Comprehensive Guide to Business Process Risk Management
Every business process carries a certain level of uncertainty, whether it’s operational inefficiencies, compliance gaps, or external threats. Without the right safeguards, these risks can disrupt workflows, weaken decision-making, and ultimately affect business performance. This is where risk management information becomes indispensable.
By systematically identifying, analyzing, and addressing potential risks within business processes, organizations can turn uncertainty into a structured framework for resilience. Risk management information doesn’t just protect against disruptions; it provides the insights leaders need to streamline operations, ensure compliance, and maintain stakeholder trust.
In this comprehensive guide, we’ll explore the concepts, benefits, and practices of business process risk management, helping you understand how to use risk management information as a strategic tool for stability and growth.
Before we dive in:
What it is: Business Process Risk Management helps organizations identify, assess, and control risks that could disrupt operations or compliance.
Why it matters: Poorly managed risks lead to financial loss, inefficiencies, and reputational damage.
Types of risks: Operational gaps, compliance failures, vendor risks, financial instability, and technology-related threats.
Key techniques: Risk mapping, audits, scenario planning, and vendor assessments.
Value add: Tools like Vendor Risk Management and a Trust Center ensure transparency, stronger governance, and improved stakeholder trust.
Understanding Business Process Risk Management
Business process risk management is the practice of identifying, assessing, and mitigating potential threats that can disrupt organizational processes. Unlike traditional risk management, which often focuses broadly on financial or operational risks, business process risk management drills down into the day-to-day workflows that keep a company running.
