Effective Vulnerability Remediation: Process and Strategies
Security isn’t just about finding vulnerabilities; it’s about fixing them fast, effectively, and with minimal disruption. But as attack surfaces grow and threat cycles accelerate, the remediation of vulnerabilities becomes more complex and resource-intensive.
Delays create risk. Missed patches create opportunity for attackers. And poor prioritization can overwhelm teams without improving security posture.
That’s why having a clear, structured approach to vulnerability remediation is essential. This guide walks through the key components of remediation, how it fits into the broader vulnerability management lifecycle, and the strategies that help security teams respond with precision, not panic.
Overview
The remediation of vulnerabilities involves identifying and fixing security flaws to prevent cyberattacks.
Prioritization is key, using CVSS scores, exploitability, exposure levels, and business impact to guide response.
Strategies include patching, mitigation, continuous monitoring, and risk-based decision-making.
Poorly managed remediation processes increase risk, delay compliance, and invite operational disruption.
Auditive simplifies vulnerability remediation with intelligent automation and a unified Trust Center for continuous security oversight.
What is Vulnerability Remediation?
Vulnerability remediation is the process of identifying and fixing security weaknesses across your systems, networks, or applications to prevent exploitation by cyber attackers. It’s a core component of vulnerability management, focused on eliminating risk at the source, not just detecting it.
Remediation may involve actions like patching software, updating configurations, or rewriting insecure code, anything required to resolve the underlying issue and close the attack vector.
Example:
Consider a SQL injection vulnerability caused by improper input validation. If left unresolved, attackers can inject malicious code and gain unauthorized access to your data. Through remediation, you’d implement input sanitization and update the code to block such exploitation, effectively neutralizing the threat.
By closing these gaps promptly, remediation protects sensitive data, ensures compliance, and supports the resilience of your organization’s digital infrastructure.
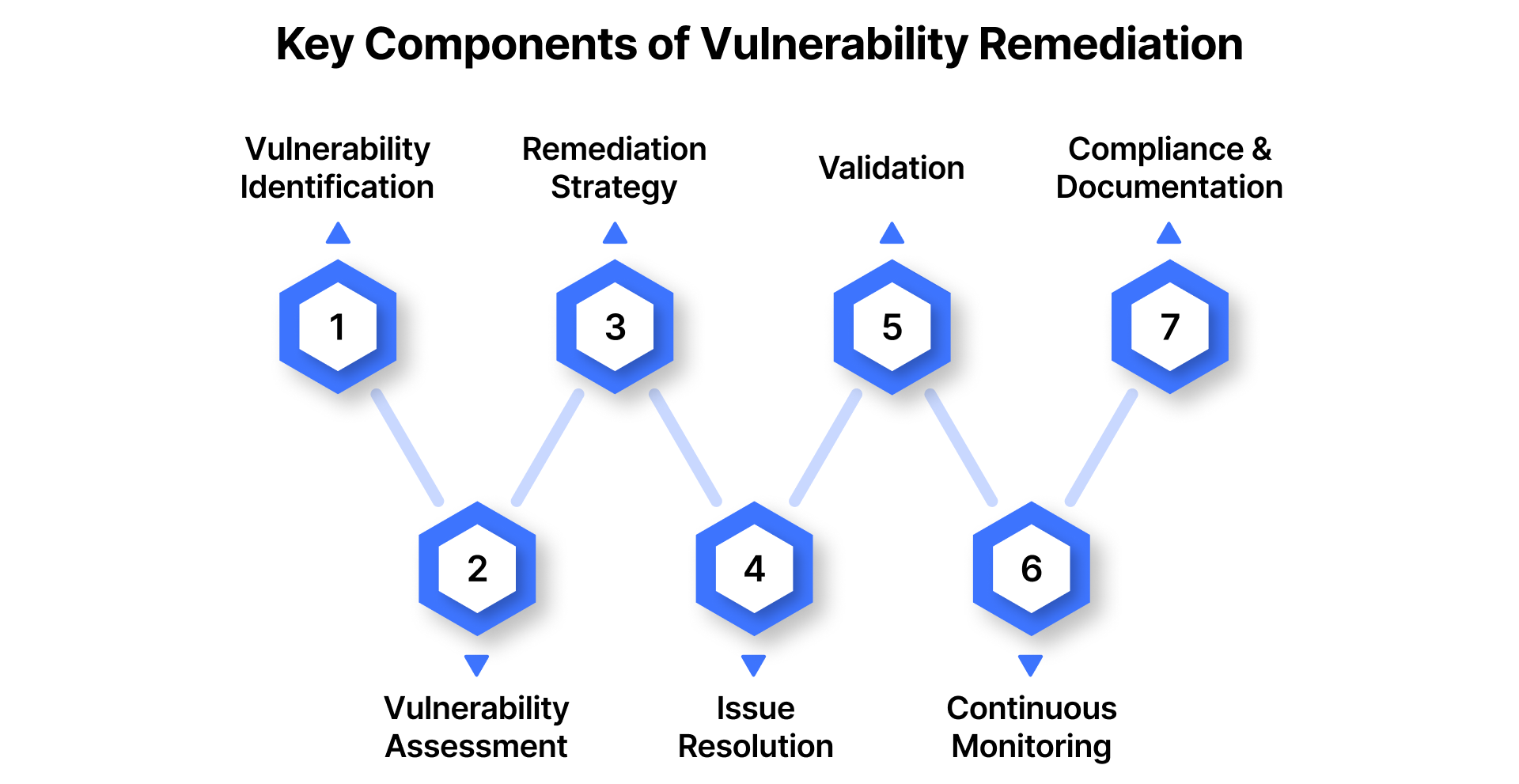
