Step-by-Step Guide to Process Remediation Basics
Security gaps are inevitable, but how organizations handle them determines their resilience. Process remediation is the systematic approach to identifying, addressing, and resolving vulnerabilities before they escalate into serious issues. It’s not just about reacting to threats; it’s about having a repeatable plan to eliminate risk efficiently and consistently.
Whether it’s a misconfigured system, an outdated dependency, or a newly discovered exploit, every weakness needs a clear path to resolution. That’s where process remediation steps in, connecting vulnerability detection to action with clarity, ownership, and speed.
This guide breaks down the essentials of vulnerability and process remediation: what it involves, why it matters, and how to get it right from the start.
Overview
Process remediation is about identifying and fixing vulnerabilities to secure systems before attackers can exploit them.
Use factors like CVSS score, exploitability, and business impact to prioritize effectively.
Addressing vendor-related risks is essential, vendor risk management must be part of your strategy.
A Trust Center helps centralize remediation activities, improve visibility, and reduce response time.
Tools like Auditive integrate context, automation, and third-party risk into your remediation workflows, streamlining operations and improving outcomes.
What is Vulnerability Remediation?
Vulnerability remediation is the process of identifying and fixing security weaknesses across an organization’s systems, networks, or applications to prevent exploitation. It's a critical component of broader vulnerability management, which includes discovering vulnerabilities, analyzing their impact, prioritizing them, and ultimately resolving them.
The goal of remediation is to close security gaps before attackers can exploit them. This includes everything from patching outdated software to reconfiguring systems or rewriting insecure code.
Example:
Suppose a web application has a SQL injection vulnerability due to improper input validation. This allows attackers to manipulate backend databases using malicious code. A proper remediation response would involve rewriting the code to sanitize inputs and eliminate the flaw, effectively blocking any unauthorized data access.
Remediation doesn’t just fix problems, it reduces risk, safeguards sensitive data, and strengthens the overall security posture of your organization.
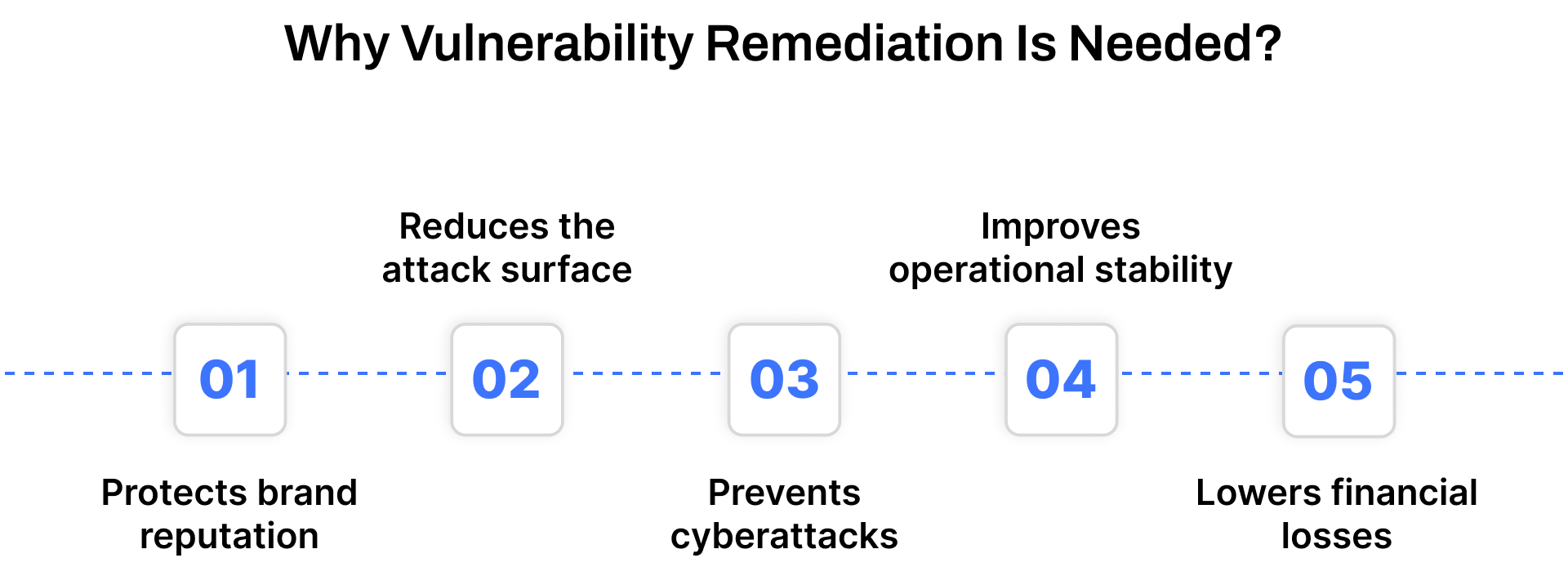
Why Vulnerability Remediation Is Needed
Unpatched vulnerabilities are a favorite entry point for attackers. Without a solid remediation strategy, these gaps can quickly lead to serious damage, compromised systems, operational downtime, and loss of trust.
