Integrating Cyber Risk and Enterprise Risk Management Strategies
Today’s cyber threats target your business model, not just your firewalls. From ransomware attacks to third-party data breaches, cyber incidents can grind operations to a halt and erode public trust overnight. Yet many organizations still treat cybersecurity and enterprise risk management (ERM) as separate functions.
To build true resilience, organizations need to embed cybersecurity directly into their ERM frameworks. This blog explores how to integrate enterprise risk management and cybersecurity into a unified strategy that protects your organization, reputation, and bottom line.
TL;DR
Cyber threats now pose enterprise-wide risks, not just IT problems.
Aligning cybersecurity with ERM ensures better governance, resilience, and visibility.
Challenges include siloed ownership, language barriers, and outdated risk models.
Embedding cyber risk in ERM frameworks like NIST, COSO, and ISO boosts response effectiveness.
Tools like Auditive’s Trust Center simplify vendor and cyber risk management in real time
Why Cybersecurity Must Be Embedded in Enterprise Risk Management?
Cyber risk is no longer a siloed IT issue; it’s a strategic business threat with far-reaching implications across the organization. From ransomware attacks that bring operations to a standstill to third-party breaches that invite regulatory scrutiny, cyber incidents affect every layer of enterprise resilience and performance.
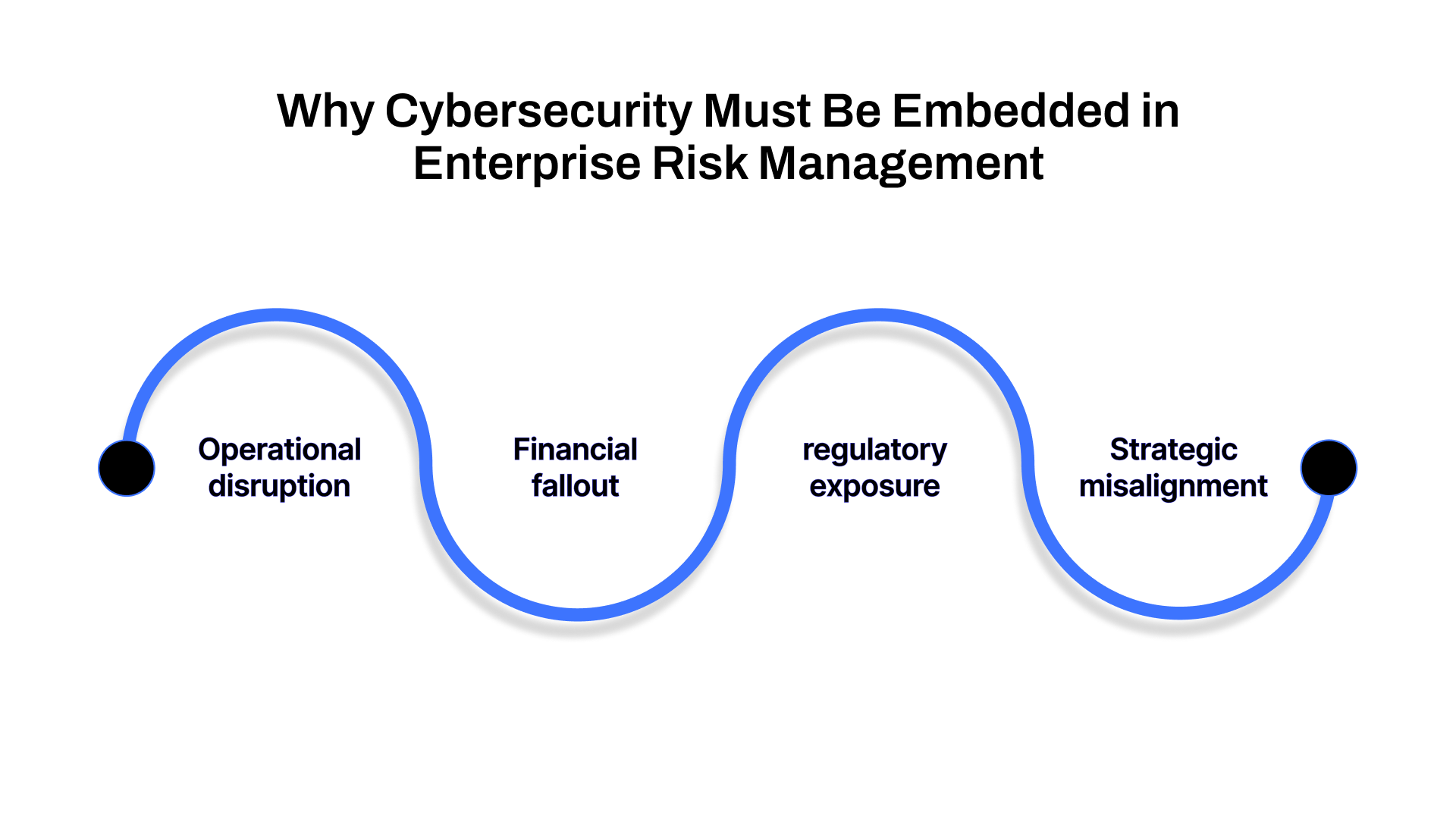
Embedding cybersecurity within your enterprise risk management (ERM) framework is essential for four key reasons:
1. Operational disruption
Cyber incidents can paralyze critical business processes. From halting logistics and manufacturing to disrupting customer portals and financial systems, the ripple effects of an attack often extend far beyond IT.
Example: A phishing attack on a vendor could disable your supply chain systems for days, resulting in shipment delays, SLA violations, and reputational damage.
2. Financial fallout
The cost of cyber incidents is growing, not just in terms of ransomware payments or regulatory fines, but also in the long-term erosion of customer trust and revenue.
According to IBM’s 2024 report, the global average cost of a data breach has risen to $4.45 million, with even higher costs when third-party vendors are involved.
3. Compliance and regulatory exposure
Modern data protection frameworks like GDPR, HIPAA, NIST CSF, and ISO 27001 require a formal, enterprise-level approach to cyber risk governance. Failing to align cybersecurity within ERM can result in audits, fines, and operational penalties.
Regulators increasingly expect cyber risk to be part of your enterprise risk posture, not a reactive sidecar.
4. Strategic misalignment
Digital transformation, cloud migration, and AI adoption are key to business growth, but each brings new cyber risks. Without aligning cyber security with strategic business goals, you risk undermining the very innovation you’re investing in.
Cyber risk isn’t just about preventing incidents, it’s about enabling secure innovation.
Failing to treat cybersecurity as a core pillar of ERM creates blind spots in decision-making and undermines organizational resilience.