Key Components of Vulnerability Remediation
The remediation of vulnerabilities is not a one-time task; it’s a continuous, structured process designed to identify, assess, fix, and prevent security weaknesses before they’re exploited. Effective remediation requires more than patching; it demands coordination across systems, teams, and policies.
Below are the key components that form a comprehensive remediation strategy:
1. Vulnerability Identification
The first step is discovery. Use a combination of tools and methods to identify security gaps across your environment:
Automated vulnerability scanners for systems, networks, and applications
Penetration testing to simulate real-world attacks
Security audits to uncover policy misalignments and system weaknesses
2. Vulnerability Assessment
Not all vulnerabilities carry equal weight. Assess and prioritize based on:
Business impact analysis – How critical is the affected asset?
Exploitability – How easily can the vulnerability be weaponized?
CVSS (Common Vulnerability Scoring System) – Use this as a benchmark, but combine with internal risk metrics for context-aware prioritization.
3. Remediation Strategy
Once prioritized, determine the most effective remediation path. Options include:
Applying vendor-issued patches or updates
Modifying application code or configurations
Hardening security settings
Replacing vulnerable or unsupported systems
A well-defined strategy ensures that fixes are both timely and appropriate for the risk level.
4. Issue Resolution And Implementation
Execute the remediation plan with precision.
Apply tested patches across all relevant environments
Update drivers, firmware, and access controls
Enforce security policies to prevent recurrence
Test fixes in staging before full deployment to avoid operational disruption
5. Validation
Don’t assume a fix worked, verify it:
Re-scan systems to ensure vulnerabilities are closed
Run follow-up penetration tests
Monitor system logs for anomalies
Document results and flag any residual risks
6. Continuous Monitoring
Security is dynamic. Even after remediation, you need to maintain vigilance:
Use SIEM tools for real-time monitoring
Integrate threat intelligence feeds for context
Set up automated alerts for emerging vulnerabilities or misconfigurations
Continuous monitoring closes the loop between remediation and early detection.