At its core, it uses risk management information to map out vulnerabilities within processes such as procurement, compliance reporting, customer service, and IT operations. For example, a delayed vendor onboarding process can create compliance issues, while poor data handling in finance can trigger regulatory penalties. By tracking these risks in detail, companies can align business continuity with performance goals.
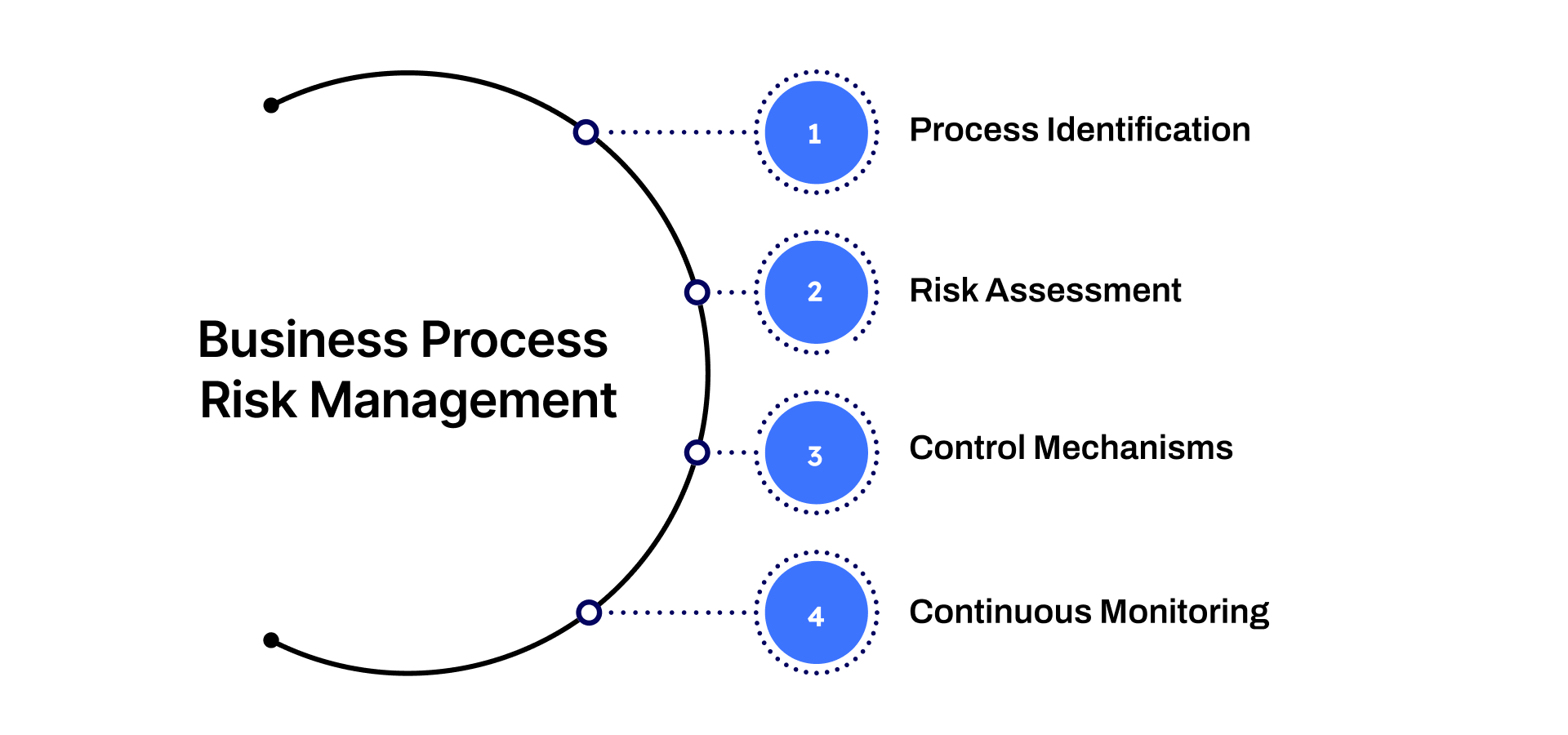
Key aspects include:
Process Identification – Pinpointing critical processes that drive business outcomes.
Risk Assessment – Evaluating risks in terms of likelihood, impact, and severity.
Control Mechanisms – Implementing controls like audits, monitoring tools, or automation.
Continuous Monitoring – Using dashboards and reports to ensure risks remain within acceptable thresholds.
Ultimately, business process risk management transforms risk from being a reactive challenge into a proactive opportunity, helping businesses strengthen efficiency, protect reputation, and achieve strategic objectives.
The Importance of Business Process Risk Management
Business process risk management (BPRM) is not just about avoiding losses; it’s about ensuring resilience, compliance, and growth. Every process, from supply chains to finance, carries risks that can disrupt operations, hurt reputation, or cause regulatory penalties.
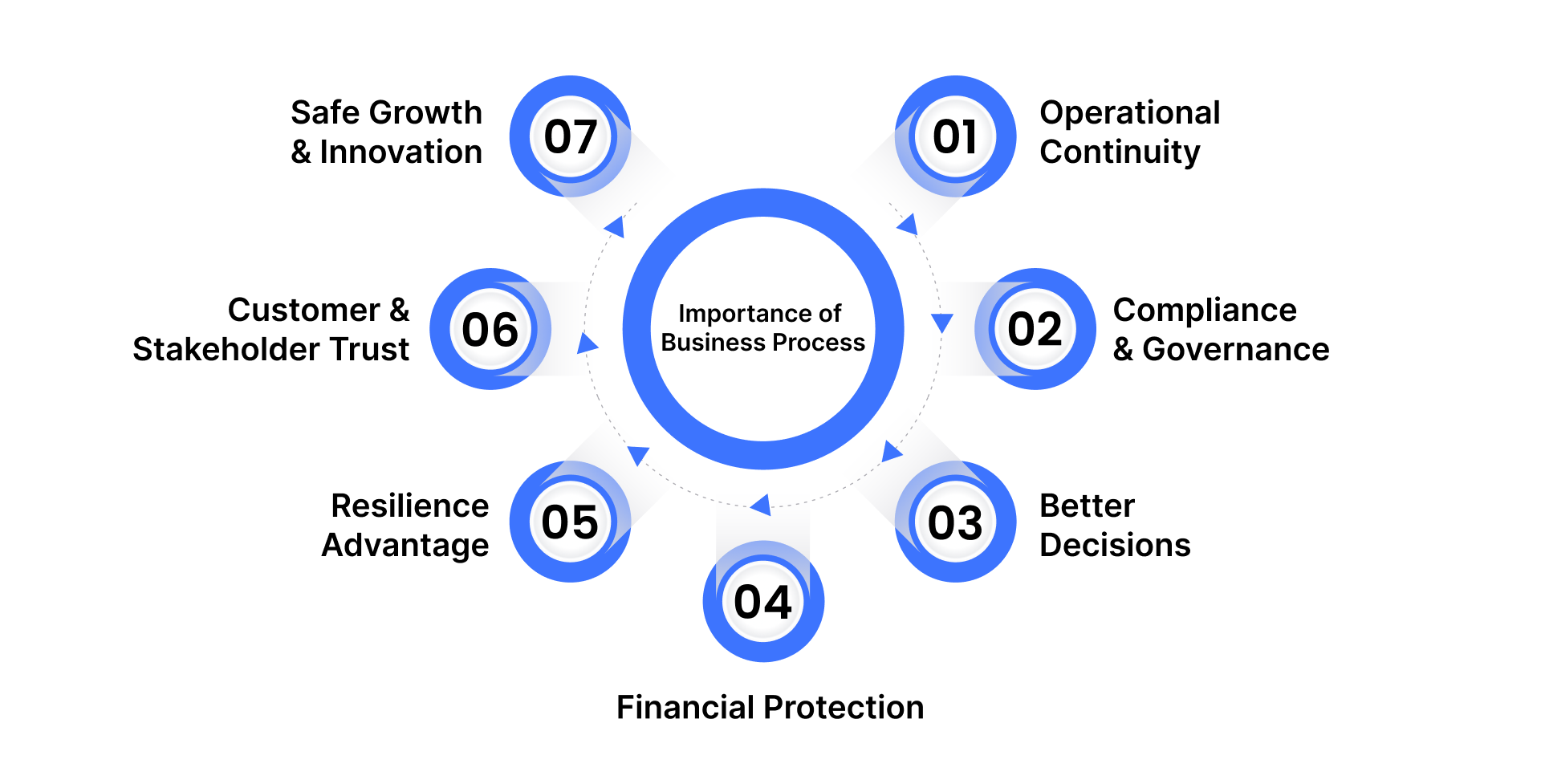
Here’s why BPRM is critical:
Operational Continuity – Proactively addressing risks keeps processes running smoothly and minimizes costly downtime.
Compliance & Governance – Embedding risk checks helps meet regulations (GDPR, SOX, HIPAA), avoiding fines and legal consequences.
Better Decisions – With visibility into risks, leaders can balance opportunities with potential threats before expanding or innovating.