Cybersecurity doesn't just support ERM, it strengthens it.
5 Key Components of an Effective Enterprise Risk Management Framework
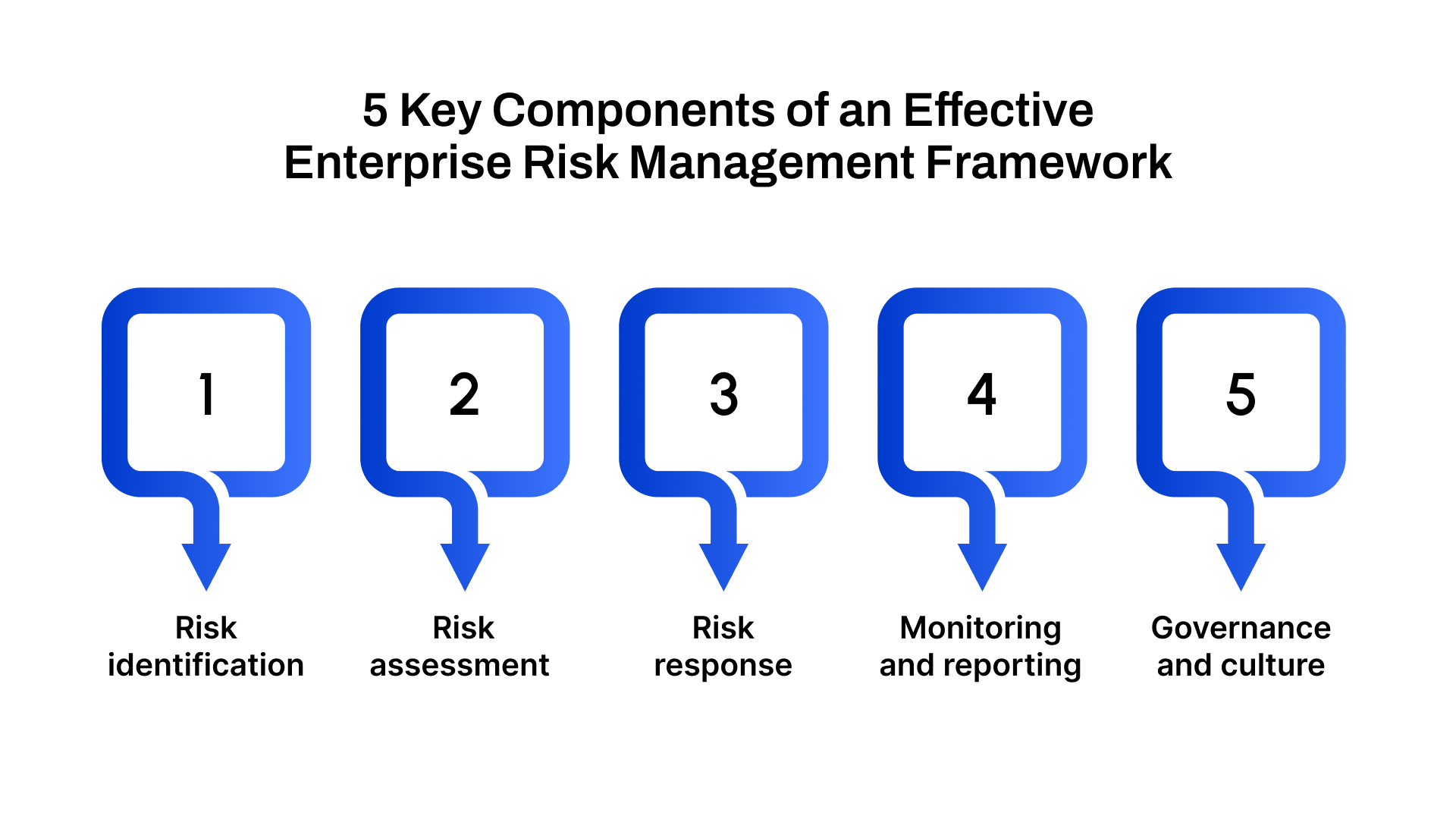
A strong ERM strategy isn’t just about creating a list of potential threats, it’s about building a living framework that continuously aligns risk awareness with business objectives. Below are the essential components that form the backbone of a mature and resilient ERM program:
1. Risk identification
The first step in managing risk is knowing where it lives. ERM begins with a comprehensive scan of both internal and external risks, from financial volatility and regulatory shifts to emerging cyber threats, operational breakdowns, third-party dependencies, and reputational issues.
Effective risk identification requires collaboration across business units to ensure no threat slips through the cracks.
2. Risk assessment
Once risks are identified, they must be assessed through two lenses:
Likelihood: How probable is this risk in the current or future environment?
Impact: What would be the consequence on operations, revenue, reputation, or compliance?
This assessment is not a one-time task. In dynamic sectors like cybersecurity, risk profiles change rapidly, and your ERM strategy must evolve just as quickly.
3. Risk response
ERM is as much about action as it is about analysis. Organizations need clear strategies to manage each identified risk:
Mitigation: Implement controls to reduce the risk.
Avoidance: Eliminate the risk by changing plans or processes.
Transfer: Shift the risk to a third party (e.g., insurance or outsourcing).