7. Compliance And Documentation
A complete remediation program supports both internal accountability and external compliance:
Maintain detailed records of vulnerabilities, fixes, and dates of resolution
Generate compliance reports to satisfy auditors and regulatory requirements
Document audit trails to demonstrate due diligence and reduce liability
Together, these components create a resilient, repeatable framework for vulnerability remediation, one that evolves with your threat landscape, supports operational continuity, and meets growing compliance demands.
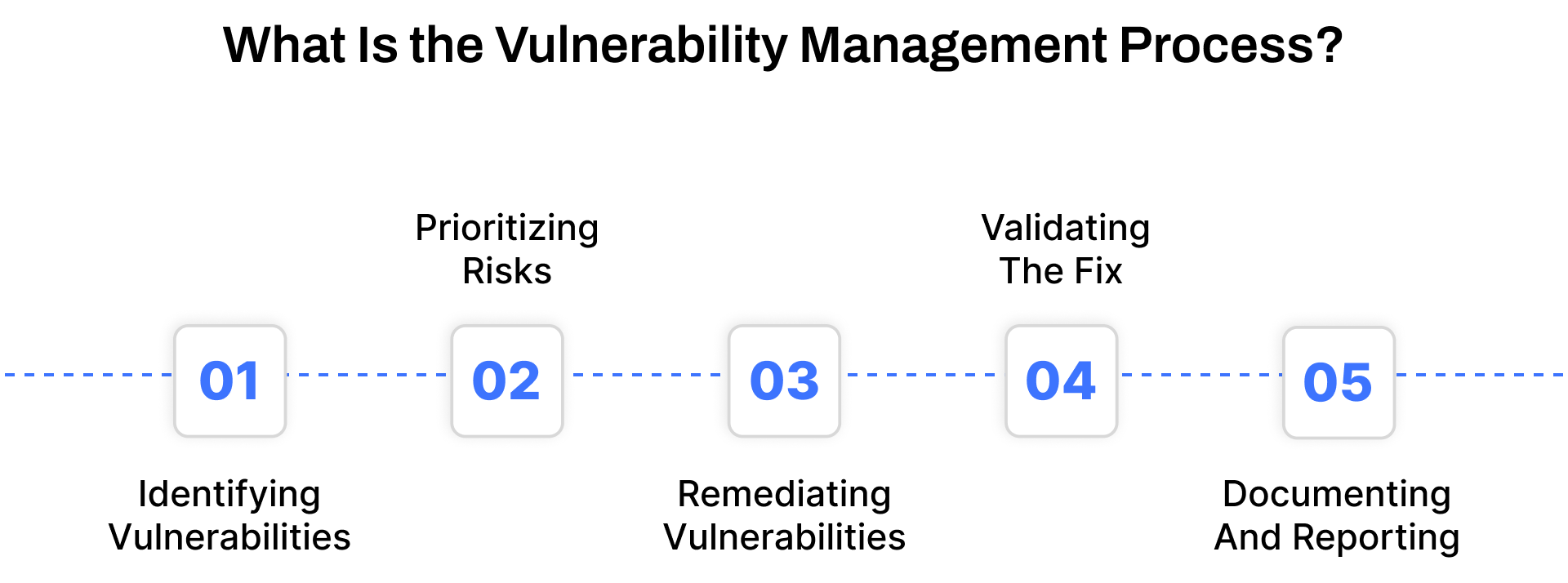
What Is the Vulnerability Management Process?
The vulnerability management process is a structured approach to identifying, assessing, prioritizing, and resolving security flaws across an organization’s IT landscape. Done correctly, it significantly reduces the risk of data breaches, malware infiltration, and compliance violations. Below are the key phases involved in the effective remediation of vulnerabilities:
Step 1. Identifying Vulnerabilities
The process begins by uncovering weaknesses, misconfigurations, exposed ports, weak passwords, outdated software, or malicious code, across networks, endpoints, and applications.
Common methods include:
Automated scanning: Use vulnerability scanners to detect missing patches, risky configurations, and known flaws.