Here’s why timely remediation is essential:
Protects brand reputation
Even a single breach can undermine years of customer trust. Resolving vulnerabilities before they’re exploited helps preserve credibility and safeguard brand reputation.
Reduces the attack surface
The more unaddressed weaknesses in your environment, the more opportunities for intrusion. Proactive remediation limits exposure and hardens defenses by eliminating known entry points.
Prevents cyberattacks
Hackers constantly scan for systems with outdated configurations and missing patches. Remediation helps close those openings and shut down potential threats before they escalate.
Improves operational stability
Security incidents often bring business operations to a halt. By fixing vulnerabilities early, organizations can avoid disruptions and maintain consistent service delivery.
Lowers financial losses
Remediation isn’t just a security measure, it’s a cost-control strategy. Preventing breaches reduces the risk of penalties, lawsuits, and direct financial hits from incidents like ransomware.
Neglecting vulnerabilities is not a passive risk, it’s an open invitation for disruption. Effective remediation isn’t just about fixing flaws; it’s about reducing exposure, protecting customer trust, and ensuring business continuity.
Key Components of Vulnerability Remediation
Effective vulnerability remediation goes beyond simply patching flaws, it’s about building a repeatable, risk-based workflow that eliminates exposure with confidence. Here are the foundational components every organization needs to strengthen their remediation lifecycle:
1. Vulnerability Identification
The first step is to detect flaws across systems, applications, networks, and endpoints. This typically involves automated scanners, penetration testing, threat intel, and internal security audits. Early and accurate detection is crucial to reducing risk before it can be exploited.
2. Vulnerability Assessment
Not every vulnerability demands immediate attention. Prioritization should be based on exploitability, business impact, and factors like CVSS scores. Categorizing threats by severity helps remediation teams focus on what actually matters, reducing risk, not just closing tickets.
3. Remediation Strategy
Once vulnerabilities are assessed, the next step is to determine the right approach for fixing them. This might include applying patches, reconfiguring systems, updating code, or isolating affected components. The strategy should align with the severity of the threat and the organization’s operational priorities.
4. Fix Implementation
Security fixes should be applied in a controlled and tested manner. Whether it’s patching third-party tools, updating internal codebases, or adjusting firewall settings, remediation needs to be executed with precision. Testing in a staging environment first helps ensure business continuity.
5. Validation
After implementing fixes, validation ensures nothing was missed. Re-scanning systems, reviewing logs, and confirming patch effectiveness are essential steps. Validation also helps maintain credibility with stakeholders and prepares your environment for audits.
6. Continuous Monitoring
Threat landscapes evolve quickly. Maintaining visibility through continuous monitoring, via SIEM tools, automated alerting, or external threat intelligence, helps detect new vulnerabilities before they become breaches. It’s the feedback loop that keeps the remediation process effective over time.
7. Compliance and Documentation
All actions taken during the remediation lifecycle should be documented. This includes vulnerability reports, fix timelines, approval workflows, and compliance evidence. These records support audit readiness and help meet regulatory requirements.
Auditive’s Trust Center and vendor risk management platform simplifies vulnerability remediation by centralizing assessments, tracking fixes, and ensuring complete, audit-ready documentation, so nothing slips through.