Acceptance: Acknowledge the risk and monitor it with contingency plans.
The chosen response should align with your risk appetite and business objectives, balancing resilience with agility.
4. Monitoring and reporting
Risk management is not static. Continuous monitoring ensures real-time visibility into evolving threats, while regular reporting keeps stakeholders informed and engaged.
Modern ERM platforms use dashboards, automated alerts, and trend analysis to flag emerging issues before they escalate, enabling leadership to make faster, more informed decisions.
Bonus: When integrated with cybersecurity, monitoring can also surface real-time threats like vendor vulnerabilities, system anomalies, or compliance lapses.
5. Governance and culture
The effectiveness of any ERM program depends on governance and culture. Strong ERM isn’t owned solely by risk or compliance teams, it must be embedded across the organization, from the boardroom to front-line employees.
Governance ensures clear roles, accountability, and oversight.
Culture fosters risk awareness, open reporting, and shared responsibility.
Building a risk-aware culture empowers teams to act proactively, rather than waiting for directives or disasters.
6 Steps to Integrate Cybersecurity into Enterprise Risk Management
Here’s how leading organizations are bridging the gap between cybersecurity and ERM:
Step 1. Embed cyber risk into your risk register
Start by incorporating cybersecurity as a top-level category in your enterprise risk register. Define specific cyber risks, like data breaches, insider threats, or DDoS attacks, and map them to business processes and assets they impact.
Tip: Use financial impact and likelihood to prioritize cyber risks, not just technical severity.
Step 2. Align risk frameworks
Select industry-standard frameworks that support both cyber and enterprise risk needs. For example:
NIST Cybersecurity Framework (CSF)
ISO 27005
COSO ERM Framework
Quantara CRC™ model for dynamic enterprise-aligned scoring
Aligning these models ensures a shared vocabulary and measurable outcomes across teams.
Step 3. Shift from maturity to consequence-based models
Instead of simply measuring how “mature” your security program is, assess the actual business consequences of different threat scenarios. This helps the board and executive team understand the financial and operational stakes.
Example: Rather than saying “we have MFA in place,” explain how its absence could expose critical payroll systems to credential compromise, leading to fraud or downtime.
Step 4. Integrate Third-Party Risk Management (TPRM)
Third parties are one of the largest blind spots in cybersecurity. Build a TPRM process that:
Evaluates vendor risk during onboarding
Aligns with your ERM risk categories
Continuously monitors vendor security posture
Auditive’s platform, for example, simplifies this by connecting vendors to frameworks relevant to your industry and tracking risk in real time.
Step 5. Use real-time monitoring and AI-driven insights
Static assessments won’t cut it. Modern enterprise risk management cyber security strategies need continuous monitoring, automated scoring, and AI insights to keep pace.
AI-driven tools can:
Prioritise threats based on business impact
Automate security reviews
Predict vulnerabilities using behavioral analytics
Platforms like Quantara and Auditive help translate raw cyber data into board-ready risk narratives.
Step 6. Foster cross-functional collaboration
Cyber and ERM teams must collaborate, not compete. Regular joint workshops, shared dashboards, and combined risk committees help unify efforts.
Tip: Translate cyber risks into business language. Instead of “phishing threat,” say “potential disruption to customer onboarding workflows.”
Challenges in Aligning Cyber Risk with Enterprise Risk Management
Bridging the gap between cybersecurity and enterprise risk management (ERM) is essential, but it’s rarely straightforward. Despite shared goals, these functions often operate in silos, using different tools, languages, and timelines. This disconnect leads to blind spots in risk visibility and delayed decision-making.
Here are the core challenges that hinder effective integration:
1. Siloed structures and ownership
Cybersecurity is typically housed within IT or security teams, while ERM resides under compliance, finance, or legal functions. Without shared accountability or governance, critical risks can be overlooked or miscommunicated, particularly those that straddle both domains, like third-party breaches or regulatory compliance failures.