Penetration testing: Simulate real-world attacks to expose deeper or contextual weaknesses that automated tools may miss.
Security assessments: Conduct internal audits to evaluate security controls against industry frameworks like HIPAA, PCI DSS, or ISO 27001.
Modern approaches also embed security earlier in development using shift-left testing and DevSecOps practices.
Step 2. Prioritizing Risks
Not all vulnerabilities demand equal attention. Prioritization ensures your team focuses on the threats most likely to cause real-world impact.
Key criteria include:
CVSS score: A numerical risk score (0–10) based on severity. Scores above 7.0 typically warrant urgent action.
Business impact: Identify vulnerabilities in systems that process sensitive data or support critical functions.
Exploitability: Immediate remediation is essential if an exploit is publicly available or if the flaw is a known zero-day.
Compliance exposure: Vulnerabilities affecting regulated data or public-facing systems often require rapid remediation to avoid penalties.
Step 3. Remediating Vulnerabilities
Once prioritized, you can begin implementing targeted fixes through a remediation plan tailored to the nature of each vulnerability.
Remediation methods include:
Patching outdated or vulnerable software with vendor-issued updates.
Code fixes to eliminate bugs or malicious functions at the application level.
Configuration changes to harden security settings and disable unused services.
System replacement if components are obsolete or pose unacceptable risk.
Compensating controls like firewalls, MFA, or network segmentation, used when a full fix isn’t yet possible.
Step 4. Implementing And Validating The Fix
Before rolling out changes across environments, test fixes in staging environments to ensure stability and avoid introducing new risks.
Post-remediation activities should include:
Re-scanning systems to confirm vulnerabilities are resolved.
Conducting penetration tests to evaluate fix effectiveness.
Reviewing security logs and monitoring tools for post-patch anomalies.
Remediation efforts should be reviewed and refined continuously to account for system changes and emerging threats.
Step 5. Documenting And Reporting
Thorough documentation is essential, for internal learning, audit readiness, and regulatory compliance.
Maintain detailed records that include:
Vulnerability source and severity
Remediation steps taken and timeline
Validation results
Residual risks or mitigation alternatives
A well-documented process provides transparency, helps demonstrate compliance, and strengthens your organization’s readiness for future vulnerabilities.
Best Practices for Vulnerability Remediation
Effective remediation isn’t about patching everything, it’s about responding with speed, clarity, and strategic focus. The following best practices help streamline the remediation of vulnerabilities while improving your overall security posture:
1. Implement Continuous Monitoring Tools
Static scans aren’t enough. Threats evolve constantly, and so should your visibility.
Deploy continuous monitoring tools to detect vulnerabilities the moment they emerge.
Leverage automated alerting and real-time dashboards to accelerate response times.
Ensure tools are configured to your environment and regularly updated for accuracy.
Continuous monitoring transforms vulnerability detection from a scheduled task into a live security function, essential for closing exposure windows before attackers can exploit them.
2. Maintain Documented Security Policies
Clarity under pressure is critical. A well-documented policy ensures everyone knows what to do, before, during, and after a security event.
Define step-by-step remediation workflows for common vulnerability types.
Outline roles, responsibilities, and escalation paths across IT, security, and compliance teams.
Use documentation as a training resource for onboarding and incident simulations.
Without a playbook, even the best tools fall short. Policies provide the structure that enables fast, coordinated remediation.
3. Prioritize Based On Risk, Not Volume
Every vulnerability isn’t created equal. Focus on what matters most.
Rank vulnerabilities by severity (e.g., CVSS score), exploitability, and potential business impact.
Align prioritization with business-critical systems and compliance requirements.
Review and reprioritize continuously as threat intelligence evolves.
Smart prioritization avoids alert fatigue and ensures resources are spent reducing real risk, not just clearing tickets.
4. Understand Your Environment
You can’t secure what you don’t fully understand.
Map out your infrastructure, applications, dependencies, network segments, and endpoints.
Identify system components that support critical operations or sensitive data.