Types of Vulnerability Remediation
Organizations don’t need a one-size-fits-all approach to fixing vulnerabilities. The best remediation method depends on the risk level, business impact, and how quickly the issue needs resolution. Below are the primary remediation strategies teams rely on to harden their environments:
1. Patching
Patching is one of the most common and effective forms of remediation. It involves applying updates or security fixes released by vendors to close known vulnerabilities. For example, deploying a Windows security patch to address a zero-day threat.
2. Code Remediation
When issues originate in custom-built applications, code remediation is essential. It involves modifying source code to eliminate vulnerabilities like cross-site scripting (XSS) or SQL injection. This proactive fix strengthens the application at its core and helps block future exploits.
3. Configuration Changes
Security misconfigurations are low-hanging fruit for attackers. Adjusting system, network, or application settings can eliminate exposure without waiting for a patch. Disabling outdated protocols like TLS 1.0 is a common step that helps tighten controls and prevent downgrade attacks.
4. Access Control Adjustments
Excessive access is a silent risk. Restricting user permissions ensures that employees and third parties can only interact with data and systems essential to their roles. For instance, finance teams don’t need admin access to IT infrastructure. Cutting unnecessary access reduces the blast radius of potential breaches.
5. Removing Vulnerable Components
Some vulnerabilities come from outdated or unsupported technologies.
The cleanest solution?
Remove and replace them. Replacing legacy operating systems or deprecated libraries limits exposure and brings your environment up to modern standards.
6. Temporary Security Measures
When a fix isn’t immediately available, interim security controls can help manage the risk. Firewalls, WAF rules, and endpoint detection tools can block known attack vectors until a patch or update is deployed.
Why this matters: Without consistent remediation processes, risks accumulate fast, and attackers only need one weakness. That’s why centralized vendor risk management and coordinated trust frameworks play a key role.
Platforms like Auditive bring visibility and structure across remediation efforts, helping teams act decisively when vulnerabilities surface. From identifying vendor-specific risks to enabling trust-based controls across your ecosystem, Auditive ensures nothing slips through the cracks.
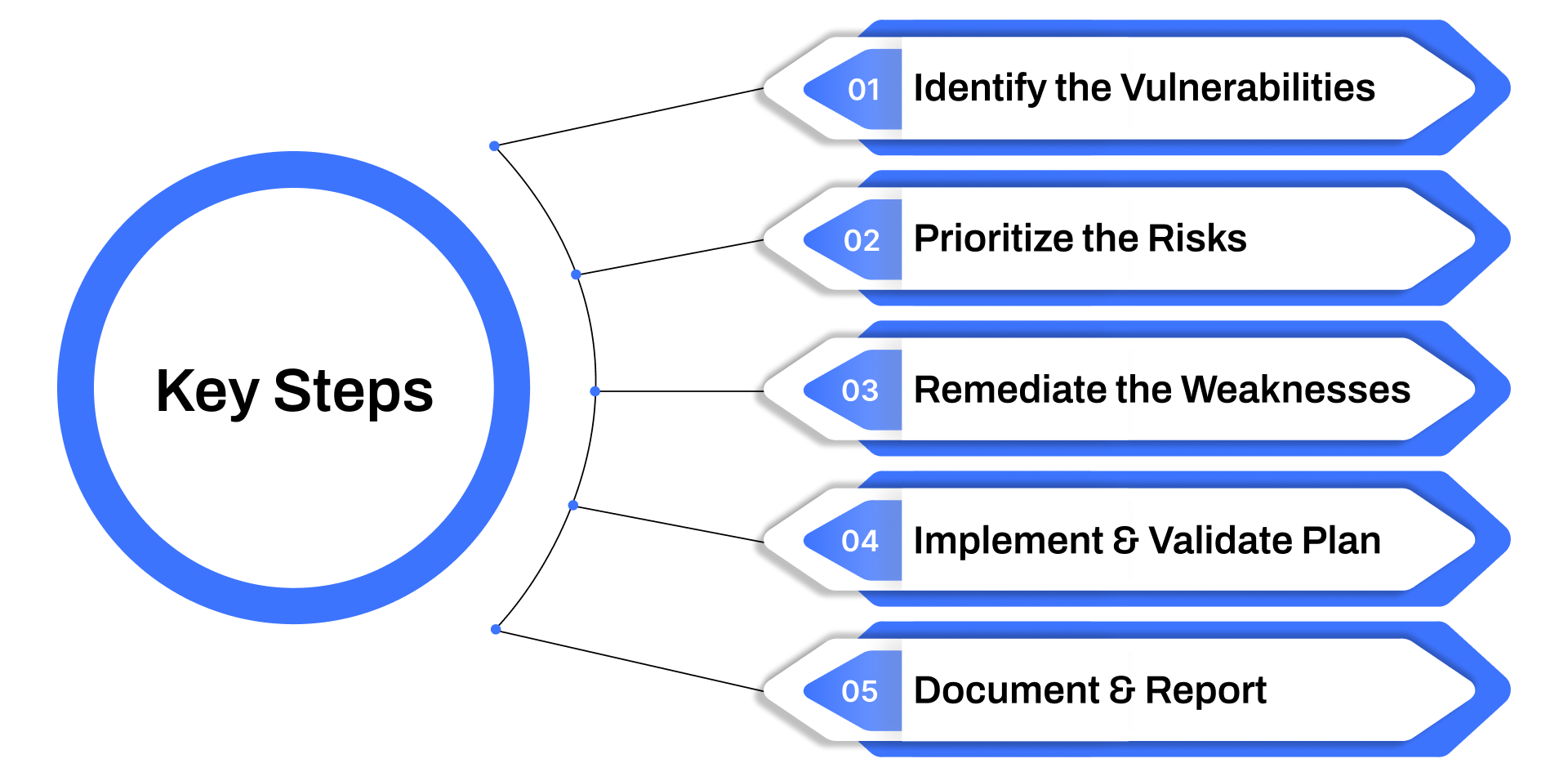
Key Steps in the Vulnerability Remediation Process
Fixing a security weakness isn’t just about applying a patch and moving on. It requires a clear, consistent, and prioritized approach that aligns with your organization’s risk tolerance, compliance needs, and infrastructure complexity. Here’s how to tackle vulnerability remediation effectively, step by step:
1. Identify the Vulnerabilities
Start by locating the cracks in your infrastructure, before someone else does. This step involves actively scanning your systems and performing controlled tests to uncover both obvious and hidden weaknesses.
Automated Scanning: Leverage advanced vulnerability scanners to automatically flag outdated software, misconfigurations, missing patches, and more.
Penetration Testing: Go beyond automation. Simulate real-world cyberattacks to expose weaknesses that standard scanners often overlook.
Security Assessments: Schedule routine internal audits to ensure security controls meet frameworks like HIPAA, PCI DSS, or GDPR.
Modern tools that integrate into the DevOps pipeline can identify flaws early in development, making them easier and cheaper to fix.
Auditive Insight: Integrating a continuous scanning and testing framework like Auditive's proactive trust controls helps businesses detect risks early, especially in highly regulated industries where vendor ecosystems can introduce new threat surfaces.
2. Prioritize the Risks
Not all vulnerabilities are created equal. The goal is to focus your efforts where they matter most. Prioritization is based on severity, exposure, business impact, and whether an exploit is actively being used in the wild.
Key prioritization criteria include:
CVSS Score: Use the Common Vulnerability Scoring System (0–10 scale) to classify severity, critical, high, medium, or low.
Business Impact: Evaluate how a vulnerability could affect systems tied to customer data, financial transactions, or operational uptime.
Exploitability: Address known exploits and zero-day threats immediately, even in the absence of a patch, by tightening controls like MFA, access limits, or firewalls.
3. Remediate the Weaknesses
Now it’s time to act. Depending on the nature of the threat and the affected system, choose the most appropriate fix.
Common remediation techniques:
Patch Management: Apply vendor-issued security updates as soon as they’re available.
Code Fixes: Clean up insecure or outdated code to eliminate logic flaws or backdoors.
Configuration Hardening: Disable unnecessary ports, enforce stricter authentication policies, and remove legacy services.
System Replacement: Decommission software or hardware that’s no longer supported or too risky to keep.
Compensating Controls: When a permanent fix isn’t possible, put temporary guards in place, like network segmentation or traffic monitoring, to limit exposure.
4. Implement and Validate the Remediation Plan
Once fixes are ready, roll them out in a controlled environment. Before deployment across production systems, test updates to ensure they don’t introduce new issues or interrupt core functions.
After implementation:
Re-scan systems to confirm vulnerabilities have been resolved.
Conduct targeted penetration tests to verify resilience.