Financial Protection – Strong controls reduce costs from errors, fraud, and penalties, safeguarding profitability.
Resilience Advantage – Businesses prepared for disruptions (cyberattacks, disasters, supply issues) recover faster and stay competitive.
Customer & Stakeholder Trust – Risk-aware operations reinforce reliability, security, and brand reputation.
Safe Growth & Innovation – Managing risks smartly enables companies to innovate and scale with confidence.
"With its importance clear, the next step is understanding how businesses can identify and manage risks across their processes effectively."
Types of Risks in Business Processes
Business processes are the backbone of organizational efficiency, but they also introduce multiple vulnerabilities. Without a structured approach to identify, assess, and control these risks, companies can face disruptions that affect revenue, compliance, and customer trust.
Below are the major types of risks that organizations should account for in their risk management strategies:
1. Operational Risks
Operational risks arise from failures in daily activities, workflows, or internal systems. These risks are often rooted in human error, poorly defined processes, or gaps in oversight.
Examples:
Production errors leading to defective products.
Inefficient order fulfillment causing delays and customer complaints.
Miscommunication between departments leading to duplication or loss of work.
Impact: Direct financial loss, productivity decline, and reduced service quality.
Mitigation: Standard operating procedures (SOPs), staff training, internal audits, and automation where possible.
2. Compliance and Regulatory Risks
Every industry is governed by regulations, financial reporting standards, labor laws, data protection policies, or environmental rules. Business processes that overlook compliance expose organizations to severe penalties and reputational harm.
Examples:
Mishandling of customer data violating GDPR or HIPAA.