Monitor how changes to one part of the environment affect others during remediation.
A deep understanding of your environment helps tailor remediation efforts, reduce unintended consequences, and ensure better long-term outcomes.
Taken together, these practices support a faster, smarter, and more adaptive remediation lifecycle, one that strengthens both security readiness and operational resilience.
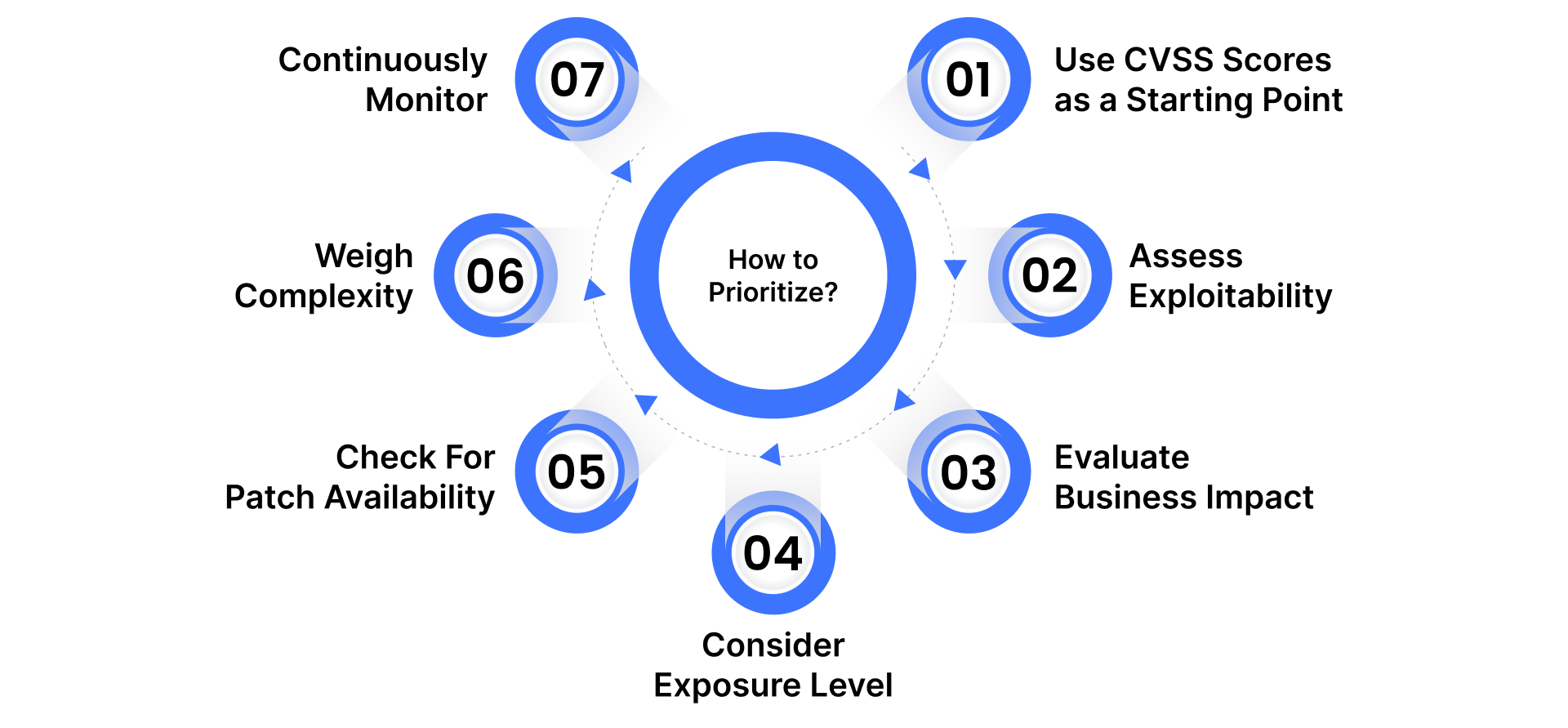
How to Prioritize Vulnerabilities for Remediation
Not all vulnerabilities pose the same threat. Some are low-risk and hard to exploit, while others are actively weaponized and exposed to the public internet. Effective remediation of vulnerabilities starts with knowing which ones to address first, and why.