Monitor logs for anomalies that may indicate incomplete remediation.
Validation isn’t a one-off task. Build ongoing verification into your security lifecycle to adapt to evolving threats.
Auditive Insight: Auditive’s Trust Center provides a centralized view of all security validation activities, offering automated assurance reports and visibility across complex environments.
5. Document Everything and Report
Good documentation helps you respond faster the next time something goes wrong, and proves compliance when regulators come calling. Record what was remediated, when, how, and by whom.
Your remediation log should include:
Vulnerability ID and description
Remediation actions taken
Dates of discovery and resolution
Impact assessment
Verification results
Auditive streamlines this process through automated reporting, making it easier for teams to stay audit-ready while maintaining complete visibility into remediation history.
How to Prioritize Vulnerabilities for Remediation
Not all vulnerabilities carry the same level of risk, or urgency. Some are actively exploited in the wild, while others may never be used. That’s why security teams need a structured method to decide what gets fixed first.
Here’s how to approach vulnerability prioritization effectively:
CVSS Score
The Common Vulnerability Scoring System (CVSS) provides a baseline for severity, rating issues from 0 to 10. While a helpful starting point, CVSS alone shouldn’t drive final decisions.
Exploitability
A vulnerability with a high CVSS score but no active exploit poses less immediate danger than one being actively weaponized. Always check exploit databases for public proof-of-concepts or real-world usage.
Business Impact
Prioritize vulnerabilities based on the sensitivity of the systems or data they affect. A low-score issue impacting core business systems may carry more risk than a high-score issue on a non-critical server.
Vulnerability Exposure
Public-facing systems demand faster attention than isolated internal components. External exposure significantly increases the likelihood of attack and should influence prioritization accordingly.
Patch Availability
If a patch is available, implement it without delay. For issues with no official fix, focus on mitigation, such as restricting access, segmenting affected systems, or applying compensating controls.
Remediation Complexity
Teams must weigh effort against risk. A moderate-risk issue that’s quick to resolve may be more urgent than a high-risk issue that requires major downtime to fix.
Continuous Monitoring
Threat landscapes shift quickly. Regular scanning, threat intelligence, and automation help ensure priorities stay aligned with the latest real-world activity.
Where Auditive Fits In
Auditive helps security and IT teams streamline prioritization through real-time risk intelligence, business context awareness, and integrated vendor risk management. Its Trust Center gives visibility into which vulnerabilities affect critical vendors and internal systems alike, allowing teams to act based on actual business impact, not just generic severity scores.
With custom workflows, exposure mapping, and continuous monitoring built-in, Auditive supports a remediation strategy that’s not just reactive, but resilient.
Conclusion
Vulnerability remediation isn’t a box to check, it’s an ongoing process tied directly to your organization’s resilience, compliance, and operational stability. But managing risks in isolation isn’t enough. Today’s threat surface spans across internal systems and external vendors, making vendor risk management a critical part of the equation.
That’s where Auditive makes a difference. With its centralized Trust Center, contextual risk insights, and intelligent workflows, teams can gain visibility across the supply chain, understand remediation priorities, and act with precision, not guesswork.
Take control of your remediation strategy with Auditive’s Trust Center and put real-time vendor risk management at the core of your security operations.
Ready to strengthen your risk posture? Explore Auditive and schedule a tailored demo.
FAQs
1. What is process remediation in cybersecurity?
Process remediation refers to the steps taken to identify, assess, and fix vulnerabilities within systems, networks, or applications to reduce the risk of exploitation.
2. How does the CVSS score help in remediation?
The CVSS score helps classify the severity of a vulnerability, guiding teams on which issues may need more urgent attention. However, it must be considered alongside exploitability, business impact, and patch availability.
3. Why is vendor risk management important in remediation?
Vulnerabilities in third-party systems can impact your operations. Effective vendor risk management ensures these external risks are monitored and addressed as part of your broader remediation efforts.
4. What’s the role of a Trust Center in security operations?
A Trust Center centralizes visibility into internal and external risk factors, compliance status, vendor performance, and remediation activities, enabling faster and smarter decision-making.
5. How often should vulnerabilities be reassessed?
Continuously. Threats evolve quickly, and so should your risk assessments. Regular scanning, monitoring, and reassessment ensure no critical issues fall through the cracks.