Inaccurate tax filings leading to government fines.
Non-compliance with workplace safety regulations.
Impact: Legal liabilities, fines, license revocations, and loss of stakeholder confidence.
Mitigation: Compliance audits, regular policy reviews, risk management information systems for tracking regulations.
3. Financial Risks
Financial risks are tied directly to monetary losses caused by weak controls, market volatility, or inefficient financial processes. These risks often have a ripple effect, damaging profitability and long-term sustainability.
Examples:
Vendor overbilling due to poor invoice verification.
Currency fluctuations impacting international contracts.
Ineffective budgeting and forecasting leading to cash flow shortages.
Impact: Reduced profitability, inability to reinvest, and increased vulnerability to market shocks.
Mitigation: Strong financial reporting systems, risk-adjusted budgeting, vendor risk monitoring, and use of predictive analytics.
Read more about: Continuous Risk Monitoring Practices Techniques
4. Technology Risks
Modern businesses rely heavily on digital infrastructure, which makes them vulnerable to IT disruptions, cyber threats, and outdated systems.
Examples:
System outages halting operations in ERP, CRM, or payroll systems.
Cyberattacks leading to data breaches.
Legacy systems failing to integrate with modern platforms.
Impact: Loss of productivity, high recovery costs, data theft, and long-term reputational damage.
Mitigation: Cybersecurity frameworks, regular system updates, disaster recovery plans, and risk monitoring dashboards.
5. Reputational Risks
Reputation is one of the most valuable yet fragile assets for any business. A single negative event in a business process can spread quickly and undermine years of trust-building.
Examples:
Poor handling of customer complaints going viral on social media.
Data misuse resulting in negative media coverage.
Environmental negligence affecting public perception.
Impact: Customer attrition, reduced market share, and loss of investor trust.
Mitigation: Transparent communication, proactive crisis management, and consistent quality controls.
6. Strategic Risks
Strategic risks occur when business processes do not align with long-term organizational goals, competitive markets, or changing consumer behavior.
Examples:
Sticking to manual processes while competitors automate.
Expanding into markets without proper risk assessment.
Misjudging consumer demand trends and failing to adapt supply chains.
Impact: Decline in competitiveness, wasted investments, and failure to capture growth opportunities.
Mitigation: Regular market analysis, strategy reviews, and integrating risk management information into executive decision-making.
7. Third-Party and Vendor Risks
Most businesses depend on external vendors, contractors, and service providers. These relationships add efficiency but also create risks that are outside direct control.
Examples:
Vendor delays disrupting the supply chain.
Outsourced IT providers mishandling sensitive data.
Single-source supplier dependency causing bottlenecks.
Impact: Supply interruptions, cost escalations, compliance failures, and reputational harm.
Mitigation: Vendor risk management frameworks, diversified sourcing strategies, and continuous performance monitoring.
Learn more: Third Party Risk Management Guidance
By classifying risks into these categories and using risk management information to continuously monitor and assess them, organizations can move from a reactive to a proactive posture. This enables faster response, stronger compliance, and greater operational resilience.
Since risks span from financial mismanagement to operational inefficiencies and regulatory exposure, organizations need more than manual oversight. With Auditive’s risk intelligence, businesses can centralize and prioritize risks, ensuring they don’t miss hidden patterns that could lead to costly disruptions.
Techniques for Identifying Process Risks
Identifying risks in business processes is the foundation of an effective risk management strategy. Without clearly understanding where risks originate and how they can affect operations, organizations may fail to respond adequately when threats materialize. Risk identification is not a one-time exercise, it requires continuous assessment as processes, technologies, and external conditions evolve.
Below are key techniques organizations can apply to uncover potential risks in their business processes:
1. Process Mapping and Workflow Analysis
Mapping each step of a business process helps reveal weak points where errors, delays, or vulnerabilities may occur.
This approach clarifies dependencies between departments, systems, and individuals, making hidden risks easier to detect.
For example, a delay in supplier approval in procurement could expose the organization to delivery failures or compliance gaps.