2. Incompatible risk languages
Cyber teams speak in vulnerabilities, CVEs, and threat actors. ERM teams assess risks in terms of financial impact, regulatory exposure, and strategic disruption. This language gap makes alignment difficult, especially when presenting cyber risks to executive stakeholders who expect business-contextual insights.
3. Lack of financial quantification
Unlike operational or financial risks, cyber threats are often difficult to quantify in monetary terms. Without converting cybersecurity scenarios into measurable business impact, it becomes challenging to prioritize cyber risk alongside other enterprise threats, like supply chain disruption, inflation, or geopolitical uncertainty.
4. Static vs. Dynamic risk models
Traditional ERM frameworks tend to rely on quarterly or annual risk assessments. But cyber risk changes daily, if not hourly. Static models can’t keep pace with zero-day vulnerabilities, real-time phishing attacks, or active third-party breaches.
A lack of continuous monitoring creates risk blind spots.
5. Poor integration of third-party risk
As more business functions rely on vendors, contractors, and cloud providers, third-party risk management (TPRM) becomes a critical component of cyber and enterprise risk. However, TPRM is often treated separately, with no centralized reporting into the ERM framework. This fragmented approach leaves organizations vulnerable to vendor-based attacks or compliance failures.
6. Misaligned communication and governance
Without unified reporting lines or shared dashboards, communication between cyber, ERM, and business units can break down. This can delay risk response, lead to inconsistent reporting, and create a false sense of security across teams.
Overcoming these challenges requires a shift in mindset and methodology, from siloed assessments to integrated, real-time visibility. A dynamic ERM program must embed cyber risk into its core operations, supported by tools, frameworks, and cross-functional collaboration that enable shared understanding and action.
How Auditive Supports Integrated Cyber-ERM Strategy
Auditive simplifies third-party risk management and cybersecurity integration across your entire vendor ecosystem:
Monitor vendor risk continuously, not just during onboarding
Quantify real business risk using industry-relevant frameworks
Accelerate security reviews with 35% higher vendor response rates
Centralize vendor data into one live network for faster insights
4x faster onboarding through seamless workflow integration
Auditive helps operationalize your vendor risk policy while providing real-time visibility, AI-backed scoring, and stronger compliance across all touchpoints.
Want to see how Auditive brings cyber and enterprise risk together? Learn more>>>>
Conclusion
In a threat landscape that moves faster than policies can be updated, integrating enterprise risk management and cybersecurity is no longer optional; it’s essential. A siloed approach puts your business, reputation, and stakeholders at risk.
By embedding cyber risk and Vendor Risk Management directly into your ERM framework, aligning to industry-relevant standards, and adopting platforms like Auditive’s Trust Center, you gain the visibility, context, and agility needed to stay ahead of evolving threats.
Cyber risk is enterprise risk, and vendor risk is a core part of that story.
Treat them accordingly, and you’ll build a safer, smarter, and more future-ready organization.
Ready to simplify vendor risk and take control of your cyber exposure? Schedule a demo with Auditive and see how real-time, contextual risk management changes everything.
FAQs
Q1. Why should cybersecurity be part of enterprise risk management?
A1. Because cyber incidents now affect operations, finances, compliance, and reputation, making them critical enterprise risks, not isolated technical issues.
Q2. What frameworks help align cyber and enterprise risk?
A2. Standards like NIST CSF, ISO 27001, COSO ERM, and Quantara CRC™ help unify language, priorities, and measurement.
Q3. How can we quantify cyber risks like we do for financial or operational risks?
A3. By translating technical risks into business impact terms, like downtime cost, revenue loss, or regulatory penalties, using consequence-based models.
Q4. How do third-party vendors factor into our cyber and enterprise risk strategy?
A4. Vendors can be significant risk vectors. An integrated vendor risk management strategy helps identify, monitor, and mitigate those exposures effectively.
Q5. What does Auditive offer for cyber-ERM integration?
A5. Auditive provides real-time vendor risk insights, industry-aligned frameworks, and automated workflows, all centralized in the Trust Center for continuous visibility and faster decision-making.