Security and IT teams typically prioritize based on a combination of risk scoring, exploitability, business impact, and operational effort. Here's a breakdown of the most reliable methods used to assess and rank vulnerabilities:
1. Use CVSS Scores as a Starting Point
The Common Vulnerability Scoring System (CVSS) assigns severity ratings from 0 (negligible) to 10 (critical). It’s widely used to quickly gage the seriousness of a security flaw.
High CVSS scores signal urgent attention, but they don’t tell the full story on their own.
2. Assess Exploitability In The Real World
A vulnerability with a known exploit poses a greater risk than one without.
Check public databases for proof-of-concept code, active exploitation reports, or listings in exploit kits.
Prioritize vulnerabilities that are currently being used in attacks or are easily exploitable.
3. Evaluate Business Impact
Risk is contextual. A vulnerability that threatens sensitive data, critical systems, or regulatory compliance carries greater weight.
Map vulnerabilities to business-critical assets.
Consider potential impact on uptime, customer data, and legal obligations.
4. Consider Exposure Level
Vulnerabilities in public-facing systems (like web apps, APIs, or internet-exposed servers) should be addressed before those in isolated environments.
Prioritization order: public > internal > isolated.
5. Check For Patch Availability
If a patch exists, apply it, fast.
For unpatched vulnerabilities, implement mitigations like network segmentation, access controls, or temporary shutdowns.
Track patch release timelines for critical flaws lacking fixes.
6. Weigh Remediation Complexity
Some high-risk vulnerabilities are quick fixes. Others require downtime, configuration changes, or system-wide testing.
Prioritize low-effort, high-impact fixes to reduce exposure quickly.
Balance remediation workload against available resources.
7. Continuously Monitor and Reprioritize
Threats evolve, and so should your remediation queue.
Implement continuous scanning and monitoring to catch emerging risks.
Adjust prioritization as new vulnerabilities, patches, or business changes arise.
Effective prioritization is what turns vulnerability data into actionable security. By combining risk intelligence with business context, organizations can focus their efforts where they matter most, and reduce exposure before it becomes exploitation.
Conclusion
Vulnerabilities are inevitable. But leaving them unaddressed isn’t just risky, it’s a missed opportunity to harden your defenses and build operational resilience. Effective remediation of vulnerabilities goes beyond patching; it’s a structured, ongoing process of prioritizing, acting, and adapting to a constantly shifting threat landscape.
At Auditive, we help organizations gain control over vulnerability management with intelligent prioritization, real-time risk insights, and vendor oversight, all through a centralized Trust Center.
Want to reduce your exposure and remediate faster?
FAQs
Q1. What is vulnerability remediation?
A1. Vulnerability remediation is the process of identifying, prioritizing, and fixing security weaknesses in software, systems, or infrastructure to reduce the risk of exploitation.
Q2. How is remediation of vulnerabilities different from vulnerability management?
A2. Remediation is a key phase within the broader vulnerability management lifecycle, which includes identification, assessment, prioritization, remediation, and ongoing monitoring.
Q3. What tools are used for vulnerability remediation?
A3. Organizations use vulnerability scanners, patch management systems, threat intelligence platforms, and compliance tools to detect and resolve vulnerabilities effectively.
Q4. How do I prioritize which vulnerabilities to remediate first?
A4. Use factors like CVSS score, exploit availability, business impact, exposure level, and remediation complexity to determine which vulnerabilities pose the highest risk.
Q5. What if a patch is not available for a known vulnerability?
A4. In such cases, implement compensating controls such as access restrictions, segmentation, disabling affected services, or applying virtual patches until a fix is released.