2. Risk Workshops and Brainstorming Sessions
Bringing together cross-functional teams (operations, finance, IT, compliance, etc.) encourages knowledge sharing and collective identification of risks.
These sessions allow teams to anticipate "what-if" scenarios and recognize potential risks that may not appear in data-driven analysis.
Facilitated workshops often lead to identifying risks that are both operational (system downtime) and strategic (loss of competitive advantage).
3. Interviews and Surveys with Stakeholders
Frontline employees and process owners often have first-hand insights into recurring problems and inefficiencies.
Structured interviews or surveys help capture risks that might otherwise go unnoticed in leadership-level discussions.
This bottom-up approach ensures alignment between leadership expectations and operational realities.
4. Root Cause Analysis (RCA)
RCA focuses on identifying underlying causes of past process failures or incidents.
By examining historical data, organizations can pinpoint systemic issues, such as inadequate training, outdated tools, or lack of compliance checks.
This method helps in preventing recurrence rather than just addressing symptoms.
5. Scenario Analysis and Simulation
Simulating possible disruptions (such as system outages, supply chain failures, or compliance breaches) helps evaluate how processes will respond under stress.
This proactive method allows organizations to prepare contingency plans and mitigate risks before they occur.
For instance, simulating cyberattacks on a financial process helps expose potential data security vulnerabilities.
6. Data Analytics and Monitoring Tools
Advanced analytics and monitoring systems, such as dashboards, audit logs, or predictive analytics, help detect anomalies and early warning signals.
Data-driven methods enable continuous monitoring of KPIs to flag irregularities like sudden spikes in transaction errors or delays in approvals.
Automated tools reduce human bias and improve accuracy in identifying risks.
7. Industry Benchmarks and Regulatory Guidelines
Comparing business processes against industry best practices or compliance standards (e.g., ISO, NIST, or SOX) highlights gaps that may pose risks.
Benchmarking not only identifies risks but also drives improvements by aligning processes with leading practices.
Traditional methods like audits and workshops are useful, but they often fall short in capturing real-time changes. By integrating Auditive’s automated monitoring tools, businesses can enhance their identification techniques, making risk management information more actionable and timely.
