risks while ensuring critical vulnerabilities receive top attention.
Step 3: Strategize for Risk Mitigation
Once risks are prioritized, the next step is developing targeted mitigation strategies. These typically fall into three categories:
Preventive Controls: Measures to reduce the likelihood of risks materializing, such as strong access controls, employee training, or supplier diversification.
Detective Controls: Tools to uncover threats early, like continuous monitoring, regular audits, and security analytics.
Corrective Controls: Plans to limit damage if an incident does occur, including disaster recovery protocols, data backups, and crisis communication plans.
Mitigation should also extend into business continuity planning, ensuring the organization can maintain operations during disruptions. Regular tabletop exercises, penetration tests, and resilience drills help refine response strategies and close gaps before real-world crises strike.
Step 4: Monitor and Report
No ESRM program is static, risks evolve daily, and so should your defenses. Continuous monitoring ensures that organizations stay ahead of both known and emerging threats.
Metrics such as Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), and control effectiveness provide tangible measures of security performance. Transparent reporting of these indicators also builds trust with executives, regulators, and customers by demonstrating accountability and progress.
Auditive strengthens this stage with automated monitoring and transparent reporting through its Trust Center. Instead of relying on static, annual assessments, businesses gain ongoing visibility into vendor performance, compliance adherence, and evolving third-party threats. This real-time intelligence ensures risk strategies remain proactive rather than reactive.
Must read: Third-Party-Contract-Management-Best-Practices
A effective ESRM program is not a one-time exercise but an ongoing cycle of identification, assessment, mitigation, and monitoring. By pairing structured frameworks with technology platforms like Auditive, organizations can embed resilience into every layer of their security management strategy.
Challenges in Implementing ESRM
Adopting enterprise protection risk management (ESRM) is not a simple checklist exercise, it requires a cultural and structural shift in how an organization views security. Unlike traditional models, which tend to operate in silos, ESRM demands integration, transparency, and alignment across every business unit. This often introduces challenges that can slow adoption if not addressed proactively.
1. Lack of Cross-Department Collaboration
Security risks don’t live in isolation. When departments operate independently, critical risk signals may be overlooked. Without collaboration between IT, operations, compliance, and legal, security strategies remain fragmented.
Establish a central risk management committee that brings together key stakeholders. A unified body ensures that risks are shared, understood, and addressed consistently across the organization.
2. Resistance to Change
Shifting from siloed security to enterprise-wide ESRM can feel disruptive. Leadership may question the value, while employees may worry about added responsibilities.
Demonstrate the business value of ESRM by connecting it directly to reduced losses, stronger compliance, and operational efficiency. Training sessions and clear communication can help build buy-in across all levels.
3. Defining and Measuring Security Risks
Security risks are often abstract, making them difficult to quantify. Without clear metrics, organizations struggle to prioritize threats or justify investments.
Adopt standardized frameworks such as NIST 800-30, ISO 27001, or FAIR to establish consistent benchmarks. Automated tools for risk tracking and reporting can further enhance visibility and provide data-driven insights.
4. Lack of Accountability
In many organizations, risk management is everyone’s responsibility, and no one’s at the same time. Without ownership, issues fall through the cracks.
Assign clear risk owners for each domain of security, with defined responsibilities tied to performance metrics. Embedding accountability ensures that risks are actively managed, not passively monitored.
Also Read: Manage Risk New Business Strategies
5. Inconsistent or Incomplete Data
Security decisions are only as strong as the data behind them. If monitoring is fragmented or incomplete, leaders risk making blind decisions.
Standardize data collection using tools like SIEM platforms, automated threat intelligence, and compliance monitoring systems. Regular audits ensure integrity and reliability of data for better decision-making.
6. Scaling Across Large Organizations
Global enterprises face the added challenge of scaling ESRM across multiple geographies, systems, and cultures. What works in one region may not be practical in another.
Roll out ESRM in phases, prioritizing high-risk areas before expanding. Leveraging cloud-based security platforms and automation can improve scalability while keeping costs in check.
Overcoming these challenges requires not only the right frameworks but also intelligent tools that simplify collaboration, accountability, and monitoring. This is where solutions like Auditive’s Trust Center and vendor risk management capabilities can bridge the gaps, making ESRM adoption smoother and more effective.
Enabling Smarter ESRM Adoption
Implementing enterprise protection risk management (ESRM) requires more than frameworks and policies—it needs technology that enables visibility, accountability, and trust across the vendor ecosystem. This is where Auditive becomes a key partner for organizations looking to modernize their security and risk programs.
With Auditive, businesses gain access to tools designed to reduce complexity and improve resilience:
Trust Center: A centralized hub that enhances transparency, allowing organizations to showcase security posture to clients, partners, and regulators.
Vendor Risk Management: Streamlined onboarding, monitoring, and auditing of third-party vendors with automated scoring and compliance tracking.
Real-Time Monitoring: Continuous oversight of risk signals across third-party ecosystems, ensuring threats are identified before they escalate.
Compliance Insights: Automated alignment with standards like ISO 27001, PCI DSS, and NIST, simplifying reporting and audits.
Collaborative Dashboards: Secure, shared views of risks that enable cross-department communication and decision-making.
Auditive bridges the gap between strategy and execution, making ESRM not just a vision but a practical, measurable reality.
By combining transparency, automation, and compliance in one platform, Auditive empowers organizations to turn risk into resilience and scale security with confidence.
Summary
Building an effective enterprise protection risk management (ESRM) program requires more than frameworks it demands collaboration, transparency, and the right tools to manage evolving risks. As organizations face increasingly complex challenges, vendor risk management and clear communication across business units become central to success. Leveraging technologies like a Trust Center not only streamlines compliance but also strengthens confidence with clients, partners, and regulators.
The organizations that thrive will be those that view risk management not as a cost but as a driver of trust, resilience, and long-term business value.
Ready to elevate your ESRM strategy?
Partner with solutions like Auditive, where automation, compliance insights, and transparency turn security into a competitive advantage. Start building a risk management approach that helps your business scale with confidence.
FAQs
1. What is Enterprise Security Risk Management (ESRM)?
ESRM is a holistic approach to aligning security initiatives with business goals, ensuring risks are managed in a way that supports organizational strategy.
2. How does ESRM differ from traditional security programs?
Unlike siloed security measures, ESRM integrates risks across all departments, aligning them with enterprise-wide objectives and prioritizing based on business impact.
3. Why is vendor risk management critical to ESRM?
Third-party vendors often present hidden risks. Effective vendor risk management ensures these external relationships don’t expose the organization to security, compliance, or operational threats.
4. What role does a Trust Center play in ESRM?
A Trust Center acts as a transparent hub for demonstrating security and compliance practices, building trust with stakeholders while simplifying audits and reporting.
5. What are the biggest challenges in implementing ESRM?
Common challenges include resistance to change, lack of collaboration across departments, inconsistent data, and difficulties in scaling programs. These can be mitigated with clear accountability and the right technology tools.