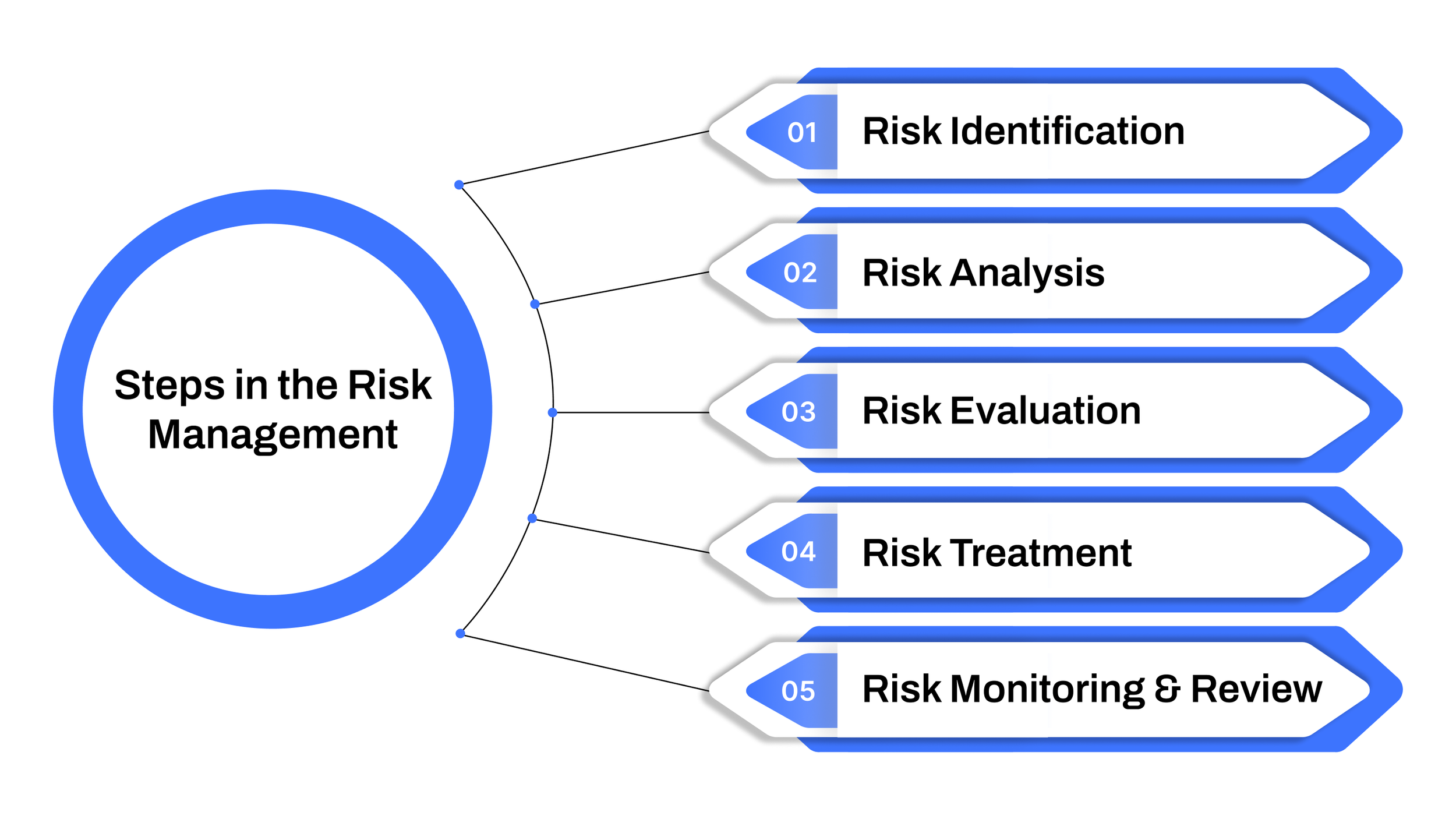
Steps in the Risk Management Process
Risk management is not a one-time task but a continuous cycle that strengthens business resilience. By following a structured process, organizations can foresee threats, minimize their impact, and seize opportunities hidden within uncertainty.
Below are the five essential steps of the risk management process, explained in detail:
1. Risk Identification
The first step is to spot potential risks before they evolve into serious issues. Risks may arise from internal factors (like process inefficiencies or system failures) or external factors (such as regulatory changes, economic fluctuations, or supply chain disruptions).
Key methods to identify risks include:
Brainstorming & Workshops – Engaging leadership teams, managers, and frontline employees to uncover possible vulnerabilities.
Process Mapping – Breaking down workflows to identify bottlenecks or weak points.
Document & Contract Reviews – Analyzing legal agreements, compliance reports, and audit findings for hidden risks.
Historical Data & Incident Reports – Learning from past events to anticipate similar scenarios.
The goal is to create a comprehensive risk register, a living document that lists every identified risk and its potential triggers.
2. Risk Analysis
Once risks are identified, they must be evaluated in depth to understand how they could affect the business. Not all risks are equally important; some may cause minor delays, while others could disrupt the entire organization.
Two primary approaches are used:
Qualitative Analysis – Risks are categorized based on likelihood (low/medium/high) and impact (minor/moderate/severe).
Quantitative Analysis – Uses data-driven methods, such as financial modeling, probability distributions, or scenario simulations, to estimate potential losses.
A risk matrix is often used to visualize where each risk stands, helping leaders quickly distinguish between critical threats and manageable concerns.
3. Risk Evaluation
Risk evaluation takes the analysis one step further by prioritizing risks in order of importance. This ensures that resources are allocated where they matter most.
High-priority risks (high likelihood, high impact) demand immediate action.
Moderate risks may be controlled through monitoring and periodic reviews.
Low-level risks can often be accepted with minimal oversight.
It’s important to remember that risk evaluation is dynamic. Business environments evolve, competitors innovate, and regulations shift. Risks that were once minor can quickly escalate, making regular re-evaluation a critical part of the process.
4. Risk Treatment (Mitigation Strategies)
This step involves deciding on the right strategy to address each risk. Organizations generally follow four approaches:
Avoidance – Restructuring plans or processes to eliminate the risk entirely. Example: exiting a high-risk market.
Mitigation – Implementing controls or safeguards to reduce the likelihood or impact. Example: adding cybersecurity protocols to protect data.
Transfer – Shifting responsibility to a third party. Example: purchasing insurance or outsourcing to a specialized vendor.
Acceptance – Acknowledging the risk and preparing contingency measures. Example: keeping reserves to handle unexpected financial shocks.
Each choice should align with the company’s risk appetite, the level of risk leadership is willing to tolerate while pursuing business objectives.
5. Risk Monitoring and Review
Risk management doesn’t end once strategies are in place. Continuous monitoring and review ensure that risks remain under control and new threats are identified in time.
This involves:
Tracking Key Risk Indicators (KRIs) – Metrics that signal early warning signs of potential issues.
Conducting Regular Audits – Ensuring mitigation strategies remain effective.
Updating Risk Registers – Adding new risks and closing resolved ones.
Feedback Loops – Gathering insights from employees, customers, and stakeholders for real-time improvements.
Effective monitoring turns risk management into an ongoing cycle, reinforcing business resilience and strengthening decision-making at every level.
In short, the risk management process moves from identification → analysis → evaluation → treatment → monitoring, creating a loop of continuous protection and adaptability.
Effective risk management demands clarity, collaboration, and continuous monitoring. Auditive empowers organizations to achieve these outcomes while staying ahead of evolving challenges.
Elevating Risk Management with Trust and Transparency
Managing risks in business processes goes beyond policies and checklists, it requires visibility, accountability, and a proactive approach to security. Auditive empowers organizations to move from reactive measures to a strategic model of continuous risk oversight, ensuring that potential vulnerabilities are addressed before they escalate into serious disruptions.
With Vendor Risk Management integrated into its core, Auditive provides a holistic view of third-party exposures, contract dependencies, and compliance gaps. This allows businesses to safeguard their operations from hidden risks while maintaining strong partnerships across the value chain.
What sets Auditive apart is its Trust Center, a dedicated space where security, compliance, and governance practices are made transparent. This not only builds stakeholder confidence but also accelerates decision-making, as teams gain access to the information they need without delays or silos.
By combining advanced analytics, collaborative workflows, and a commitment to transparency, Auditive helps businesses align their security posture with long-term growth objectives, enabling leaders to focus on innovation rather than firefighting risks.
Summary
Effective business process risk management is no longer optional, it is essential for organizations seeking resilience, efficiency, and trust. From identifying process vulnerabilities to implementing structured controls, the ability to manage risks directly impacts growth, customer confidence, and compliance readiness.
This is where Auditive strengthens the equation. With its integrated Vendor Risk Management capabilities and transparent Trust Center, businesses gain the clarity and control needed to manage risks holistically. The platform helps leaders move beyond reactive firefighting and instead adopt a proactive, scalable risk strategy that aligns with long-term goals.
Take the next step toward strengthening your organization’s trust and resilience.
Partner with Auditive to transform risk management into a strategic advantage.
FAQs
1. What is business process risk management?
It is the structured approach to identifying, assessing, and mitigating risks within an organization’s operational and strategic processes to ensure continuity, compliance, and efficiency.
2. Why is Vendor Risk Management important in business process risk management?
Third-party vendors can introduce significant risks such as data breaches, compliance failures, or supply chain disruptions. Vendor Risk Management helps organizations identify, monitor, and mitigate these risks effectively.
3. How does a Trust Center support risk management?
A Trust Center provides stakeholders with transparent insights into an organization’s security, compliance, and governance practices, building credibility and improving trust with customers, regulators, and partners.
4. What are common challenges in business process risk management?
Key challenges include lack of visibility into processes, fragmented data, overreliance on manual monitoring, and evolving regulatory requirements.
5. How can technology improve risk management in business processes?
Technology platforms like Auditive enable real-time monitoring, vendor risk oversight, and centralized governance, making risk management more efficient, scalable, and transparent.